About system kali linux
Kali Linux (formerly known as BackTrack Linux) is an open-source, Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing. It does this by providing common tools, configurations, and automations which allows the user to focus on the task that needs to be completed, not the surrounding activity.
Kali Linux contains industry specific modifications as well as several hundred tools targeted towards various Information Security tasks, such as Penetration Testing, Security Research, Computer Forensics, Reverse Engineering, Vulnerability Management and Red Team Testing.
Kali Linux is a multi-platform solution, accessible and freely available to information security professionals and hobbyists.
Kali Linux Features
- More than 600 penetration testing tools included: After reviewing every tool that was included in BackTrack, we eliminated a great number of tools that either simply did not work or which duplicated other tools that provided the same or similar functionality. Details on what’s included are on the Kali Tools site.
- Free (as in beer) and always will be: Kali Linux, like BackTrack, is completely free of charge and always will be. You will never, ever have to pay for Kali Linux.
- Open source Git tree: We are committed to the open source development model and our development tree is available for all to see. All of the source code which goes into Kali Linux is available for anyone who wants to tweak or rebuild packages to suit their specific needs.
- FHS compliant: Kali adheres to the Filesystem Hierarchy Standard, allowing Linux users to easily locate binaries, support files, libraries, etc.
- Wide-ranging wireless device support: A regular sticking point with Linux distributions has been support for wireless interfaces. We have built Kali Linux to support as many wireless devices as we possibly can, allowing it to run properly on a wide variety of hardware and making it compatible with numerous USB and other wireless devices.
- Custom kernel, patched for injection: As penetration testers, the development team often needs to do wireless assessments, so our kernel has the latest injection patches included.
- Developed in a secure environment: The Kali Linux team is made up of a small group of individuals who are the only ones trusted to commit packages and interact with the repositories, all of which is done using multiple secure protocols.
- GPG signed packages and repositories: Every package in Kali Linux is signed by each individual developer who built and committed it, and the repositories subsequently sign the packages as well.
- Multi-language support: Although penetration tools tend to be written in English, we have ensured that Kali includes true multilingual support, allowing more users to operate in their native language and locate the tools they need for the job.
- Completely customizable: We thoroughly understand that not everyone will agree with our design decisions, so we have made it as easy as possible for our more adventurous users to customize Kali Linux to their liking, all the way down to the kernel.
- ARMEL and ARMHF support: Since ARM-based single-board systems like the Raspberry Pi and BeagleBone Black, among others, are becoming more and more prevalent and inexpensive, we knew that Kali’s ARM support would need to be as robust as we could manage, with fully working installations for both ARMEL and ARMHF systems. Kali Linux is available on a wide range of ARM devices and has ARM repositories integrated with the mainline distribution so tools for ARM are updated in conjunction with the rest of the distribution.
- For more features of Kali Linux, please see the following page: Kali Linux Overview.
Kali Linux is specifically tailored to the needs of penetration testing professionals, and therefore all documentation on this site assumes prior knowledge of, and familiarity with, the Linux operating system in general. Please see Should I Use Kali Linux? for more details on what makes Kali unique.
Updated on: 2023-Mar-06
Author: g0tmi1k
The 22 most basic commands of Kali Linux
This is a beginner’s guide to using the Kali interface. We will discuss some of the simplest yet very important commands that we recommend beginners to get comfortable with early on. We will show the syntax to each of these commands and demonstrate how they work.With the knowledge of these commands at your disposal, you’ll begin to learn Kali in no time.
We’ve divided these basic commands into five different categories.
- General
- Manipulation
- Reading commands
- Editing commands
- Permission commands
Category 1: General
Let’s begin with the general commands first.
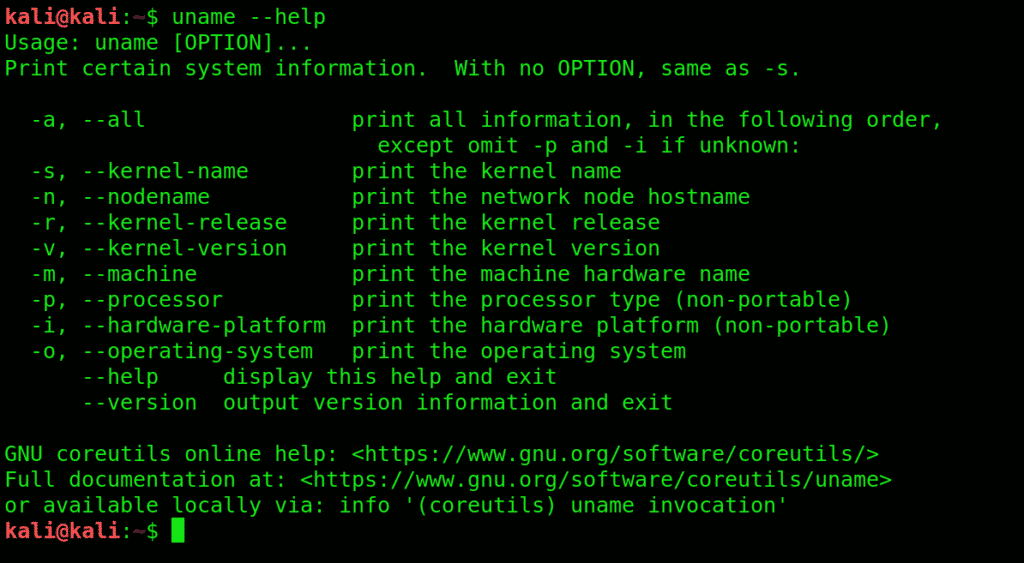
1. uname: Get detailed info on your system specifications with this command. Great place to start familiarizing yourself with Kali User Interface.
2. pwd: This command prints the name of the working directory
A convenient way of showing the directory you’re working in. Especially useful for novices since Kali Linux has a command shell where it’s easy to get lost when you’re in the middle of something complicated.
3. ls: This command Displays what each file contains and the directories they’re stored in. An easy way to view all the contents (files) contained in a directory
The -l flag details each category, other than that, you can use -an attribute.
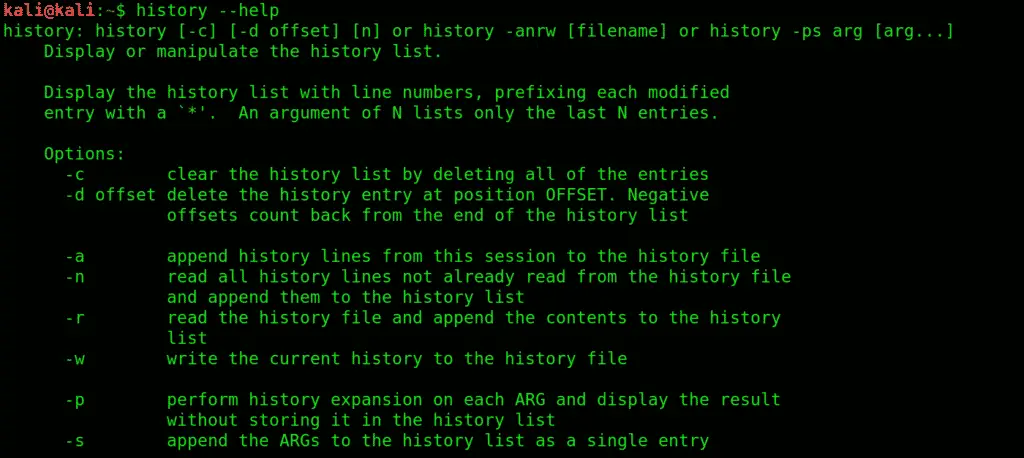
4. history: Get to know all the previously used commands and attributes with history command. It lists all the previous commands you entered (stored in bash shell).
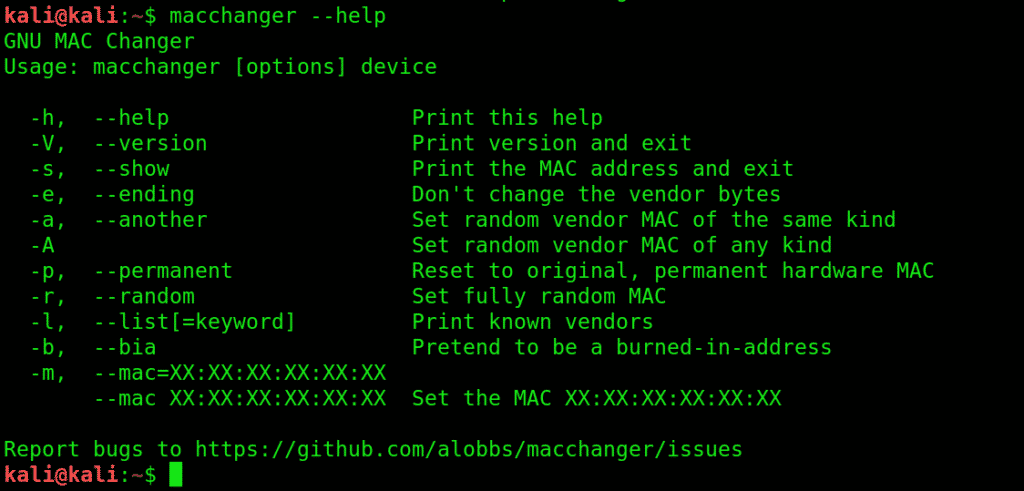
5. macchanger:macchanger changes your mac address, essentially changing your identity.
It helps with protecting your anonymity on the internet, making your IP untraceable.
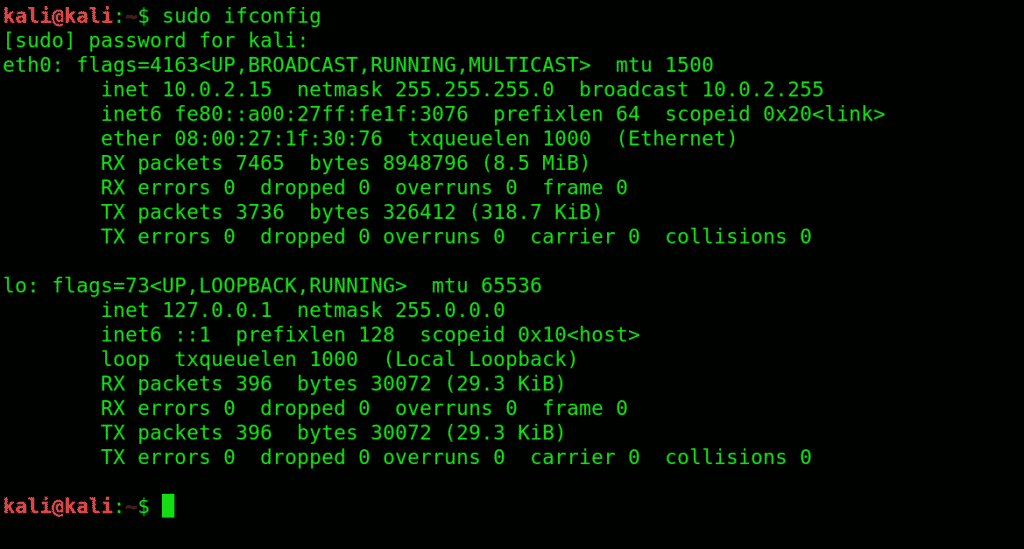
6. ifconfig :ifconfig interface configuration.
Lets you view current network interface settings and configure them.
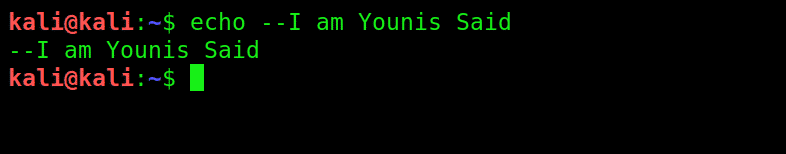
7. echo: It’s like the basic print function you learned in GW basic. Prints any text to where you direct it to.
echo > [file name] prints the copied text in a new file.
echo >> [file name] prints the copied text to an existing file.
Using echo without a ‘>’ will automatically create a new file for the text.
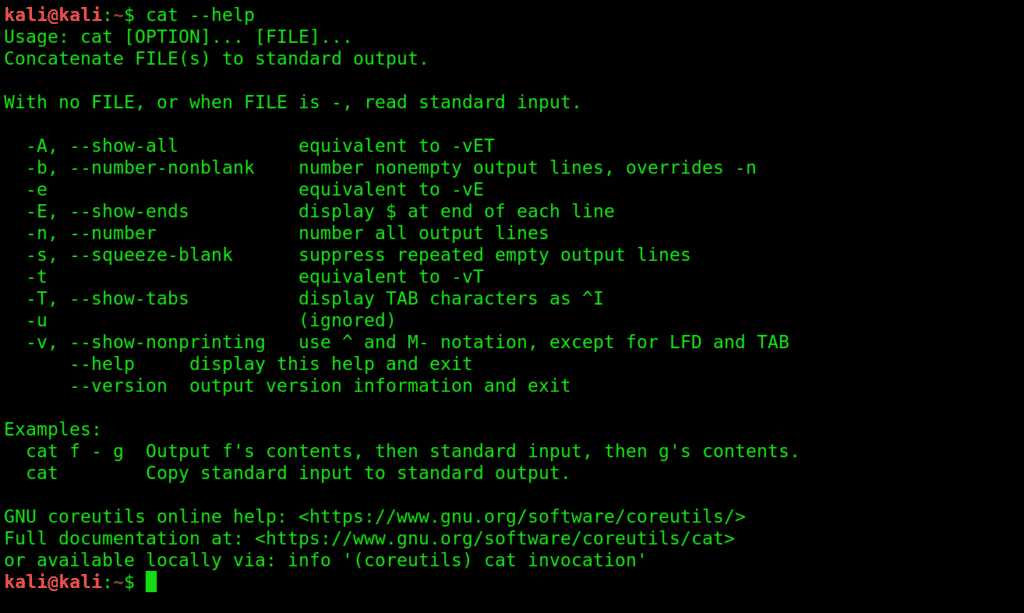
8. cat: Lets your read files and link them together, exchange their contents, etc.
9. Clear: Pretty self-explanatory, clears the terminal screen, and lets you fill it anew.
Category 2: Manipulation commands:
Manipulation commands let you make modifications to files and their content.s
10. mkdir:Creates a new directory.
To create a directory under Desktop called folder1, open a terminal and type this:
11. cd:changes the directory you’re working in. Very commonly used, and a very convenient way to shift directories.
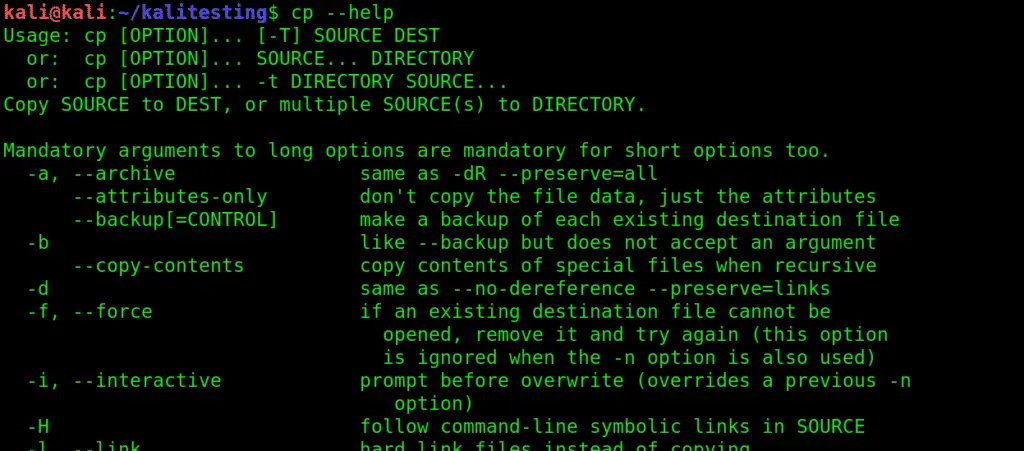
12. cp:Serves the basic copy-text/something purpose. Use this to copy one or more files to a location of your choice. You can pretty much move entire directories with this command.
13. mv:This command moves files between directories.
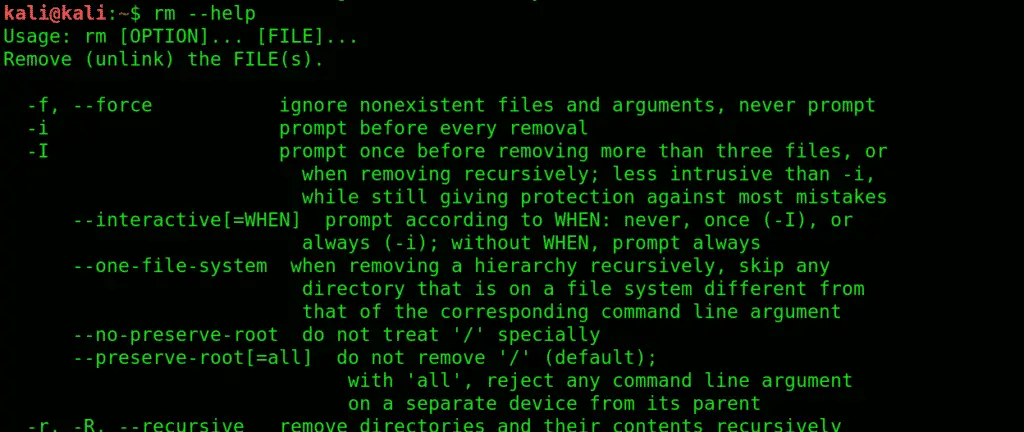
14. rm:Very basic yet essential command, rm removes highlighted texts.
PART THREE: Reading Commands
You get access to files with the following commands.
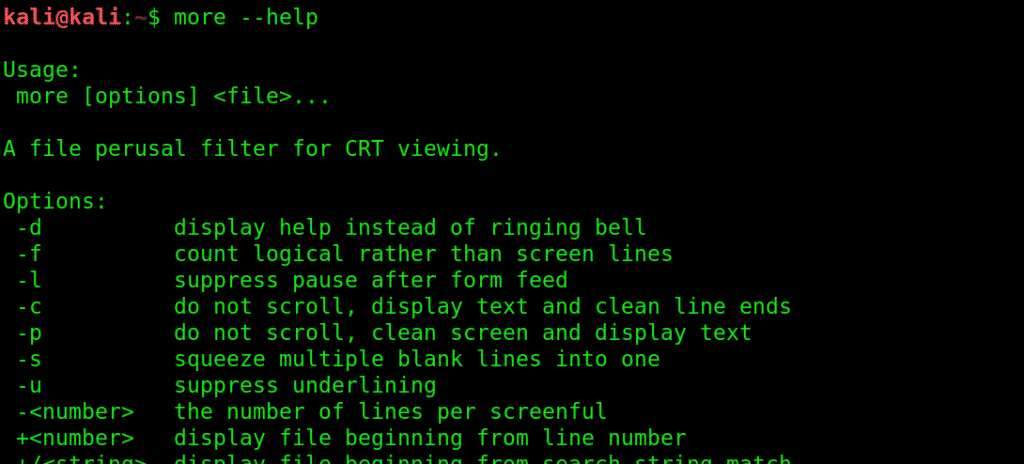
15. more:more gives you bird’s eye view of the contents of a file.
Use more to view contents in a file in a convenient manner, one page at a time instead of making you scroll down the whole thing.
16. less:does everything that more does, just saves you some RAM while it’s at it. Shows you what’s going on with a certain file, except it doesn’t completely load it.
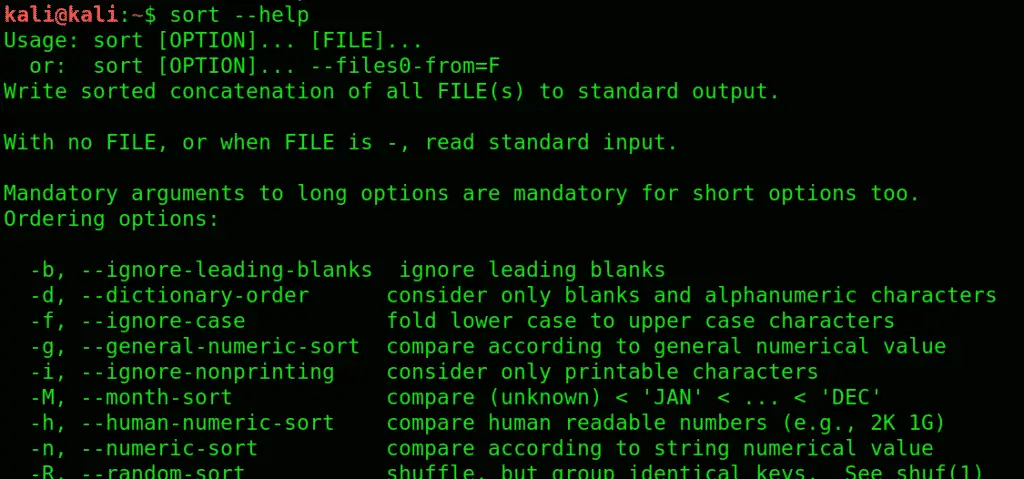
17. sort:see information sorted, to see contents in a certain orderly arrangement. Use -r switch, to sort the contents in reverse order.
PART FOUR: Editing Commands
Edit your text files with either one of the following text editors:
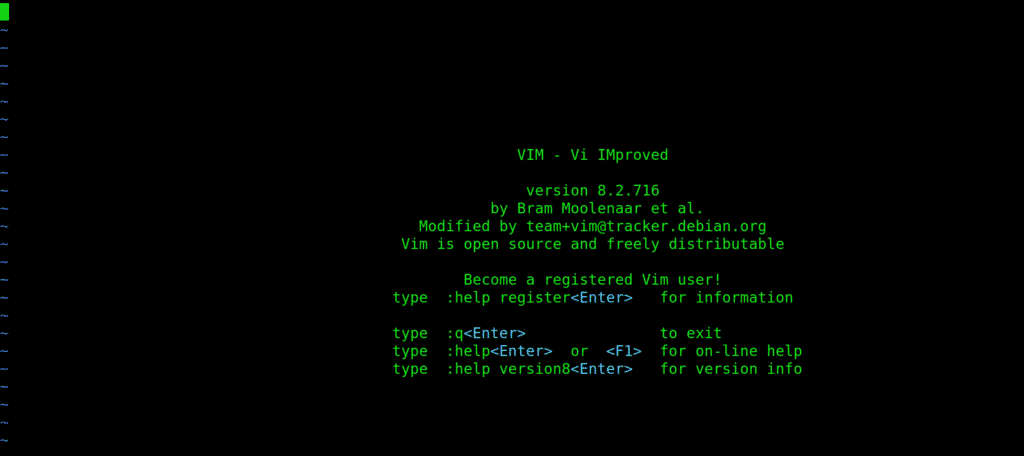
18. vi: Short for the visual editor
This is a text editor you type filenames into. Type your text like vi(filename). This editor has two modes: command and insert. You are in command mode by default. To enter the insert mode, type i then type Esc to exit. Exit vi by typing ‘:wq’
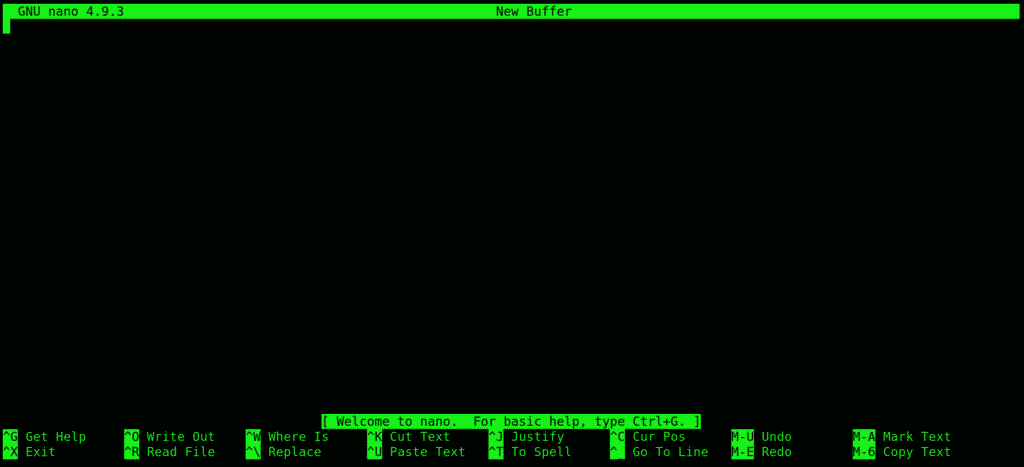
19. nano: Another text editor, used as an alternative to the visual editor.
20. leafpad: A basic and convenient GTK+ text editor, especially useful for beginners. Summon this editor bt typing leafpad /etc/passwd
PART FIVE: Permission Commands
Before we list the permission commands, let’s discuss the three major types of access permissions:
User: User access to a file is given to the user who created it.
Group: All the users that have reading privileges to a file
Other: means customized privileges.
21. chmod: short for change mod. Restricts user access to a file as per your instructions. Use the chmod command to change the modes of access as you wish.
You can use certain flags that serve as permissions to instruct kali to give what privileges to which user.
r= lets a user read the file.
w =enables a user to edit a file (write or delete).
x = Grants permission to execute the file or search a directory.
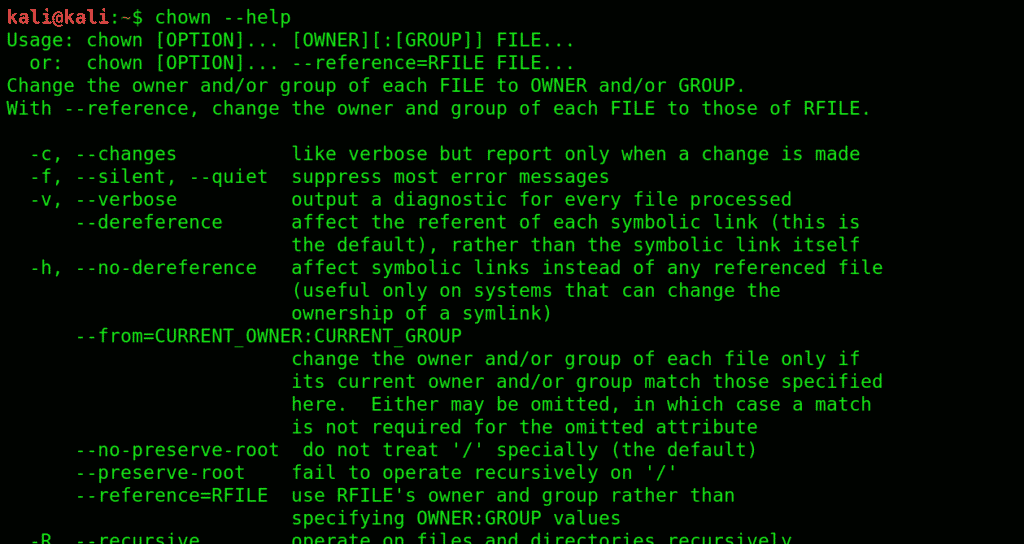
22. chown: Short for change user, similar to chmod.
Wrapping things up:
We have listed and explained some of the most basic commands that are at the roots of most functions in Kali Linux. Kali Linux can be very intimidating to newcomers, and getting to know these basics can save you a lot of energy you could otherwise spend doing all sorts of cool stuff with Kali. We recommend novices to get a good grip on these fundamentals, as learning Kali Linux can be a bit of a learning curve.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.