- What is the Significance of the “wheel” Group in Ubuntu?
- Significance of the “wheel” Group in Ubuntu
- How to Add a User to the “wheel” group in Ubuntu?
- Optional: Create “wheel” Group
- How to Remove a User from the “wheel” Group?
- Conclusion
- How To Add User to Sudoers & Add User to Sudo Group on CentOS 7
- Add User to Sudoers on CentOS
- Step 1: Login as Administrator
- Step 2: Create a New Sudo User
- How to Add Users to Sudo Group
- Step 1: Verify the Wheel Group is Enabled
- Step 2: Add User to Group
- Step: 3 Switch to the Sudo User
- Alternative: Add User to Sudoers Configuration File
- Step 1: Open the Sudoers File in an Editor
- Step 2: Add the New User to file
- Step 3: Test Sudo Privileges for the User Account
- Configuring sudo and adding users to Wheel group
What is the Significance of the “wheel” Group in Ubuntu?
In Ubuntu, the “wheel” group is a special group that has significant security implications. It restricts access to the root user account and provides limited root privileges to certain trusted users. When a user is added to the “wheel” group, they are granted the ability to use the “su” (switch user) command to switch to the root user account. It allows the user to execute administrative tasks that need root authority, such as installing software, changing system files, and managing system services.
This guide will illustrate the significance of the “wheel” group along with practical implementation in Ubuntu.
Significance of the “wheel” Group in Ubuntu
The “su” command is only available to members of the wheel group. This means that even if a user knows the root password, they cannot switch to the root user account unless they are a member of the wheel group.
- Extra Layer of Security: It provides an extra layer of security for the root user account.
- Restrict Access: It restricts access to the root user account, which reduces the risk of accidental or malicious changes to the system.
- Delegate Certain Administrative Tasks: It also allows system administrators to delegate certain administrative tasks to trusted users without giving them full root access.
- Maintain the Stability of the System: It provides limited root privileges to trusted users.
How to Add a User to the “wheel” group in Ubuntu?
By default, the first user created during installation is added to the “sudo” group. It permits the performance of administrative operations. To add a user to the “wheel” group in Ubuntu, you can follow these steps:
Step 1: Check the “wheel” Group with Existing Users
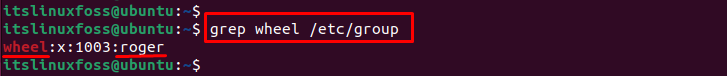
To check if the “wheel” group is already present on the system, run the “grep” command by specifying the directory such as “/etc/group”:
The output shows that the “wheel” group exists and has one user assigned to it named as “roger“
Optional: Create “wheel” Group
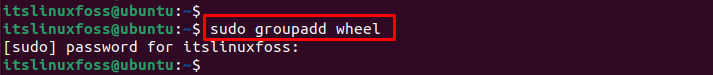
If the “wheel” group does not exist, create it using the “groupadd” command by specifying the “wheel” group as below:
The output shows that the “wheel” group has been created.
Step 2: Add the User to the “wheel” Group
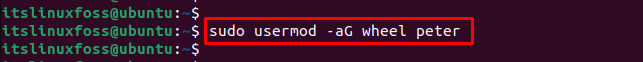
Once the “wheel” group is created, add the user to it by using the “usermod” command with the “aG” option. In our case, specify the username as “peter” to add to the “wheel” group:
$ sudo usermod -aG wheel peter
The output shows that “peter” has been added to the “wheel” group.
Step 3: Verify Added User to the “wheel” Group
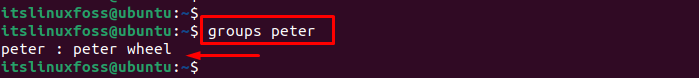
To verify the added user “peter” is part of the “wheel” group, run the following command:
The output confirms that the user “peter” is now a member of the “wheel” group.
How to Remove a User from the “wheel” Group?
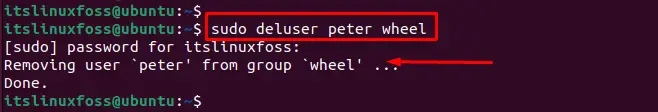
To remove an existing user from the wheel group, use the “deluser” command by specifying the group and user names. In our case, remove the “peter” from the “wheel” group:
The output shows that “peter” has been removed from the “wheel” group. To explore more methods to delete a user from a group, follow our link.
Conclusion
In Ubuntu, the “wheel” is a user group that provides administrative access to certain users on a system. Members of the “wheel” group can perform tasks, such as installing packages, updating/modifying system settings, and managing groups and users. This article has explained the significance of the “wheel” group along with adding a user to the “wheel” group in Ubuntu.
How To Add User to Sudoers & Add User to Sudo Group on CentOS 7
The sudo command stands for “Super User DO” and temporarily elevates the privileges of a regular user for administrative tasks. The sudo command in CentOS provides a workaround by allowing a user to elevate their privileges for a single task temporarily.
This guide will walk you through the steps to add a user to sudoers in CentOS.
Note: Linux Sudo Command tutorials also available for Debian and Ubuntu.
Add User to Sudoers on CentOS
Step 1: Login as Administrator
If you’re working on a local machine, log in to the system with administrator credentials.
If you’re connecting to a remote machine (over a network), open a terminal window and enter the command:
ssh root@server_ip_addressThe server_ip_address is the network IP address of the server you’re logging into. Enter your credentials when prompted.
Step 2: Create a New Sudo User
To add a new sudo user, open the terminal window and enter the command:
Use the actual username for your new user in place of UserName.
Next, create a password for the new user by entering the following in your terminal window:
The system should display a prompt in which you can set and confirm a password for your new user account. If successful, the system should respond with “all authentication tokens updated successfully.”
Note: A strong secure password has more characters and a few special characters (such as numbers, symbols, or capitals). To master managing passwords with passwd commands, refer to our article How To Use The Passwd Command.
How to Add Users to Sudo Group
By default, CentOS 7 has a user group called the “wheel” group. Members of the wheel group are automatically granted sudo privileges. Adding a user to this group is a quick and easy way to grant sudo privileges to a user.
Step 1: Verify the Wheel Group is Enabled
Your CentOS 7 installation may or may not have the wheel group enabled.
Open the configuration file by entering the command:
Scroll through the configuration file until you see the following entry:
## Allows people in group wheel to run all commands # %wheel ALL=(ALL) ALLIf the second line begins with the # sign, it has been disabled and marked as a comment. Just delete the # sign at the beginning of the second line so it looks like the following:
Then save the file and exit the editor.
Note: If this line didn’t start with a # sign, you don’t need to make any changes. The wheel group is already enabled, and you can close the editor.
Step 2: Add User to Group
To add a user to the wheel group, use the command:
usermod –aG wheel UserNameAs usual, replace UserName with the name of the user receiving sudo privileges.
Step: 3 Switch to the Sudo User
Switch to the new (or newly-elevated) user account with the su (substitute user) command:
Enter the password if prompted. The terminal prompt should change to include the UserName.
Enter the following command to list the contents of the /root directory:
The terminal should request the password for UserName. Enter it, and you should see a display of the list of directories. Since listing the contents of /root requires sudo privileges, this works as a quick way to prove that UserName can use the sudo command.
Alternative: Add User to Sudoers Configuration File
If there’s a problem with the wheel group, or administrative policy prevents you from creating or modifying groups, you can add a user directly to the sudoers configuration file to grant sudo privileges.
Step 1: Open the Sudoers File in an Editor
In the terminal, run the following command:
This will open the /etc/sudoers file in a text editor.
Step 2: Add the New User to file
Scroll down to find the following section:
## Allow root to run any commands anywhere root ALL=(ALL) ALLRight after this entry, add the following text:
Replace UserName with the username you created in Step 2. This section should look like the following:
## Allow root to run any commands anywhere root ALL=(ALL) ALL UserName ALL=(ALL) ALLStep 3: Test Sudo Privileges for the User Account
Switch user accounts with the su (substitute user) command:
Enter the password for the account, if prompted. The terminal prompt should change to include UserName.
List the contents of the /root directory:
Enter the password for this user when prompted. The terminal should display a list of all the directories in the /root directory.
This guide showed you how to add a user to sudoers in CentOS or modify the privileges of an existing sudo user.
The Linux sudo command is critical for running advanced and administrative tasks on a Linux system. While this could be done using a root user (or administrator account) using the su command, system administrators advise against operating permanently in a root account. Not only can it be a security risk, but it can also allow changes to a Linux system that can break functionality.
Configuring sudo and adding users to Wheel group
If a server needs to be administered by a number of people it is normally not a good idea for them all to use the root account. This is because it becomes difficult to determine exactly who did what, when and where if everyone logs in with the same credentials. The sudo utility was designed to overcome this difficulty.
With sudo (which stands for “superuser do”), you can delegate a limited set of administrative responsibilities to other users, who are strictly limited to the commands you allow them. sudo creates a thorough audit trail, so everything users do gets logged; if users somehow manage to do something they shouldn’t have, you’ll be able to detect it and apply the needed fixes. You can even configure sudo centrally, so its permissions apply to several hosts.
The privileged command you want to run must first begin with the word sudo followed by the command’s regular syntax. When running the command with the sudo prefix, you will be prompted for your regular password before it is executed. You may run other privileged commands using sudo within a five-minute period without being re-prompted for a password. All commands run as sudo are logged in the log file /var/log/messages.
The sudo configuration file is /etc/sudoers . We should never edit this file manually. Instead, use the visudo command: # visudo
This protects from conflicts (when two admins edit this file at the same time) and guarantees that the right syntax is used (the permission bits are correct). The program uses Vi text editor.
All Access to Specific Users
You can grant users bob and bunny full access to all privileged commands, with this sudoers entry.
user1, user2 ALL=(ALL) ALL
This is generally not a good idea because this allows user1 and user2 to use the su command to grant themselves permanent root privileges thereby bypassing the command logging features of sudo.
Access To Specific Users To Specific Files
This entry allows user1 and all the members of the group operator to gain access to all the program files in the /sbin and /usr/sbin directories, plus the privilege of running the command /usr/apps/check.pl.
user1, %operator ALL= /sbin/, /usr/sbin, /usr/apps/check.pl
Access to Specific Files as Another User
user1 ALL=(accounts) /bin/kill, /usr/bin/kill, /usr/bin/pkill
Access Without Needing Passwords
This example allows all users in the group operator to execute all the commands in the /sbin directory without the need for entering a password.
%operator ALL= NOPASSWD: /sbin/
Adding users to the wheel group
The wheel group is a legacy from UNIX. When a server had to be maintained at a higher level than the day-to-day system administrator, root rights were often required. The ‘wheel’ group was used to create a pool of user accounts that were allowed to get that level of access to the server. If you weren’t in the ‘wheel’ group, you were denied access to root.
Edit the configuration file (/etc/sudoers) with visudo and change these lines:
# Uncomment to allow people in group wheel to run all commands
# %wheel ALL=(ALL) ALL
# Uncomment to allow people in group wheel to run all commands
%wheel ALL=(ALL) ALL
This will allow anyone in the wheel group to execute commands using sudo (rather than having to add each person one by one).
Now finally use the following command to add any user (e.g- user1) to Wheel group
# usermod -G10 user1