- Users and groups
- Overview
- Permissions and ownership
- Users and groups administrations from the command line in Linux
- Creating groups under Linux:
- Creating users under Linux:
- Command adduser vs useradd
- Creating or changing a user password under Linux:
- Modifying users under Linux:
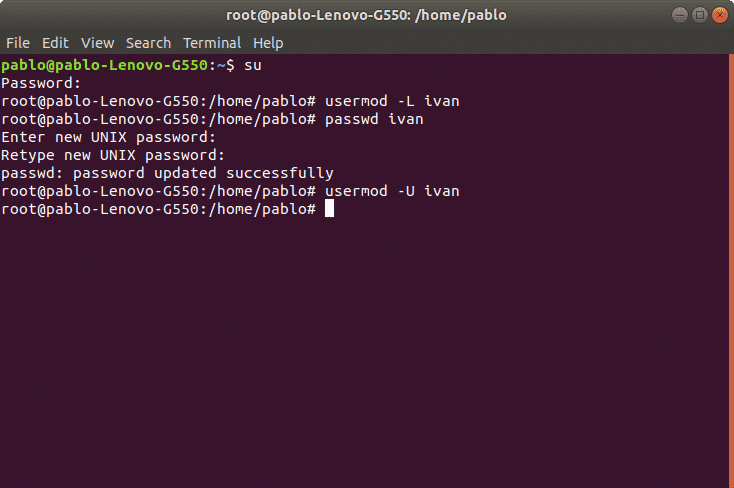
- Lock/Unlock user account
- Deleting users under Linux:
- Modifying groups under Linux:
- Deleting groups under Linux:
- Graphic user and groups management under Ubuntu Linux (Gnome)
- About the author
- David Adams
Users and groups
Users and groups are used on GNU/Linux for access control—that is, to control access to the system’s files, directories, and peripherals. Linux offers relatively simple/coarse access control mechanisms by default. For more advanced options, see ACL, Capabilities and PAM#Configuration How-Tos.
Overview
A user is anyone who uses a computer. In this case, we are describing the names which represent those users. It may be Mary or Bill, and they may use the names Dragonlady or Pirate in place of their real name. All that matters is that the computer has a name for each account it creates, and it is this name by which a person gains access to use the computer. Some system services also run using restricted or privileged user accounts.
Managing users is done for the purpose of security by limiting access in certain specific ways. The superuser (root) has complete access to the operating system and its configuration; it is intended for administrative use only. Unprivileged users can use several programs for controlled privilege elevation.
Any individual may have more than one account as long as they use a different name for each account they create. Further, there are some reserved names which may not be used such as «root».
Users may be grouped together into a «group», and users may be added to an existing group to utilize the privileged access it grants.
Note: The beginner should use these tools carefully and stay away from having anything to do with any other existing user account, other than their own.
Permissions and ownership
The UNIX operating system crystallizes a couple of unifying ideas and concepts that shaped its design, user interface, culture and evolution. One of the most important of these is probably the mantra: «everything is a file,» widely regarded as one of the defining points of UNIX. This key design principle consists of providing a unified paradigm for accessing a wide range of input/output resources: documents, directories, hard-drives, CD-ROMs, modems, keyboards, printers, monitors, terminals and even some inter-process and network communications. The trick is to provide a common abstraction for all of these resources, each of which the UNIX fathers called a «file.» Since every «file» is exposed through the same API, you can use the same set of basic commands to read/write to a disk, keyboard, document or network device.
A fundamental and very powerful, consistent abstraction provided in UNIX and compatible operating systems is the file abstraction. Many OS services and device interfaces are implemented to provide a file or file system metaphor to applications. This enables new uses for, and greatly increases the power of, existing applications — simple tools designed with specific uses in mind can, with UNIX file abstractions, be used in novel ways. A simple tool, such as cat, designed to read one or more files and output the contents to standard output, can be used to read from I/O devices through special device files, typically found under the /dev directory. On many systems, audio recording and playback can be done simply with the commands, » cat /dev/audio > myfile » and » cat myfile > /dev/audio ,» respectively.
Every file on a GNU/Linux system is owned by a user and a group. In addition, there are three types of access permissions: read, write, and execute. Different access permissions can be applied to a file’s owning user, owning group, and others (those without ownership). One can determine a file’s owners and permissions by viewing the long listing format of the ls command:
total 13740 drwxr-xr-x 2 root root 4096 Jan 12 00:33 grub -rw-r--r-- 1 root root 8570335 Jan 12 00:33 initramfs-linux-fallback.img -rw-r--r-- 1 root root 1821573 Jan 12 00:31 initramfs-linux.img -rw-r--r-- 1 root root 1457315 Jan 8 08:19 System.map26 -rw-r--r-- 1 root root 2209920 Jan 8 08:19 vmlinuz-linux
The first column displays the file’s permissions (for example, the file initramfs-linux.img has permissions -rw-r—r— ). The third and fourth columns display the file’s owning user and group, respectively. In this example, all files are owned by the root user and the root group.
total 16 drwxrwx--- 1 root vboxsf 16384 Jan 29 11:02 sf_Shared
In this example, the sf_Shared directory is owned by the root user and the vboxsf group. It is also possible to determine a file’s owners and permissions using the stat command:
Users and groups administrations from the command line in Linux
Linux offers us a lot of useful tools to keep our environment’s safety and order, assigning or denying permissions to users and groups is a primary tool on any linux system. For security reasons only root users and users within the sudo group are able to manage users and groups.Through the command line, it is easy to create and modify or remove users, to restrict or release permissions, while allowing us to log users activity.
To manage permissions lets start by becoming the root user. Enter the command “su” to become root and press “Enter”, type the password when requested. If you don’t have root access we must use the sudo command before running a privileged command. For information on sudo you can read Managing sudo privileges.
Note: remember Linux is a case sensitive OS.
After authenticating we can manage users and groups.
Creating groups under Linux:
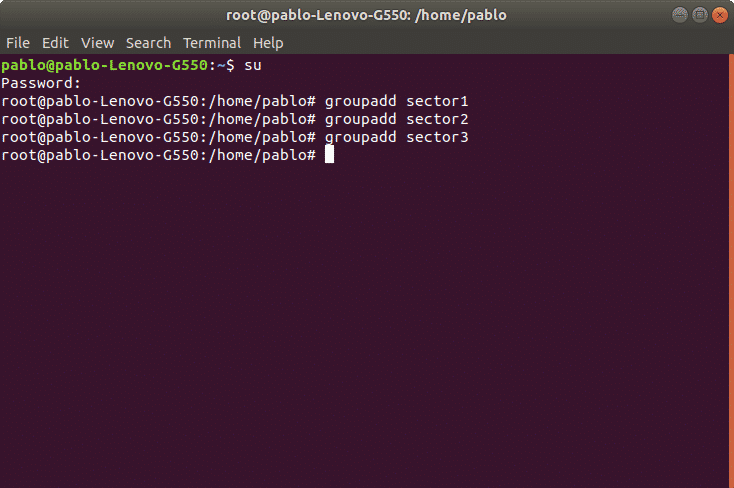
To create groups we’ll use first the command “groupadd” followed by the group’s name. The syntax is: “groupadd ”.
In the following picture is an example where I create three groups: sector1, sector2 and sector3. To do it on the command line type:
Once the groups are created we can create users to be assigned to the groups.
Creating users under Linux:
Using the command “useradd” we can add a user to our system. The proper syntax is “useradd [options] ”
Among the most used options we have:
-g Main user group (gid)
-d User Home directory, by default located at /home/
-m Create Home directory in case it doesn’t exist.
-s Assign a specific shell to the user, by default it is /bin/bash.
As an example we will create the user nicolas and will assign him the group sector1, also we’ll define the user’s home and shell.
Now we’ll do the same with user martin to be added to group sector2, and a third user ivan for sector3. We’ll use the same syntax:
Command adduser vs useradd
While the command useradd runs a system binary file the command adduser is a perl script to interact with useradd. With the adduser command, the advantage is the home is created automatically. If using the command adduser we need to specify the -m option.
Creating or changing a user password under Linux:
After adding a user with the command “useradd” we need to set a password for the user using the command “passwd”. Remember Linux is case sensitive.
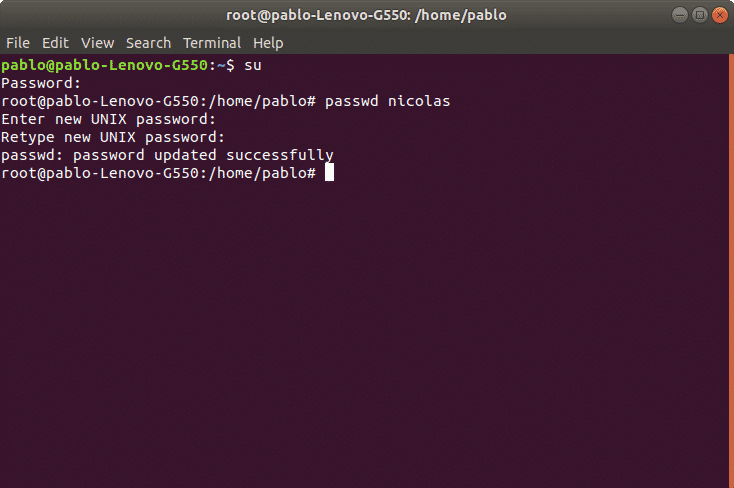
In the following example we’ll create a password for the user nicolas using the following syntax:
Then it will request for password and confirmation, after confirmation the password will be established. We can know the process succeeded when the system returns “password updated successfully” like in the image:
passwd nicolas
Enter new UNIX password: ( ingresar contraseña )
Retype new UNIX password: ( repetir contraseña )
passwd: password updated successfully
Modifying users under Linux:
We can edit the user’s username, his home directory, his shell and groups to which he belongs among more options. For this we’ll use the command “usermod”.
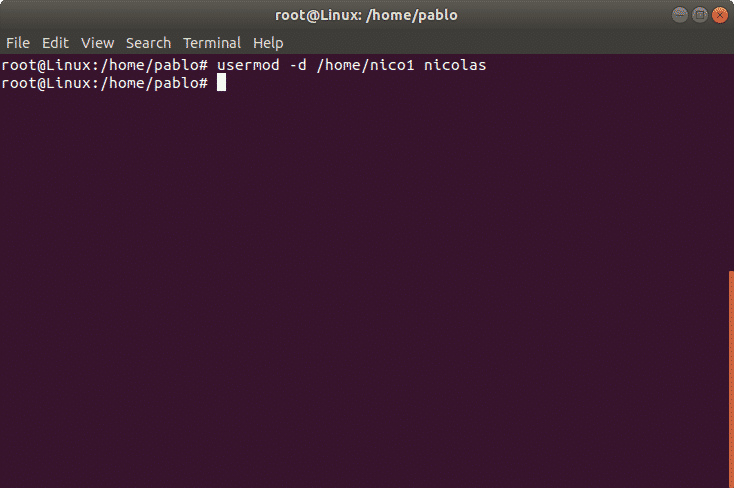
As an example we’ll modify the user nicholas’ home directory which we previously defined as /home/nicolas and we’ll replace it for /home/nico1.
The previous command updated the user’s home.
Lock/Unlock user account
We can also lock a user account. In the following example we’ll lock user ivan account. The parameter -L (lock) will block the user account. The syntax is:
To enable a locked user we can use the -U (Unlock) parameter. In the following example we will unlock the user ivan:
Deleting users under Linux:
We can remove a user with the command userdel followed by the username. We can also combine parameters, among most used options we have:
-f remove user files.
-r remove user home and mail tail.
In the following example we’ll delete the user account “ivan”
Note: The command “userdel” won’t remove the user if is running process.
Modifying groups under Linux:
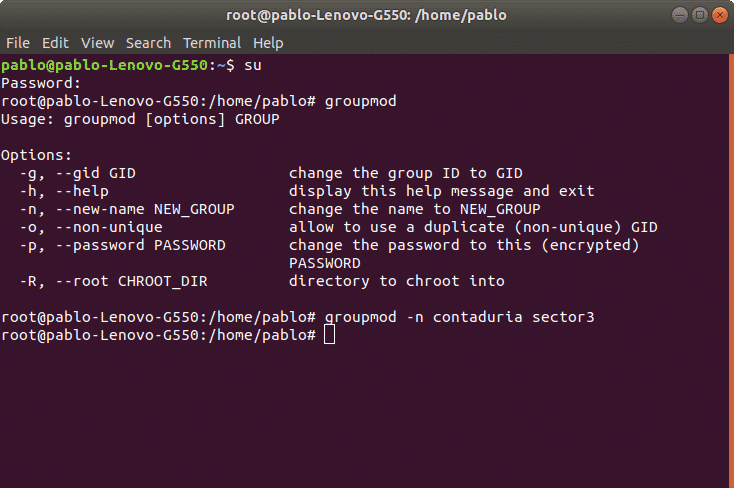
In order to modify groups we’ll use the command “groupmod”. This command allows to modify a group name or user gid. The syntax is:
In the following example we’ll modify the group name for “sector3” to “contaduria”
Deleting groups under Linux:
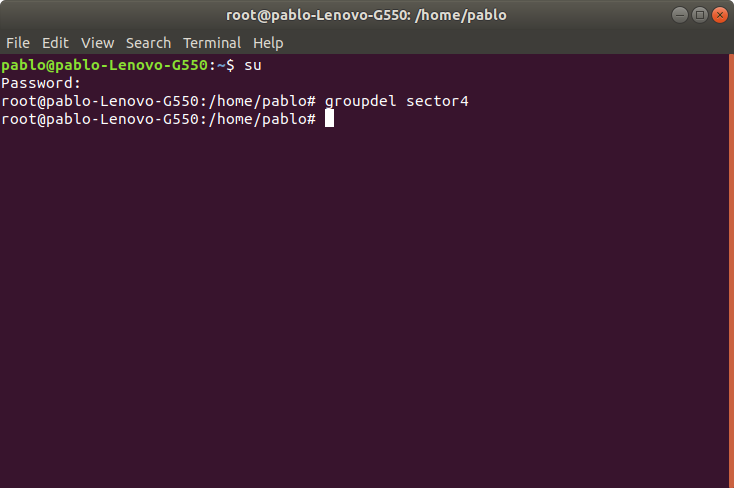
We can remove a group using the command “groupdel” followed by the group name. For example, to remove the group sector4 we’ll use the following syntax:
In this case it would be just:
Note: If another user is a member of the group we try to remove, the command won’t remove the group.
Graphic user and groups management under Ubuntu Linux (Gnome)
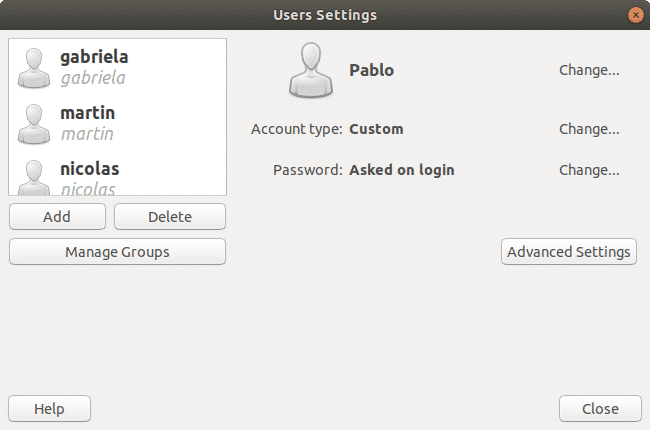
Ubuntu offers a graphical management for users and groups. The interface is user friendly, intuitive and easy to use.
If we haven’t installed this interface on the terminal run:
When asked for confirmation press “Y” and “enter”
The following NEW packages will be installed
Once finished we can run the tool from the command line as “users-admin”
Thank you for reading this article. Now you can easily manage users and groups on linux.
About the author
David Adams
David Adams is a System Admin and writer that is focused on open source technologies, security software, and computer systems.