Users and groups
Users and groups are used on GNU/Linux for access control—that is, to control access to the system’s files, directories, and peripherals. Linux offers relatively simple/coarse access control mechanisms by default. For more advanced options, see ACL, Capabilities and PAM#Configuration How-Tos.
Overview
A user is anyone who uses a computer. In this case, we are describing the names which represent those users. It may be Mary or Bill, and they may use the names Dragonlady or Pirate in place of their real name. All that matters is that the computer has a name for each account it creates, and it is this name by which a person gains access to use the computer. Some system services also run using restricted or privileged user accounts.
Managing users is done for the purpose of security by limiting access in certain specific ways. The superuser (root) has complete access to the operating system and its configuration; it is intended for administrative use only. Unprivileged users can use several programs for controlled privilege elevation.
Any individual may have more than one account as long as they use a different name for each account they create. Further, there are some reserved names which may not be used such as «root».
Users may be grouped together into a «group», and users may be added to an existing group to utilize the privileged access it grants.
Note: The beginner should use these tools carefully and stay away from having anything to do with any other existing user account, other than their own.
Permissions and ownership
The UNIX operating system crystallizes a couple of unifying ideas and concepts that shaped its design, user interface, culture and evolution. One of the most important of these is probably the mantra: «everything is a file,» widely regarded as one of the defining points of UNIX. This key design principle consists of providing a unified paradigm for accessing a wide range of input/output resources: documents, directories, hard-drives, CD-ROMs, modems, keyboards, printers, monitors, terminals and even some inter-process and network communications. The trick is to provide a common abstraction for all of these resources, each of which the UNIX fathers called a «file.» Since every «file» is exposed through the same API, you can use the same set of basic commands to read/write to a disk, keyboard, document or network device.
A fundamental and very powerful, consistent abstraction provided in UNIX and compatible operating systems is the file abstraction. Many OS services and device interfaces are implemented to provide a file or file system metaphor to applications. This enables new uses for, and greatly increases the power of, existing applications — simple tools designed with specific uses in mind can, with UNIX file abstractions, be used in novel ways. A simple tool, such as cat, designed to read one or more files and output the contents to standard output, can be used to read from I/O devices through special device files, typically found under the /dev directory. On many systems, audio recording and playback can be done simply with the commands, » cat /dev/audio > myfile » and » cat myfile > /dev/audio ,» respectively.
Every file on a GNU/Linux system is owned by a user and a group. In addition, there are three types of access permissions: read, write, and execute. Different access permissions can be applied to a file’s owning user, owning group, and others (those without ownership). One can determine a file’s owners and permissions by viewing the long listing format of the ls command:
total 13740 drwxr-xr-x 2 root root 4096 Jan 12 00:33 grub -rw-r--r-- 1 root root 8570335 Jan 12 00:33 initramfs-linux-fallback.img -rw-r--r-- 1 root root 1821573 Jan 12 00:31 initramfs-linux.img -rw-r--r-- 1 root root 1457315 Jan 8 08:19 System.map26 -rw-r--r-- 1 root root 2209920 Jan 8 08:19 vmlinuz-linux
The first column displays the file’s permissions (for example, the file initramfs-linux.img has permissions -rw-r—r— ). The third and fourth columns display the file’s owning user and group, respectively. In this example, all files are owned by the root user and the root group.
total 16 drwxrwx--- 1 root vboxsf 16384 Jan 29 11:02 sf_Shared
In this example, the sf_Shared directory is owned by the root user and the vboxsf group. It is also possible to determine a file’s owners and permissions using the stat command:
How to Add a User on Arch Linux
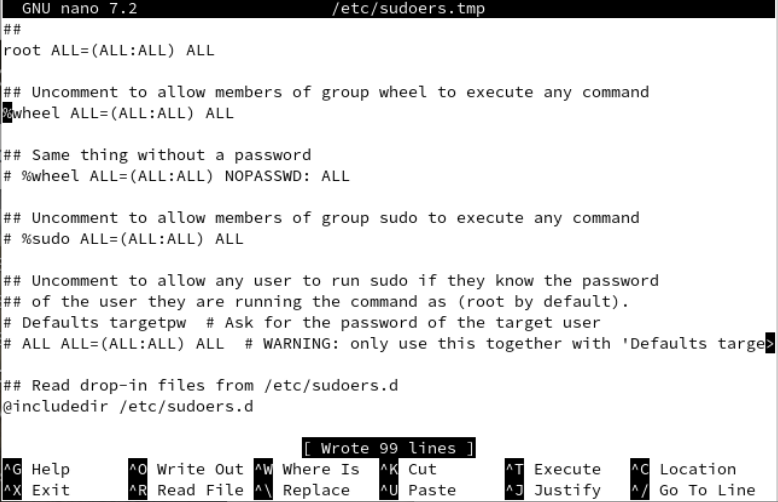
User management is the most needed utility in any operating system because it makes your system secure and provides you an opportunity to assign the right privileges to the right ones. The users can make a lot of changes to your system according to the rights they have. Therefore, it’s very necessary to have a very close look at each activity that is performed by the users. Thus, this guide elaborates on the method to add the new users to the Arch Linux system and how to manage them. Before moving towards the addition of users in the Arch Linux system, we need to make sure that the group is already enabled. To do so, we use the following “visudo” command with “sudo”. This is typically used to make changes to the sudoers file:
The sudouers file is launched in the “nano” editor. You will find the “wheel” group in the following illustration. Uncomment it and save the file to update the changes. Use “Ctrl-x” to exit.
Add a User
Now, we add a new “test” user to the Arch Linux system using the “useradd” instruction with the “sudo” rights. This instruction doesn’t take anything in return which indicates that the user is created.
Now, it’s very necessary to secure an account that is just created. For this, we establish a new user and add a new password. Therefore, we utilize the shell’s “passwd” command along with the user “test” as our input. You are prompted by the terminal to enter a new password. After providing the password twice, it is updated successfully.
passwd: password updated successfully
In case you want to perform the process of user addition to arch Linux along with setting its password at once, you can do so by modifying the useradd instruction. For this, you should use the “-m” and “-p” flags in the instruction. The “-m” flag can be utilized to name a new user while the “-p” option can be used to set the password for the user to be created. For example, we create a “dummy” user with the “dummy123” password via the useradd instruction in the following:
The other thing that you can achieve using the useradd instruction is to set the custom directory for a new user using the “-d” option with the path to the directory. The following instruction shows that we created a “new” user and a “new” password and set its custom directory as “/tmp/new”:
There are a lot of groups which are available in Arch Linux to perform the different functions according to their group types. To add a user to a particular group in Arch Linux, the useradd command comes up with the “-G” option to add a particular user to any group. For example, the following instruction adds a new “blue” user in the wheel, audio, and video group while creating:
There is also a way to add the system users in Arch Linux using the useradd instruction. For this, you need to use the “-r” option with the “-s” flag followed by the path to the “fish” directory, i.e. “/usr/bin/fish”. The “hell” user is created as you can see from the attached command. The output of this instruction generates a warning.
useradd: Warning: missing or non-executable shell ‘/usr/bin/fish’
You can also do it if you wish to confirm the outcome of the aforementioned instruction. For that, try using the following “su’ instruction with the name of a user that you just created. It might show you a warning.
su: warning: cannot change directory to /home/hell: No such file or directory
After that, try the whoami one-word instruction on the shell. You will see that it returns the name of a system user that you just created.
User Modification
While using the arch Linux and creating new users, you should have a piece of knowledge about the user properties and a way to modify them. Consider the scenario where we want to rename the “test” to “test1” user. For this, we use the usermod instruction with the “-l” option followed by the new name and then an old name as shown in the following attached command:
Now, if you want to set the expiry date for a newly created user account, you can also set that using the usermod instruction followed by its “—expiry date” option. The option follows the date and then a username. The “test1” is our new user name in this case.
Now, if you want to add your user to the additional groups, you can do so by using the –append option in the usermod instruction followed by the –groups option with the group names and the name of a user to be added. The wheel and users are 2 groups while the test1 is a user.
To modify the default shell that is used by a user, you can use the –shell option in a usermod instruction. In this instruction, you should provide the path to the shell file like /usr/bin/bash.
Lock/Unlock the User
In case you don’t want anybody to use the particular account, you might lock it. To lock an account, the –lock option can be used in the usermod instruction with the name of a user which is “test1”.
In the same way, if you want to allow a particular user to use its system account, you should unlock the particular account using the “unlock” option in the usermod instruction with the same user name as shown in the attached instruction:
Delete the User
To display the currently available users of your Arch Linux, try using the instruction as follows:
To delete the new and previously made users, the “userdel” instruction can be utilized. This command takes one or more usernames at once.
[ omar @ omar ~ ] $ sudo userdel test1
[ omar @ omar ~ ] $ sudo userdel hell
[ omar @ omar ~ ] $ sudo userdel blue new
[ / c ] c
If you create a user with a related home directory, you can delete it using the –r option.
[ cc lang = «bash» width = «100%» height = «100%» escaped = «true» theme = «blackboard» nowrap = «0» ]
[ omar @ omar ~ ] $ sudo userdel -r dummy
Conclusion
The introductory paragraph explains the importance of user management in all sorts of operating systems. To support the discussion, we tried the different instructions to create the new users, modify, lock or unlock, and delete them. For this, we utilized the useradd, usermod, and userdel instructions with the –m, -p, -G, -r, -s, -l, –append, –shell, –lock, –unlock, and –expiredate options.
About the author
Omar Farooq
Hello Readers, I am Omar and I have been writing technical articles from last decade. You can check out my writing pieces.