- Bluetooth Pentesting Tools (HW/SW)
- Requirements
- Information gathering
- hcitool
- bluetoothctl
- bettercap
- bluelog
- Capturing bluetooth traffic
- btmon
- Wireshark
- Bluetooth Pentesting Software
- BlueMaho
- GATT Tool
- Bluepot
- spooftooph
- Bluetooth Pentesting Hardware
- References
- 7 Most Popular Bluetooth Hacking Software to Hack Mobile Phones
- 1. Super Bluetooth Hack 1.08
- 2. Blue Scanner
- 3. Blue Sniff
- 4. BlueBugger
- 5. BTBrowser
- 6. BTCrawler
- 7. BlueSnarfing
- H A C K R Z
Bluetooth Pentesting Tools (HW/SW)
This article describes various tools for bluetooth penetration testing and aims to provide an overview to choose the right tool for a use case.
Requirements
In order to use hardware pentesting devices a dedicated installation of kali linux is recommended but it is also possible to use hypervisors which are capable of passing USB devices from the host- to the guestsystem e.g. VMWare Workstation or the free hypervisor VirtualBox.
Information gathering
The offical linux bluetooth protocol stack BlueZ is already installed on kali linux but can be installed on other linux maschines with:
apt install -y bluez bluez-utils systemctl start bluetooth.service systemctl status bluetooth.service
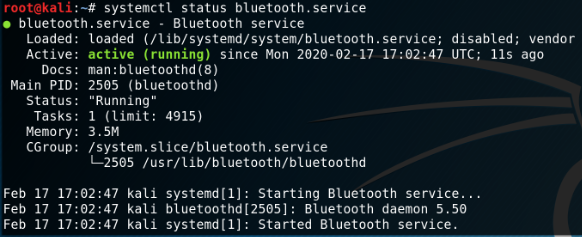
hcitool
To start with penetration testing we need to gather information about our environment, for this purpose scan for available bluetooth devices with the included packages ‘hcitool’ or ‘bluetoothctl’.
First check if your bluetooth device is available:
Scan for BR/EDR Bluetooth devices with hcitool:
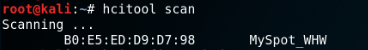
In order to scan for BLE devices use:
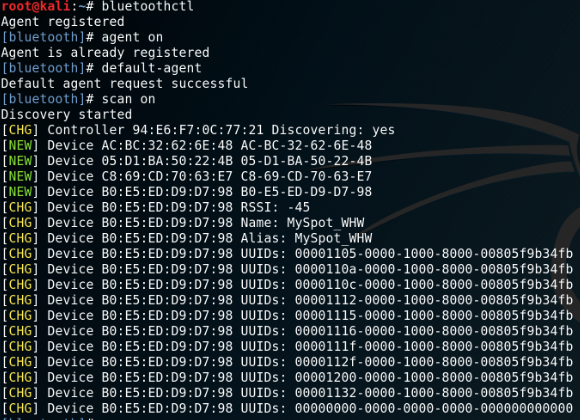
bluetoothctl
Alternatively you can use bluetoothctl which is also included in the bluez-utils package:
bettercap
This Software is described in the Bettercap Documentation.
bluelog
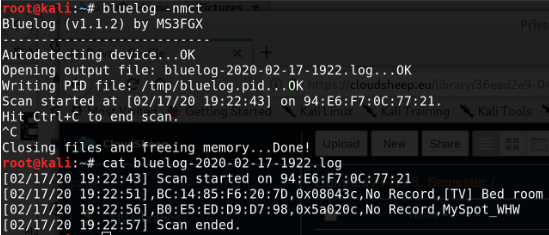
Another great tool for bluetooth device discovery is ‘bluelog’. It is extremly lightweight and can be automated for background usage without user intervention. Bluelog is already preinstalled on kali linux but can be installed with:
To start scanning for bluetooth devices use:
(n=log device names;m=log manufacturer;t=log timestamps of discovery;c=log device class)
Capturing bluetooth traffic
btmon
With the preinstalled package ‘btmon’ it is possible to capture traffic between the HCI and the controller:
btmon --write ~/Documents/bttraffic.snoop
These files can be viewed and analysed with ‘Wireshark’ which is also preinstalled on kali linux.
Wireshark
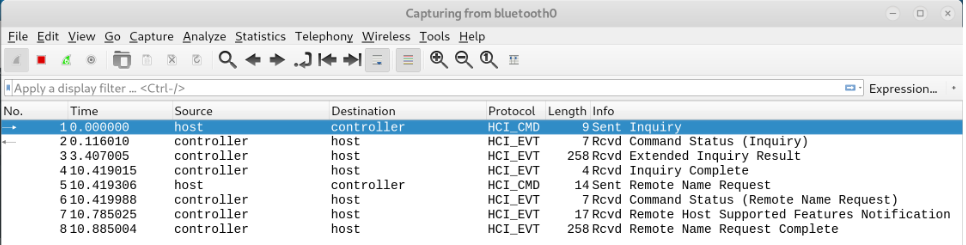
Alternatively you can capture bluetooth traffic directly with Wireshark. Start Wireshark with.
wireshark -w ~/Documents/bttraffic.snoop
. and select your bluetooth interface e.g. bluetooth0 or bluetooth1.
Bluetooth Pentesting Software
In the following chapter we will present some software pentesting tools which are used for ethical bluetooth device hacking.
BlueMaho
BlueMaho is a tool suite for bluetooth device pentesting and provides various exploits. It is written in python and uses wxPython. The feature set includes: scanning, tracking, alerts on new devices or targeted devices, sending files or changing BT values like the BD_ADDR.
Although it is still listed in the kali linux tool list, it has to be manually installed:
apt install autoconf build-essential build-dep git python-wxtools git clone https://github.com/zenware/bluemaho cd bluemaho/config ./build.sh
In order to run the GUI use:
GATT Tool
Before you can start using the GATT Tool you need to know the Bluetooth Address of the victim device. For gathering this information you can use the hcitool, which is described above.
The GATT Tool has a powerful interactive mode. During this mode the devices stay connected and you can use more than one handle sequentially.
sudo gatttool -I -b connect
To get the name of your Bluetooth interfaces use hciconfig, which is described above.
The Interactive mode also allows to list the characteristics of the connected device and control them.
Depending on the Privileges you can Read, Write characteristics of the device.
Read: char-read-hnd Write: char-write-req or char-write-cmd
The Privileges are described in the following graph

An example of an guided exploit can be found at the Mipow Playbulb: Bluetooth Connection Sniffing documentation
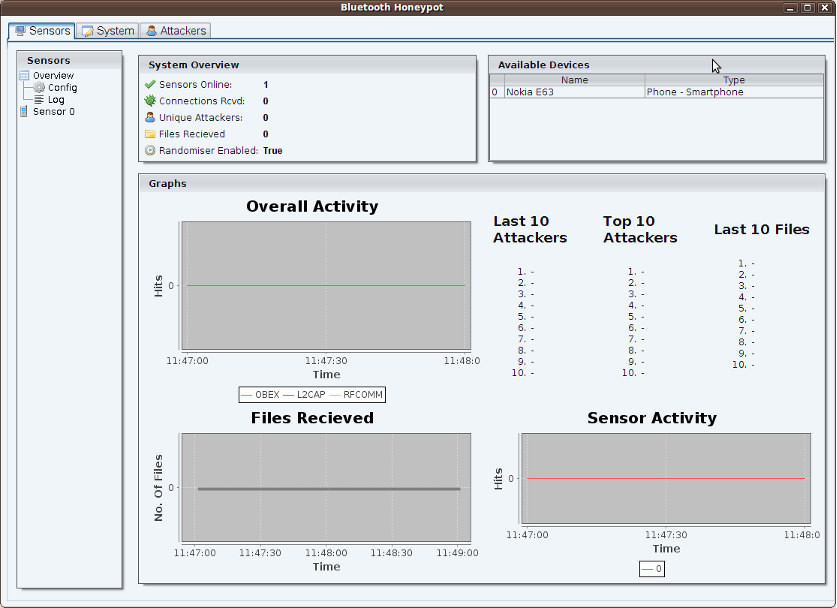
Bluepot
Bluepot is a Bluetooth Honeypot written in Java, it is designed to accept and store any malware sent to it and interact with common Bluetooth attacks. The system also allows monitoring of attacks via a graphical user interface that provides graphs, lists, a dashboard and further detailed analysis from log files.
In order to install bluepot use following commands:
wget https://github.com/andrewmichaelsmith/bluepot/raw/master/bin/bluepot-0.1.tar.gz tar xfz bluepot-0.1.tar.gz java -jar bluepot/BluePot-0.1.jar
spooftooph
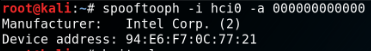
Spooftooph is designed to automate spoofing or cloning Bluetooth device information. The software is able to clone and log bluetooth devices, generate or change new random bluetooth profiles and specify device information for bluetooth interfaces.
E.g.: Spoof your own device address for the interface hci0:
Bluetooth Pentesting Hardware
For hardware pentesting devices like the Ubertooth one please see following documentations:
References
7 Most Popular Bluetooth Hacking Software to Hack Mobile Phones
We all are familiar with the term hacking and the disadvantages faced by anyone when it is being used in illegal ways. Previously, hacking was restricted to computers or computer networks only but as time changed this field has grown up and now mobile phones, especially the multimedia phones are more prone to hacking. There are various hacks and software already present on the web which helps hackers in hacking any multimedia phones. In this post, I have outlined only Bluetooth Hacking Software. These software are very efficient and can hack any Bluetooth-enabled device without any prior knowledge of the user.
So here comes the list of useful Bluetooth hacking software.
1. Super Bluetooth Hack 1.08
This software is used for controlling and reading information from a remote phone via Bluetooth or infrared. Phone list and SMS can be stored in HTML format. In addition to it, it will display information about battery, network, and sim card.
2. Blue Scanner
Blue Scanner searches out for Bluetooth-enabled devices and tries to extract as much information as possible for each newly discovered device in other words one can use this one to spy on others who are close.
3. Blue Sniff
BlueSniff is a simple utility for finding discoverable and hidden Bluetooth-enabled devices. It operates on Linux.
4. BlueBugger
This simply exploits the BlueBug (name of a set of Bluetooth security holes) vulnerability of the Bluetooth-enabled devices. By exploiting these vulnerabilities one can access phone-book, call lists, and other information of that device.
5. BTBrowser
BT Browser is a J2ME application which can browse and explore the technical specification of surrounding Bluetooth-enabled devices. One can browse device information and all supported profiles and services records of each device.
6. BTCrawler
BT Crawler is a scanner for Windows Mobile Based devices. It scans for other devices in range and performs service queries. It implements Bluejacking and BlueSnarfing attacks.
7. BlueSnarfing
Bluesnarfing is a method of hacking into Bluetooth-enabled mobile phones and with this, you can copy its entire information like contact book, etc. With this software you give the complete freedom to hackers, to send a “corruption code” to you which will completely shut-down the phone down and make it unusable for you.
Disclaimer: I have outlined these software for your information and knowledge purpose only. It’s an advice to all the multimedia phone users to keep off your Bluetooth and if any harm will occur then we do not take any responsibility.
Please leave your thoughts on Bluetooth hacking in the comments section below.
H A C K R Z
Bluetooth Technology is great. No doubt. It provides an easy way for a wide range of mobile devices to communicate with each other without the need for cables or wires. However, despite its obvious benefits, it can also be a potential threat for the privacy and security of Bluetooth users (remember Paris Hilton?).
If you are planning to gain a deeper understanding of Bluetooth security, you will need a good set of tools with which to work. By familiarizing yourself with the following tools, you will not only gain a knowledge of the vulnerabilities inherent in Bluetooth-enabled devices, but you will also get a glimpse at how an attacker might exploit them.
This hack highlights the essential tools, mostly for the Linux platform, that can be used to search out and hack Bluetooth-enabled devices.
DISCOVERING BLUETOOTH DEVICES
BlueScanner – BlueScanner searches out for Bluetooth-enabled devices. It will try to extract as much information as possible for each newly discovered device.
BlueSniff – BlueSniff is a GUI-based utility for finding discoverable and hidden Bluetooth-enabled devices.
BTBrowser – Bluetooth Browser is a J2ME application that can browse and explore the technical specification of surrounding Bluetooth-enabled devices. You can browse device information and all supported profiles and service records of each device. BTBrowser works on phones that supports JSR-82 – the Java Bluetooth specification.
BTCrawler – BTCrawler is a scanner for Windows based devices. It scans for other devices in range and performs service query. It implements the BlueJacking and BlueSnarfing attacks.
HACKING BLUETOOTH DEVICES
BlueBugger – BlueBugger exploits the BlueBug vulnerability. BlueBug is the name of a set of Bluetooth security holes found in some Bluetooth-enabled mobile phones. By exploiting those vulnerabilities, one can gain an unauthorized access to the phone-book, calls lists and other private information.
CIHWB – Can I Hack With Bluetooth (CIHWB) is a Bluetooth security auditing framework for Windows Mobile 2005. Currently it only support some Bluetooth exploits and tools like BlueSnarf, BlueJack, and some DoS attacks. Should work on any PocketPC with the Microsoft Bluetooth stack.
Bluediving – Bluediving is a Bluetooth penetration testing suite. It implements attacks like Bluebug, BlueSnarf, BlueSnarf++, BlueSmack, has features such as Bluetooth address spoofing, an AT and a RFCOMM socket shell and implements tools like carwhisperer, bss, L2CAP packetgenerator, L2CAP connection resetter, RFCOMM scanner and greenplaque scanning mode.
Transient Bluetooth Environment Auditor – T-BEAR is a security-auditing platform for Bluetooth-enabled devices. The platform consists of Bluetooth discovery tools, sniffing tools and various cracking tools.
Bluesnarfer – Bluesnarfer will download the phone-book of any mobile device vulnerable to Bluesnarfing. Bluesnarfing is a serious security flow discovered in several Bluetooth-enabled mobile phones. If a mobile phone is vulnerable, it is possible to connect to the phone without alerting the owner, and gain access to restricted portions of the stored data.
BTcrack – BTCrack is a Bluetooth Pass phrase (PIN) cracking tool. BTCrack aims to reconstruct the Passkey and the Link key from captured Pairing exchanges.
Blooover II – Blooover II is a J2ME-based auditing tool. It is intended to serve as an auditing tool to check whether a mobile phone is vulnerable.
BlueTest – BlueTest is a Perl script designed to do data extraction from vulnerable Bluetooth-enabled devices.
BTAudit – BTAudit is a set of programs and scripts for auditing Bluetooth-enabled devices.
What’s next ? Let everyone know to disable Bluetooth until they really need it. Additionally, make sure to update your phone software on a regular basis.


