A Basic Guide to Linux Boot Process
Every time you power on your Linux PC, it goes through a series of stages before finally displaying a login screen that prompts for your username or password. There are 4 distinct stages that every Linux distribution goes through in a typical boot-up process.
In this guide, we will highlight the various steps taken by the Linux OS from the time it is powered on to the time you log in. Kindly note that this guide only takes into consideration the GRUB2 bootloader and systemd init as they are currently in use by a vast majority of modern Linux distributions.
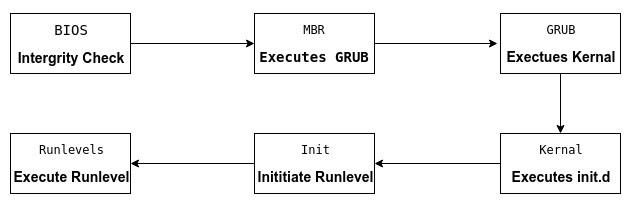
The booting process takes the following 4 steps that we will discuss in greater detail:
- BIOS Integrity check (POST)
- Loading of the Boot loader (GRUB2)
- Kernel initialization
- Starting systemd, the parent of all processes
1. The BIOS Integrity Check (POST)
The boot process is usually initialized when a user presses the power-on button – if the PC was already shut down – or reboots the system using either the GUI or on the command line.
When the Linux system powers up, the BIOS (Basic Input Output System) kicks in and performs a Power On Self Test (POST). This is an integrity check that performs a plethora of diagnostic checks.
The POST probes the hardware operability of components such as the HDD or SSD, Keyboard, RAM, USB ports, and any other piece of hardware. If some hardware device is not detected, or if there’s a malfunction in any of the devices such as a corrupt HDD or SSD, an error message is splashed on the screen prompting your intervention.
In some cases, a beeping sound will go off especially in the event of a missing RAM module. However, if the expected hardware is present and functioning as expected, the booting process proceeds to the next stage.
2. The Bootloader (GRUB2)
Once the POST is complete and the coast is clear, the BIOS probes the MBR (Master Boot Record) for the bootloader and disk partitioning information.
The MBR is a 512-byte code that is located on the first sector of the hard drive which is usually /dev/sda or /dev/hda depending on your hard drive architecture. Note, however, that sometimes the MBR can be located on a Live USB or DVD installation of Linux.
There are 3 main types of bootloaders in Linux: LILO, GRUB, and GRUB2. The GRUB2 bootloader is the latest and primary bootloader in modern Linux distributions and informs our decision to leave out the other two which have become antiquated with the passage of time.
GRUB2 stands for GRand Unified Bootloader version 2. Once the BIOS locates the grub2 bootloader, it executes and loads it onto the main memory (RAM).
The grub2 menu allows you to do a couple of things. It allows you to select the Linux kernel version that you’d want to use. If you have been upgrading your system a couple of times, you might see different kernel versions listed. Additionally, it gives you the ability to edit some kernel parameters by pressing a combination of keyboard keys.
Also, in a dual-boot setup where you have multiple OS installations, the grub menu allows you to select which OS to boot into. The grub2 configuration file is the /boot/grub2/grub2.cfg file. GRUB’s main objective is to load the Linux kernel onto the main memory.
3. Kernel Initialization
The kernel is the core of any Linux system. It interfaces the PC’s hardware with the underlying processes. The kernel controls all the processes on your Linux system. Once the selected Linux kernel is loaded by the bootloader, it must self extract from its compressed version before undertaking any task. Upon self-extracting, the selected kernel mounts the root file system and initializes the /sbin/init program commonly referred to as init.
Init is always the first program to be executed and is assigned the process ID or PID of 1. It’s the init process that spawns various daemons & mounts all partitions that are specified in the /etc/fstab file.
The kernel then mounts the initial RAM disk (initrd) which is a temporary root filesystem until the real root filesystem is mounted. All kernels are located in the /boot directory together with the initial RAM disk image.
4.Starting Systemd
The kernel finally loads Systemd, which is the replacement of the old SysV init. Systemd is the mother of all Linux processes and manages among other things mounting of file systems, starting and stopping services to mention just a few.
Systemd uses the /etc/systemd/system/default.target file to determine the state or target that the Linux system should boot into.
- For a desktop workstation (with a GUI) the default target value is 5 which is the equivalent of run level 5 for the old SystemV init.
- For a server, the default target is multi-user.target which corresponds to run level 3 in SysV init.
Here’s a breakdown of the systemd targets:
- poweroff.target (runlevel 0): Poweroff or Shutdown the system.
- rescue.target (runlevel 1): launches a rescue shell session.
- multi-user.target (runlevel 2,3,4): Configures the system to a non-graphical (console) multi-user system.
- graphical.target (runlevel 5): Set the system to use a graphical multi-user interface with network services.
- reboot.target (runlevel 6): reboots the system.
To check the current target on your system, run the command:
You can switch from one target to another by running the following command on the terminal:
For example, init 3 configures the system to a non-graphical state.
The init 6 command reboots your system and init 0 powers off the system. Be sure to invoke sudo command when you want to switch to these two targets.
The booting process ends once systemd loads all the daemons and sets the target or run level value. It’s at this point you are prompted for your username and password upon which you gain entry to your Linux system.
The Linux Booting Process — 6 Steps Described in Detail
An operating system (OS) is the low-level software that manages resources, controls peripherals, and provides basic services to other software. In Linux, there are 6 distinct stages in the typical booting process.
1. BIOS
BIOS stands for Basic Input/Output System. In simple terms, the BIOS loads and executes the Master Boot Record (MBR) boot loader.
When you first turn on your computer, the BIOS first performs some integrity checks of the HDD or SSD.
Then, the BIOS searches for, loads, and executes the boot loader program, which can be found in the Master Boot Record (MBR). The MBR is sometimes on a USB stick or CD-ROM such as with a live installation of Linux.
Once the boot loader program is detected, it’s then loaded into memory and the BIOS gives control of the system to it.
2. MBR
MBR stands for Master Boot Record, and is responsible for loading and executing the GRUB boot loader.
The MBR is located in the 1st sector of the bootable disk, which is typically /dev/hda , or /dev/sda , depending on your hardware. The MBR also contains information about GRUB, or LILO in very old systems.
3. GRUB
Sometimes called GNU GRUB, which is short for GNU GRand Unified Bootloader, is the typical boot loader for most modern Linux systems.
The GRUB splash screen is often the first thing you see when you boot your computer. It has a simple menu where you can select some options. If you have multiple kernel images installed, you can use your keyboard to select the one you want your system to boot with. By default, the latest kernel image is selected.
The splash screen will wait a few seconds for you to select and option. If you don’t, it will load the default kernel image.
In many systems you can find the GRUB configuration file at /boot/grub/grub.conf or /etc/grub.conf . Here’s an example of a simple grub.conf file:
#boot=/dev/sda default=0 timeout=5 splashimage=(hd0,0)/boot/grub/splash.xpm.gz hiddenmenu title CentOS (2.6.18-194.el5PAE) root (hd0,0) kernel /boot/vmlinuz-2.6.18-194.el5PAE ro root=LABEL=/ initrd /boot/initrd-2.6.18-194.el5PAE.img4. Kernel
The kernel is often referred to as the core of any operating system, Linux included. It has complete control over everything in your system.
In this stage of the boot process, the kernel that was selected by GRUB first mounts the root file system that’s specified in the grub.conf file. Then it executes the /sbin/init program, which is always the first program to be executed. You can confirm this with its process id (PID), which should always be 1.
The kernel then establishes a temporary root file system using Initial RAM Disk (initrd) until the real file system is mounted.
5. Init
At this point, your system executes runlevel programs. At one point it would look for an init file, usually found at /etc/inittab to decide the Linux run level.
Modern Linux systems use systemd to choose a run level instead. According to TecMint, these are the available run levels:
Run level 0 is matched by poweroff.target (and runlevel0.target is a symbolic link to poweroff.target).
Run level 1 is matched by rescue.target (and runlevel1.target is a symbolic link to rescue.target).
Run level 3 is emulated by multi-user.target (and runlevel3.target is a symbolic link to multi-user.target).
Run level 5 is emulated by graphical.target (and runlevel5.target is a symbolic link to graphical.target).
Run level 6 is emulated by reboot.target (and runlevel6.target is a symbolic link to reboot.target).
Emergency is matched by emergency.target.
systemd will then begin executing runlevel programs.
6. Runlevel programs
Depending on which Linux distribution you have installed, you may be able to see different services getting started. For example, you might catch starting sendmail …. OK .
These are known as runlevel programs, and are executed from different directories depending on your run level. Each of the 6 runlevels described above has its own directory:
- Run level 0 – /etc/rc0.d/
- Run level 1 – /etc/rc1.d/
- Run level 2 – /etc/rc2.d/
- Run level 3 – /etc/rc3.d/
- Run level 4 – /etc/rc4.d/
- Run level 5 – /etc/rc5.d/
- Run level 6 – /etc/rc6.d/
Note that the exact location of these directories varies from distribution to distribution.
If you look in the different run level directories, you’ll find programs that start with either an «S» or «K» for startup and kill, respectively. Startup programs are executed during system startup, and kill programs during shutdown.
That’s everything you need to know about the Linux booting process. Now go out there and make Tux proud.