- 5.3. Viewing the Current Status and Settings of firewalld
- 5.3.2. Viewing Current firewalld Settings
- 5.3.2.1. Viewing Allowed Services using GUI
- 5.3.2.2. Viewing firewalld Settings using CLI
- Checking Whether a Firewall Is Running on Linux
- 1. Overview
- 2. Uncomplicated Firewall (ufw) and gufw Tool
- 2.1. Uncomplicated Firewall (ufw)
- 2.2. Using gufw Tool
- 3. Using firewalld
- 4. Using iptables
- 5. Conclusion
- How do I know if my firewall is on?
- 5 Answers 5
5.3. Viewing the Current Status and Settings of firewalld
The firewall service, firewalld , is installed on the system by default. Use the firewalld CLI interface to check that the service is running.
~]# systemctl status firewalld firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor pr Active: active (running) since Mon 2017-12-18 16:05:15 CET; 50min ago Docs: man:firewalld(1) Main PID: 705 (firewalld) Tasks: 2 (limit: 4915) CGroup: /system.slice/firewalld.service └─705 /usr/bin/python3 -Es /usr/sbin/firewalld --nofork --nopid Furthermore, it is important to know how firewalld is set up and which rules are in force before you try to edit the settings. To display the firewall settings, see Section 5.3.2, “Viewing Current firewalld Settings”
5.3.2. Viewing Current firewalld Settings
5.3.2.1. Viewing Allowed Services using GUI
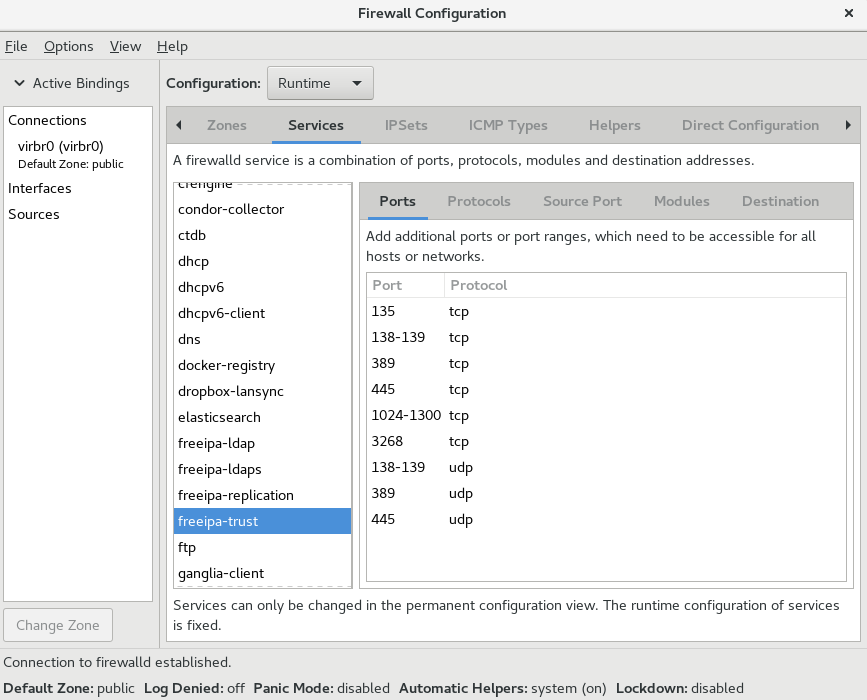
To view the list of services using the graphical firewall-config tool, press the Super key to enter the Activities Overview, type firewall , and press Enter . The firewall-config tool appears. You can now view the list of services under the Services tab.
Alternatively, to start the graphical firewall configuration tool using the command-line, enter the following command:
The Firewall Configuration window opens. Note that this command can be run as a normal user, but you are prompted for an administrator password occasionally.
Figure 5.2. The Services tab in firewall-config
5.3.2.2. Viewing firewalld Settings using CLI
With the CLI client, it is possible to get different views of the current firewall settings. The —list-all option shows a complete overview of the firewalld settings.
firewalld uses zones to manage the traffic. If a zone is not specified by the —zone option, the command is effective in the default zone assigned to the active network interface and connection.
~]# firewall-cmd --list-all public target: default icmp-block-inversion: no interfaces: sources: services: ssh dhcpv6-client ports: protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: To specify the zone for which to display the settings, add the —zone=zone-name argument to the firewall-cmd —list-all command, for example:
~]# firewall-cmd --list-all --zone=home home target: default icmp-block-inversion: no interfaces: sources: services: ssh mdns samba-client dhcpv6-client . [output truncated] To see the settings for particular information, such as services or ports, use a specific option. See the firewalld manual pages or get a list of the options using the command help:
~]# firewall-cmd --help Usage: firewall-cmd [OPTIONS. ] General Options -h, --help Prints a short help text and exists -V, --version Print the version string of firewalld -q, --quiet Do not print status messages Status Options --state Return and print firewalld state --reload Reload firewall and keep state information . [output truncated] ~]# firewall-cmd --list-services ssh dhcpv6-client Listing the settings for a certain subpart using the CLI tool can sometimes be difficult to interpret. For example, you allow the SSH service and firewalld opens the necessary port (22) for the service. Later, if you list the allowed services, the list shows the SSH service, but if you list open ports, it does not show any. Therefore, it is recommended to use the —list-all option to make sure you receive a complete information.
Checking Whether a Firewall Is Running on Linux
The Kubernetes ecosystem is huge and quite complex, so it’s easy to forget about costs when trying out all of the exciting tools.
To avoid overspending on your Kubernetes cluster, definitely have a look at the free K8s cost monitoring tool from the automation platform CAST AI. You can view your costs in real time, allocate them, calculate burn rates for projects, spot anomalies or spikes, and get insightful reports you can share with your team.
Connect your cluster and start monitoring your K8s costs right away:
1. Overview
In this tutorial, we’ll discuss the various ways to check firewall status in Linux.
There are diverse firewall options available at our disposal and we can choose any according to our needs. We’ll look at ufw, firewalld, and iptables and learn how to check their status.
2. Uncomplicated Firewall (ufw) and gufw Tool
ufw is the default firewall configuration tool for most Linux distros including Ubuntu. It runs on top of iptables and it’s easier to manage.
For the distributions that lack it, we can simply install it:
2.1. Uncomplicated Firewall (ufw)
ufw provides a user-friendly way to create an IPv4/IPv6 host-based firewall. To check the status of ufw we run:
$ sudo ufw status Status: inactiveIf it’s the first time we’re running our system, then it should show inactive. Otherwise, if we’ve enabled it before, it should display active:
$ sudo ufw status Status: active To Action From -- ------ ---- Nginx Full ALLOW Anywhere OpenSSH ALLOW Anywhere For a more detailed output, we append the verbose option:
$ ufw status verbose Status: active Logging: on (low) Default: deny (incoming), allow (outgoing), disabled (routed) New profiles: skip To Action From -- ------ ---- 80,443/tcp (Nginx Full) ALLOW IN Anywhere 22/tcp (OpenSSH) ALLOW IN AnywhereWe can also show a numbered list of the active rules when we use the numbered option:
$ ufw status numbered Status: active To Action From -- ------ ---- [ 1] Nginx Full ALLOW IN Anywhere [ 2] OpenSSH ALLOW IN Anywhere Further, we can also filter out the state of active services using deny or allow. They both show the firewall’s active:
$ sudo ufw status | grep -i deny 23 DENY Anywhere 23 (v6) DENY Anywhere (v6) $ sudo ufw status | grep -i allow Nginx Full ALLOW Anywhere OpenSSH ALLOW Anywhere 2.2. Using gufw Tool
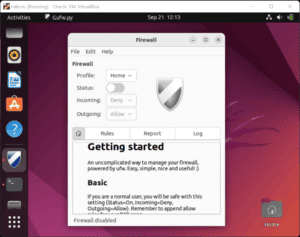
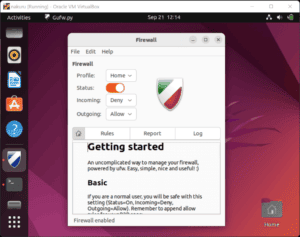
Besides using ufw on the terminal, we can install gufw. gufw is a graphical application tool powered by ufw. We can also use it to manage our firewall including checking its status.
Afterward, we can open the application either through the terminal or by clicking on the app itself. To open it from the terminal, we run:
Thereafter, we check the status. By default it’s not enabled and the status switch is off:
The status switch turns to orange when the firewall’s active:
3. Using firewalld
Aside from ufw, we can also use firewalld to manage our firewall rules. firewalld provides a dynamically managed firewall. It supports network/firewall zones that define the trust level of network connections.
It doesn’t come preinstalled in some distros (for RedHat-based distros it’s the default). For those that lack it, we can install it:
$ sudo apt update $ sudo apt install firewalldfirewalld can run alongside ufw. But we’ve to disable ufw if it’s enabled. This is solely to avoid any conflicts that may occur.
The firewall should run by default after the installation. Let’s check its status using:
$ sudo firewall-cmd --state $ sudo firewall-cmd --list-allApart from the firewall-cmd command, we can use systemctl status firewalld to check if the firewalld service is running:
$ sudo systemctl status firewalld ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled) Active: active (running) since Fri 2022-09-23 13:47:20 UTC; 49s ago Docs: man:firewalld(1) Main PID: 2292374 (firewalld) Tasks: 2 (limit: 1119) Memory: 24.3M CPU: 366ms CGroup: /system.slice/firewalld.service └─2292374 /usr/bin/python3 /usr/sbin/firewalld --nofork --nopid 4. Using iptables
We can also use iptable to check the status of our firewall.
iptables are used to set up, maintain, and inspect the tables of an IP packet filter rule in the Linux kernel. The tables contain in-built chains and may also have user-defined chains (a chain is a list of rules). To view the chains, we run:
For instance, when the firewall is running and the rules are set, the rules are listed:
$ sudo iptables -L -v Chain INPUT (policy DROP 1899K packets, 119M bytes) pkts bytes target prot opt in out source destination 13M 1737M ufw-before-logging-input all -- any any anywhere anywhere Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 ufw-before-forward all -- any any anywhere anywhere Chain OUTPUT (policy ACCEPT 5531 packets, 644K bytes)Otherwise, we get an empty table, showing three rows with no rules specified:
$ iptables -L -v Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination5. Conclusion
In this article, we’ve looked at three ways we can check if the firewall is up and running in Linux. Depending on our distribution, we’ll always find one of these three available by default.
We learned that it’s important we only activate one firewall at a time. For ufw, we saw that it also has a graphical interface gufw we can use.
Lastly, we discussed how we can check if the firewall’s status, i.e., whether it’s running on our machine.
How do I know if my firewall is on?
I installed Firestarter, and configured my firewall. But I’m in doubt : On boot, I sometimes see a [FAIL] marker, and to the left, I guess it was something like «start firewall». I can’t be sure because the message is seen for less than a second, so I wanted to know if there is a way, without starting the whole firestarter software, to know if the firewall is on and working, or not. Either a gadget, or better, some console instruction, the exact name of the firewall process/daemon, or bash script, will do. Edit: I already tested my computer with the «Shield’s Up» http://www.grc.com feature, which marks my computer as «Stealth», but as I am behind a router, I’m not surprised. Still, apparently, my computer answers to pings. Strange.
This question appears to be abandoned, if you are experiencing a similar issue please ask a new question with details pertaining to your problem. If you feel this question is not abandoned, please flag the question explaining that. 🙂
This question has helpful, upvoted answers and consequently is not abandoned. It should be reopened.
5 Answers 5
There are basically 2 ways of seeing if the firewall is configured. You should use both of the methods and verify that the firewall is both configured and configured the way you wish it to be.
First, check that the firewall rules have been applied. Pretty much all modern Linux firewall solutions use iptables for firewall. You can see that there are rules in place with iptables command:
This will return the current set of rules. There can be a few rules in the set even if your firewall rules haven’t been applied. Just look for lines that match your given rulesets. This will give you an idea of what rules have been entered to the system. this doesn’t guarantee the validity of the rules, only that they have been understood.
Next, you will use a second computer to test for connections against the host in question. This can be easily done with the nmap command (found in nmap package). Quick and dirty way of checking is:
nmap -P0 10.0.0.10 nmap -P0 -sU 10.0.0.10 Replace the IP address 10.0.0.10 with your destination hosts IP address.
The first line will scan for TCP ports that are open and available from the second computer. Second line will repeat the scan but this time with UDP ports. -P0 flag will prevent the host from being tested with a ICMP Echo packet, but might be blocked by your firewall rules.
The scan might take a while so be patient. There is also a GUI frontend for nmap called zenmap which makes it a bit easier to interpret the scan results if there is a lot of output.