- How can I see what ports are open on my machine?
- 10 Answers 10
- nmap (install)
- How to Use Netstat Command in Linux to Check a Specific Port
- Installing netstat on Debian 9 Stretch:
- Listing All Ports and Sockets Using netstat:
- Listing All the Listening Ports and Sockets with netstat:
- Listing All the Listening TCP Ports with netstat:
- Listing All the Listening UDP Ports with netstat:
- Find out What Service Name Represent What Port:
- How to Get Help with netstat:
- About the author
- Shahriar Shovon
- How to check opened/closed ports on my computer?
- 8 Answers 8
How can I see what ports are open on my machine?
I would like to see what ports are open on my machine, e.g. what ports my machine is listening on. E.g. port 80 if I have installed a web server, and so on. Is there any command for this?
10 Answers 10
If the netstat command is not available, install it with:
sudo apt install net-tools -l already filters for listening. grep LISTEN won’t help beyond hiding 2 lines of header information.
-t : tcp, -l : listening socket, -p : show pid and program name, -n : print 127.0.0.1:80 instead of localhost:http . Reference: linux.die.net/man/8/netstat
The expanded command is sudo netstat —tcp —listening —programs —numeric . There’s no need to use grep unless you want to eliminate column headers.
nmap (install)
Nmap («Network Mapper») is a free and open source utility for network exploration or security auditing.
Use nmap 192.168.1.33 for internal PC or nmap external IP address .
More information man nmap .
Zenmap is the official GUI frontend.
Remember that there is a difference between nmap localhost and nmap 192.168.0.3 (or what ever you machine IP is)
I think netstat is a better answer to this. netstat will list what the system is listening on directly, and without using an additional application or doing unnecessary calls over localhost or thought the network.
This is stupid. If you have access to the computer, just use netstat -ln . You’ll instantly see all the open ports.
nmap localhost didn’t find services that were bound only to localhost. For example, I run influxd with bind-address:localhost:8086 . That didn’t show up in sudo nmap localhost , but did show up in sudo netstat -tulpn .
Other good ways to find out what ports are listenting and what your firewall rules are:
To list open ports use the netstat command.
$ sudo netstat -tulpn | grep LISTEN tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 5452/dnsmasq tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1037/cupsd tcp6 0 0 ::1:631 . * LISTEN 1037/cupsd In the above example three services are bound to the loopback address.
IPv4 services bound to the loopback address «127.0.0.1» are only available on the local machine. The equivalent loopback address for IPv6 is «::1». The IPv4 address «0.0.0.0» means «any IP address», which would mean that other machines could potentially connect to any of the locally configured network interfaces on the specific port.
Another method is to use the lsof command:
$ sudo lsof -nP -i | grep LISTEN cupsd 1037 root 9u IPv6 11276 0t0 TCP [::1]:631 (LISTEN) cupsd 1037 root 10u IPv4 11277 0t0 TCP 127.0.0.1:631 (LISTEN) dnsmasq 5452 nobody 5u IPv4 212707 0t0 TCP 127.0.0.1:53 (LISTEN) For more details see man netstat or man lsof .
How to Use Netstat Command in Linux to Check a Specific Port
netstat is a powerful networking tool on Linux. In this article, I am going to show you how to install netstat on Debian 9 Stretch and how to use netstat to show listening ports on Debian 9 Stretch. Let’s get started.
Installing netstat on Debian 9 Stretch:
netstat command is a part of the net-tools utility package on Debian 9 Stretch. It may not be installed by default on your Debian 9 Stretch operating system. The net-tools package is available in the official package repository of Debian 9 Stretch. So installing it is very easy.
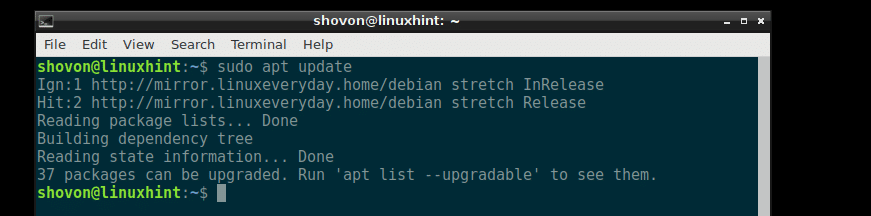
First update the apt package repository cache of your Debian 9 Stretch machine with the following command:
The apt package repository cache should be updated.
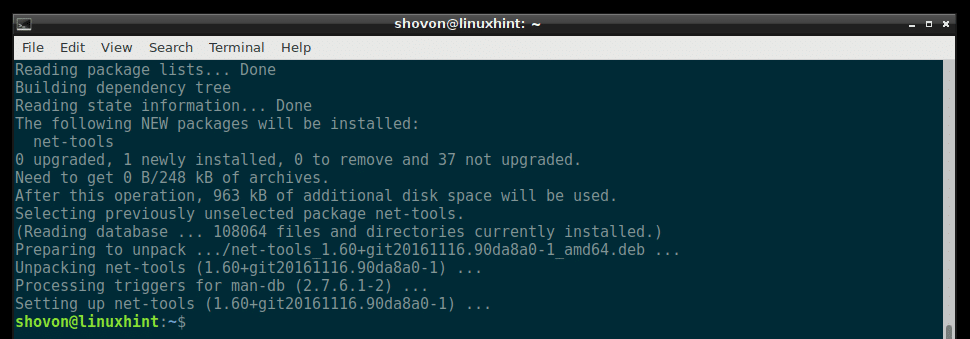
Now run the following command to install the net-tools utility on Debian 9 Stretch:
net-tools should be installed.
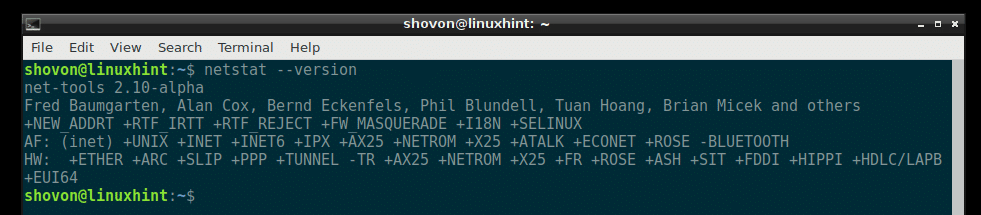
Now check whether netstat is working with the following command:
Listing All Ports and Sockets Using netstat:
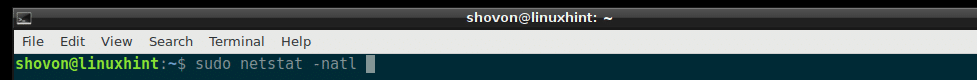
You can list all the opened ports and connected sockets on your Debian 9 machine with the following command:
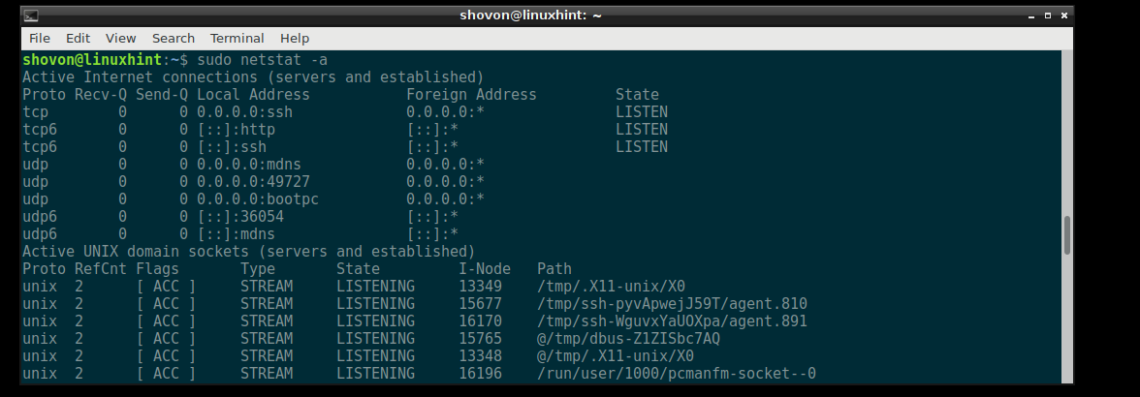
As you can see, all the opened ports and sockets are listed. It’s a very long list.
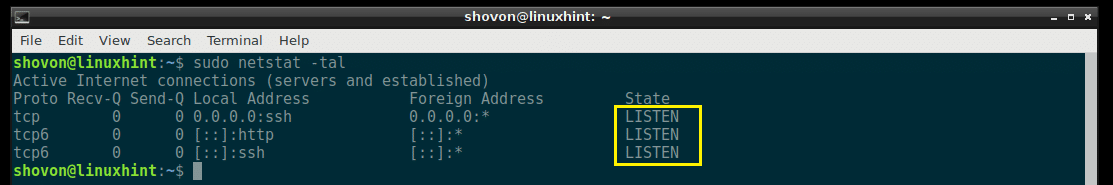
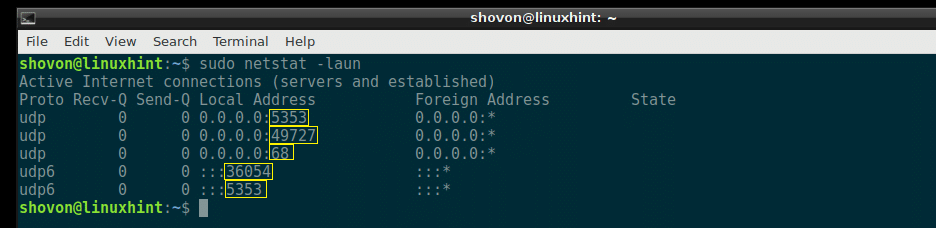
Listing All the Listening Ports and Sockets with netstat:
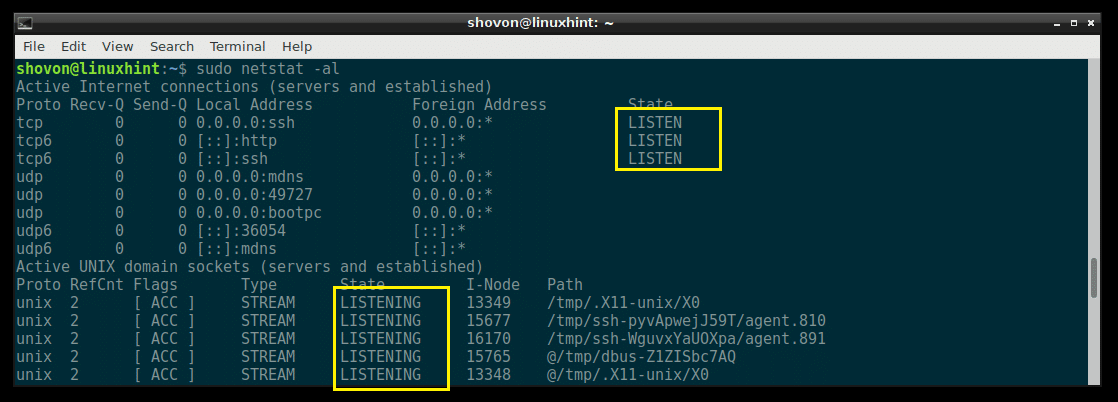
You can use netstat to see a list of all the ports and sockets that are listening with the following command:
As you can see, all the ports and sockets on your Debian 9 machine is listed. It’s a long list.
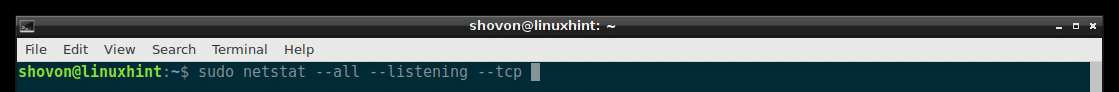
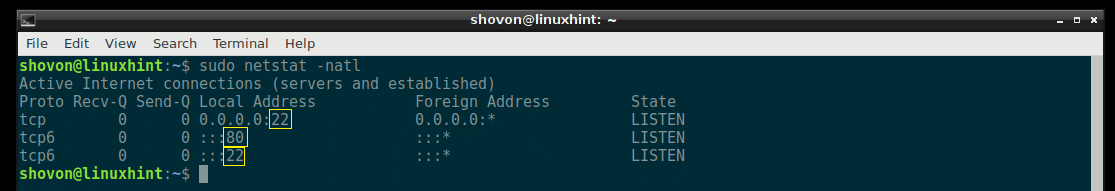
Listing All the Listening TCP Ports with netstat:
You can list all the TCP (Transmission Control Protocol) ports that are listening using netstat with the following command:
As you can see, all the TCP ports that are listening is listed.
In the output of netstat, all the common ports are replaced by the service name by default. For example, the port 80 by default is the port for the HTTP (HyperText Transfer Protocol), which we all are familiar with. So in the output of netstat, it is shown as http instead of port 80 as you can see in the marked section of the screenshot below.
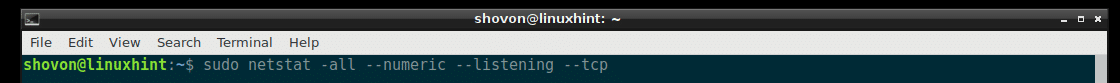
If you need the port number, not the service name, then you can run the following netstat command:
As you can see from the marked section of the screenshot below, the service names are replaced by the port number.
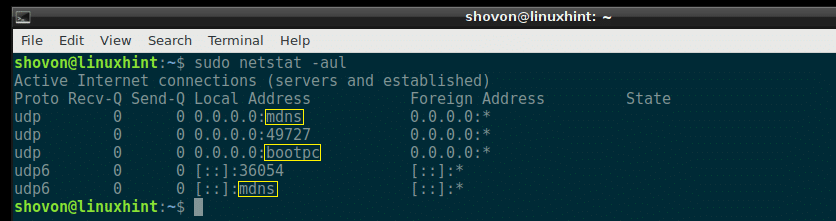
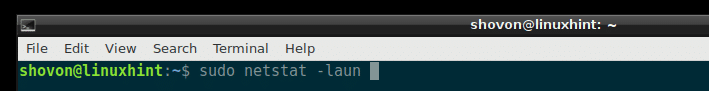
Listing All the Listening UDP Ports with netstat:
If you want to list all the UDP (User Datagram Protocol) ports that are listening on your Debian 9 machine, you can do so with the following netstat command:
All the listening UDP ports should be listed. Just like the TCP port example, the common port numbers are replaced by the service names by default here as well, as you can see from the marked section of the screenshot below.
But the ports that are not common are not replaced by the service names as you can see from the marked section of the screenshot below.
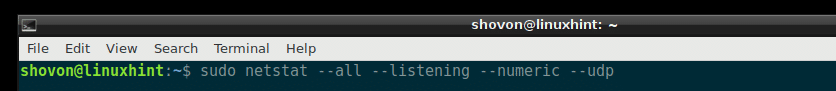
If you want all the ports to be displayed, not the service name as before, then run the following netstat command:
As you can see from the marked section of the screenshot below, the service names are replaced by the UDP port number.
Find out What Service Name Represent What Port:
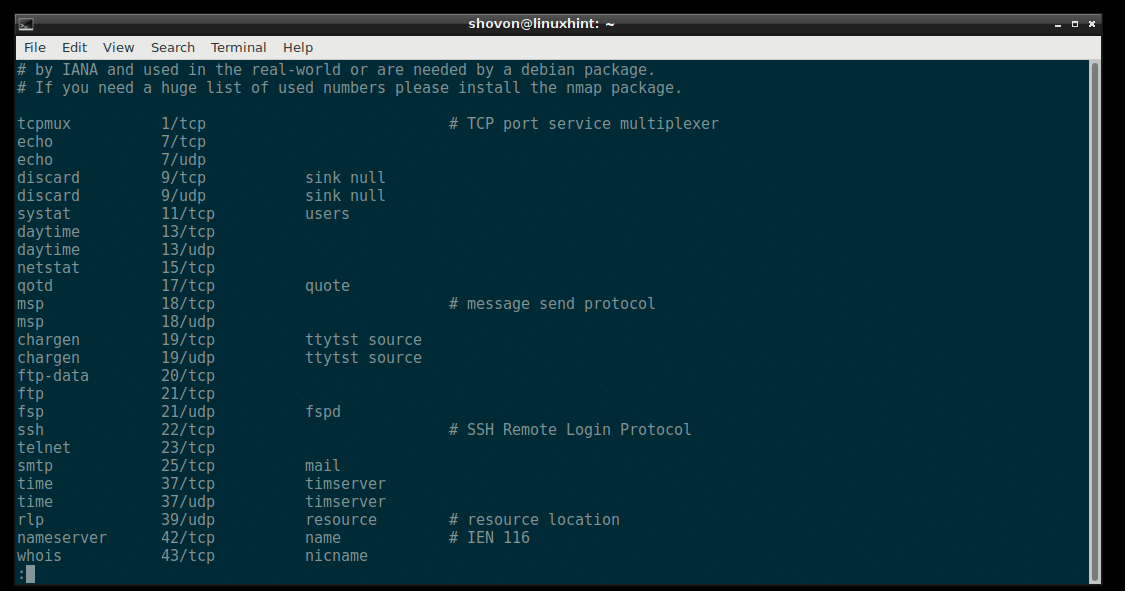
Debian 9 Stretch has a service file which can be found at /etc/services
You can open the service file /etc/services with the following command:
The contents of the /etc/services file:
The /etc/services file contains a long list of service name, and the port number and protocol of that specific service that a client or server may use. Programs on Linux system such as netstat uses this file to resolve the port numbers to service names and vice versa.
The service name, port number and protocol of the SSH service in /etc/services file:
How to Get Help with netstat:
On Debian 9 Stretch, if you need any help with the netstat command, you can just go to the manpage of netstat and you should be able to get a clear documentation of what netstat command line options are available and what they do.
To go to the manpage of netstat, run the following command:
The netstat manpage:
That’s how you show listening ports on Debian 9 Stretch with netstat. Thanks for reading this article.
About the author
Shahriar Shovon
Freelancer & Linux System Administrator. Also loves Web API development with Node.js and JavaScript. I was born in Bangladesh. I am currently studying Electronics and Communication Engineering at Khulna University of Engineering & Technology (KUET), one of the demanding public engineering universities of Bangladesh.
How to check opened/closed ports on my computer?
@Justgivemeaname: nmap is a tool to check for open ports on another host. If you can run netstat on a machine, it’s much faster and reliable to use it.
@DavidFoerster: Didn’t know about netstat , so I learned that. It says in the link that it should be used from another host, though. Thanks!
8 Answers 8
There’s a few parameters to netstat that are useful for this :
- -l or —listening shows only the sockets currently listening for incoming connection.
- -a or —all shows all sockets currently in use.
- -t or —tcp shows the tcp sockets.
- -u or —udp shows the udp sockets.
- -n or —numeric shows the hosts and ports as numbers, instead of resolving in dns and looking in /etc/services.
You use a mix of these to get what you want. To know which port numbers are currently in use, use one of these:
netstat -atn # For tcp netstat -aun # For udp netstat -atun # For both In the output all port mentioned are in use either listening for incoming connection or connected to a peer** all others are closed. TCP and UDP ports are 16 bits wide (they go from 1-65535)
** They can also be connecting/disconnecting from the peer.
If it shows some process its used. Its closed(not used) if there is no output.
Another alternative command line easy to use to find out which process is using a port:
lsof -n -i4TCP:$PORT | grep LISTEN I added the next function in my .bash_profile,
and now run «pslisten 5060» to see who is grabing my SIP port.
It’s work with Apple Mac OS X too.
Is the port status «LISTENING» indicated that the port is opened?
Yes. It means that some service is listening to that port on your computer for incoming connection i.e. this port is open for establishing new connections.
Any port that are not shown in the output indicated that it’s closed?
Yes. Remember netstat -a will show all active (listening) and passive (non-listening) connections i.e. the ports that are acting as both server (some services are listening to these ports for connections from a different machine/process) and established (connections are established on these ports regardless of the fact the host/a service can be a server or client)
All TCP and UDP ports belong to a category called sockets and there are a whole lot of those. To view socket info you can check man ss .
Thanks. you wrote that -a means server and established. Does «server» means ports that are being listened at by some services? Does «established» mean ports where there are existing connections regardless of it is a client or server’s port? Then what kinds of ports does -a not show?
I don’t think the -a option means «all active» sockets; it just means «all». netstat shows all active sockets by default, but leaves out the passive sockets (open, listening). By using the -a option both active and passive sockets are shown.
@heemayl The second part of your answer is still not correct. A TCP socket in the «listening» state can never be a connection; it is not connected to anything, it is only listening. Listening TCP sockets are also called passive sockets because of this. If a client attempts to connect to a (listening) socket on a server, a new socket will be created on the server to establish a connection with the client. A socket which is part of an established connection is called an active socket.
Another option is ss. It’s much easier to use.
The below command will only output a list of current listening sockets.
root@server:~# ss -l Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port u_dgr UNCONN 0 0 * 23353 * 23352 u_dgr UNCONN 0 0 * 568 * 362 u_dgr UNCONN 0 0 * 14836 * 14837 u_dgr UNCONN 0 0 * 20446 * 369 u_dgr UNCONN 0 0 * 22877 * 369 u_dgr UNCONN 0 0 * 504 * 347 u_dgr UNCONN 0 0 * 16298 * 369 u_dgr UNCONN 0 0 * 23343 * 369 u_dgr UNCONN 0 0 * 24125 * 369 u_dgr UNCONN 0 0 * 24617 * 369 u_dgr UNCONN 0 0 * 23352 * 23353 u_dgr UNCONN 0 0 * 23334 * 369 u_dgr UNCONN 0 0 * 17113 * 369 u_dgr UNCONN 0 0 * 16957 * 369 u_dgr UNCONN 0 0 * 14793 * 362 u_dgr UNCONN 0 0 * 23345 * 362 u_dgr UNCONN 0 0 * 24070 * 369 udp UNCONN 0 0 *:sunrpc *:* udp UNCONN 0 0 *:981 *:* udp UNCONN 0 0 . sunrpc . * udp UNCONN 0 0 . 981 . * tcp LISTEN 0 128 127.0.0.1:85 *:* tcp LISTEN 0 128 *:ssh *:* tcp LISTEN 0 128 *:3128 *:* tcp LISTEN 0 100 127.0.0.1:smtp *:* tcp LISTEN 0 128 *:8006 *:* tcp LISTEN 0 128 *:sunrpc *:* tcp LISTEN 0 128 . ssh . * tcp LISTEN 0 100 ::1:smtp . * tcp LISTEN 0 128 . sunrpc . *