- How to Test Port [TCP/UDP] Connectivity from a Linux Server
- Testing TCP port connectivity with telnet
- Using nc command to test TCP port connectivity
- Testing UDP port connectivity wit nc command
- Some more articles you might also be interested in …
- How to check if TCP / UDP port is open on Linux & Windows Cloud Servers
- Linux
- Windows
- Related Tutorials
- Testing UDP port connectivity
- 10 Answers 10
- Проверка доступности TCP / UDP портов на удаленной машине
- Selectel — ведущий провайдер облачной инфраструктуры и услуг дата-центров
- UPD 05.01.2022
- 5 ways to check if a Port is open on a remote Linux PC
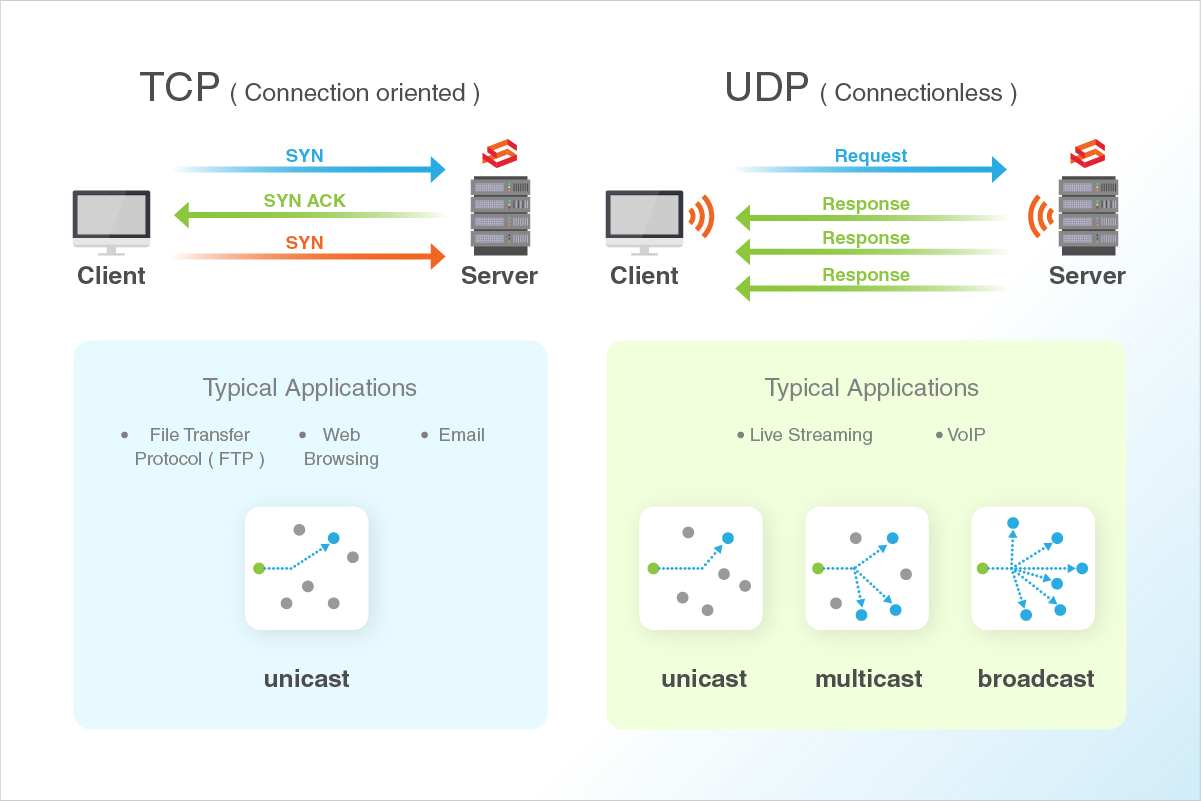
- TCP and UDP ports
- Best ways to check if a Port is open on a Linux PC
- 1. netcat command
How to Test Port [TCP/UDP] Connectivity from a Linux Server
Here is a short post to check port [TCP/UDP] connectivity from a Linux server. A TCP/IP network connection may be either blocked, dropped, open, or filtered. These actions are generally controlled by the IPtables firewall the system uses and is independent of any process or program that may be listening on a network port.
Telnet and nc are common tools used to test port connectivity from Linux server. Telnet can be used to test tcp port connections, where as nc can be used to test both tcp/udp ports connectivity. Make sure telnet and nc tools are installed on the Linux server you are trying to test connectivity.
# yum install nc # yum install telnet
Testing TCP port connectivity with telnet
Lets see how we can use telnet command to test the TCP port connectivity. The syntax to use the telnet command is as follows:
# telnet [hostname/IP address] [port number]
Example of successful connection:
# telnet 192.168.12.10 22 Trying 192.168.12.10. Connected to 192.168.12.10. Escape character is '^]'. SSH-2.0-OpenSSH_6.6.1 Protocol mismatch. Connection closed by foreign host.
Example of unsuccessful connection:
# telnet 192.168.12.10 22 Trying 192.168.12.10. telnet: connect to address 192.168.12.10: No route to host
Using nc command to test TCP port connectivity
The syntax to use nc command for testing TCP post connectivity is as follows:
# nc -z -v [hostname/IP address] [port number]
Example of successful connection:
# nc -z -v 192.168.10.12 22 Connection to 192.118.20.95 22 port [tcp/ssh] succeeded!
Example of unsuccessful connection:
# nc -z -v 192.168.10.12 22 nc: connect to 192.118.20.95 port 22 (tcp) failed: No route to host
Testing UDP port connectivity wit nc command
The syntax to test UDP port connectivity with nc command is as follows:
# nc -z -v -u [hostname/IP address] [port number]
Example of successful connection:
# nc -z -v -u 192.168.10.12 123 Connection to 192.118.20.95 123 port [udp/ntp] succeeded!
Some more articles you might also be interested in …
How to check if TCP / UDP port is open on Linux & Windows Cloud Servers
Verifying which all ports (TCP/UDP) are open and listening on the network interfaces of a server is very important when it comes to server security as well as troubleshooting service-related issues. Vulnerable open ports can be the cause of severe security breaches in a server. It is a must that such ports are found out and closed/disabled.
In case of service-related issues, checking which all ports are in use can be used as a troubleshooting mechanism to find if multiple services are listening on the same port.
The following are the common port numbers:
- Ports 0 to 1023 are Well-Known Ports
- Ports 1024 to 49151 are Registered Ports (*Often registered by a software developer to designate a particular port for their application)
- Ports 49152 to 65535 are Public Ports
| Port | Name of the Service | Transport protocol |
|---|---|---|
| 20,21 | FTP | TCP |
| 22 | SSH | TCP and UDP |
| 23 | Telnet | TCP |
| 25 | SMTP | TCP |
| 50,51 | IPSec | / |
| 53 | DNS | TCP and UDP |
| 67,68 | DHCP | UDP |
| 69 | TFTP | UDP |
| 80 | HTTP | TCP |
| 110 | POP3 | TCP |
| 119 | NNTP | TCP |
| 123 | NTP | TCP |
| 135-139 | NetBIOS | TCP and UDP |
| 143 | IMAP | TCP and UDP |
| 161,162 | SNMP | TCP and UDP |
| 389 | Lightweight Directory Access | TCP and UDP |
| 443 | HTTPS | TCP and UDP |
| 465 | SMTP over SSL | TCP |
| 989 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 990 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 993 | IMAP over SSL | TCP |
| 995 | POP3 over SSL | TCP |
| 3389 | Remote Desktop | TCP and UDP |
This guide outlines the basic steps to determine which all ports are open in a service using commands such as lsof , netstat and nmap in Linux server and netstat on Windows server.
Linux
An example of this is when both Apache and Nginx services run on the same server.
Method 1 — Using lsof command
lsof (list open files) is a command that is used to display the list of all open files in a server and the services that have opened them.
- The general syntax of the lsof command is as below:
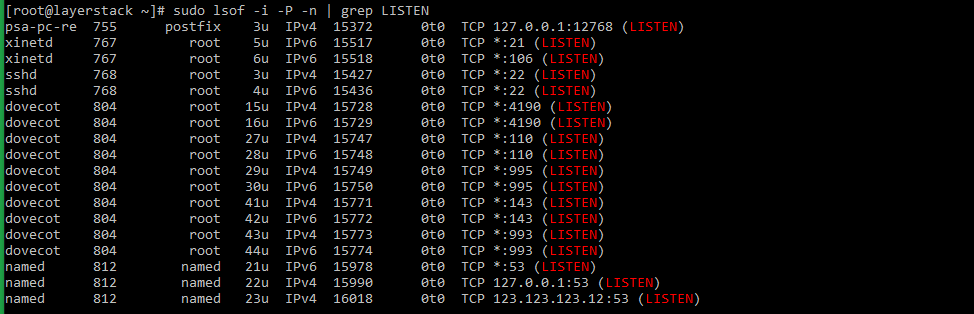
Using pipe and grep commands, the result of the above command can be filtered to show the result of files that are listening on different ports in the server.
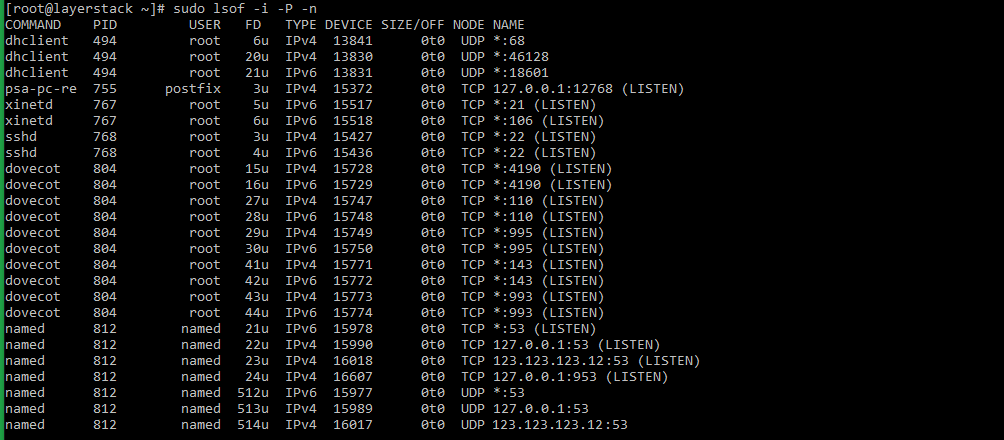
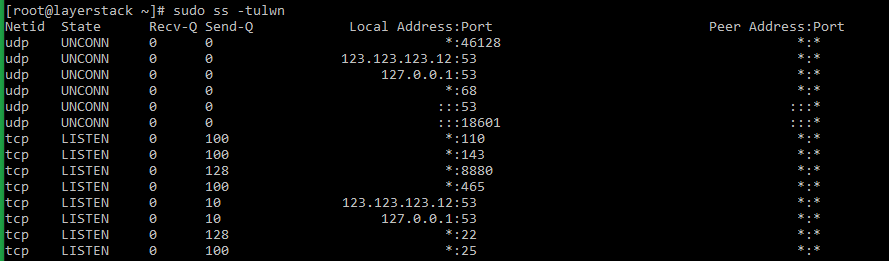
# sudo lsof -i -P -n | grep LISTEN # doas lsof -i -P -n | grep LISTEN (for OpenBSD systems) Taking the last line from sample output, the result can be explained as below:
named 812 named 23u IPv4 16018 0t0 TCP 123.123.123.12:53 (LISTEN) - named : name of the service.
- 123.123.123.12 : IP on which the named service is bound to.
- 53 : TCP port of the service that is being used.
- 812 : Process ID of the service.
Method 2 — Using netstat command
netstat (network statistics) is a command-line tool that can be used to monitor both incoming and outgoing network connections in a server.
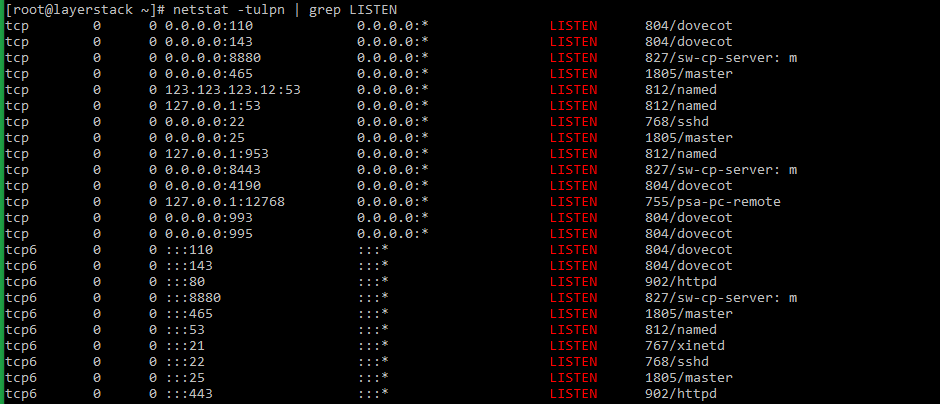
- The netstat command along with the grep command to check the listening services can be used in the below syntax
# netstat -tulpn | grep LISTEN # netstat -nat | grep LISTEN (for OpenBSD systems) netstat command has been deprecated in the latest versions of Linux distribution. The ss command has taken its place.
The syntax for using the ss command is as provided below:
The switches for the ss command mean as follows:
- t: Show only TCP sockets.
- u: Show only UDP sockets.
- l: Show listening sockets.
- p: Show the name of the process that opened the socket.
- n: Do not try to resolve service names.
Method 3 — Using nmap command
nmap (network mapper) is a network scanner command tool that can be used to find out hosts and services on a server. This is done by sending packets to the server and analyzing the results further.
- The general syntax of the nmap command that can be executed from within the server is as follows:
# sudo nmap -sT -O localhost # sudo nmap -sTU -O 123.123.123.12 (scan both TCP and UDP for server) 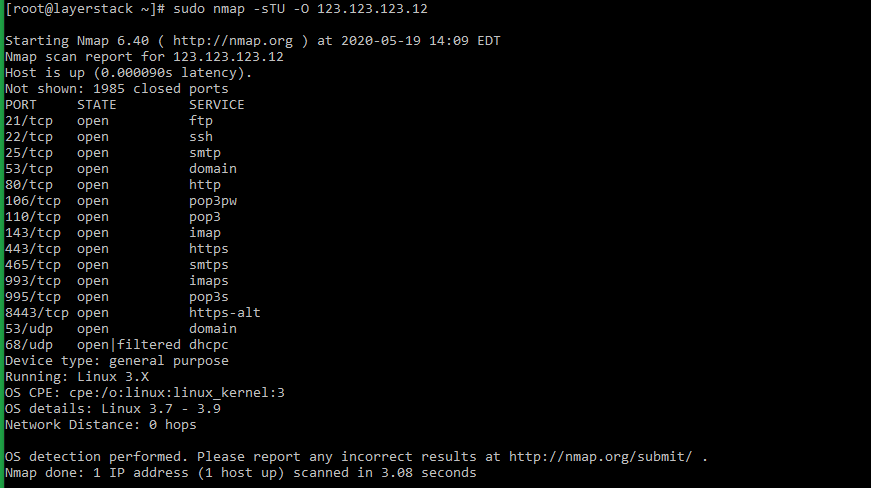
Windows
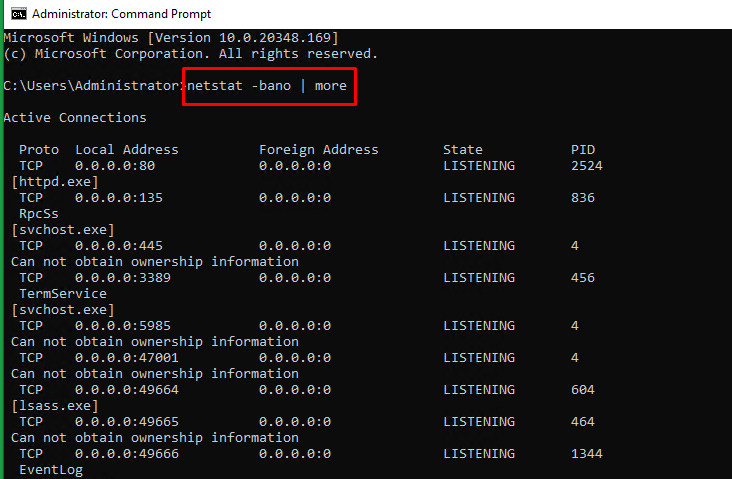
In Windows servers, the netstat command can be used to check the ports that are currently in use in the server.
- The syntax for the netstat command to be used in Windows servers is as below:
> netstat -bano | more > netstat -bano | findstr /R /C:"[LISTENING]" 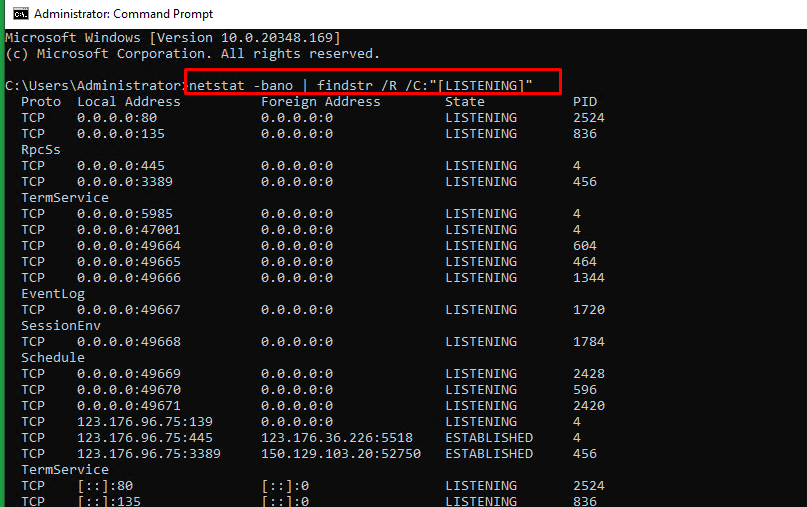
- Proto : The protocol being used for the socket (TCP/UDP).
- Local address : Source IP address and port to which the service is listening to.
- State : The current state of the service.
- PID : Process ID of the service, followed by the service name.
Related Tutorials
Testing UDP port connectivity
I am trying to test whether I can get to a particular port on a remote server (both of which I have access to) through UDP. Both servers are internet facing. I am using netcat to have a certain port listening. I then use nmap to check for that port to see if it is open, but it doesn’t appear to be. Iptables is turned off. Any suggestions why this could be? I am eventually going to setup a VPN tunnel, but because I’m very new to tunnels, I want to make sure I have connectivity on port UDP 1194 before advancing.
I’ve respondend to the «Testing UDP port connectivity» question. But I suggest to concentrate on the more specific «make sure OpenVPN receives my UDP packets» part — that could be easily achieved by looking at OpenVPN logs.
10 Answers 10
There is no such thing as an «open» UDP port, at least not in the sense most people are used to think (which is answering something like «OK, I’ve accepted your connection»). UDP is session-less, so «a port» (read: the UDP protocol in the operating system IP stack) will never respond «success» on its own.
UDP ports only have two states: listening or not. That usually translates to «having a socket open on it by a process» or «not having any socket open». The latter case should be easy to detect since the system should respond with an ICMP Destination Unreachable packet with code=3 (Port unreachable). Unfortunately many firewalls could drop those packets so if you don’t get anything back you don’t know for sure if the port is in this state or not. And let’s not forget that ICMP is session-less too and doesn’t do retransmissions: the Port Unreachable packet could very well be lost somewhere on the net.
A UDP port in the «listening» state may not respond at all (the process listening on it just receives the packet and doesn’t transmit anything) or it could send something back (if the process does act upon reception and if it acts by responding via UDP to the original sender IP:port). So again, you never know for sure what’s the state if you don’t get anything back.
You say you can have control of the receiving host: that makes you able to construct your own protocol to check UDP port reachability: just put a process on the receiving host that’ll listen on the given UDP port and respond back (or send you an email, or just freak out and unlink() everything on the host file system. anything that’ll trigger your attention will do).
Проверка доступности TCP / UDP портов на удаленной машине
Для проверки доступности TCP / UDP портов на удаленной машине будем использовать утилиту Netcat Установка:
### CentOS $ sudo yum install nc ### Debian / Ubuntu $ sudo apt update $ sudo apt install netcatSelectel — ведущий провайдер облачной инфраструктуры и услуг дата-центров
Компания занимает лидирующие позиции на рынке на рынке выделенных серверов и приватных облаков, и входит в топ-3 крупнейших операторов дата-центров в России.
$ nc -zv 10.10.4.4 22 srv-app.local [10.10.4.4] 22 (ssh) open$ nc -uv 10.10.4.2 123 srv-dc01.local [10.10.4.2] 123 (ntp) openUPD 05.01.2022
$ sudo nmap -p22 79.308.191.187 Starting Nmap 6.40 ( http://nmap.org ) at 2022-01-05 19:40 MSK Nmap scan report for 79.308.191.187 Host is up (0.0015s latency). PORT STATE SERVICE 22/tcp open ssh Nmap done: 1 IP address (1 host up) scanned in 0.53 seconds $ sudo nmap -sU -p U:123 94.247.111.10 Starting Nmap 6.40 ( http://nmap.org ) at 2022-01-05 19:37 MSK Nmap scan report for ntp.truenetwork.ru (94.247.111.10) Host is up (0.049s latency). PORT STATE SERVICE 123/udp open ntp Nmap done: 1 IP address (1 host up) scanned in 0.47 secondsУ блога появился новый хостинг от компании Selectel.
Нашли интересную или полезную информацию в блоге? Хотели бы видеть на нем еще больше полезных статей? Поддержи автора рублем. Если вы размещаете материалы этого сайта в своем блоге, соц. сетях, и т.д., убедительная просьба публиковать обратную ссылку на оригинал.
5 ways to check if a Port is open on a remote Linux PC
T here is an ample number of ways to check for any open ports on a remote Linux PC. Knowing open ports on a Linux machine helps system administrators to connect to the remote PC for troubleshooting system and cloud server issues.
TCP and UDP ports
TCP stands for Transmission Control Protocol. In this method, the computers get connected directly until the data transfer is taking place. Therefore, with this method, the data transfer is guaranteed and is reliable but puts a higher load on the server as it has to monitor the connection and the data transfer too.
UDP stands for User Datagram Protocol. Using this method, the data is sent in the form of little packages into the network with the hope that it reaches the final destination. It means the two computers are not connected directly to each other. This method does not provide any guarantee that the data you send will ever reach its destination. Load on the server is less, and so this method is used commonly by the system administrators first to try something that’s not so important.
Now that you know the types are ports on a Linux system, let’s get started with ways of finding the ones that are open.
Best ways to check if a Port is open on a Linux PC
There are multiple ways you can do it. However, the most reliable way to do this is by using the following commands:
- nc: netcat command
- nmap: network mapper tool
- telnet: telnet command
- echo > /dev/tcp/..
- netstat – tuplen
Let’s go through each method one by one.
1. netcat command
netcat is a simple Unix utility that can be used to write and read data using UDP and TCP protocol across network connections.
The primary reason for its design is to provide a back-end tool that works with the scripts and programs. It is also an exploration and network debugging tool that offers tons of features.
To use it, you need to install it in your distro using the respective installation commands.