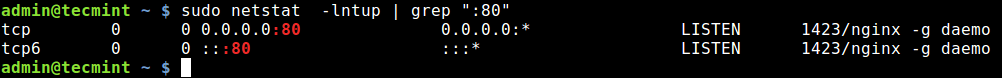How to check opened/closed ports on my computer?
@Justgivemeaname: nmap is a tool to check for open ports on another host. If you can run netstat on a machine, it’s much faster and reliable to use it.
@DavidFoerster: Didn’t know about netstat , so I learned that. It says in the link that it should be used from another host, though. Thanks!
8 Answers 8
There’s a few parameters to netstat that are useful for this :
- -l or —listening shows only the sockets currently listening for incoming connection.
- -a or —all shows all sockets currently in use.
- -t or —tcp shows the tcp sockets.
- -u or —udp shows the udp sockets.
- -n or —numeric shows the hosts and ports as numbers, instead of resolving in dns and looking in /etc/services.
You use a mix of these to get what you want. To know which port numbers are currently in use, use one of these:
netstat -atn # For tcp netstat -aun # For udp netstat -atun # For both In the output all port mentioned are in use either listening for incoming connection or connected to a peer** all others are closed. TCP and UDP ports are 16 bits wide (they go from 1-65535)
** They can also be connecting/disconnecting from the peer.
If it shows some process its used. Its closed(not used) if there is no output.
Another alternative command line easy to use to find out which process is using a port:
lsof -n -i4TCP:$PORT | grep LISTEN I added the next function in my .bash_profile,
and now run «pslisten 5060» to see who is grabing my SIP port.
It’s work with Apple Mac OS X too.
Is the port status «LISTENING» indicated that the port is opened?
Yes. It means that some service is listening to that port on your computer for incoming connection i.e. this port is open for establishing new connections.
Any port that are not shown in the output indicated that it’s closed?
Yes. Remember netstat -a will show all active (listening) and passive (non-listening) connections i.e. the ports that are acting as both server (some services are listening to these ports for connections from a different machine/process) and established (connections are established on these ports regardless of the fact the host/a service can be a server or client)
All TCP and UDP ports belong to a category called sockets and there are a whole lot of those. To view socket info you can check man ss .
Thanks. you wrote that -a means server and established. Does «server» means ports that are being listened at by some services? Does «established» mean ports where there are existing connections regardless of it is a client or server’s port? Then what kinds of ports does -a not show?
I don’t think the -a option means «all active» sockets; it just means «all». netstat shows all active sockets by default, but leaves out the passive sockets (open, listening). By using the -a option both active and passive sockets are shown.
@heemayl The second part of your answer is still not correct. A TCP socket in the «listening» state can never be a connection; it is not connected to anything, it is only listening. Listening TCP sockets are also called passive sockets because of this. If a client attempts to connect to a (listening) socket on a server, a new socket will be created on the server to establish a connection with the client. A socket which is part of an established connection is called an active socket.
Another option is ss. It’s much easier to use.
The below command will only output a list of current listening sockets.
root@server:~# ss -l Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port u_dgr UNCONN 0 0 * 23353 * 23352 u_dgr UNCONN 0 0 * 568 * 362 u_dgr UNCONN 0 0 * 14836 * 14837 u_dgr UNCONN 0 0 * 20446 * 369 u_dgr UNCONN 0 0 * 22877 * 369 u_dgr UNCONN 0 0 * 504 * 347 u_dgr UNCONN 0 0 * 16298 * 369 u_dgr UNCONN 0 0 * 23343 * 369 u_dgr UNCONN 0 0 * 24125 * 369 u_dgr UNCONN 0 0 * 24617 * 369 u_dgr UNCONN 0 0 * 23352 * 23353 u_dgr UNCONN 0 0 * 23334 * 369 u_dgr UNCONN 0 0 * 17113 * 369 u_dgr UNCONN 0 0 * 16957 * 369 u_dgr UNCONN 0 0 * 14793 * 362 u_dgr UNCONN 0 0 * 23345 * 362 u_dgr UNCONN 0 0 * 24070 * 369 udp UNCONN 0 0 *:sunrpc *:* udp UNCONN 0 0 *:981 *:* udp UNCONN 0 0 . sunrpc . * udp UNCONN 0 0 . 981 . * tcp LISTEN 0 128 127.0.0.1:85 *:* tcp LISTEN 0 128 *:ssh *:* tcp LISTEN 0 128 *:3128 *:* tcp LISTEN 0 100 127.0.0.1:smtp *:* tcp LISTEN 0 128 *:8006 *:* tcp LISTEN 0 128 *:sunrpc *:* tcp LISTEN 0 128 . ssh . * tcp LISTEN 0 100 ::1:smtp . * tcp LISTEN 0 128 . sunrpc . * 4 Ways to Find Out What Ports Are Listening in Linux
The state of a port is either open, filtered, closed, or unfiltered. A port is said to be open if an application on the target machine is listening for connections/packets on that port.
In this article, we will explain four ways to check open ports and also will show you how to find which application is listening on what port in Linux.
1. Using Netstat Command
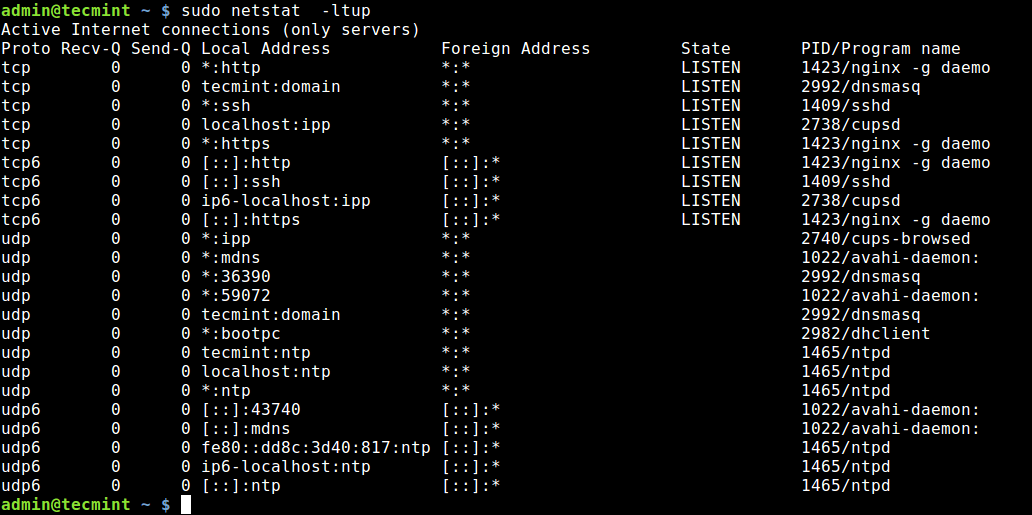
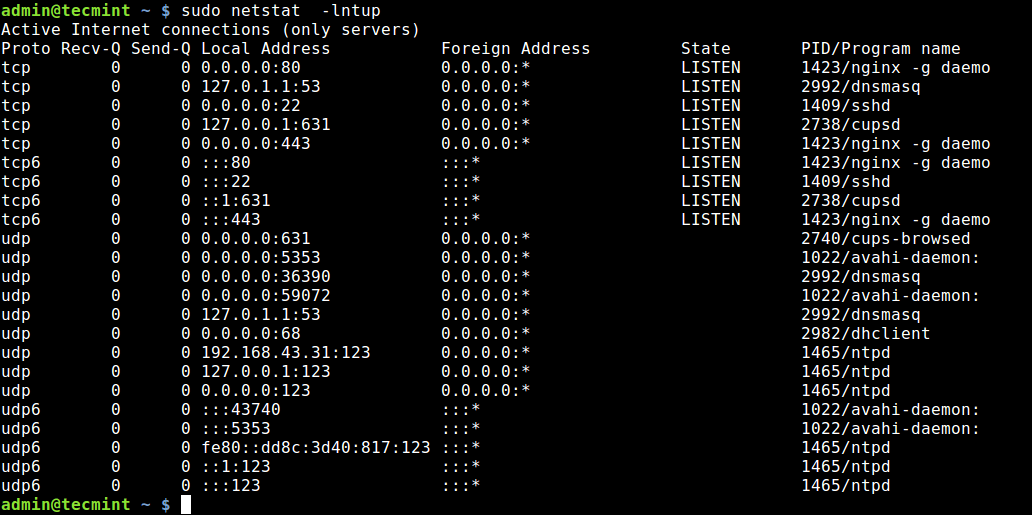
Netstat is a widely used tool for querying information about the Linux networking subsystem. You can use it to print all open ports like this:
The flag -l tells netstat to print all listening sockets, -t shows all TCP connections, -u displays all UDP connections and -p enables printing of application/program name listening on the port.
To print numeric values rather than service names, add the -n flag.
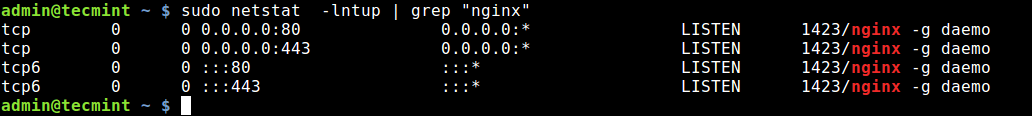
You can also use grep command to find out which application is listening on a particular port, for example.
$ sudo netstat -lntup | grep "nginx"
Alternatively, you can specify the port and find the application bound to, as shown.
$ sudo netstat -lntup | grep ":80"
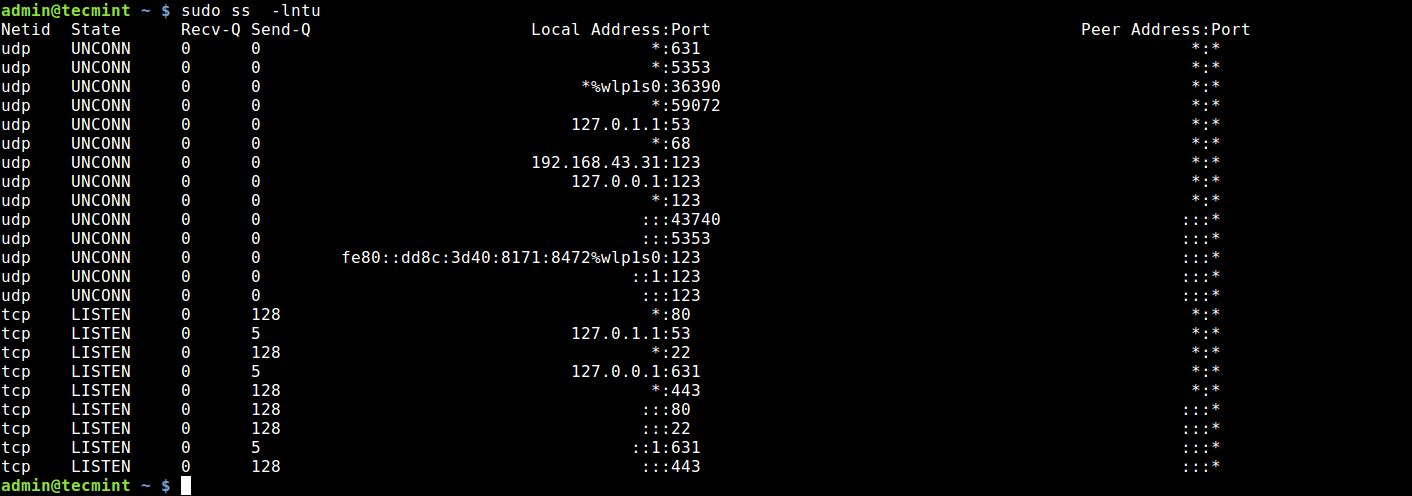
2. Using ss Command
ss command is another useful tool for displaying information about sockets. It’s output looks similar to that of netstat. The following command will show all listening ports for TCP and UDP connections in numeric value.
3. Using Nmap Command
Nmap is a powerful and popular network exploration tool and port scanner. To install nmap on your system, use your default package manager as shown.
$ sudo apt install nmap [On Debian/Ubuntu] $ sudo yum install nmap [On CentOS/RHEL] $ sudo dnf install nmap [On Fedora 22+]
To scan all open/listening ports in your Linux system, run the following command (which should take a long time to complete).
$ sudo nmap -n -PN -sT -sU -p- localhost
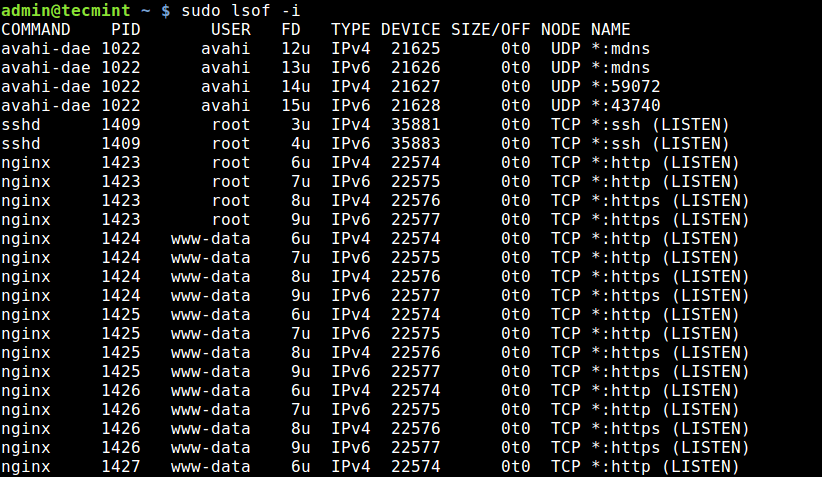
4. Using lsof Command
The final tool we will cover for querying open ports is lsof command, which is used to list open files in Linux. Since everything is a file in Unix/Linux, an open file may be a stream or a network file.
To list all Internet and network files, use the -i option. Note that this command shows a mix of service names and numeric ports.
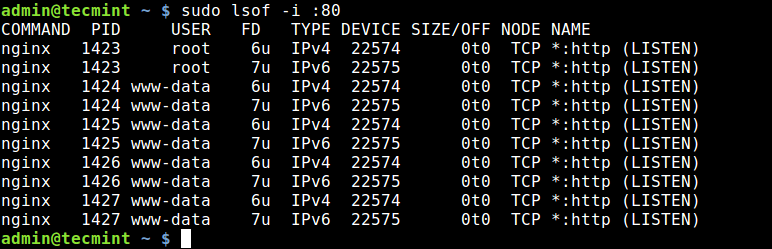
To find which application is listening on a particular port, run lsof in this form.
That’s all! In this article, we have explained four ways to check open ports in Linux. We also showed how to check which processes are bound upon particular ports. You can share your thoughts or ask any questions via the feedback form below.
Check if port is open or closed on a Linux server?
It’s not quite clear what you’re asking. What do you mean by «open»? Do you mean some server is listening on that port? Or do you mean it’s allowed by the system firewall? Or what?
nc -w5 -z -v
A topic that contains an answer also for kernel level services and programs serverfault.com/questions/1078483/…
8 Answers 8
You can check if a process listens on a TCP or UDP port with netstat -tuplen .
To check whether some ports are accessible from the outside (this is probably what you want) you can use a port scanner like Nmap from another system. Running Nmap on the same host you want to check is quite useless for your purpose.
GNU netstat knows the parameters -t , -u , -p , -l , -e , and -n . Thanks to the options parser it can be expressed as -tuplen . linux.die.net/man/8/netstat
Also, the telnet command usually does only supports TCP, so you’re out of luck if the service you want to check runs on another protocol.
According to article: computingforgeeks.com/netstat-vs-ss-usage-guide-linux netstat is deprecated, and ss is it’s replacement, so you can do ss -an , ss -tuplen or for tcp listening sockets ss -ntlp .
Quickest way to test if a TCP port is open (including any hardware firewalls you may have), is to type, from a remote computer (e.g. your desktop):
Which will try to open a connection to port 80 on that server. If you get a time out or deny, the port is not open 🙂
OK, in summary, you have a server that you can log into. You want to see if something is listening on some port. As root, run:
this will show a listing of processes listening on TCP and UDP ports. You can scan (or grep) it for the process you’re interest in,and/or the port numbers you expect to see.
If the process you expect isn’t there, you should start up that process and check netstat again. If the process is there, but it’s listening on a interface and port that you did not expect, then there’s a configuration issue (e.g., it could be listening, but only on the loopback interface, so you would see 127.0.0.1:3306 and no other lines for port 3306, in the case of the default configuration for MySQL).
If the process is up, and it’s listening on the port you expect, you can try running a «telnet» to that port from your Macbook in your office/home, e.g.,
telnet xxxxxxxxxxxx.co.uk 443 That will test if (assuming standard ports) that there’s a web server configured for SSL. Note that this test using telnet is only going to work if the process is listening on a TCP port. If it’s a UDP port, you may as well try with whatever client you were going to use to connect to it. (I see that you used port 224. This is masqdialer, and I have no idea what that is).
If the service is there, but you can’t get to it externally, then there’s a firewall blocking you. In that case, run:
This will show all the firewall rules as defined on your system. You can post that, but, generally, if you’re not allowing everything on the INPUT chain, you probably will need to explicitly allow traffic on the port in question:
iptables -I INPUT -p tcp --dport 224 -j ACCEPT or something along those lines. Do not run your firewall commands blindly based on what some stranger has told you on the Internet. Consider what you’re doing.
If your firewall on the box is allowing the traffic you want, then your hosting company may be running a firewall (e.g., they’re only allowing SSH (22/tcp), HTTP (80/tcp) and HTTPS (443/tcp) and denying all other incoming traffic). In this case, you will need to open a helpdesk ticket with them to resolve this issue, though I suppose there might be something in your cPanel that may allow it.