- 5.3. Viewing the Current Status and Settings of firewalld
- 5.3.2. Viewing Current firewalld Settings
- 5.3.2.1. Viewing Allowed Services using GUI
- 5.3.2.2. Viewing firewalld Settings using CLI
- How to configure firewalld quickly
- Great Linux resources
- How do you check the firewalld status?
- How do you check the current configuration?
- How do you open a port?
- How do you close a port?
- How do you make the firewall settings persistent?
- How do you reload the configuration?
- Kubernetes and OpenShift
- Learn more
- How do I know if my firewall is on?
- 5 Answers 5
- How to Check Firewall Status in Ubuntu Firewall
- Display firewall rule numbers
- Filter Firewall status with grep command
- Example : Display default firewall policy
- Example : Filter the by specific port
5.3. Viewing the Current Status and Settings of firewalld
The firewall service, firewalld , is installed on the system by default. Use the firewalld CLI interface to check that the service is running.
~]# systemctl status firewalld firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor pr Active: active (running) since Mon 2017-12-18 16:05:15 CET; 50min ago Docs: man:firewalld(1) Main PID: 705 (firewalld) Tasks: 2 (limit: 4915) CGroup: /system.slice/firewalld.service └─705 /usr/bin/python3 -Es /usr/sbin/firewalld --nofork --nopid Furthermore, it is important to know how firewalld is set up and which rules are in force before you try to edit the settings. To display the firewall settings, see Section 5.3.2, “Viewing Current firewalld Settings”
5.3.2. Viewing Current firewalld Settings
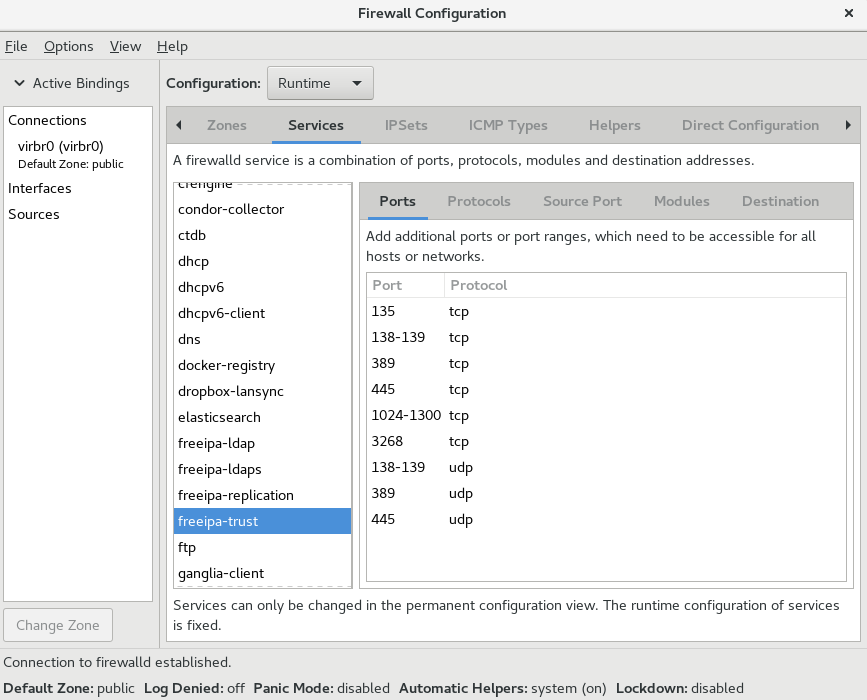
5.3.2.1. Viewing Allowed Services using GUI
To view the list of services using the graphical firewall-config tool, press the Super key to enter the Activities Overview, type firewall , and press Enter . The firewall-config tool appears. You can now view the list of services under the Services tab.
Alternatively, to start the graphical firewall configuration tool using the command-line, enter the following command:
The Firewall Configuration window opens. Note that this command can be run as a normal user, but you are prompted for an administrator password occasionally.
Figure 5.2. The Services tab in firewall-config
5.3.2.2. Viewing firewalld Settings using CLI
With the CLI client, it is possible to get different views of the current firewall settings. The —list-all option shows a complete overview of the firewalld settings.
firewalld uses zones to manage the traffic. If a zone is not specified by the —zone option, the command is effective in the default zone assigned to the active network interface and connection.
~]# firewall-cmd --list-all public target: default icmp-block-inversion: no interfaces: sources: services: ssh dhcpv6-client ports: protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: To specify the zone for which to display the settings, add the —zone=zone-name argument to the firewall-cmd —list-all command, for example:
~]# firewall-cmd --list-all --zone=home home target: default icmp-block-inversion: no interfaces: sources: services: ssh mdns samba-client dhcpv6-client . [output truncated] To see the settings for particular information, such as services or ports, use a specific option. See the firewalld manual pages or get a list of the options using the command help:
~]# firewall-cmd --help Usage: firewall-cmd [OPTIONS. ] General Options -h, --help Prints a short help text and exists -V, --version Print the version string of firewalld -q, --quiet Do not print status messages Status Options --state Return and print firewalld state --reload Reload firewall and keep state information . [output truncated] ~]# firewall-cmd --list-services ssh dhcpv6-client Listing the settings for a certain subpart using the CLI tool can sometimes be difficult to interpret. For example, you allow the SSH service and firewalld opens the necessary port (22) for the service. Later, if you list the allowed services, the list shows the SSH service, but if you list open ports, it does not show any. Therefore, it is recommended to use the —list-all option to make sure you receive a complete information.
How to configure firewalld quickly
Learn the basic commands to check your firewall’s configuration, add or remove rules, and reload settings.
This article covers the fundamental tasks necessary to configure the firewalld service quickly. I’ll assume you already appreciate the importance of a firewall and have a general understanding of how firewalls protect servers and workstations.
Great Linux resources
These are the steps for configuring this firewall:
- Check its current status
- Check its configuration
- Open a port
- Close a port
- Make the settings persistent
- Reload the firewall configuration
To help you find the information you need, I’ve organized the article in a How do you? format that addresses these steps. Simply scroll down to your question and find the commands. If you need more detail on managing firewalld , read Shashank Nandishwar Hegde’s article An introduction to firewalld rules and scenarios.
How do you check the firewalld status?
First, ensure the firewalld service is installed, started, and enabled:
$ sudo systemctl status firewalld $ sudo systemctl start firewalld $ sudo systemctl enable firewalldStarting a service activates it for the current runtime, whereas enabling a service causes it to start when the system boots.
How do you check the current configuration?
To display the services or ports currently open on the firewall for the public zone, type:
$ sudo firewall-cmd --list-all --zone=publicNotice the zone and the services or ports. The zone is a configuration related to a specific location or server role.
If desired, you can display the open ports by service or port number:
$ sudo firewall-cmd --list-services $ sudo firewall-cmd --list-ports[ Help your colleagues understand containers and hybrid cloud. Download How to explain orchestration in plain English. ]
How do you open a port?
If the existing firewall configuration blocks a service you need, open the appropriate port. You can specify it by service name if it’s a common service. However, if the service is uncommon, developed in-house, or uses a custom port number, you can open the firewall port by port number. Here are two examples for web services:
$ sudo firewall-cmd --zone=public --add-service=http $ sudo firewall-cmd --zone=public --add-port=80/tcpNote the use of /tcp (or /udp , depending on the protocol).
This configuration is non-persistent. As noted below, you’ll need the —permanent flag to persist the settings.
Use the —list-services or —list-ports option to verify the settings.
[ Dowload the firewall cheat sheet to keep the necessary commands close at hand. ]
How do you close a port?
It’s also possible that an open port represents a no-longer-installed service on the system or that it should be closed for some other reason. Close ports by service name or port number by using these commands:
$ sudo firewall-cmd --zone=public --remove-service=http $ sudo firewall-cmd --zone=public --remove-port=80/tcpAgain, with the above commands, this configuration is non-persistent.
How do you make the firewall settings persistent?
The —permanent option makes the firewall changes persist through reboots. You can integrate the flag into the configuration commands:
$ sudo firewall-cmd --permanent --zone=public --add-port=80/tcpHow do you reload the configuration?
Finally, reload the firewall to integrate your changes into the current runtime. Do this as a separate step following the configuration changes:
Kubernetes and OpenShift
One note regarding restart versus reload : Linux reads configuration files during the boot process, so what do you need to do when changing a configuration file? The obvious answer is to reboot the server, causing the system to reread the configuration file and implement the new changes. A reboot is often a bad idea (causing downtime), so you may choose to restart a service ( systemctl restart sshd ).
However, the problem with restarting a service is that it drops existing connections. In many cases, a better alternative is to reload the service, which rereads the config file but does not drop existing connections, and therefore there is no interruption in service.
Learn more
The importance of a firewall is an established fact. This article provides the basic commands necessary to quickly check the configuration, add or remove rules, and reload the settings. You can check the Red Hat documentation for details on additional configurations, using various zones, port forwarding, and more.
How do I know if my firewall is on?
I installed Firestarter, and configured my firewall. But I’m in doubt : On boot, I sometimes see a [FAIL] marker, and to the left, I guess it was something like «start firewall». I can’t be sure because the message is seen for less than a second, so I wanted to know if there is a way, without starting the whole firestarter software, to know if the firewall is on and working, or not. Either a gadget, or better, some console instruction, the exact name of the firewall process/daemon, or bash script, will do. Edit: I already tested my computer with the «Shield’s Up» http://www.grc.com feature, which marks my computer as «Stealth», but as I am behind a router, I’m not surprised. Still, apparently, my computer answers to pings. Strange.
This question appears to be abandoned, if you are experiencing a similar issue please ask a new question with details pertaining to your problem. If you feel this question is not abandoned, please flag the question explaining that. 🙂
This question has helpful, upvoted answers and consequently is not abandoned. It should be reopened.
5 Answers 5
There are basically 2 ways of seeing if the firewall is configured. You should use both of the methods and verify that the firewall is both configured and configured the way you wish it to be.
First, check that the firewall rules have been applied. Pretty much all modern Linux firewall solutions use iptables for firewall. You can see that there are rules in place with iptables command:
This will return the current set of rules. There can be a few rules in the set even if your firewall rules haven’t been applied. Just look for lines that match your given rulesets. This will give you an idea of what rules have been entered to the system. this doesn’t guarantee the validity of the rules, only that they have been understood.
Next, you will use a second computer to test for connections against the host in question. This can be easily done with the nmap command (found in nmap package). Quick and dirty way of checking is:
nmap -P0 10.0.0.10 nmap -P0 -sU 10.0.0.10 Replace the IP address 10.0.0.10 with your destination hosts IP address.
The first line will scan for TCP ports that are open and available from the second computer. Second line will repeat the scan but this time with UDP ports. -P0 flag will prevent the host from being tested with a ICMP Echo packet, but might be blocked by your firewall rules.
The scan might take a while so be patient. There is also a GUI frontend for nmap called zenmap which makes it a bit easier to interpret the scan results if there is a lot of output.
How to Check Firewall Status in Ubuntu Firewall
In the last lesson we learned how to enable and disable Ubuntu Firewall in Ubuntu Linux. In This tutorial we are going to learn how to check the firewall status in Ubuntu UFW.
To check firewall status use the ufw status command in the terminal.
If the firewall is enabled, you will see the list of firewall rules and the status as active. If the firewall is disabled, you will get the message “Status: inactive”.
For more detailed status use verbose option with ufw status command.
Verbose option displays additional settings including default firewall settings.
Display firewall rule numbers
The numbered option of the ufw status command will display the rule number.
Once we know the rule number, We can use rule number to modify existing firewall rules. For example, I can delete the firewall rule number by typing
Filter Firewall status with grep command
The Linux grep command will help us to filter the output of the ufw status command.
Example : Display default firewall policy
sudo ufw status verbose | grep -i default
Example : Filter the by specific port
Rules related to the ssh port 22 will be displayed
sudo ufw status | grep -i deny
This time we filter the status to display firewall rules that have configured to deny connections. As per above screenshot you can see we have block TCP port 80 from the Ubuntu firewall.