How to close ports in Linux?
It will show the list of processes with port number and process id the number before is a process id. Now use command to kill the process implies the process will be killed forcefully. Solution 4: Option 1 A One-liner to kill only LISTEN on specific port: Option 2 If you have npm installed you can also run Question: Posix requires changing RTS pin on port opening.
How to close ports in Linux?
I have some question in closing port, I think I got some strange things.
nmap --top-ports 10 192.168.1.1 it shows that 23/TCP port is open.
nmap --top-ports 10 localhost it show that 23/tcp port is closed.
Which of them is true? I want to close this port on my whole system, how can I do it?
Nmap is a great port scanner, but sometimes you want something more authoritative. You can ask the kernel what processes have which ports open by using the netstat utility:
me@myhost:~$ sudo netstat -tlnp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 1004/dnsmasq tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 380/sshd tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 822/cupsd tcp6 0 0 . 22 . * LISTEN 380/sshd tcp6 0 0 ::1:631 . * LISTEN 822/cupsd
The options I have given are:
- -t TCP only
- -l Listening ports only
- -n Don’t look up service and host names, just display numbers
- -p Show process information (requires root privilege)
In this case, we can see that sshd is listening on any interface ( 0.0.0.0 ) port 22, and cupsd is listening on loopback ( 127.0.0.1 ) port 631. Your output may show that telnetd has a local address of 192.168.1.1:23 , meaning it will not answer to connections on the loopback adapter (e.g. you can’t telnet 127.0.0.1 ).
There are other tools that will show similar information (e.g. lsof or /proc ), but netstat is the most widely available. It even works on Windows ( netstat -anb ). BSD netstat is a little different: you’ll have to use sockstat(1) to get the process information instead.
Once you have the process ID and program name, you can go about finding the process and killing it if you wish to close the port. For finer-grained control, you can use a firewall (iptables on Linux) to limit access to only certain addresses. You may need to disable a service startup. If the PID is «-» on Linux, it’s probably a kernel process (this is common with NFS for instance), so good luck finding out what it is.
Note: I said «authoritative» because you’re not being hindered by network conditions and firewalls. If you trust your computer, that’s great. However, if you suspect that you’ve been hacked, you may not be able to trust the tools on your computer. Replacing standard utilities (and sometimes even system calls) with ones that hide certain processes or ports (a.k.a. rootkits) is a standard practice among attackers. Your best bet at this point is to make a forensic copy of your disk and restore from backup; then use the copy to determine the way they got in and close it off.
To «close» the port you can use iptables
sudo iptables -A INPUT -p tcp --dport 23 -m state --state NEW,ESTABLISHED -j DROP A Linux system has a so called loopback interface, which is for internal communication. Its hostname is localhost and its IP address is 127.0.0.1 .
When you run nmap on localhost , you actually run the portscan on the virtual loopback interface. 192.168.1.1 is the IP address of your physical (most likely eth0 ) interface.
So you’ve run nmap on two different network interfaces, this is why there’s a difference in the open ports. They are both true.
If you have TCP port 23 open, it is likely that you have a telnet server running (which is not a good thing due to its lack of encryption) or you have some kind of trojan horse on your machine.
If you do nmap localhost , it tells you about a different situation: some programs on linux work as server although they are used only locally. This is because other programs use them like a server they connect to. So both answers are true, since you ask something different.
Port 23 is used for telnet. Normally not used anymore. Try to do nmap -sV 192.168.1.1 to find out which program opens the port.
(192. is a local network IP, so the result of nmap will also give a different result, because of possible firewall settings etc)
Tcp — How do I reserve ports for my application?, 3 Answers Sorted by: 26 To ensure the kernel won’t give out 49000 and 49001 to clients as you wish to use them for your servers on linux. sysctl -w net.ipv4.ip_local_reserved_ports = 49000, 49001 drop it in /etc/sysctl.conf, and then run sysctl -p. Note that this is untested. References Documentation / networking …
How to Find and Close Open Ports in Linux
Network and Server administration is one of the key areas in which Linux is actually preferred to any other operating system. Hence most data center admins are well versed with the Linux command line.
There can be scenarios when certain ports on a server, which were required to be closed, are open and causing unexpected traffic on the server.
Today, we will learn how to find and close an open port in Linux.
Finding Open Ports in Linux
For finding the open ports, we will make use of the ss command, which is preinstalled in most common Linux distributions and it is now the replacement for the previously very popular netstat command.
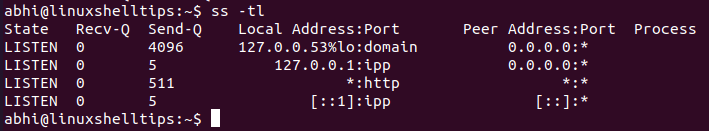
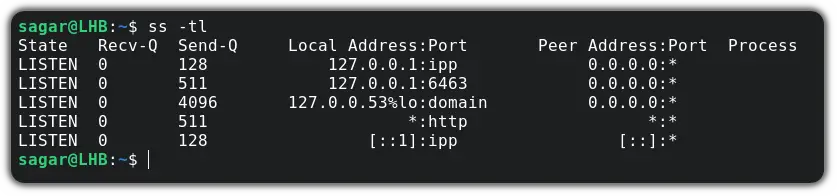
Let’s run the ss command with the following syntax, to get all listening TCP sockets:
Here, the ‘t’ stands for TCP and the ‘l’ stands for Listening sockets.
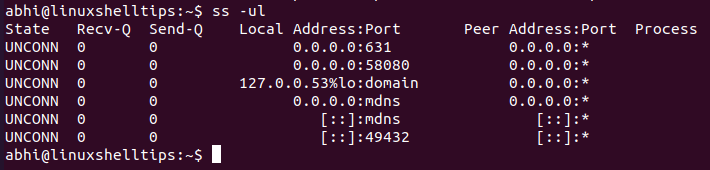
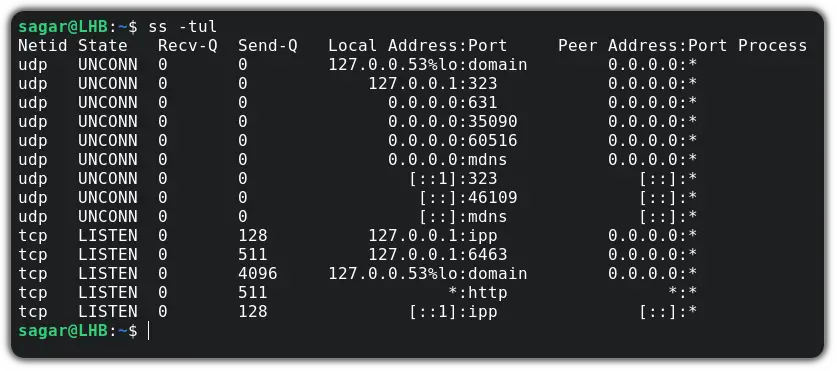
Similarly to get all listening UDP ports, run:
Observe the output. In the ‘State‘ column for UDP, all the ports have state UNCONN, i.e., unconnected. Since we only need the ports which are actively listening, we pipe the output and filter it with the grep command.
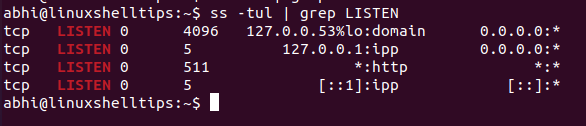
We can also combine the TCP and UDP output together.
Another addition that can be done here is: the argument ‘-n’ . In the output above, the command is resolving the name of the service associated with a port: Eg. HTTP, IPP, etc.
With the argument ‘-n’ it just shows the port number which is listening.
Closing Open Ports in Linux
The manual way to close an open port in Linux is quite tedious and programmatic. Hence, we will use the easier approach: to close the processes which are listening on the port.
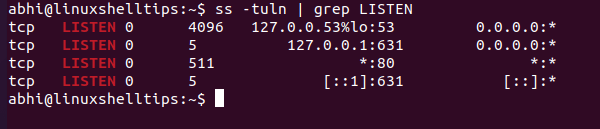
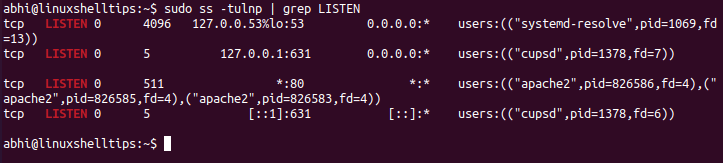
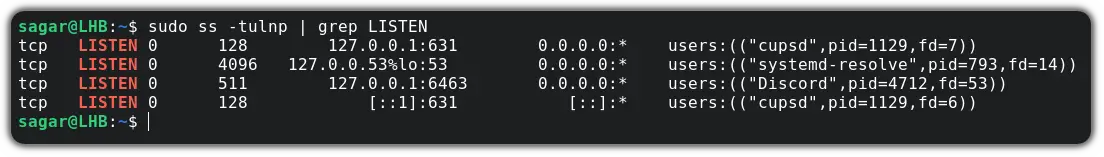
We need to call ss with another argument, ‘-p’ to list the process which is using each port (run the command as a sudo user).
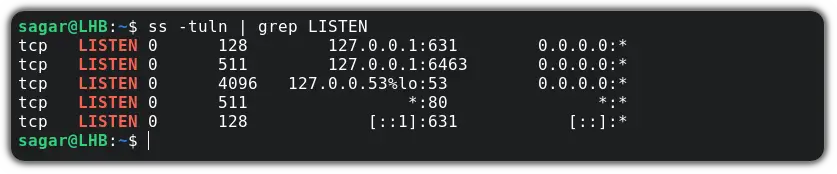
$ sudo ss -tulnp | grep LISTEN
As shown above, the last column lists the ‘users’, i.e., the processes which use the port number. Now you can close the port by terminating the process using it. For example, to close port 80, we have to stop the process ‘Apache2’.
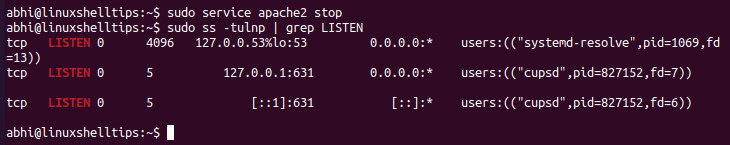
$ sudo service apache2 stop OR $ sudo systemctl stop apache2
Thus, we have successfully closed port 80 and no process is listening on it any longer.
Conclusion
In this article, we learned how to find and close an open port in Linux. Many ports like 22 (SSH), 21 (Telnet), etc. should be kept closed at most times, as these are the ports from which cyber attacks can arise.
Other ports should also be closed when the process of using them is no longer required. Thanks for reading and let us know your thoughts in the comments below!
How to Find Open Ports and Close Them in Linux
Troubleshooting networks? Here’s how to find the open ports and close those open ports in the Linux command line.
So you are dealing with a critical server where you have to maintain security at any cost. And closing ports to block unwanted traffic is the first step you’d take.
Find open ports in Linux
In this tutorial, I am going to use the ss command to find open ports.
You can use the -l option with the ss command to get listening ports. But to be more specific, I’m going with -lt to get listening TCP ports:
Similarly, if you want to have a list of both TCP and UDP in the listening state, you can use the given command:
And to get the listening port of each service, you can use -n and for more fine-tuned results, you can always use the grep command:
Enough of finding open ports, let’s jump to how you can close them.
Close open ports in Linux
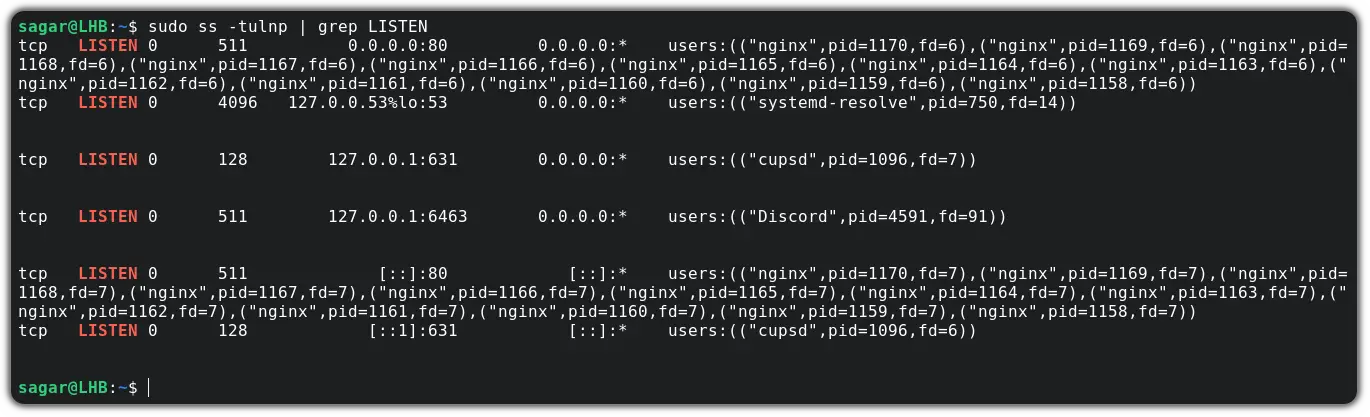
To close the port, first, you will need to stop the service and to find the service name, you can use the same ss command with -p option:
sudo ss -tulnp | grep LISTENAs you can see, the NGINX is utilizing port number 80. So let’s stop it using the given command:
sudo systemctl stop nginxAs it will enable itself on every boot and you can alter this behavior using the given command:
sudo systemctl disable nginxFor better results, I would recommend changing firewall rules.
Here, I’m going to block port no 80 (used by NGINX) in UFW (which is pre-installed in Ubuntu).
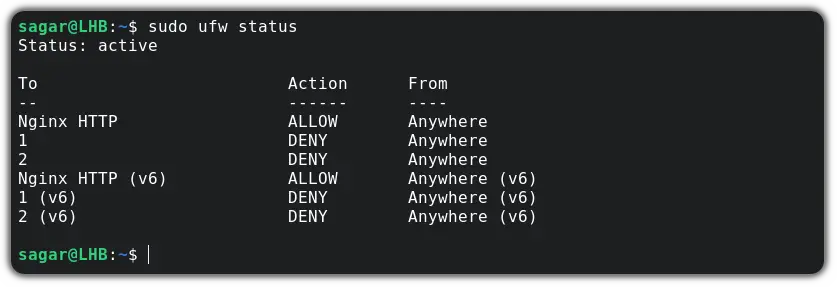
First, let’s check the status of UFW:
And if it shows inactive , you can use the given command to enable it:
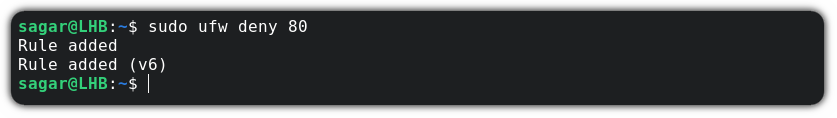
Now, you just have to pair the deny option with the port number :
Wrapping Up
This was my take on how you can find and close open ports in Linux. I hope you will find this helpful.
And if you have any queries, let me know in the comments.