Kali Linux: Top 5 tools for password attacks
These are five great tools for password attacks from Kali Linux. By learning how to crack passwords with Kali, you not only learn how to break into systems, but you also get the skills necessary for defending against these types of attacks.
There are many other tools available in Kali Linux that can help with this type of attack, so don’t be afraid to explore them.
These are the most commonly used tools for password attacks in Kali Linux.
1. John the Ripper
John the Ripper can be used to crack passwords from text files and word lists, also known as password dictionaries. It’s often one of the most important tools that anyone who wants to break into systems will need for performing password attacks.
John the Ripper is a great place to start if you’re interested in learning how to perform these types of attacks on your own system or by using one of Kali Linux’s virtual machines.
For John the Ripper to work, it needs both text files and word lists that contain passwords.
The number of passwords available in your dictionary or word list will determine the size of the file, so the bigger the file, the more passwords it will contain.
After you’ve compiled the text files and word lists that contain passwords, simply pass them to John for processing.
Once a password has been identified as matching one of your texts or word lists, John will print out the username it belonged to and how many times it appeared in your list.
2. Hydra
Among the password cracking programs available, Hydra can be used to brute force passwords. It has many advantages over John the Ripper, but it’s slower and requires more processing power from your system to work correctly.
Hydra is just as straightforward as most of Kali Linux’s tools: simply launch it with a wordlist and start guessing passwords until one works. Hydra will take longer to crack a long password than it will to crack a shorter one, so the length of the password can make a big difference.
Hydra uses parallelization to perform its login cracker tasks. It is capable of attacking numerous protocols. It utilizes multiple CPUs and can significantly reduce the time it takes to recover passwords from encrypted wireless networks, WPA/WPA2 protected access points and even heavily firewalled corporate LANs.
Using Hydra, researchers can demonstrate the ease of gaining unauthorized access to a system remotely in a very short space of time, sometimes in mere minutes. This can be a real wake-up call for users that do not use proper password security measures.
3. Cain & Abel
Cain is a Windows password recovery tool that can search and crack various password hashes and filter net packets using methods, including network packet sniffing.
Cain can often be used by computer forensics experts to decrypt an NT LAN Manager (NTLM) hash, which encrypts time-sensitive information between client computers and servers like Active Directory or LDAP servers to verify credentials.
Cain can be used in many different ways, making it a very handy tool to have as part of your toolkit. It’s been designed with these four major features in mind: NetWare LAN Manager/Windows NT LM Hashes Cracker, Rainbow Table Generator, Offline NT Password & Registry Editor and Salted Hash Keeper.
You can test many different types of systems with Cain & Abel, so it is definitely worth becoming familiar with them.
4. Ophcrack
Ophcrack is a tool that can be used for breaking Windows passwords. This is a free, open-source tool that can recover all the hashes of the SAM (security accounts manager) registry key in older versions and LM Hashes in more recent ones.
This program runs by mapping out what’s called rainbow tables to get you access to your password. Accelerating a process is achieved by using graphics processing units, or GPUs. These are the same graphics cards that are used for gaming and 3D design.
The first thing you need to do is select your Windows version and then download the rainbow tables for that specific version of Windows. Once this has been done, it will take about an hour or so for Ophcrack to finish running through its calculations with GPUs.
This is much quicker than traditional CPU-bound tools because graphics cards are capable of dealing with advanced mathematical calculations very quickly.
5. Hashcat
The world’s fastest password hacking utility, Hashcat supports five different types of attack in conjunction with more than 200 hashing algorithms. Hashcat can be used to crack passwords by leveraging hardware on computer systems such as GPUs for added speed.
There are many ways to attack passwords such as brute-force, cracking the hashes with wordlists and rainbow tables.
Currently, Hashcat can be used with computer components like CPUs and GPUs. It also has multiple OS support with Linux, Windows and OSX, as well as the ability to enable distributed password cracking.
Some of the hash types that can be cracked with Hashcat are md512, MDBMZ (Mdaij), Windows LM Hashes and Cisco Type-based Password Lists. The support for these hashes is constantly growing and we will update as new algorithms get added to the program.
Where would a password cracking tool be useful?
In your daily tasks as a cybersecurity professional, you may be asked to help a client identify the password of an email account or social media profile.
It’s important to understand that all passwords have strengths and weaknesses, so it is not enough just to try guessing them until you find the right one.
You will need tools like John the Ripper to crack those types of passwords to access a machine like this.
The John the Ripper tool is very powerful and it’s easy to use, which makes it perfect for everyday penetration testers.
Exploring Kali Linux password attack tools
Now that you know which tools are available in Kali for password cracking, you can start to try them out for yourself. It is satisfying when you finally gain access to a test machine that you thought you couldn’t crack, and learning how these tools work will help you to validate your theoretical knowledge with tangible, real world results.
Password attacks are a common way to break into systems, so you must be aware of what types of tools are available and how they work. Kali Linux is an operating system that has many tools for performing these types of attacks, which can be found in this post if you’re interested in learning.
The key takeaway here is that you will be able to identify telltale signs of password cracking attempts on computer systems if you practice these techniques yourself.
Kali Linux — Password Cracking Tools
In this chapter, we will learn about the important password cracking tools used in Kali Linux.
Hydra
Hydra is a login cracker that supports many protocols to attack ( Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP).
To open it, go to Applications → Password Attacks → Online Attacks → hydra.
It will open the terminal console, as shown in the following screenshot.
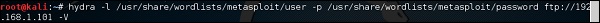
In this case, we will brute force FTP service of metasploitable machine, which has IP 192.168.1.101
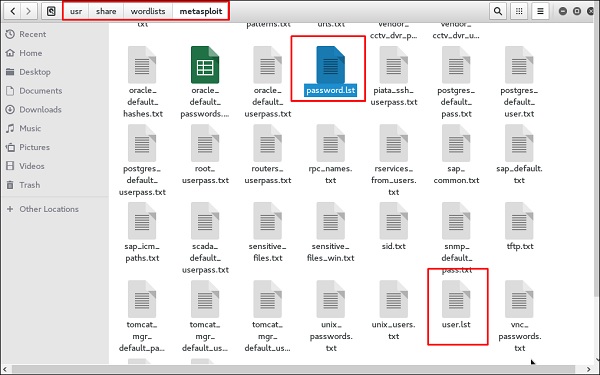
We have created in Kali a word list with extension ‘lst’ in the path usr\share\wordlist\metasploit.
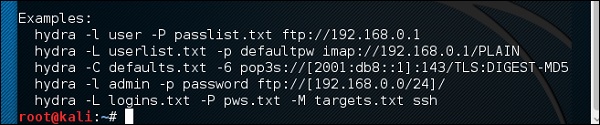
The command will be as follows −
hydra -l /usr/share/wordlists/metasploit/user -P /usr/share/wordlists/metasploit/ passwords ftp://192.168.1.101 –V
where –V is the username and password while trying
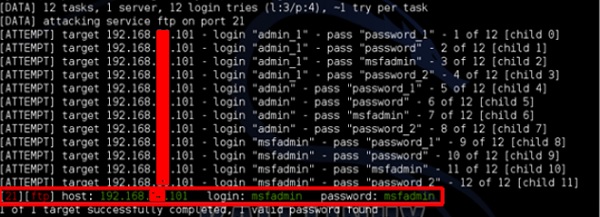
As shown in the following screenshot, the username and password are found which are msfadmin:msfadmin
Johnny
Johnny is a GUI for the John the Ripper password cracking tool. Generally, it is used for weak passwords.
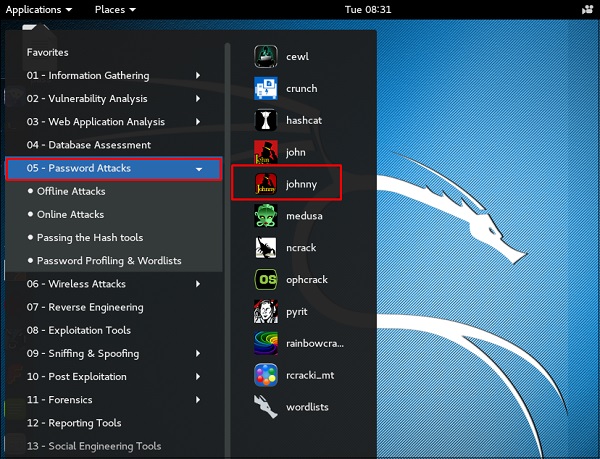
To open it, go to Applications → Password Attacks → johnny.
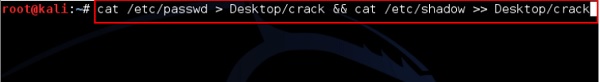
In this case, we will get the password of Kali machine with the following command and a file will be created on the desktop.
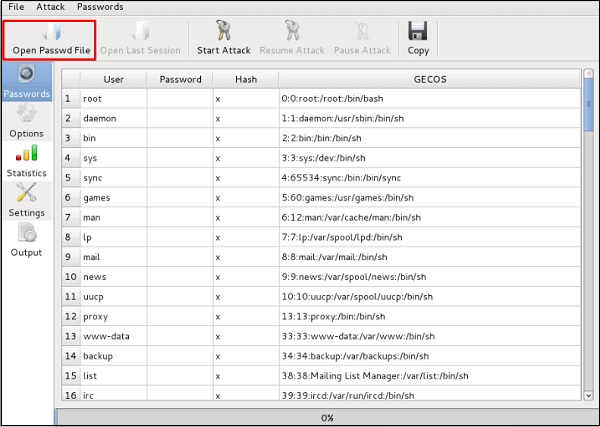
Click “Open Passwd File” → OK and all the files will be shown as in the following screenshot.
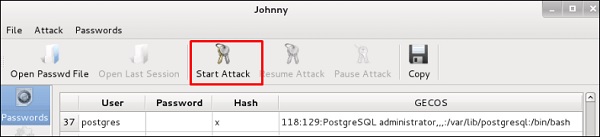
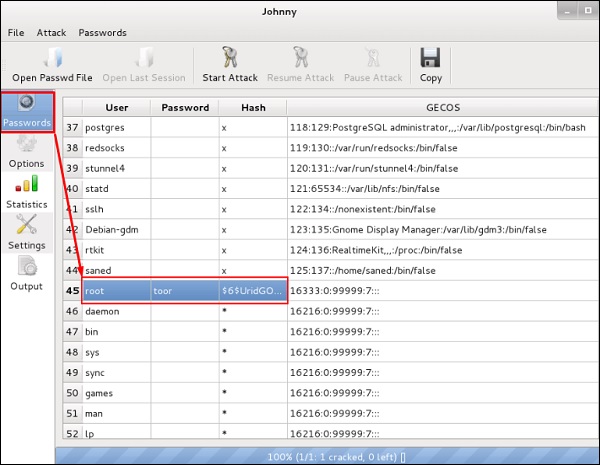
After the attack is complete, click the left panel at “Passwords” and the password will be unshaded.
John
john is a command line version of Johnny GUI. To start it, open the Terminal and type “john”.
In case of unshadowing the password, we need to write the following command −
root@kali:~# unshadow passwd shadow > unshadowed.txt
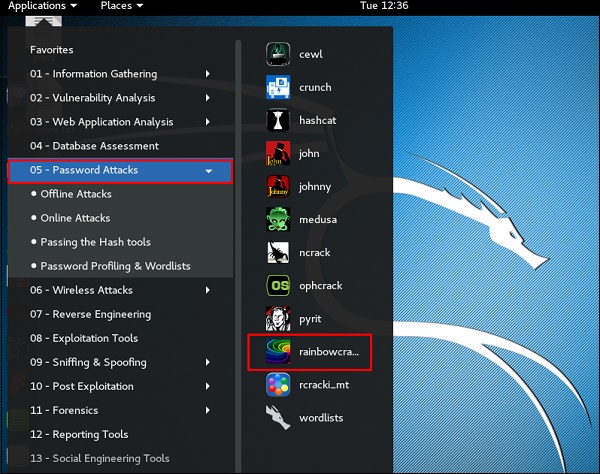
Rainbowcrack
The RainbowCrack software cracks hashes by rainbow table lookup. Rainbow tables are ordinary files stored on the hard disk. Generally, Rainbow tables are bought online or can be compiled with different tools.
To open it, go to Applications → Password Attacks → click “rainbowcrack”.
The command to crack a hash password is −
rcrack path_to_rainbow_tables -f path_to_password_hash
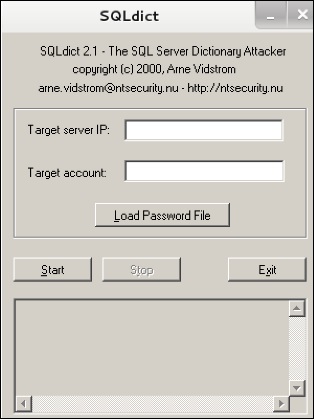
SQLdict
It is a dictionary attack tool for SQL server and is very easy and basic to be used. To open it, open the terminal and type “sqldict”. It will open the following view.
Under “Target IP Server”, enter the IP of the server holding the SQL. Under “Target Account”, enter the username. Then load the file with the password and click “start” until it finishes.
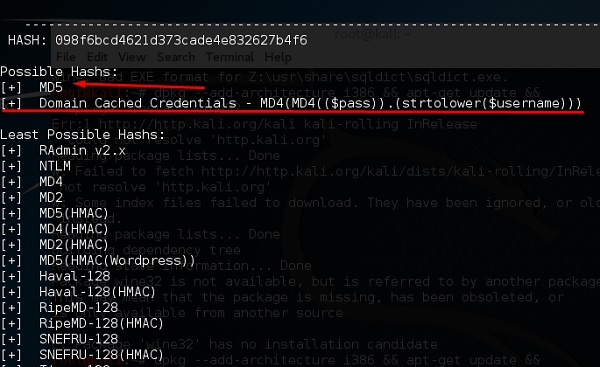
hash-identifier
It is a tool that is used to identify types of hashes, meaning what they are being used for. For example, if I have a HASH, it can tell me if it is a Linux or windows HASH.
The above screen shows that it can be a MD5 hash and it seems a Domain cached credential.