- How To Allow or Deny SSH Root Login in Linux
- Deny SSH Access to a User or Group
- Disable SSH Access for Root User
- Conclusion
- How to Disable SSH Login to Specific User in Linux
- Disable SSH Access to User
- Disable SSH Root Access
- Disable or Enable SSH Root Login and Limit SSH Access in Linux
- Disable SSH Root Login
- Enable SSH Root Login
- Limit SSH User Logins
How To Allow or Deny SSH Root Login in Linux
If you want to allow SSH access for one or two particular users from the remote Linux or Unix server, and you need to edit the configuration file named sshd_config under /etc/ssh directory using your vi/vim text editor:
$ sudo vim /etc/ssh/sshd_config
then adding the following line into the file:
AllowUsers devops devops01
If you want to allow an entire group for SSH Access, and you can edit the configuration file /etc/ssh/sshd_config using vim text editor:
$ sudo vim /etc/ssh/sshd_config
add the following line into the file:
Then those users who are in the “ devops ” group can be able to ssh access from the remote server.
You need to restart SSHD service to take effect for changes by using the following command:
$ sudo systemctl restart sshd.service
Deny SSH Access to a User or Group
If you want to deny SSH access to a user or group, and you can edit the sshd_config file by adding the following lines:
$ sudo vim /etc/ssh/sshd_config
Adding the following lines:
DenyUsers devops DenyGroups devops
save and close the file and restart sshd service.
Disable SSH Access for Root User
If you want to disable SSH Access for root user, and you also need to edit /etc/ssh/sshd_config file using your vim text editor:
$ sudo vim /etc/ssh/sshd_config
find the following line and uncomment it, and set the value to no.
Save and close the file. and restart the sshd service with the following command:
$ sudo systemctl restart sshd
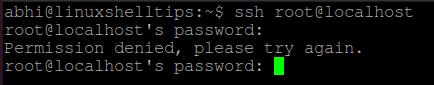
Let’s try to ssh to your server using root user, type:
devops@devops:~$ ssh root@192.168.3.50 The authenticity of host '192.168.3.50 (192.168.3.50)' can't be established. ECDSA key fingerprint is SHA256:dcUJtf8y1Wq2N+CD15pabodk9DhjpQI/RI7P5+5AhBI. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.3.50' (ECDSA) to the list of known hosts. root@192.168.3.50's password: Permission denied, please try again. root@192.168.3.50's password:
From the above outputs, you can see that you are not able to user root user to ssh to your server.
Conclusion
You should know that how to allow or deny ssh access to your server for root user or a particular user or group by modifying /etc/ssh/sshd_config file in your Linux system.
How to Disable SSH Login to Specific User in Linux
As you might already know, SSH (Secure Shell) is a network protocol for securely accessing a computer remotely. The server and client software in Linux are thereby known as SSH Server and SSH Client respectively and have many implementations.
By default, SSH allows you to log in to any user of the computer, as long as you have the password for the user. However, this comes with the same problem which is faced by any software using password-based authentication: an invitation for an attacker to exploit and gain admin access.
Today, we will see how to disable SSH login to a specific user, and more importantly, to the root user.
Disable SSH Access to User
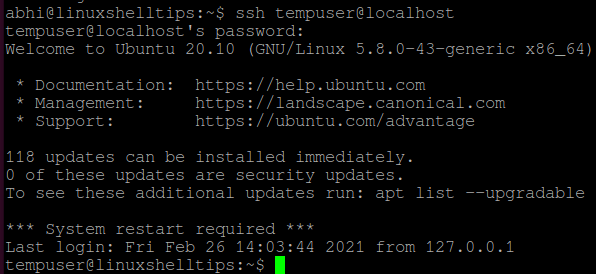
You can log in to a system using SSH with any user, using the following syntax:
Right now, SSH access is allowed on my machine for all users. Let us now deny access to a particular user called ‘tempuser‘.
Open file ‘/etc/ssh/sshd_config’ in any text editor.
$ sudo vim /etc/ssh/sshd_config
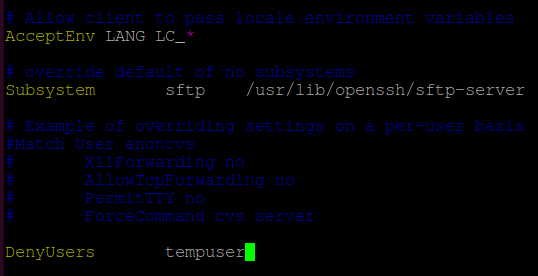
Add the following line at the end of the file:
Important: There is a ‘Tab‘ between ‘DenyUsers‘ and ‘tempuser‘ and not space. It won’t recognize the directive if you add a space.
Restart SSH server with the following command:
$ sudo systemctl restart sshd
If you are using a system that does not have SystemD, run:
$ sudo service sshd restart
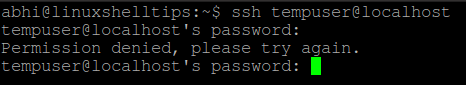
Now, try logging in to localhost with user ‘tempuser’ using SSH. It should show the error ‘Permission denied’, as displayed below:
Disable SSH Root Access
The same way described above can be used to disable login to a root user. However to disable complete root access, i.e., to disable access to all root users, follow the steps given below.
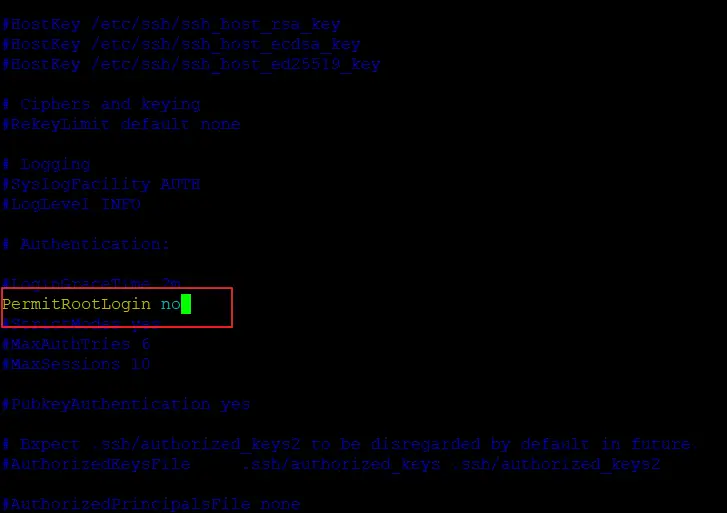
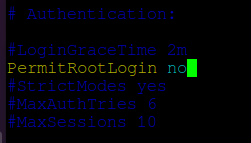
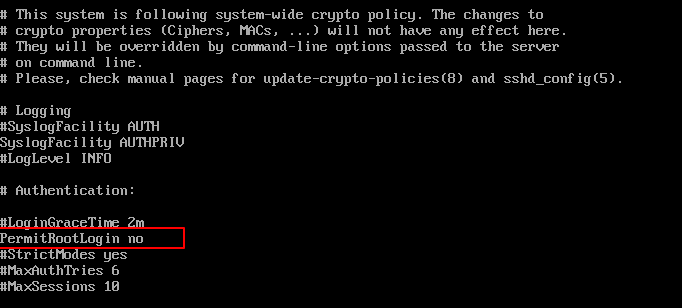
Open the file ‘/etc/ssh/sshd_config’ in any text editor and search for the string ‘PermitRootLogin’. Uncomment the line and if it has any other value, set the value to ‘no’.
Save and exit the file. Restart SSH with:
$ sudo systemctl restart sshd
Or if you are not having SystemD:
$ sudo service sshd restart
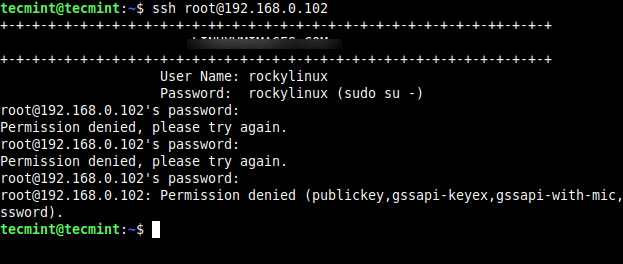
Now try logging in to localhost with user ‘root’. It will also show the error ‘Permission Denied’.
Conclusion
In this article, we learned how to disable SSH login access to a specific user. Restricting access to a Non-root user depends on individual scenarios, however, access to Root must be always restricted.
If there is a need for remote Root access, you should set up SSH with RSA authentication, which is more secure than password authentication. Read the man page of SSH (‘man ssh’) for more details.
Thanks for reading and let us know your thoughts in the comments section below!
Disable or Enable SSH Root Login and Limit SSH Access in Linux
Everyone knows that Linux systems come with root user access and by default, root access is enabled for the outside world.
For security reasons, it’s not a good idea to have ssh root access enabled for unauthorized users. Because any hacker can try to brute force your password and gain access to your system.
So, it’s better to have another account that you regularly use and then switch to the root user by using the ‘su –‘ command when necessary. Before we start, make sure you have a regular user account and with that, you su or sudo to gain root access.
In Linux, it’s very easy to create a separate account, log in as a root user and simply run the adduser command to create a separate user. Once the user is created, just follow the below steps to disable root login via SSH.
We use sshd master configuration file to disable root login and this will may decrease and prevent the hacker from gaining root access to your Linux box. We also see how to enable root access again as well as how to limit ssh access based on users’ list.
Disable SSH Root Login
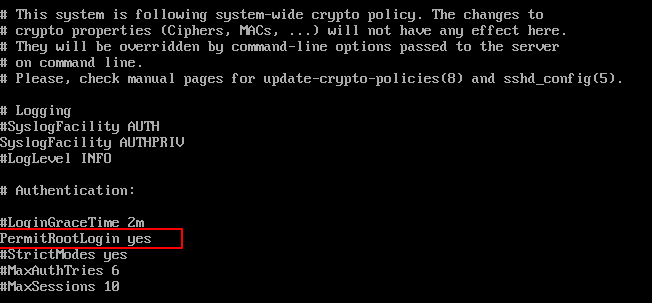
To disable root login, open the main ssh configuration file /etc/ssh/sshd_config with your choice of editor.
Search for the following line in the file.
Remove the ‘#‘ from the beginning of the line. Make the line look similar to this.
Next, we need to restart the SSH daemon service.
# systemctl restart sshd OR # /etc/init.d/sshd restart
Now try to log in with the root user, you will get a “Permission denied” error.
$ ssh [email protected] [email protected]'s password: Permission denied, please try again.
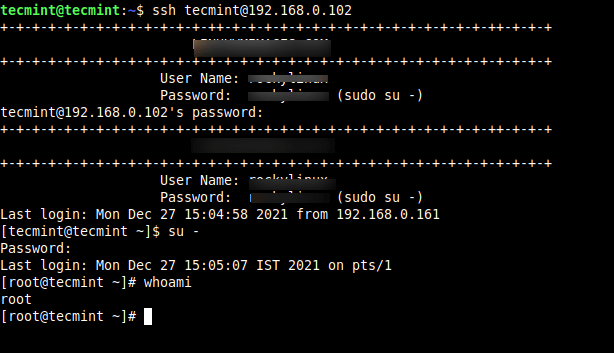
So, from now onwards login as a normal user and then use the ‘su’ command to switch to root user.
$ ssh [email protected] [email protected]'s password: Last login: Mon Dec 27 15:04:58 2021 from 192.168.0.161 $ su - Password: Last login: Mon Dec 27 15:05:07 IST 2021 on pts/1
Enable SSH Root Login
To enable ssh root logging, open the file /etc/ssh/sshd_config.
Search for the following line and remove the ‘#‘ at the beginning and save the file.
Restart the sshd service.
# systemctl restart sshd OR # /etc/init.d/sshd restart
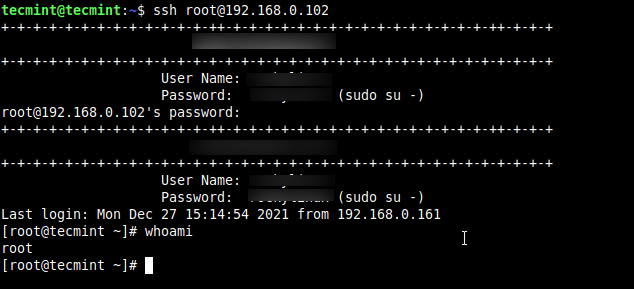
Now try to log in with the root user.
$ ssh [email protected] [email protected]'s password: Last login: Mon Dec 27 15:14:54 2021 from 192.168.0.161
Limit SSH User Logins
If you have a large number of user accounts on the systems, then it makes sense that we limit remote SSH access to those users who really need it. Open the /etc/ssh/sshd_config file.
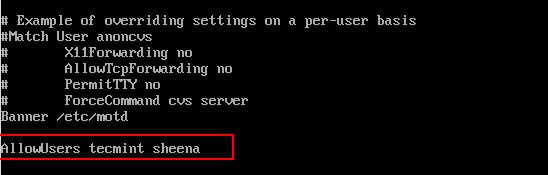
Add an AllowUsers line at the bottom of the file with a space separated by a list of usernames. For example, user tecmint and sheena both have access to remote ssh.
AllowUsers tecmint sheena
Now restart ssh service.