How to «close» open ports?
A few days ago I started to care a lot about my data security, I end up nmap ing myself with: nmap 127.0.0.1 Surprise, surprise, I have lots of active services listen to localhost:
$ nmap 127.0.0.1 Starting Nmap 5.21 ( http://nmap.org ) at 2013-05-05 00:19 WEST Nmap scan report for localhost (127.0.0.1) Host is up (0.00025s latency). Not shown: 993 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 53/tcp open domain 111/tcp open rpcbind 139/tcp open netbios-ssn 445/tcp open microsoft-ds 631/tcp open ipp Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds The only one that I might use is ssh (although it is probably not well configured, I will keep this matter to another question). As far as I know ipp protocol is used by CUPS to share my printers, I don’t need to share them, just access printers from a server. This is the output of netstat -lntup by the root user, removing the localhost addresses:
Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 497/sshd tcp 0 0 0.0.0.0:17500 0.0.0.0:* LISTEN 2217/dropbox tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN 892/smbd tcp 0 0 0.0.0.0:50022 0.0.0.0:* LISTEN 1021/rpc.statd tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN 892/smbd tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 906/rpcbind tcp6 0 0 . 22 . * LISTEN 497/sshd tcp6 0 0 . 42712 . * LISTEN 1021/rpc.statd tcp6 0 0 . 445 . * LISTEN 892/smbd tcp6 0 0 . 139 . * LISTEN 892/smbd tcp6 0 0 . 111 . * LISTEN 906/rpcbind udp 0 0 0.0.0.0:51566 0.0.0.0:* 615/avahi-daemon: r udp 0 0 0.0.0.0:68 0.0.0.0:* 7362/dhclient udp 0 0 0.0.0.0:111 0.0.0.0:* 906/rpcbind udp 0 0 192.168.1.255:137 0.0.0.0:* 1782/nmbd udp 0 0 192.168.1.67:137 0.0.0.0:* 1782/nmbd udp 0 0 0.0.0.0:137 0.0.0.0:* 1782/nmbd udp 0 0 192.168.1.255:138 0.0.0.0:* 1782/nmbd udp 0 0 192.168.1.67:138 0.0.0.0:* 1782/nmbd udp 0 0 0.0.0.0:138 0.0.0.0:* 1782/nmbd udp 0 0 0.0.0.0:655 0.0.0.0:* 906/rpcbind udp 0 0 0.0.0.0:17500 0.0.0.0:* 2217/dropbox udp 0 0 0.0.0.0:5353 0.0.0.0:* 615/avahi-daemon: r udp 0 0 0.0.0.0:34805 0.0.0.0:* 1021/rpc.statd udp6 0 0 . 40192 . * 1021/rpc.statd udp6 0 0 . 111 . * 906/rpcbind udp6 0 0 . 655 . * 906/rpcbind udp6 0 0 . 5353 . * 615/avahi-daemon: r udp6 0 0 . 42629 . * 615/avahi-daemon: r How do I configure those services so they only listen to the outside world when I’m actually using them?
How to Check, Open, and Close a Port on Ubuntu
In this tutorial we’ll learn how to check for listening ports, using numerous tools, along with managing ports by allowing or disallowing incoming and outgoing connections.
Ports in Ubuntu
What is a port? In simple words: a door to a program running in your operating system. Or: application-specific or process-specific software construct used as a numeric identifier of a particular connection between two applications.
Port numbers is a 16-bit unsigned integer that range from 0 to 65535. Applications listen for ports to achieve a successful communication from the outside.
When dealing with a well-known distribution as Ubuntu, there are multiple tricks and features that check for, close or open ports.
So as an alert Linux user, it’s imperative to be aware of probe for open ports in your system, which ones are open by default, closing open ports and allowing exceptions. If not, securities holes and system’s vulnerabilities would be the least of your problems, not to mention bandwidth and resource consuming connections.
| Port Name | Port Number/Protocol | Alias |
|---|---|---|
| ftp | 21/tcp | // |
| -ssh | 22/tcp | // |
| -smtp | 25/tcp | |
| domain | 53/tcp | nameserver |
| domain | 53/udp | nameserver |
| http | 80/tcp | www www-http |
| -https | 443/tcp | // |
| pop3 | 110/tcp | pop-3 |
Table of Contents
How to Inspect Listening Ports
Obviously, before even starting to open or close ports, it’s necessary to be familiar with which ports are open in your system. To do that, we can use various built-in command line utilities or installed.
Fire up your machine, open the terminal, then type the next command to list running services and which ports are used.
ftp 21/tcp fsp 21/udp fspd ssh 22/tcp # SSH Remote Login Protocol telnet 23/tcp smtp 25/tcp mail time 37/tcp timserver time 37/udp timserver whois 43/tcp nicname
When you want to quit less , hit the q key.
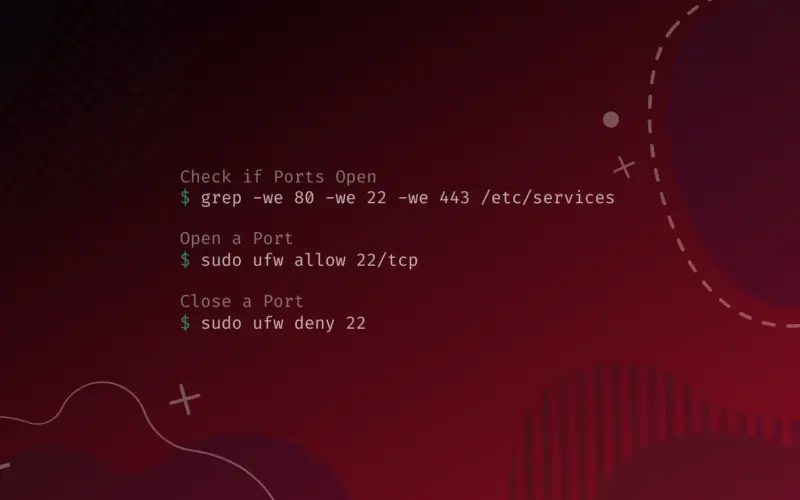
Suppose we want to check for specific ports (80, 443 and 22). Easily use the grep tool like so:
grep -we 80 -we 22 -we 443 /etc/services
ssh 22/tcp # SSH Remote Login Protocol http 80/tcp www # WorldWideWeb HTTP https 443/tcp # http protocol over TLS/SSL https 443/udp # HTTP/3
The next command is using netstat , which is a well known utility that can be used to inspect listening ports and socket information. There are multiple variations of using this tool, but we will be ok by the next (tcp/udp):
We can also be using the ss tool, which is very similar to netstat .
lsof is a command line utility for listing open files, but can be used to check what process and tool is listening on a specific port; or by using the protocol.
Now to one of the major tools in the port scanning field: Nmap. We can also use this tool in a variety of ways, but we will see only the following example:
Note that the utilities above will only display the port if a service or a process is actually listening for incoming connections, (if port is in use). But keep in mind, this does not mean that the listening service is open to the internet, since our firewall could be blocking incoming connections for certain ports.
How to Open Ports
Generally to open or close ports on Ubuntu we use ufw command (Uncomplicated Firewall); which is a frontend for iptables. Before starting to manage our ports, we have to check the ufw statues by running the next command:
Enable your firewall as so:
Firewall is active and enabled on system startup
Status: active Logging: on (low) Default: deny (incoming), allow (outgoing), disabled (routed) New profiles: skip
As you can see, our firewall is denying incoming connections. So if we want to add an exception (22 tcp), we should run the below mentioned command.
Check if our firewall is indeed making an exception for port 22:
Status: active Logging: on (low) Default: deny (incoming), allow (outgoing), disabled (routed) New profiles: skip To Action From -- ------ ---- 22/tcp ALLOW IN Anywhere 22/tcp (v6) ALLOW IN Anywhere (v6)
In the even we want to allow a specific IP address to connect to port 22:
sudo ufw allow from 40.200.14.5 to any port 22
We could use the same previous command for a subnet of IP addresses:
sudo ufw allow from 40.200.14.0/24 to any port 22
We checked managing incoming connections; for allowing outgoing connections we use the out option:
Let’s check the iptables examples for opening ports. First let’s make an exception for incoming connections to port 80:
sudo iptables -I INPUT -p tcp --dport 80 -j ACCEPT
This second command for making an exception for outgoing connections to port 80:
sudo iptables -I OUTPUT -p tcp --sport 80 -j ACCEPT
How to Close Ports
Like opening ports, there are numerous commands for closing ports. Upon discovery of an open port that should be closed. The easiest way as before is using ufw .
Let’s start by blocking port 22:
We could use the reject keyword instead:
Note that reject and deny options achieve similar results, the key difference though, is that reject informs back the sender that their connection was rejected via error packet.
As before, in case we want to block outgoing call, we use the following command:
Let’s try iptables to block incoming connections:
sudo iptables -A INPUT -p tcp --dport 80 -j DROP
Just like ufw , DROP keyword is used to block connections without sending back an error packet.
sudo iptables -A INPUT -p tcp --dport 80 -j REJECT
The REJECT option, for informing the sender that their request has been rejected.
When trying to block users from using a specific port (outgoing), we use the following:
sudo iptables -A OUTPUT -p tcp --sport 80 -j DROP
Bonus: In case that you missed around with your firewall (adding and dropping a whole lot of exceptions). Do not worry; just run the command mentioned below to start over.
Resetting all rules to installed defaults. Proceed with operation (y|n)? y Backing up 'user.rules' to '/etc/ufw/user.rules.20220503_211753' Backing up 'before.rules' to '/etc/ufw/before.rules.20220503_211753' Backing up 'after.rules' to '/etc/ufw/after.rules.20220503_211753' Backing up 'user6.rules' to '/etc/ufw/user6.rules.20220503_211753' Backing up 'before6.rules' to '/etc/ufw/before6.rules.20220503_211753' Backing up 'after6.rules' to '/etc/ufw/after6.rules.20220503_211753'
Conclusion
In this how to article we learned about checking which ports are used by our services and programs, we did that by testing different utilities and command lines. We also learned about managing ports with ufw and iptables ; we’ve managed that by being acquainted with executing allow exceptions, deny/reject exceptions and how to run them for different scenarios.
How to close ports in Linux?
it show that 23/tcp port is closed. Which of them is true? I want to close this port on my whole system, how can I do it?
they are both true. TCP ports aren’t associated with hosts. they are associated with network interfaces. the difference is subtle but important. interfaces are often the same as hosts, but not always. in this case (as stated in answers) localhost is accessing the lo (loopback) interface. the IP Address is accesing your real interface, probably eth0 or wlan0 or somesuch.
5 Answers 5
Nmap is a great port scanner, but sometimes you want something more authoritative. You can ask the kernel what processes have which ports open by using the netstat utility:
me@myhost:~$ sudo netstat -tlnp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 1004/dnsmasq tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 380/sshd tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 822/cupsd tcp6 0 0 . 22 . * LISTEN 380/sshd tcp6 0 0 ::1:631 . * LISTEN 822/cupsd
The options I have given are:
- -t TCP only
- -l Listening ports only
- -n Don’t look up service and host names, just display numbers
- -p Show process information (requires root privilege)
In this case, we can see that sshd is listening on any interface ( 0.0.0.0 ) port 22, and cupsd is listening on loopback ( 127.0.0.1 ) port 631. Your output may show that telnetd has a local address of 192.168.1.1:23 , meaning it will not answer to connections on the loopback adapter (e.g. you can’t telnet 127.0.0.1 ).
There are other tools that will show similar information (e.g. lsof or /proc ), but netstat is the most widely available. It even works on Windows ( netstat -anb ). BSD netstat is a little different: you’ll have to use sockstat(1) to get the process information instead.
Once you have the process ID and program name, you can go about finding the process and killing it if you wish to close the port. For finer-grained control, you can use a firewall (iptables on Linux) to limit access to only certain addresses. You may need to disable a service startup. If the PID is «-» on Linux, it’s probably a kernel process (this is common with NFS for instance), so good luck finding out what it is.
Note: I said «authoritative» because you’re not being hindered by network conditions and firewalls. If you trust your computer, that’s great. However, if you suspect that you’ve been hacked, you may not be able to trust the tools on your computer. Replacing standard utilities (and sometimes even system calls) with ones that hide certain processes or ports (a.k.a. rootkits) is a standard practice among attackers. Your best bet at this point is to make a forensic copy of your disk and restore from backup; then use the copy to determine the way they got in and close it off.