- How To Install dsniff on Kali Linux
- What is dsniff
- Install dsniff Using apt-get
- Install dsniff Using apt
- Install dsniff Using aptitude
- How To Uninstall dsniff on Kali Linux
- Uninstall dsniff And Its Dependencies
- Remove dsniff Configurations and Data
- Remove dsniff configuration, data, and all of its dependencies
- References
- Summary
- dsniff on Kali Linux
- 2. Uninstall / Remove dsniff package
- 3. Details of dsniff package
- 4. References on Kali Linux
- 5. The same packages on other Linux Distributions
- Packages and Binaries:
- Denial of Service (DoS) Attack Using dSniff
- Requirements
- 1) Installation of dSniff
- 2) In Kali Linux, enable IP forwarding.
- 3) Find the victim’s IP address.
- 4) Check for a victim connection.
- 5) Check your internet interface
- 6) Launch the attack
How To Install dsniff on Kali Linux
In this tutorial we learn how to install dsniff on Kali Linux.
What is dsniff
This package contains several tools to listen to and create network traffic:
- arpspoof — Send out unrequested (and possibly forged) arp replies.
- dnsspoof — forge replies to arbitrary DNS address / pointer queries on the Local Area Network.
- dsniff — password sniffer for several protocols.
- filesnarf — saves selected files sniffed from NFS traffic.
- macof — flood the local network with random MAC addresses.
- mailsnarf — sniffs mail on the LAN and stores it in mbox format.
- msgsnarf — record selected messages from different Instant Messengers.
- sshmitm — SSH monkey-in-the-middle. proxies and sniffs SSH traffic.
- sshow — SSH traffic analyser.
- tcpkill — kills specified in-progress TCP connections.
- tcpnice — slow down specified TCP connections via “active” traffic shaping.
- urlsnarf — output selected URLs sniffed from HTTP traffic in CLF.
- webmitm — HTTP / HTTPS monkey-in-the-middle. transparently proxies.
- webspy — sends URLs sniffed from a client to your local browser (requires libx11-6 installed).
Please do not abuse this software.
There are three ways to install dsniff on Kali Linux . We can use apt-get , apt and aptitude . In the following sections we will describe each method. You can choose one of them.
Install dsniff Using apt-get
Update apt database with apt-get using the following command.
After updating apt database, We can install dsniff using apt-get by running the following command:
sudo apt-get -y install dsniff Install dsniff Using apt
Update apt database with apt using the following command.
After updating apt database, We can install dsniff using apt by running the following command:
sudo apt -y install dsniff Install dsniff Using aptitude
If you want to follow this method, you might need to install aptitude first since aptitude is usually not installed by default on Kali Linux. Update apt database with aptitude using the following command.
After updating apt database, We can install dsniff using aptitude by running the following command:
sudo aptitude -y install dsniff How To Uninstall dsniff on Kali Linux
To uninstall only the dsniff package we can use the following command:
sudo apt-get remove dsniff Uninstall dsniff And Its Dependencies
To uninstall dsniff and its dependencies that are no longer needed by Kali Linux, we can use the command below:
sudo apt-get -y autoremove dsniff Remove dsniff Configurations and Data
To remove dsniff configuration and data from Kali Linux we can use the following command:
sudo apt-get -y purge dsniff Remove dsniff configuration, data, and all of its dependencies
We can use the following command to remove dsniff configurations, data and all of its dependencies, we can use the following command:
sudo apt-get -y autoremove --purge dsniff References
Summary
In this tutorial we learn how to install dsniff using different package management tools like apt, apt-get and aptitude.
dsniff on Kali Linux
This tutorial shows how to install dsniff package:
2. Uninstall / Remove dsniff package
This is a short guide on how to uninstall dsniff package:
3. Details of dsniff package
Package: dsniff
Source: dsniff (2.4b1+debian-30)
Version: 2.4b1+debian-30+b1
Installed-Size: 439
Maintainer: Debian Security Tools
Architecture: amd64
Depends: libc6 (>= 2.33), libdb5.3, libnet1 (>= 1.1.2.1), libnids1.21 (>= 1.23), libpcap0.8 (>= 0.9.8), libssl3 (>= 3.0.0), libtirpc3 (>= 1.0.2), libx11-6, libxmu6 (>= 2:1.1.3), openssl
Size: 105524
SHA256: b5b24d950763616b9a665375e761b07fefc8f862d790312d983267cd9c5eab04
SHA1: d312361674e131d1154859f7a057c494ba806a90
MD5sum: 6dd85a3358d73a65704902e227dd5f6b
Description: Various tools to sniff network traffic for cleartext insecurities
This package contains several tools to listen to and create network traffic:
.
* arpspoof — Send out unrequested (and possibly forged) arp replies.
* dnsspoof — forge replies to arbitrary DNS address / pointer queries
on the Local Area Network.
* dsniff — password sniffer for several protocols.
* filesnarf — saves selected files sniffed from NFS traffic.
* macof — flood the local network with random MAC addresses.
* mailsnarf — sniffs mail on the LAN and stores it in mbox format.
* msgsnarf — record selected messages from different Instant Messengers.
* sshmitm — SSH monkey-in-the-middle. proxies and sniffs SSH traffic.
* sshow — SSH traffic analyser.
* tcpkill — kills specified in-progress TCP connections.
* tcpnice — slow down specified TCP connections via «active»
traffic shaping.
* urlsnarf — output selected URLs sniffed from HTTP traffic in CLF.
* webmitm — HTTP / HTTPS monkey-in-the-middle. transparently proxies.
* webspy — sends URLs sniffed from a client to your local browser
(requires libx11-6 installed).
.
Please do not abuse this software.
Description-md5: f59711cd7b27b929d9435bf6750d88a7
Homepage: https://www.monkey.org/~dugsong/dsniff/
Tag: implemented-in::c, interface::commandline, protocol::ethernet,
protocol::http, protocol::ip, protocol::smtp, protocol::ssh,
role::program, scope::utility, use::monitor, works-with::mail
Section: net
Priority: optional
Filename: pool/main/d/dsniff/dsniff_2.4b1+debian-30+b1_amd64.deb
4. References on Kali Linux
5. The same packages on other Linux Distributions
dsniff (2.4b1+debian-28.1~build1) Ubuntu 18.04 LTS (Bionic Beaver)
dsniff (2.4b1+debian-22.1) Ubuntu 16.04 LTS (Xenial Xerus)
dsniff (2.4b1+debian-30) Ubuntu 21.04 (Hirsute Hippo)
dsniff (2.4b1+debian-29) Ubuntu 20.10 (Groovy Gorilla)
dsniff (2.4b1+debian-30) Ubuntu 21.10 (Impish Indri)
dsniff (2.4b1+debian-30build1) Ubuntu 22.04 LTS (Jammy Jellyfish)
dsniff (2.4b1+debian-29) Debian 10 (Buster)
Packages and Binaries:
This package contains several tools to listen to and create network traffic:
- arpspoof — Send out unrequested (and possibly forged) arp replies.
- dnsspoof — forge replies to arbitrary DNS address / pointer queries on the Local Area Network.
- dsniff — password sniffer for several protocols.
- filesnarf — saves selected files sniffed from NFS traffic.
- macof — flood the local network with random MAC addresses.
- mailsnarf — sniffs mail on the LAN and stores it in mbox format.
- msgsnarf — record selected messages from different Instant Messengers.
- sshmitm — SSH monkey-in-the-middle. proxies and sniffs SSH traffic.
- sshow — SSH traffic analyser.
- tcpkill — kills specified in-progress TCP connections.
- tcpnice — slow down specified TCP connections via “active” traffic shaping.
- urlsnarf — output selected URLs sniffed from HTTP traffic in CLF.
- webmitm — HTTP / HTTPS monkey-in-the-middle. transparently proxies.
- webspy — sends URLs sniffed from a client to your local browser (requires libx11-6 installed).
Please do not abuse this software.
Installed size: 430 KB
How to install: sudo apt install dsniff
- libc6
- libdb5.3
- libnet1
- libnids1.21
- libpcap0.8
- libssl3
- libtirpc3
- libx11-6
- libxmu6
- openssl
arpspoof
Intercept packets on a switched LAN
[email protected]:~# arpspoof --help arpspoof: invalid option -- '-' Version: 2.4 Usage: arpspoof [-i interface] [-c own|host|both] [-t target] [-r] host dnsspoof
Forge replies to DNS address / pointer queries
[email protected]:~# dnsspoof --help dnsspoof: invalid option -- '-' Version: 2.4 Usage: dnsspoof [-i interface] [-f hostsfile] [expression] dsniff
[email protected]:~# dsniff --help dsniff: invalid option -- '-' Version: 2.4 Usage: dsniff [-cdmn] [-i interface | -p pcapfile] [-s snaplen] [-f services] [-t trigger[. ]] [-r|-w savefile] [expression] filesnarf
Sniff files from NFS traffic
[email protected]:~# filesnarf --help filesnarf: invalid option -- '-' Version: 2.4 Usage: filesnarf [-i interface | -p pcapfile] [[-v] pattern [expression]] macof
Flood a switched LAN with random MAC addresses
[email protected]:~# macof --help macof: invalid option -- '-' Version: 2.4 Usage: macof [-s src] [-d dst] [-e tha] [-x sport] [-y dport] [-i interface] [-n times] mailsnarf
Sniff mail messages in Berkeley mbox format
[email protected]:~# mailsnarf --help mailsnarf: invalid option -- '-' Version: 2.4 Usage: mailsnarf [-i interface | -p pcapfile] [[-v] pattern [expression]] msgsnarf
[email protected]:~# msgsnarf --help msgsnarf: invalid option -- '-' Version: 2.4 Usage: msgsnarf [-i interface | -p pcapfile] [[-v] pattern [expression]] sshmitm
[email protected]:~# sshmitm --help sshmitm: invalid option -- '-' Version: 2.4 Usage: sshmitm [-d] [-I] [-p port] host [port] sshow
SSH traffic analysis tool
[email protected]:~# sshow --help sshow: invalid option -- '-' Usage: sshow [-d] [-i interface | -p pcapfile] tcpkill
Kill TCP connections on a LAN
[email protected]:~# tcpkill --help tcpkill: invalid option -- '-' Version: 2.4 Usage: tcpkill [-i interface] [-1..9] expression tcpnice
Slow down TCP connections on a LAN
[email protected]:~# tcpnice --help tcpnice: invalid option -- '-' Version: 2.4 Usage: tcpnice [-A] [-I] [-M] [-i interface] expression urlsnarf
Sniff HTTP requests in Common Log Format
[email protected]:~# urlsnarf --help urlsnarf: invalid option -- '-' Version: 2.4 Usage: urlsnarf [-n] [-i interface | -p pcapfile] [[-v] pattern [expression]] webmitm
HTTP / HTTPS monkey-in-the-middle
[email protected]:~# webmitm --help webmitm: invalid option -- '-' Version: 2.4 Usage: webmitm [-d] [host] webspy
Display sniffed URLs in Netscape in real-time
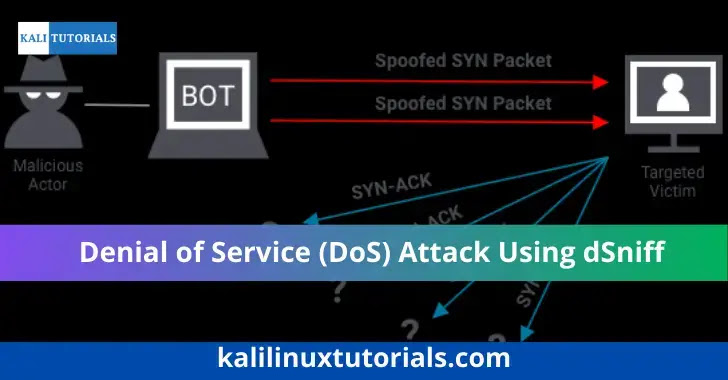
[email protected]:~# webspy --help webspy: invalid option -- '-' Version: 2.4 Usage: webspy [-i interface | -p pcapfile] host Denial of Service (DoS) Attack Using dSniff
A Denial-of-Service (DoS) attack using dSniff, aims to bring down a computer system or network so that its intended users cannot access it. DoS attacks achieve this by sending the target excessive traffic or information that causes a crash.
Requirements
- Linux machine ( I used Kali Linux)
- Victim OS (Virtual or Real Machine)
- dSniff tool
1) Installation of dSniff
Install a dSniff using the command – “apt-get install dsniff”
2) In Kali Linux, enable IP forwarding.
Now we have to enable the Ip forwarding using the command “echo > 1 /proc/sys/net/ipv4/ip_forward” in Kali Linux’s Terminal
3) Find the victim’s IP address.
- As the victim machine, I am using a virtual machine, i.e., Windows 10. Now we have to navigate to the command prompt.
- In the command prompt for knowing the IP address of the Victim Machine, we will type the command ‘ipconfig”
Now we will use the command “arp -a” which displays the current ARP entry for the hosts with a table of Internet Address, Physical Address, and Type of Connection.
As we can see, there are many connected devices on one network. In a real-world scenario, it is very difficult to identify the IP of the victim. I have two virtual machines for this tutorial, which makes it simple for me to check the IP address of the victim’s machine.
Now focus only on the physical address of the gateway 192.168.148.2
4) Check for a victim connection.
On the victim machine, check for a connection by opening the browser and searching for anything.
5) Check your internet interface
The command “ifconfig” must now be used on the Kali Linux machine to check the Internet interface.
My internet interface, as shown is ”eth0”
6) Launch the attack
When everything is in place, the command structure is ready to launch the attack – “arpspoof -i [your internet interface] -t [target IP address] -r [gateway IP address]”
In my case – “arpspoof -i eth0 -t 192.168.148.129 -r 192.168.148.2”
When I try to refresh the page after the attack has been launched, let us check the connection with the victim again. The result will look like this.
As we can see, the Webpage of the victim’s machine becomes unreachable as our attack gets successful.
Now when we use the command “arp -a” again in the victim’s machine, we can see that the physical addresses of the two Internet addresses are the same.
If you know how ARP functions, you can change the physical address of the router to your Kali IP address. The victim is then prevented from connecting to the internet by your Kali, which then blocks the connection from the router to the victim.
Please consider following and supporting us to stay updated with the latest info