- Saved searches
- Use saved searches to filter your results more quickly
- License
- adamff1/ESP8266-Captive-Portal
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
- Saved searches
- Use saved searches to filter your results more quickly
- License
- cyb3rt3ch/ESP8266_WiFi_Captive_Portal
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
- Saved searches
- Use saved searches to filter your results more quickly
- License
- anson-vandoren/esp8266-captive-portal
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
- Saved searches
- Use saved searches to filter your results more quickly
- Alpha-1729/ESP_WiFi_Captive_Portal
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
🔑 WiFi captive portal for ESP8266 for phishing WiFi passwords
License
adamff1/ESP8266-Captive-Portal
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
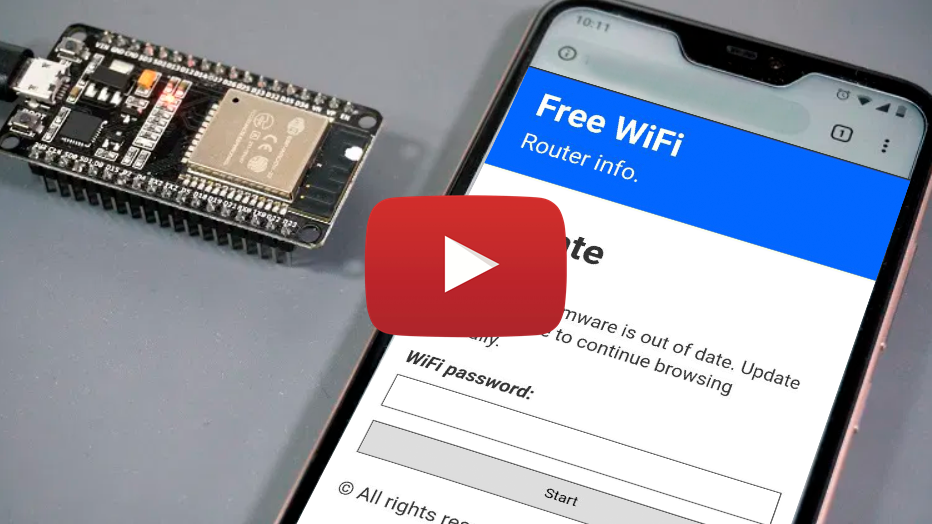
ESP8266 WiFi Captive Portal
This project is for testing and educational purposes. Use it only against your own networks and devices. I don’t take any responsibility for what you do with this program.
WiFi captive portal for the NodeMCU (ESP8266 Module) with DNS spoofing.
The built-in LED will blink 5 times when a password is posted.
Warning! Your saved passwords will not disappear when you restart/power off the ESP8266.
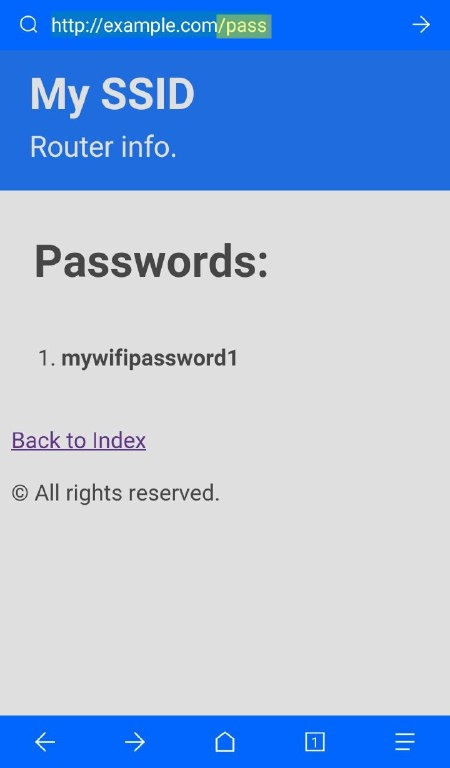
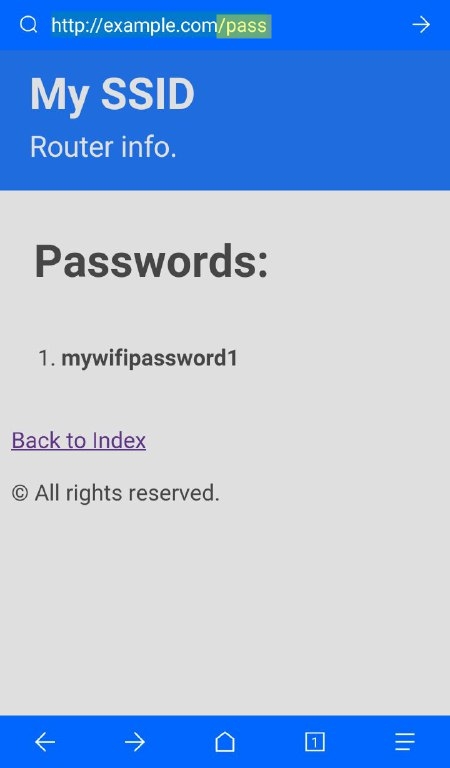
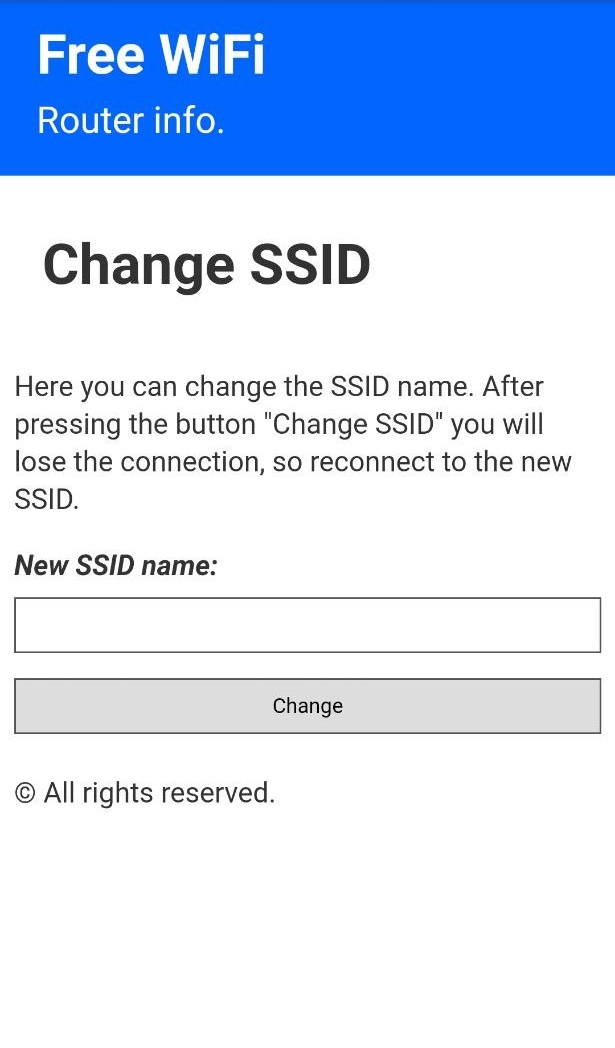
Note: If you want to see the stored passwords go to «172.0.0.1/pass». For changing the SSID, go to «172.0.0.1/ssid»
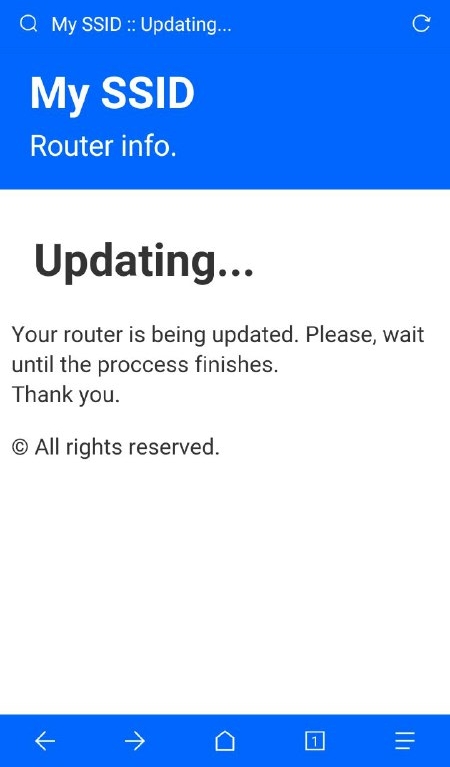
| 172.0.0.1/index | 172.0.0.1/post | 172.0.0.1/pass | 172.0.0.1/ssid |
|---|---|---|---|
| This is the main page. Here the user will write his password and send it. | This is the post page. The user will be redirected here after posting the password. | This is where the attacker can retrieve all the passwords that has been posted. | Here the attacker can change the SSID name of the Access Point on the go. |
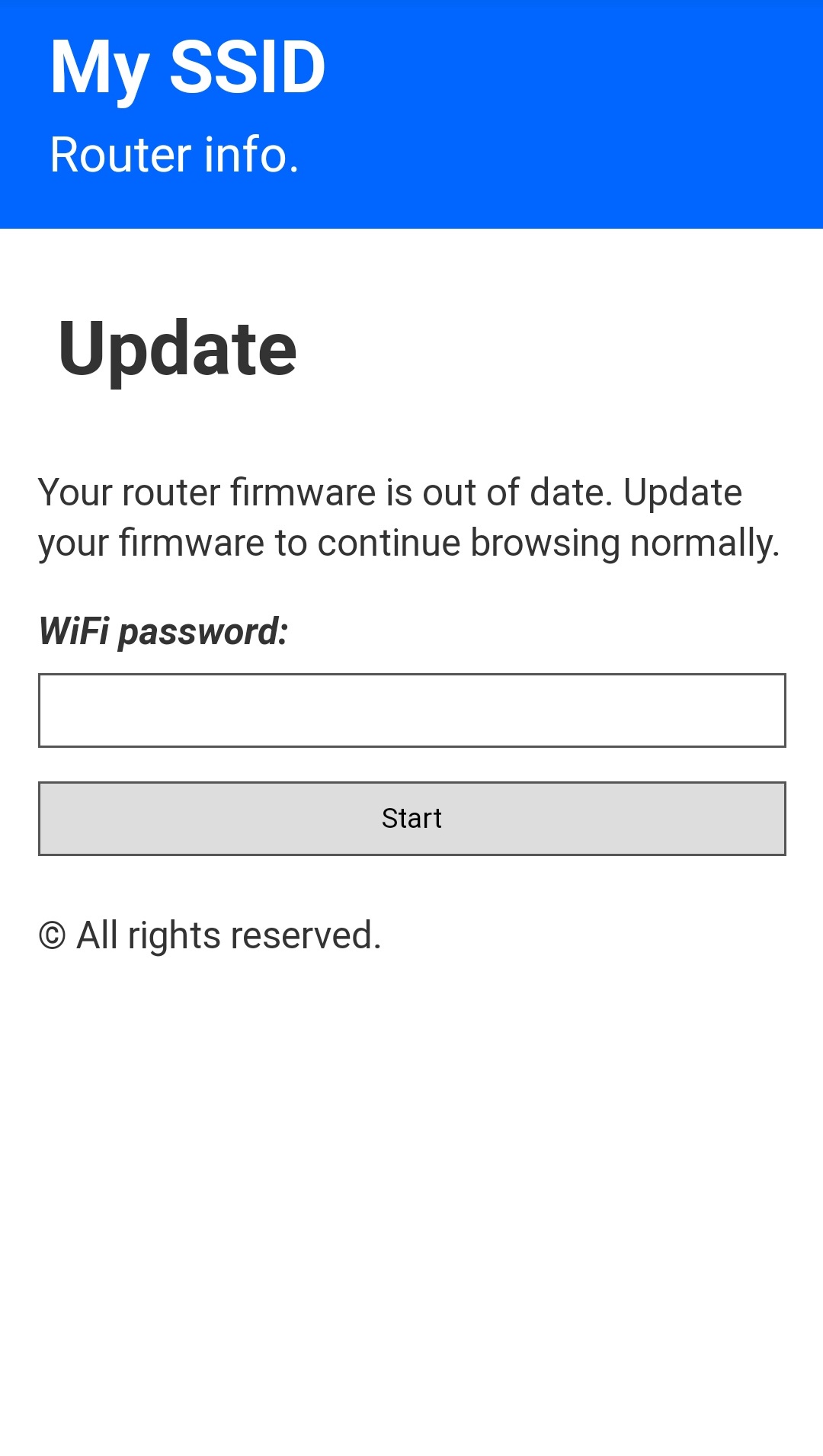 | 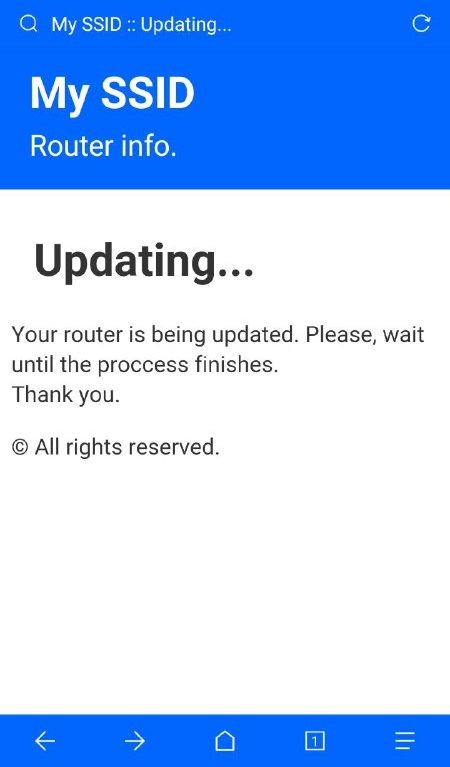 |  |  |
Here you can donate if you liked my project and you want to support me:
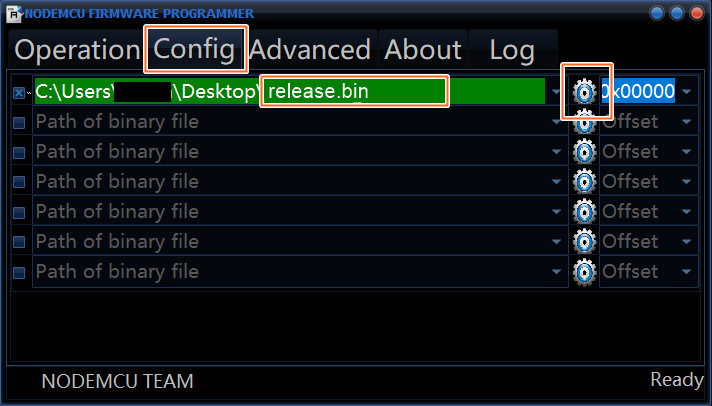
Installation (ESP8266 Flasher — Easy way)
- Download ESP8266 Flasher.
- Download the release.bin file.
- Open the ESP8266 Flasher and select the Node MCU port
- Open your Arduino IDE and go to «File -> Preferences -> Boards Manager URLs» and paste the following link: http://arduino.esp8266.com/stable/package_esp8266com_index.json
- Go to «Tools -> Board -> Boards Manager», search «esp8266» and install esp8266
- Go to «Tools -> Board» and select you board»
- Download and open the sketch «WiFi_Captive_Portal.ino«
- You can optionally change some parameters like the SSID name and texts of the page like title, subtitle, text body.
- Upload the code into your board.
- You are done!
Check out my other projects
- WiFi-Spam: 📧 📡 Spam thousands of WiFi access points with custom SSIDs.
- https://github.com/125K/WiFi-Spam
- https://github.com/125K/PwrDeauther
About
🔑 WiFi captive portal for ESP8266 for phishing WiFi passwords
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
🔑 WiFi captive portal for ESP8266 for phishing WiFi passwords
License
cyb3rt3ch/ESP8266_WiFi_Captive_Portal
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
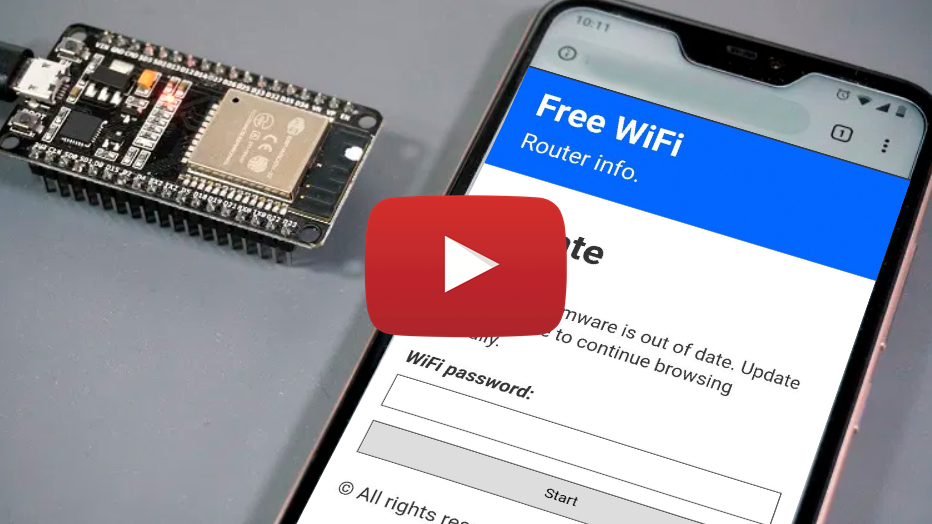
ESP8266 WiFi Captive Portal
WiFi captive portal for the NodeMCU (ESP8266 Module) with DNS spoofing.
The built-in LED will blink 5 times when a password is posted.
Warning! Your saved passwords will not disappear when you restart/power off the ESP8266.
Note: If you want to see the stored passwords go to «172.0.0.1/pass». For changing the SSID, go to «172.0.0.1/ssid»
172.0.0.1/index 172.0.0.1/post 172.0.0.1/pass 172.0.0.1/ssid This is the main page. Here the user will write his password and send it. This is the post page. The user will be redirected here after posting the password. This is where the attacker can retrieve all the passwords that has been posted. Here the attacker can change the SSID name of the Access Point on the go. Here you can donate if you liked my project and you want to support me:
Installation (ESP8266 Flasher — Easy way)
- Download ESP8266 Flasher.
- Download the release.bin file.
- Open the ESP8266 Flasher and select the Node MCU port
- Open your Arduino IDE and go to «File -> Preferences -> Boards Manager URLs» and paste the following link: http://arduino.esp8266.com/stable/package_esp8266com_index.json
- Go to «Tools -> Board -> Boards Manager», search «esp8266» and install esp8266
- Go to «Tools -> Board» and select you board»
- Download and open the sketch «WiFi_Captive_Portal.ino«
- You can optionally change some parameters like the SSID name and texts of the page like title, subtitle, text body.
- Upload the code into your board.
- You are done!
Check out my other projects
- WiFi-Spam: 📧 📡 Spam thousands of WiFi access points with custom SSIDs.
- https://github.com/125K/WiFi-Spam
- https://github.com/125K/PwrDeauther
This project is for testing and educational purposes. Use it only against your own networks and devices. I don’t take any responsibility for what you do with this program.
About
🔑 WiFi captive portal for ESP8266 for phishing WiFi passwords
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Create a captive web portal for ESP8266
License
anson-vandoren/esp8266-captive-portal
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
The code in this repo is the results of a blog series I wrote about building a captive web portal for a Wemos D1 Mini using MicroPython. You can find the articles here:
Starting the captive portal
Copy the .py and .html files to your ESP8266 board. If you already have a main.py file, then just copy the contents of the main.py file from this repo. There’s only a couple of lines there.
Instantiating a CaptivePortal and calling its start() method will turn on your MCU’s WiFi access point, and you can then connect to it and input your home WiFi credentials. Once you do, the MCU will turn off its AP, and connect to your home WiFi instead.
This is not really a standalone project, but rather a bit of useful functionality that I drop into other projects I make so that if I send one to someone else, I don’t need to hardcode their home WiFi credentials to get the thing to work. Instead, they can easily enter their own WiFi SSID and password to allow the device to connect and start doing whatever it’s supposed to be doing.
About
Create a captive web portal for ESP8266
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
ESP8266 WiFi captive portal for phishing WiFi passwords.
Alpha-1729/ESP_WiFi_Captive_Portal
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
ESP8266 Wifi Captive Portal
WiFi captive portal for the NodeMCU (ESP8266 Module) with DNS spoofing.
This project is for testing and educational purposes. Use it only against your own networks and devices. I don’t take any responsibility for what you do with this program.
- 💪 The LED will blink 5 times when a password is posted.
- 💪 All captured password will be stored in the ESP8266 itself.
- 💪 Your saved passwords will not disappear when you:
- ▶️ Restart/power off the ESP8266.
- ▶️ Change the SSID.
- Passwords and SSID will be stored in the EEPROM of the ESP8266.
- EEPROM Memory location:
- 0-19 ▶️ For storing SSID.
- 20-24 ▶️ To check the first boot of ESP8266.
- 30-END ▶️ For storing password.
- ✏️ Changing the SSID: ▶️ 172.0.0.1/ssid ◀️
- 💥 Clearing the passwords: ▶️ 172.0.0.1/clear ◀️
- 🙈 To see saved passwords: ▶️ 172.0.0.1/pass ◀️
- 📜 Testing victim page: ▶️ 172.0.0.1/index ◀️
172.0.0.1/index 172.0.0.1/post 172.0.0.1/pass 172.0.0.1/ssid This is the main page. Here the user will write his password and send it. This is the post page. The user will be redirected here after posting the password. This is where the attacker can retrieve all the passwords that has been posted and saved passwords can be cleared. Here the attacker can change the SSID name of the Access Point on the go. 1. ESP8266 Flasher — Easy way
- Download ESP8266 Flasher.
- Download the esp-wifi-captive-portal-v1.0.bin file.
- Open the ESP8266 Flasher and select the Node MCU port
- Open your Arduino IDE and go to File 🔎 Preferences 🔎 Boards Manager URLs and paste the following link: https://arduino.esp8266.com/stable/package_esp8266com_index.json
- Go to Tools 🔎 Board 🔎 Boards Manager, search «esp8266» and install esp8266.
- Go to Tools 🔎 Board and select you board.
- Download and open the sketch «esp-wifi-captive-portal.ino«.
- You can optionally change some parameters like the SSID name and texts of the page like title, subtitle, text body.
- Upload the code into your board.
- You are done!
- After uploading the code, first clear the passwords already in the EEPROM.
- If any error happens, kindly report the issue.
About
ESP8266 WiFi captive portal for phishing WiFi passwords.