CentOS / RHEL 5 : How to use the faillog command to track failed login attempts
The failog command formats and displays the contents of the failure log (/var/log/faillog) and maintains failure counts and limits. The faillog functionality has to be enabled by adding the pam_tally.so module to the respective file in /etc/pam.d/. Below are the steps to setup the faillog utility to track failed login attempts.
1. Edit the /etc/pam.d/system-auth file and add the following lines:
# vi /etc/pam.d/system-auth auth required pam_tally.so no_magic_root account required pam_tally.so deny=2 no_magic_root
2. Test the configuration by attempting to login as a normal user, but using a wrong password. Verify the failed count increments by running the command:
# faillog Login Failures Maximum Latest On geek 1 2 05/24/17 15:39:35 +0200 /dev/tty2
The faillog command prints out only users with no successful login since the last failure. To print out a user who has had a successful login since his last failure, you must explicitly request the user with the -u option.
3. The failed login is recorded in /var/log/faillog in some specific binary format by default, and the utility faillog only can parse /var/log/faillog to get the failed logins. We don’t have any option to make faillog to read logs in other places.
4. To grant access again to a user who had more failures than the limit, enter:
You can also use pam_tally commands to do the same – to display the number of failed attempts:
# pam_tally --user [username] --reset[=n]
faillog(8) — Linux man page
faillog formats the contents of the failure log from /var/log/faillog database. It also can be used for maintains failure counters and limits. Run faillog without arguments display only list of user faillog records who have ever had a login failure.
Options
The options which apply to the faillog command are: -a, —all Display faillog records for all users. -h, —help Display help message and exit. -l, —lock-time SEC Lock account to SEC seconds after failed login. -m, —maximum MAX Set maximum number of login failures after the account is disabled to MAX. Selecting MAX value of 0 has the effect of not placing a limit on the number of failed logins. The maximum failure count should always be 0 for root to prevent a denial of services attack against the system. -r, —reset Reset the counters of login failures or one record if used with the -u LOGIN option. Write access to /var/log/faillog is required for this option. -t, —time DAYS Display faillog records more recent than DAYS. The -t flag overrides the use of -u. -u, —user LOGIN Display faillog record or maintains failure counters and limits (if used with -l, -m or -r options) only for user with LOGIN.
Caveats
faillog only prints out users with no successful login since the last failure. To print out a user who has had a successful login since their last failure, you must explicitly request the user with the -u flag, or print out all users with the -a flag.
Files
/var/log/faillog Failure logging file.
How to Find All Failed SSH login Attempts in Linux
Each attempt to login to SSH server is tracked and recorded into a log file by the rsyslog daemon in Linux. The most basic mechanism to list all failed SSH logins attempts in Linux is a combination of displaying and filtering the log files with the help of cat command or grep command.
In order to display a list of the failed SSH logins in Linux, issue some of the commands presented in this guide. Make sure that these commands are executed with root privileges.
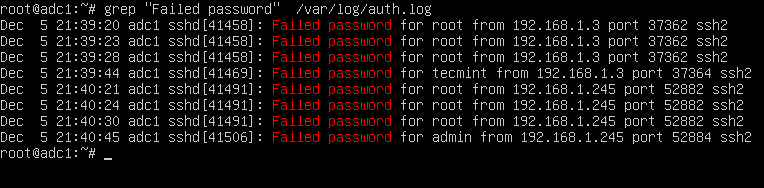
The most simple command to list all failed SSH logins is the one shown below.
# grep "Failed password" /var/log/auth.log
The same result can also be achieved by issuing the cat command.
# cat /var/log/auth.log | grep "Failed password"
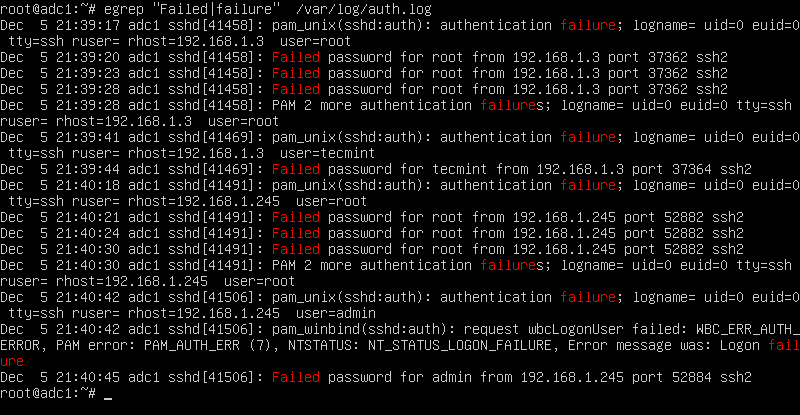
In order to display extra information about the failed SSH logins, issue the command as shown in the below example.
# egrep "Failed|Failure" /var/log/auth.log
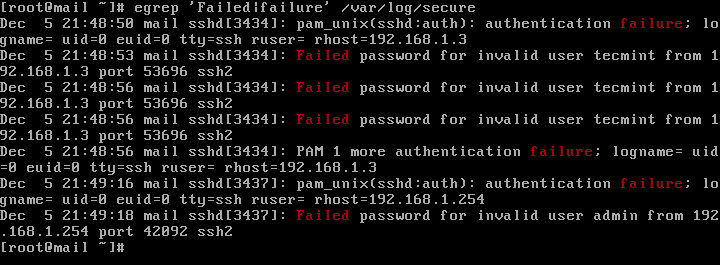
In CentOS or RHEL, the failed SSH sessions are recorded in /var/log/secure file. Issue the above command against this log file to identify failed SSH logins.
# egrep "Failed|Failure" /var/log/secure
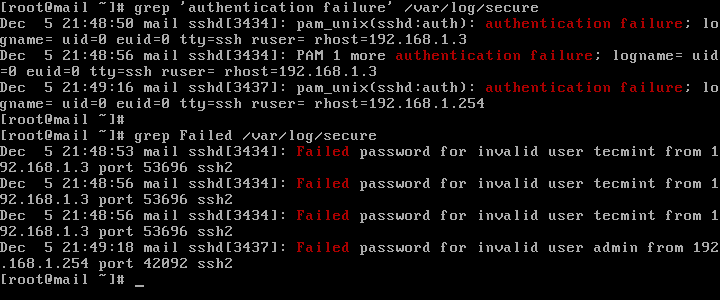
A slightly modified version of the above command to display failed SSH logins in CentOS or RHEL is as follows.
# grep "Failed" /var/log/secure # grep "authentication failure" /var/log/secure
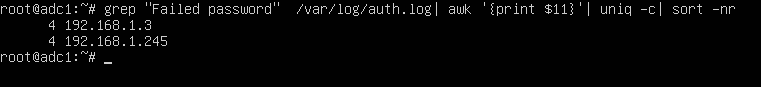
To display a list of all IP addresses that tried and failed to log in to the SSH server alongside the number of failed attempts of each IP address, issue the below command.
# grep "Failed password" /var/log/auth.log | awk ‘’ | uniq -c | sort -nr
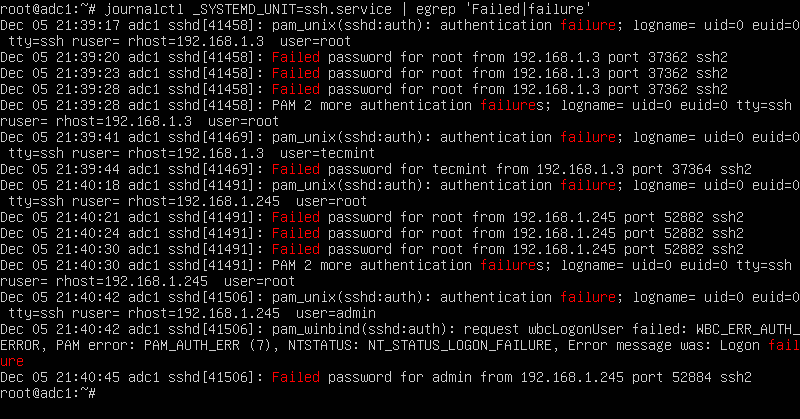
On newer Linux distributions you can query the runtime log file maintained by Systemd daemon via journalctl command. In order to display all failed SSH login attempts you should pipe the result via grep filter, as illustrated in the below command examples.
# journalctl _SYSTEMD_UNIT=ssh.service | egrep "Failed|Failure" # journalctl _SYSTEMD_UNIT=sshd.service | egrep "Failed|Failure" #In RHEL, CentOS
In CentOS or RHEL, replace the SSH daemon unit with sshd.service, as shown in the below command examples.
# journalctl _SYSTEMD_UNIT=sshd.service | grep "failure" # journalctl _SYSTEMD_UNIT=sshd.service | grep "Failed"
After you’ve identified the IP addresses that frequently hit your SSH server in order to log in to the system with suspicious user accounts or invalid user accounts, you should update your system firewall rules to block the failed SSH attempts IP addresses or use a specialized software, such as fail2ban to manage these attacks.
fallog
The manual page and help for the faillog Linux command. THE fallog command displays the error log database (/var/log/faillog) content, and you can also set the error counters and limit values. If faillog is run with no arguments, it will only display faillog records for users who had the login failure.
Man page output
Usage: faillog [options] Options: -a, --all display faillog records for all users -h, --help display this help message and exit -l, --lock-secs SEC after failed login lock account for SEC seconds -m, --maximum MAX set maximum failed login counters to MAX -r, --reset reset the counters of login failures -R, --root CHROOT_DIR directory to chroot into -t, --time DAYS display faillog records more recent than DAYS -u, --user LOGIN/RANGE display faillog record or maintains failure counters and limits (if used with -r, -m, or -l) only for the specified LOGIN(s)
Help output
Usage: faillog [options] Options: -a, --all display faillog records for all users -h, --help display this help message and exit -l, --lock-secs SEC after failed login lock account for SEC seconds -m, --maximum MAX set maximum failed login counters to MAX -r, --reset reset the counters of login failures -R, --root CHROOT_DIR directory to chroot into -t, --time DAYS display faillog records more recent than DAYS -u, --user LOGIN/RANGE display faillog record or maintains failure counters and limits (if used with -r, -m, or -l) only for the specified LOGIN(s)