- How to Password Protect a Folder in Linux
- Password protect folders in Linux
- Method 1: Lock folders with Gnome EncFS Manager
- Method 2: Lock files with VeraCrypt
- Private or not?
- How to Protect Files and Directories from Deleting in Linux
- Protecting File
- Protecting a file
- Removing the protection to file
- Protecting Directories
- Protecting a directory
- Removing protection to the directory
- Implement shell file protection in Linux
- Protecting Files With noclobber
- Overriding Protections
- Example: Truncating a Logfile
- Conclusion
How to Password Protect a Folder in Linux
Got some special files to save from prying eyes? Learn how to create password protected folders in the Linux desktop.
In a situation where you often share your computer with others but have some private files that you don’t want others to see? You can try hiding it in places where others cannot find it. Like in a deeply nested folder structure but that’s not entirely foolproof because the files could be shown in the desktop search results. On Android, there are several applications to lock gallery photos or hide them. I haven’t used such folder-locking applications in Linux. My laptop is used only by me and I do not need to hide any files. If so, then why are we talking about folder lock for Linux today? I got a request from an It’s FOSS reader for a tutorial on encrypted folders in Ubuntu. If this interests you, let’s see how to lock a folder in Linux.
Password protect folders in Linux
The tools discussed here do not give you military-grade encryption. But for average desktop users, they should work just fine.
I am using Ubuntu in this tutorial but you can use any other Linux distribution based on Ubuntu such as Linux Mint, elementary OS, etc. The steps should apply to other Linux distributions such as Fedora, Arch Linux, etc but the commands to install the tool won’t be the same.
Method 1: Lock folders with Gnome EncFS Manager
Let’s see how to install Gnome Encfs Manager.
If you are using Ubuntu or Linux Mint or other Linux distributions based on Ubuntu, you can use the official PPA using the commands below one by one:
sudo add-apt-repository ppa:gencfsm sudo apt update sudo apt install gnome-encfs-managerPackages for Debian, Fedora, and OpenSUSE are available here.
If you are using GNOME on Wayland and don’t have the system tray app indicator support, you should use this GNOME extension to add quick access to the top panel. Read this article to learn how to use GNOME extensions.
Once installed, you may have to log out to see the application working. Now, go to the application menu and start Gnome Encfs Manager. On the first opening, it will show you a warning message about the existing vulnerability. You need to press Enter on OK to continue.
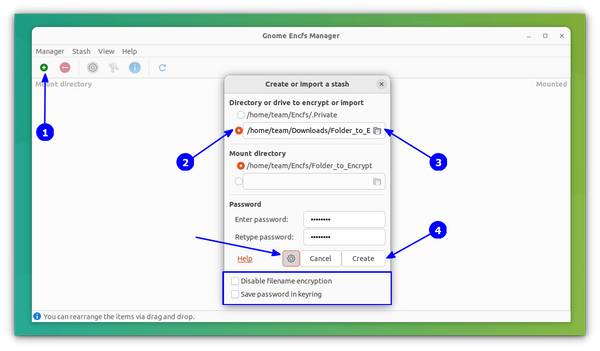
Now, click on the + sign to add a new folder that you’ll be locking with a password. A password-protected folder is called stash in this application’s terminology.
Here, you can create a new directory or browse an existing one. You can try password-protect an existing folder, but the files already in the folder won’t be locked. For this reason, I suggest creating a new folder and moving the files after you password-protect it.
Don’t forget to use a password that you will remember easily. If you forget the password, you should also forget the files locked with it.
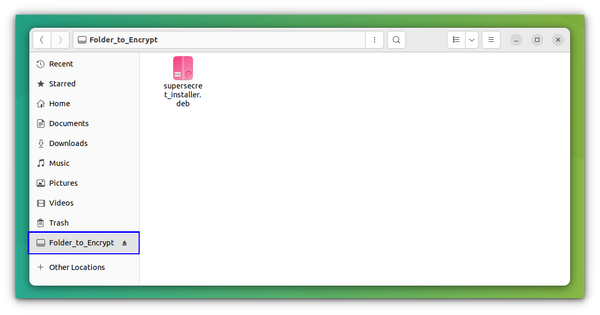
Once the folder is created, you can start copying the files into it. Your locked folder will be seen as a mounted drive when you have unlocked it.
You can get control of the locked folder from the GNOME extension. I am not sure if other desktop environments have anything similar. I leave that to your exploration.
Once you have copied the files into the secret folder, simply unmount it. You can do that by unchecking the mounted folder from the panel extension as shown above. When you want to access it, use the launcher in the top panel or start the program again.
You can also use advanced settings such as auto-start or auto-unmount after a certain idle time.
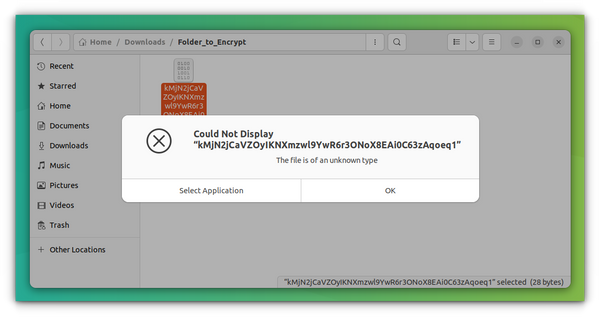
Note that the so-called secret directory will be visible and accessible to anyone in its usual location. However, its content won’t be in a readable format, not even the filenames.
When you mount the locked folder, it will become readable.
That’s all you need to know about password-protecting folders with Gnome Encfs Manager.
Method 2: Lock files with VeraCrypt
VeraCrypt is a free, open-source disk encryption software, available for all major platforms, and is based on TrueCrypt 7.1a.
It is available as a deb package for Ubuntu releases up to 22.04. It also offers several installation packages for various recent versions of Fedora, Debian, OpenSUSE, etc. You need to download the appropriate file from their official downloads page.
Once downloaded the file, install the deb file in Ubuntu using the terminal, software center, or GDebi package installer, according to your choice.
After installation, open VeraCrypt from the Ubuntu Activities overview.
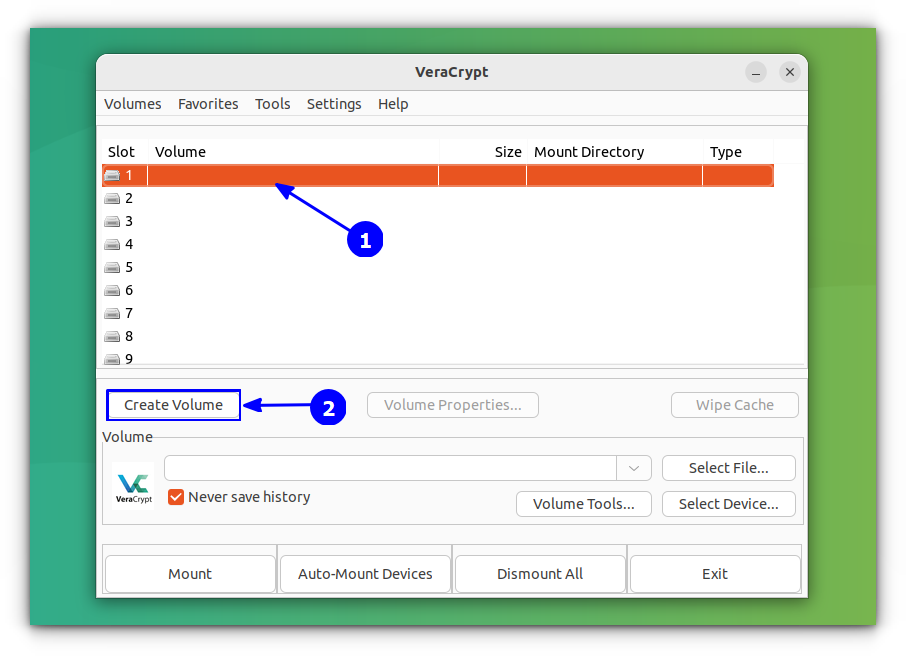
Now, select a slot (64 by default) and click on create volume button.
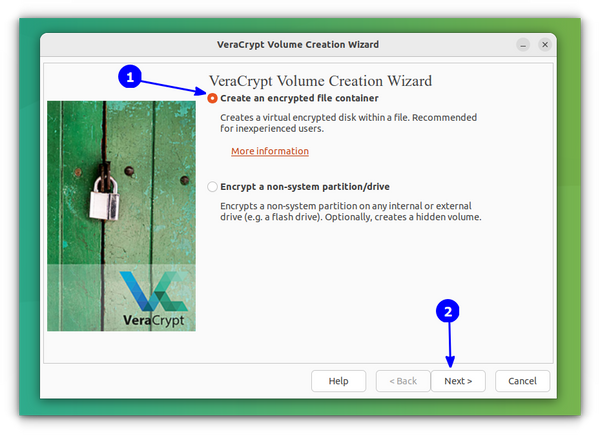
Select the Create an encrypted file container option on the next screen and click Next.
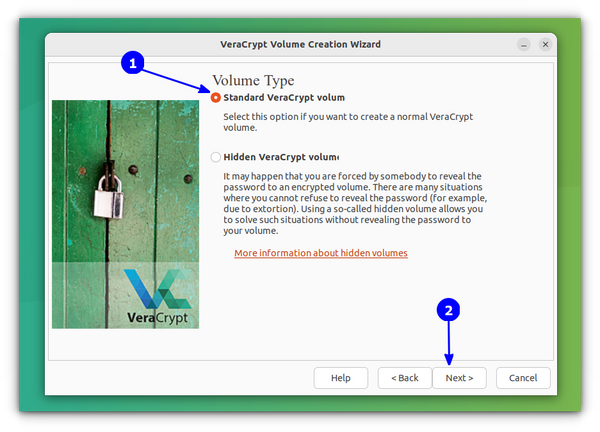
After that, select the Standard VeraCrypt volume as the Volume Type and press Next.
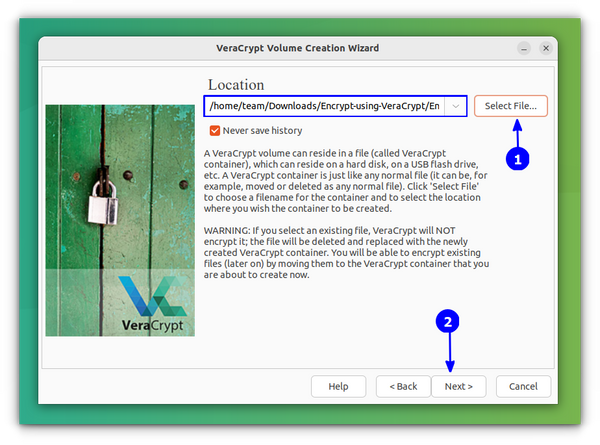
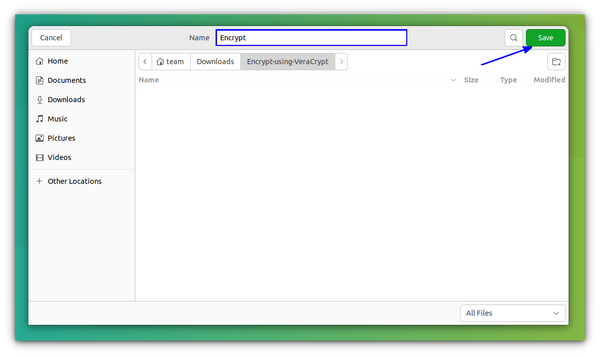
This will lead you to a window, where, you want to select a file to store the encrypted volume. You need to press the Select File option.
This will open the file explorer window and you can create a new file by typing a name on the top name bar as shown below and pressing Save.
If you select any existing file, the process still works. It won’t encrypt that existing file but replace that file with a new one, leading to loss of content. So better create a new file for this purpose.
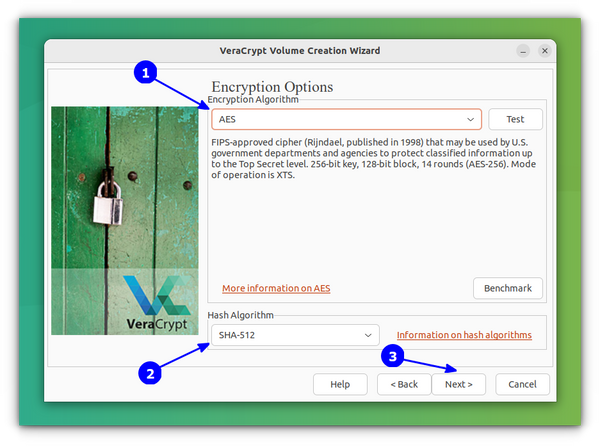
Once the file is selected, in the next step, you need to specify the Encryption type, that is the Encryption and Hash algorithm. The default is AES and SHA-512. Press Next.
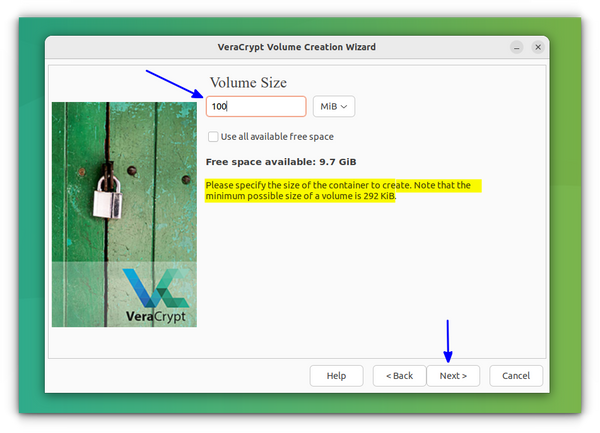
Now, give a size for the encrypted volume. Here, allocate a size that will satisfy your need.
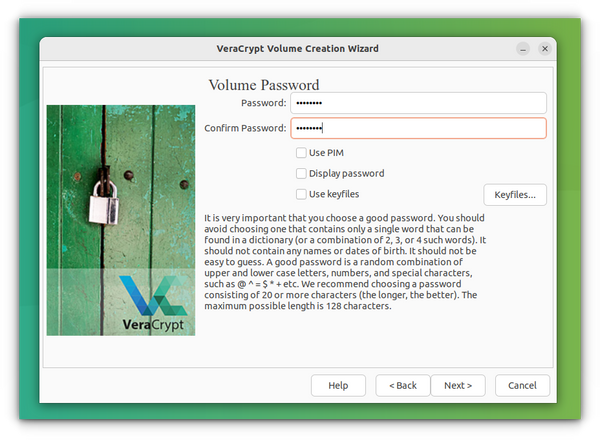
Following the above step, you must provide a password for the encryption. VeraCrypt suggests (not mandatory) a 20+ character password; they will prompt this if not satisfied.
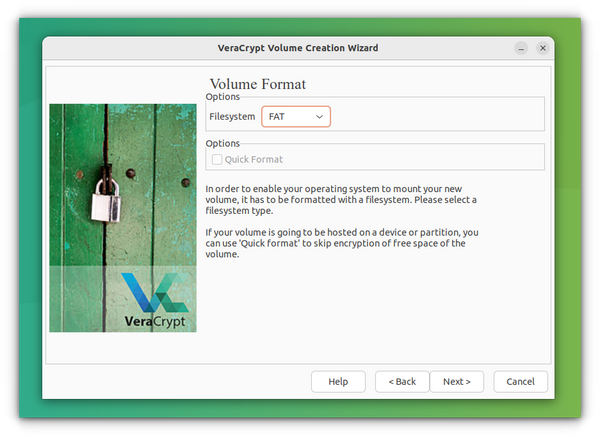
In the Next step, choose the filesystem for the volume. Several options are available including NTFS. After selecting, press Next.
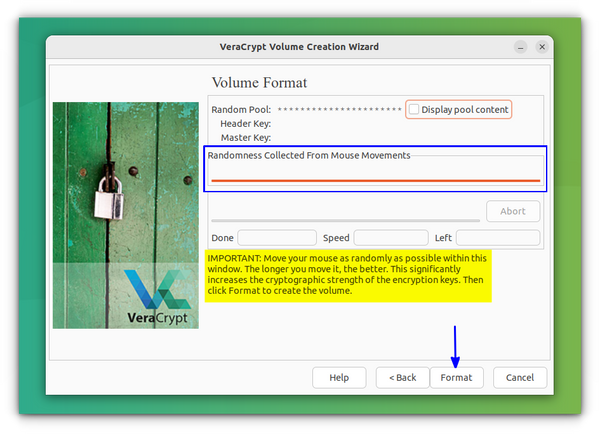
The last page will ask you to randomly move your mouse inside the window to increase encryption strength. Do it till the progress bar reaches the other end :). Now press Format.
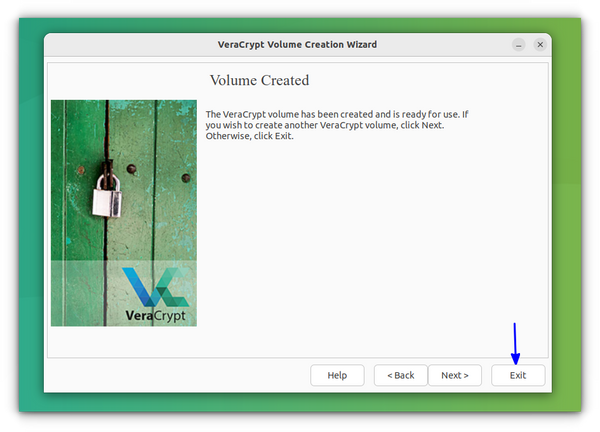
Now, you can press Exit to finish the process.
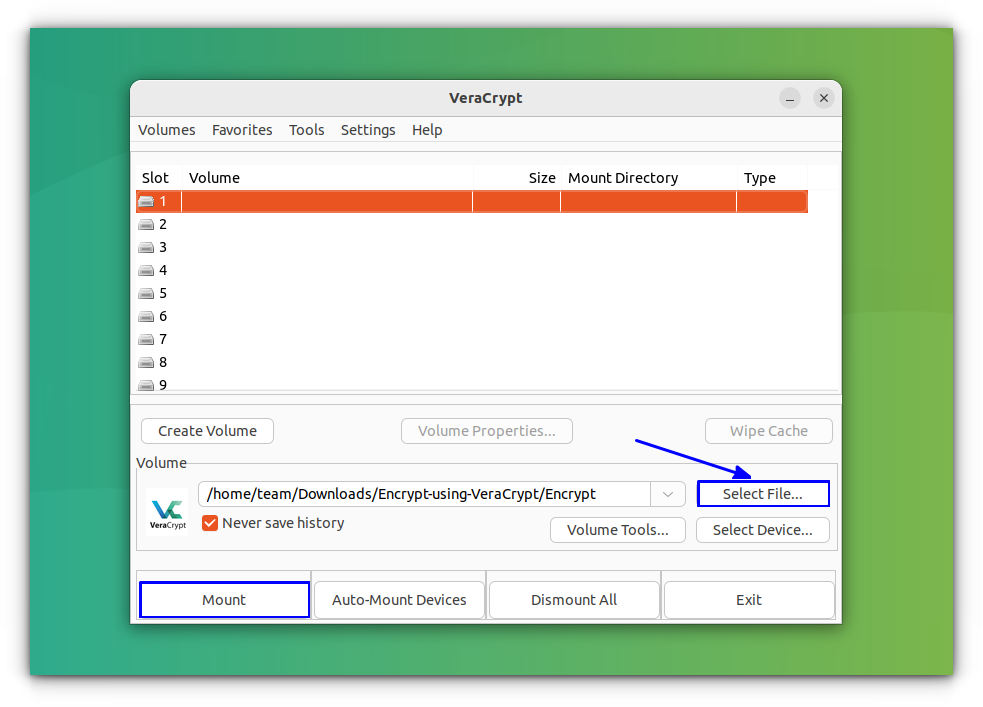
Once the volume is created, you need to mount this. To do that, open VeraCrypt and select Select File.
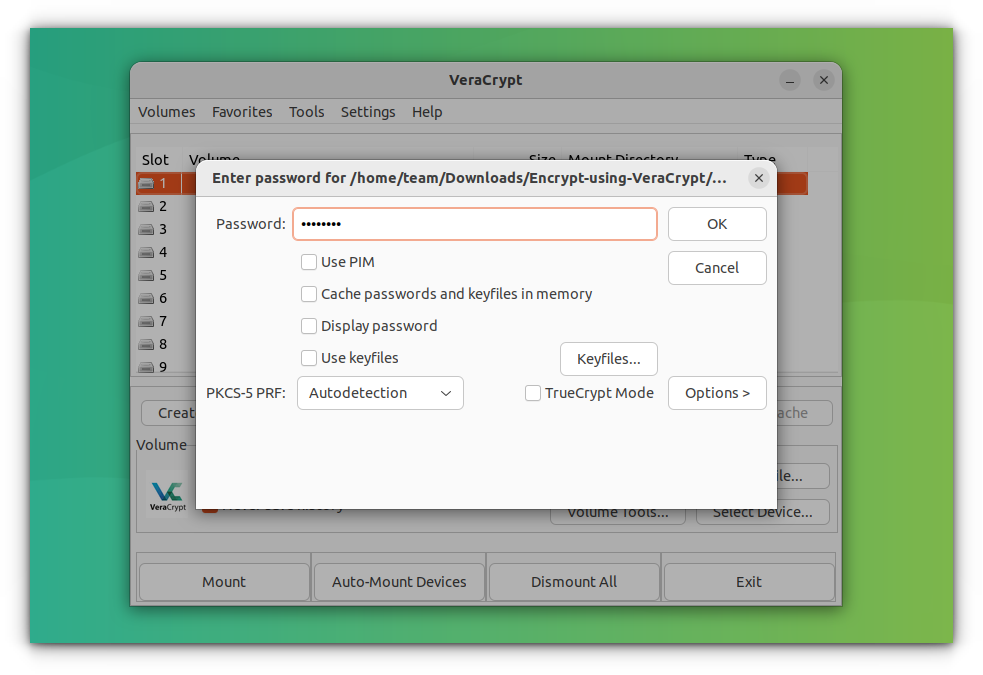
Choose the file you created initially and press Mount to mount the volume.
This will ask you for the encryption password. Also, you may be asked for your user password in this process. Give them.
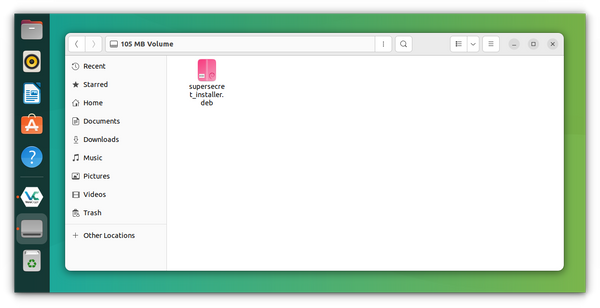
Now, you can paste the files you want to encrypt inside this volume. Upon unmounting, you need the password to reaccess it. Keep in mind the size of the volume you allotted to it at the beginning; this will be the copying limit.
Note that, VeraCrypt won’t be started automatically at each boot. If you want that, read this guide to manage start up applications in Ubuntu and see how can you start VeraCrypt at each boot.
Private or not?
Enjoy your private locked folder in Linux. As I mentioned earlier, it gives you some basic functionality where an average person cannot access the files you have kept in the locked folder.
For better security, you should encrypt the entire disk while installing the operating system. Most people don’t need security at such a level.
Questions or suggestions are always welcome.
How to Protect Files and Directories from Deleting in Linux
Are you working as a Linux Admin? Do you generally defend script documents or any important files? You might be aware that, Chattr (change Attribute) is a command line Linux utility that is used to set/unset exact attributes to a file in Linux process to comfortable unintended deletion or change of major files and folders, although you’re logged in as a root user.
This article helps you to look after your records or folders that may support in disallowing an unauthorized user to delete your touchy contents.
Protecting File
In the below example abc.txt is the file name
Protecting a file
To protect file, use the following command –
Now try to remove file, using rm command as shown below –
The sample output should be like this –
rm: remove write-protected regular file 'abc.txt'?
Removing the protection to file
To remove the protection to file, use the following command –
To verify the above command, use the following command as shown below-
The above command removes the file without giving information.
Protecting Directories
In the below example abc is a directory name
Protecting a directory
To protect directory, use the following command –
To verify the above command, use the following command as shown below –
The sample output should be like this –
rm: descend into write-protected directory 'abc'?
Removing protection to the directory
To remove protection to the directory, use the following command-
To verify the above command, use the following command as shown below –
The above command remove the file without giving information.
In the above article, we have learnt about – Learn how to protect files & directories from delete. In our next articles, we will come up with more Linux based tricks and tips. Keep reading!
I love programming (: That’s all I know
Implement shell file protection in Linux
This article will show you how to protect your files from unauthorized access using the Linux file system permissions, and how to use chmod command to set permissions for a specific user or group of users.
Besides the Linux file permission mechanisms that help us keep our files safe from misuses, most Linux shells have built-in safeguards against accidental file overwrite. We’ll cover some of them here.
Protecting Files With noclobber
All POSIX shell implementations support the noclobber option. If you’re using a shell script, meaning the shell will complain if you try to overwrite an existing directory.
By default, because of tradition, the noclobber option is disabled by default. To turn it on for bash or ksh, run the following command −
To use csh or tcsh when running scripts, we’ll first need to set an environment variable called “csh
If we set the noclobber option, then when we attempt to overwrite a file, Bash will complain: «File exists.»
set -o noclobber touch temp.txt # Create temp.txt file echo "Hello" > temp.txt # Try to overwrite file contents -bash: temp.txt: cannot overwrite existing file
Using cshell (or tcsh), the error message is slightly more cryptic −
set noclobber touch temp.txt # Create temp.txt file echo "Hello" > temp.txt # Try to overwrite file contents temp.txt: File exists
We should note that we’re not protecting against file overwriting by redirections. If you remove the file using the command line tool rm, redirect its output to another file using the shell operator “>>”, or write to the file from within an application, then everything will be fine.
Overriding Protections
We can either disable the noclobbers restriction by returning to the default behaviour by disabling the shell options or temporarily overriding them. For example, if we want to disable the noclobbing restriction for the current session, we could run the following command −
To temporarily override the noclobber behavior, our shell processes provide special redirection operators: “>!” and “>|” respectively. Let’s show our original example using bash −
set -o noclobber touch temp.txt # Create temp.txt file echo "Hello" > temp.txt # Try to overwrite file contents -bash: temp.txt: cannot overwrite existing file echo "Hello" >| temp.txt # Overwrite file contents using override operator
When using tcsh, we’ll just replace “>|” with “>!” −
set noclobber touch temp.txt # Create temp.txt file echo "Hello" > temp.txt # Try to overwrite file contents temp.txt: File exists echo "Hello" >! temp.txt # Overwrite file contents using override operator
Example: Truncating a Logfile
An example where we might want to use this feature would be when truncating a log file. Therefore, logs tend to be left open by services that keep them. Because of this, we’re often unable to remove them as the operating systems keeps track of open file handle. To truncate the logs, we redirect /dev/* to the files −
This solution has an additional benefit: It doesn’t update the modified date when the contents stay the same. So if you run the redirect in cron and the content stays empty, the modified date will show the last change made by the script.
If you want to use the command-lne redirection method but don’t want to use the -s flag, another option is to use truncate. The next example will have the same result as the previous one, which will resize the file to zero.
truncate -s 0 my_logfile.log
The truncate (truncate) function has another advantage, as it lets us resized our log files to any size. The next example will shrink our log files to 50 MB −
truncate -s 50M my_logfile.log
Conclusion
Here, we discuss the noclobber command and how we can implement shell file protection. We also cover the use of truncates as an optional tool for file resizing.