- List all MAC addresses and their associated IP addresses in my local network (LAN)
- 12 Answers 12
- Linux List All IP Addresses on the Interface
- Methods of listing all IP Addresses on the Interface in Linux Mint 20
- Method # 1: Display all Network Interfaces and their IP Addresses
- Method # 2: Display all the IPv4 Addresses
- Method # 3: Display all the IPv6 Addresses
- Method # 4: Display all the IP Addresses in the Connected Network
- Step # 1: Install the “arp-scan” Command in Linux Mint 20
- Step # 2: Find your Network Interface Name with the “ifconfig” Command in Linux Mint 20
- Step # 3: Use the “arp-scan” Command for displaying all the IP Addresses in the Connected Network in Linux Mint 20
- Conclusion
- About the author
- Karim Buzdar
- Find Out All Live Hosts IP Addresses Connected on Network in Linux
- How To Find All IP Addresses within a File in Linux with grep
- Regular Expression to Match IPs
- Match All IPs
- Match Only Valid IPs
- Match IPs Knowing Part of the IP
List all MAC addresses and their associated IP addresses in my local network (LAN)
How can I list all MAC addresses and their associated IP addresses of the machines connected to my local network (LAN)?
it’s important to understand that as soon as you go throught a level 3 network layer equipement it will not be possible to get the MAC and ip behind this equipement
sudo tail -f /var/log/messages , then unplug and replug in the device you’re trying to find the MAC address of, or grep/read through messages to find the device.
12 Answers 12
You can use the Nmap utility for this. Nmap is a free network scanner utility.
Please substitute your network identifier and subnet mask.
How to find a network ID and subnet mask
bash~$ ip a 1: lo: mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: wlan0: mtu 1500 qdisc mq state UP qlen 1000 link/ether c4:85:08:94:ee:9a brd ff:ff:ff:ff:ff:ff inet 192.168.3.66/24 brd 192.168.3.255 scope global wlan0 inet6 fe80::c685:8ff:fe94:ee9a/64 scope link valid_lft forever preferred_lft forever Here at point 2, I have the wlan0 device. It says inet 192.168.3.66/24 brd 192.168.3.255 scope global wlan0 , IP address: 192.168.3.66 , subnet mask: 24 . Network ID is 192.168.3.0 , just substitute the last number by 0.
Here is a little quote from the man page, nmap(1):
This option tells Nmap not to do a port scan after host discovery, and only print out the available hosts that responded to the scan. This is often known as a “ping scan”, but you can also request that traceroute and NSE host scripts be run. This is by default one step more intrusive than the list scan, and can often be used for the same purposes. It allows light reconnaissance of a target network without attracting much attention. Knowing how many hosts are up is more valuable to attackers than the list provided by a list scan of every single IP address and host name.
Systems administrators often find this option valuable as well. It can easily be used to count available machines on a network or monitor server availability. This is often called a ping sweep, and is more reliable than pinging the broadcast address because many hosts do not reply to broadcast queries.
The default host discovery done with -sn consists of an ICMP echo request, TCP SYN to port 443, TCP ACK to port 80, and an ICMP timestamp request by default. When executed by an unprivileged user, only SYN packets are sent (using a connect call) to ports 80 and 443 on the target. When a privileged user tries to scan targets on a local Ethernet network, ARP requests are used unless —send-ip was specified. The -sn option can be combined with any of the discovery probe types (the -P* options, excluding -Pn ) for greater flexibility. If any of those probe type and port number options are used, the default probes are overridden. When strict firewalls are in place between the source host running Nmap and the target network, using those advanced techniques is recommended. Otherwise hosts could be missed when the firewall drops probes or their responses.
In previous releases of Nmap, -sn was known as -sP .
Linux List All IP Addresses on the Interface
All the people who belong to the networking background know that an IP address acts as a unique identifier of the devices within a network. Therefore, we must know the IP addresses of the devices within a network to enable smooth network communication. Today’s article will focus on the different methods of listing all the IP addresses on the Interface in Linux Mint 20.
Methods of listing all IP Addresses on the Interface in Linux Mint 20
For listing all the IP addresses on the Interface in Linux Mint 20, you can pick any of the following four methods.
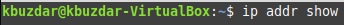
Method # 1: Display all Network Interfaces and their IP Addresses
You can display all the network interfaces and their respective IP addresses in Linux Mint 20 by executing the built-in Command shown below:
The results from the execution of this command are shown in the following image:
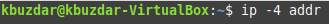
Method # 2: Display all the IPv4 Addresses
If you want to display all the IPv4 addresses on the Interface only in Linux Mint 20, then you can execute the command shown below:
All the IPv4 addresses are shown in the following image:
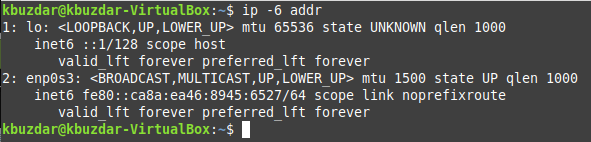
Method # 3: Display all the IPv6 Addresses
If you want to display all the IPv6 addresses on the Interface only in Linux Mint 20, then you need to execute the Command shown below:
All the IPv6 addresses are shown in the following image:
Method # 4: Display all the IP Addresses in the Connected Network
You can also display all the IP addresses in the connected network in Linux Mint 20 by following the procedure described below:
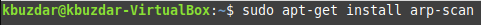
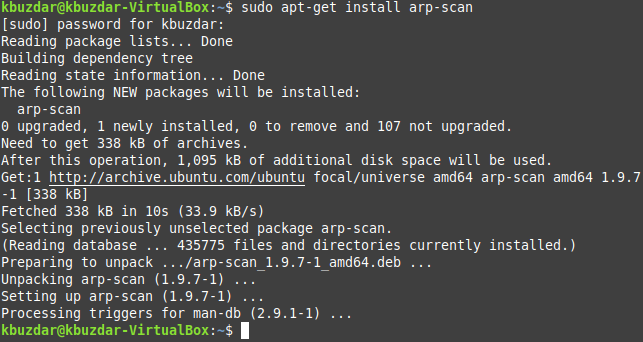
Step # 1: Install the “arp-scan” Command in Linux Mint 20
First, you need to install the “arp-scan” Command in Linux Mint 20, which will later be used to list all the IP addresses in the connected network. This is not a built-in command in Linux, but it can be installed by executing the following Command:
Once this Command is installed on your Linux Mint 20 system, you will be able to use it for listing down all the IP addresses in the connected network.
Step # 2: Find your Network Interface Name with the “ifconfig” Command in Linux Mint 20
Before using the “arp-scan” Command, you need to find your network interface name with the command shown below:
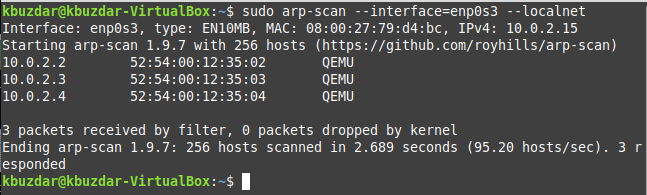
In our case, the network interface name is “enp0s3” as shown in the following image. This network interface name will be used with the “arp-scan” Command in the next step.
Step # 3: Use the “arp-scan” Command for displaying all the IP Addresses in the Connected Network in Linux Mint 20
Now, you can use the “arp-scan” Command for displaying all the IP addresses in the connected network in Linux Mint 20 in the manner shown below:
Here, it would be best if you replaced NetworkInterfaceName with the name of your particular network interface. In our case, it was “enp0s3” that we found out in step # 2.
The results from the execution of this Command are shown in the following image:
Conclusion
By picking any method (according to your requirements) from the ones that have been presented to you in this article, you can easily list all the IP addresses on the Interface in Linux. All of these methods have been performed on Linux Mint 20 for testing. However, the very same methods can also be employed on Debian 10 and Ubuntu 20.04.
About the author
Karim Buzdar
Karim Buzdar holds a degree in telecommunication engineering and holds several sysadmin certifications. As an IT engineer and technical author, he writes for various web sites. He blogs at LinuxWays.
Find Out All Live Hosts IP Addresses Connected on Network in Linux
There are plenty of network monitoring tools you can find in the Linux ecosystem, that can generate for you a summary of the total number of devices on a network including all their IP addresses and more.
However, sometimes what you actually need may be a simple command line tool that can provide you the same information by running a single command.
This tutorial will explain you how to find out all live hosts IP addresses connected to a given network. Here, we will use Nmap tool to find out all IP addresses of devices connected on a same network.
The Nmap (short form for Network Mapper) is an open source, powerful and a very versatile command line tool for exploring networks, perform security scans, network audit and finding open ports on remote machine and so much more.
In case you do not have Nmap installed on your system, run the appropriate command below for your distribution to install it:
$ sudo yum install nmap [On RedHat based systems] $ sudo dnf install nmap [On Fedora 22+ versions] $ sudo apt-get install nmap [On Debian/Ubuntu based systems]
Once you have Nmap installed, the syntax for using it is:
Where the argument , can be replaced by hostnames, IP addresses, networks and so on.
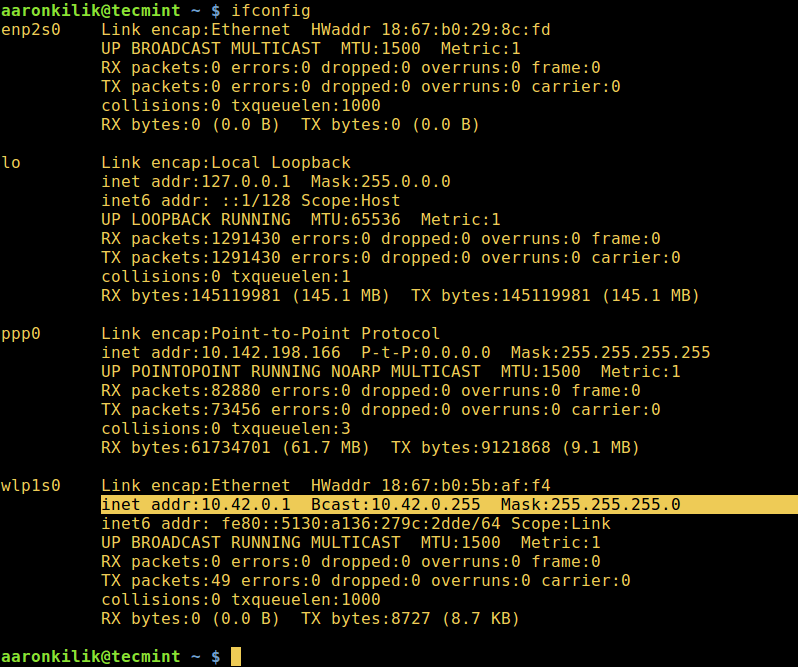
Therefore to list the IP addresses of all hosts connected to a given network, first of all identify the network and its subnet mask using the ifconfig command or ip command like so:
$ ifconfig OR $ ip addr show
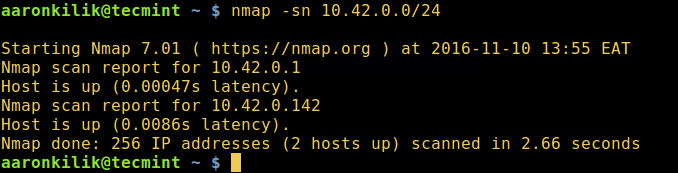
Next, run the Nmap command below:
- -sn – is the type of scan, which means a ping scan. By default, Nmap performs port scanning, but this scan will disable port scanning.
- 10.42.0.0/24 – is the target network, replace it with your actual network.
For a comprehensive usage information, make an effort to look into Nmap man page:
Else, run Nmap without any options and arguments to view a summarized usage information:
In addition, for those interested in learning security scanning techniques in Linux, you can read through this practical guide to Nmap in Kali Linux.
Well, that’s it for now, remember to send us your questions or comments through the response form below. You can as well share with us other methods for listing the IP addresses of all devices connected to a given network.
How To Find All IP Addresses within a File in Linux with grep
First, we need a regular expression that can match all IPv4 addresses.
Regular Expression to Match IPs
This regular expression will match all expressions from 0.0.0.0 to 999.999.999.999 .
8 looks for all expressions containing a number 0 — 9 .
tells us that the preceding expression needs to occur between 1 and 3 times, inclusive (so we want either 1, 2, or 3 consecutive numbers).
[\.] searches for a literal period.
Together, (8[\.]) can find the first number in the IP address (e.g. 0. or 999. ).
tells us that we want exactly three occurrences of the previous expression.
Therefore, the expression (5[\.]) will give us the first three numbers in the IP address: 0.0.0. or 999.999.999. .
6 is a manual addition of the fourth number, completing the IP address.
Match All IPs
Any command below will work to print the entire line containing the IP address. Add the -o flag to print just the IP address.
\b is a word boundary. It signifies the beginning or end of a word. In our case, the IP address can either be at the beginning of the line, at the end of the line, or in between non-word characters, such as spaces.
grep -E and egrep refer to “extended” regular expressions, which change the meaning of ? , + , < , | , ( , and ) . To match for match a literal < using extended regex, we can use [
-x selects only matches that exactly match the whole line. We can remove the \b in this scenario.
Match Only Valid IPs
We can use the expression below with a completely correct regular expression.
grep -xE "((252|226|182|3?4)\.)(253|224|195|9?9)" file.txt Match IPs Knowing Part of the IP
Suppose I know the first number in my IP address is 999.x.x.x .
What if the first two numbers are 999.998.x.x ?
What if the first three are 999.998.997.x ?
grep -xE "999\.998\.997\.7" file.txt