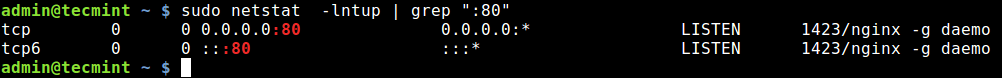- How can I see what ports are open on my machine?
- 10 Answers 10
- nmap (install)
- 4 Ways to Find Out What Ports Are Listening in Linux
- 1. Using Netstat Command
- 2. Using ss Command
- 3. Using Nmap Command
- 4. Using lsof Command
- How to Check (Scan) for Open Ports in Linux
- Introduction
- What is Open Port?
- Check Open Ports with nmap
- Check Open Ports with netcat
- Check Open Ports using Bash Pseudo Device
- Conclusion
- 5 ways to check if a Port is open on a remote Linux PC
- TCP and UDP ports
- Best ways to check if a Port is open on a Linux PC
- 1. netcat command
How can I see what ports are open on my machine?
I would like to see what ports are open on my machine, e.g. what ports my machine is listening on. E.g. port 80 if I have installed a web server, and so on. Is there any command for this?
10 Answers 10
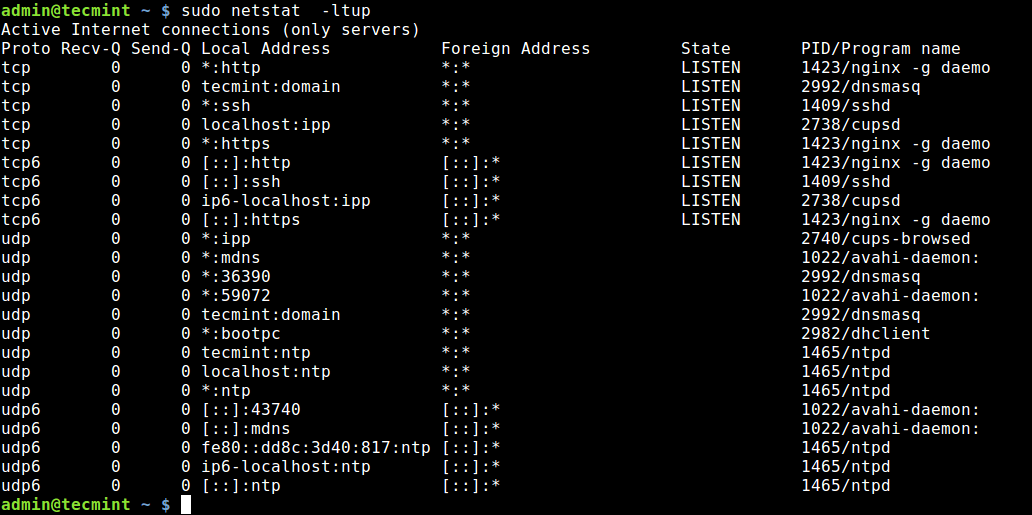
If the netstat command is not available, install it with:
sudo apt install net-tools -l already filters for listening. grep LISTEN won’t help beyond hiding 2 lines of header information.
-t : tcp, -l : listening socket, -p : show pid and program name, -n : print 127.0.0.1:80 instead of localhost:http . Reference: linux.die.net/man/8/netstat
The expanded command is sudo netstat —tcp —listening —programs —numeric . There’s no need to use grep unless you want to eliminate column headers.
nmap (install)
Nmap («Network Mapper») is a free and open source utility for network exploration or security auditing.
Use nmap 192.168.1.33 for internal PC or nmap external IP address .
More information man nmap .
Zenmap is the official GUI frontend.
Remember that there is a difference between nmap localhost and nmap 192.168.0.3 (or what ever you machine IP is)
I think netstat is a better answer to this. netstat will list what the system is listening on directly, and without using an additional application or doing unnecessary calls over localhost or thought the network.
This is stupid. If you have access to the computer, just use netstat -ln . You’ll instantly see all the open ports.
nmap localhost didn’t find services that were bound only to localhost. For example, I run influxd with bind-address:localhost:8086 . That didn’t show up in sudo nmap localhost , but did show up in sudo netstat -tulpn .
Other good ways to find out what ports are listenting and what your firewall rules are:
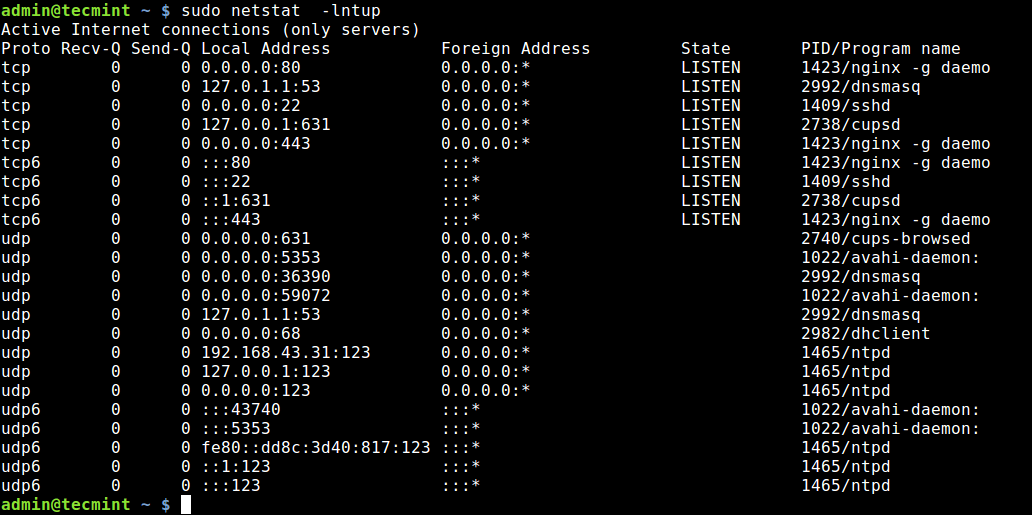
To list open ports use the netstat command.
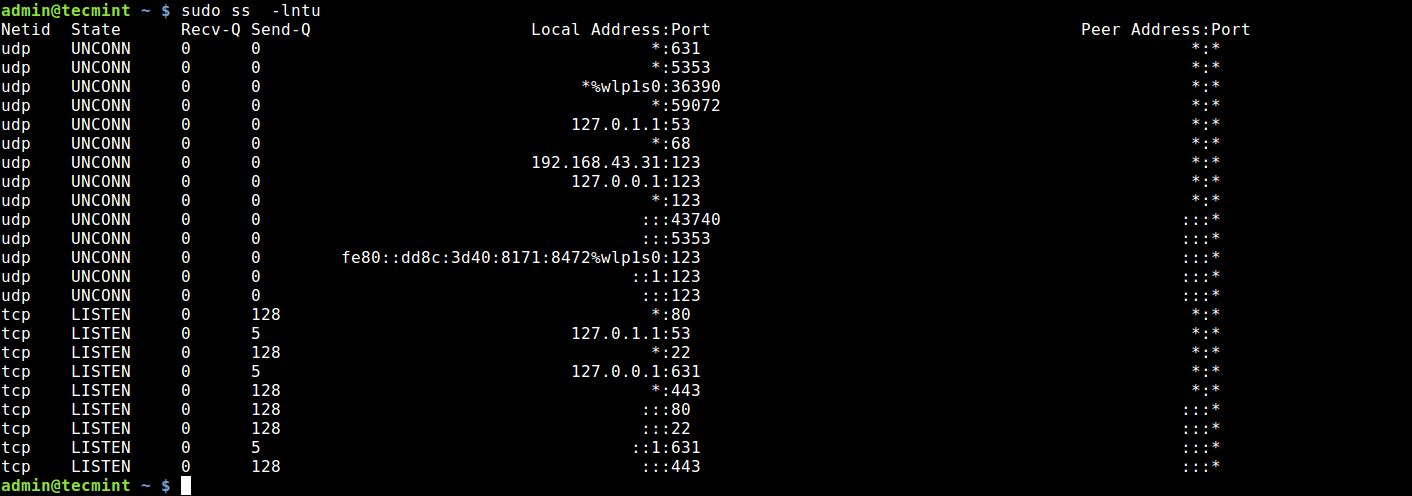
$ sudo netstat -tulpn | grep LISTEN tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 5452/dnsmasq tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1037/cupsd tcp6 0 0 ::1:631 . * LISTEN 1037/cupsd In the above example three services are bound to the loopback address.
IPv4 services bound to the loopback address «127.0.0.1» are only available on the local machine. The equivalent loopback address for IPv6 is «::1». The IPv4 address «0.0.0.0» means «any IP address», which would mean that other machines could potentially connect to any of the locally configured network interfaces on the specific port.
Another method is to use the lsof command:
$ sudo lsof -nP -i | grep LISTEN cupsd 1037 root 9u IPv6 11276 0t0 TCP [::1]:631 (LISTEN) cupsd 1037 root 10u IPv4 11277 0t0 TCP 127.0.0.1:631 (LISTEN) dnsmasq 5452 nobody 5u IPv4 212707 0t0 TCP 127.0.0.1:53 (LISTEN) For more details see man netstat or man lsof .
4 Ways to Find Out What Ports Are Listening in Linux
The state of a port is either open, filtered, closed, or unfiltered. A port is said to be open if an application on the target machine is listening for connections/packets on that port.
In this article, we will explain four ways to check open ports and also will show you how to find which application is listening on what port in Linux.
1. Using Netstat Command
Netstat is a widely used tool for querying information about the Linux networking subsystem. You can use it to print all open ports like this:
The flag -l tells netstat to print all listening sockets, -t shows all TCP connections, -u displays all UDP connections and -p enables printing of application/program name listening on the port.
To print numeric values rather than service names, add the -n flag.
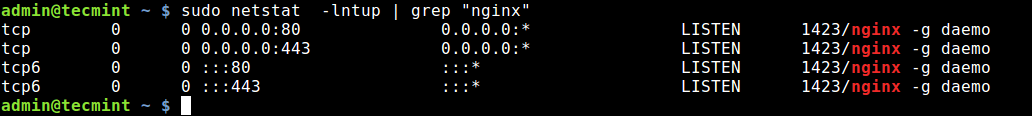
You can also use grep command to find out which application is listening on a particular port, for example.
$ sudo netstat -lntup | grep "nginx"
Alternatively, you can specify the port and find the application bound to, as shown.
$ sudo netstat -lntup | grep ":80"
2. Using ss Command
ss command is another useful tool for displaying information about sockets. It’s output looks similar to that of netstat. The following command will show all listening ports for TCP and UDP connections in numeric value.
3. Using Nmap Command
Nmap is a powerful and popular network exploration tool and port scanner. To install nmap on your system, use your default package manager as shown.
$ sudo apt install nmap [On Debian/Ubuntu] $ sudo yum install nmap [On CentOS/RHEL] $ sudo dnf install nmap [On Fedora 22+]
To scan all open/listening ports in your Linux system, run the following command (which should take a long time to complete).
$ sudo nmap -n -PN -sT -sU -p- localhost
4. Using lsof Command
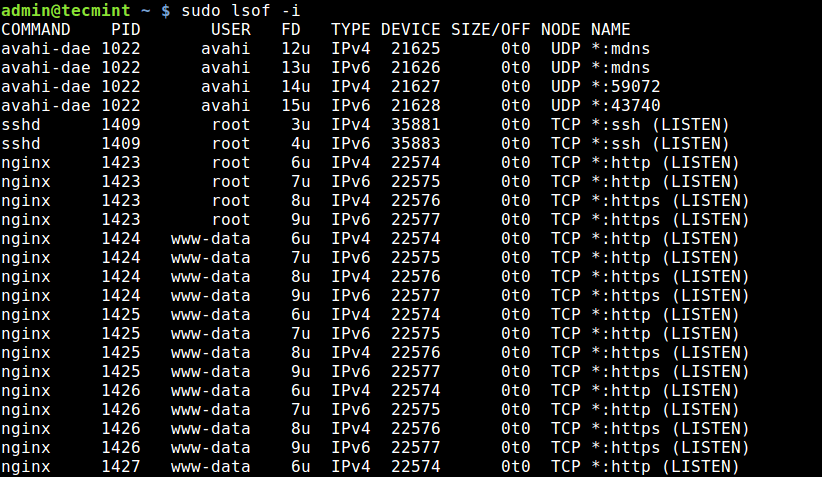
The final tool we will cover for querying open ports is lsof command, which is used to list open files in Linux. Since everything is a file in Unix/Linux, an open file may be a stream or a network file.
To list all Internet and network files, use the -i option. Note that this command shows a mix of service names and numeric ports.
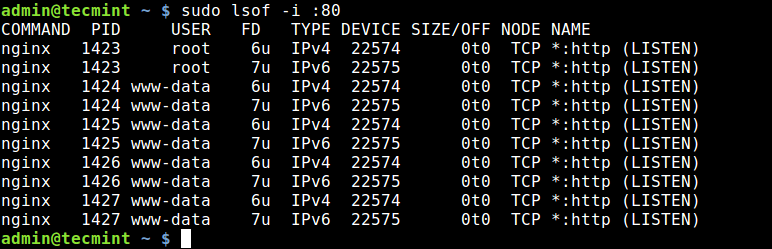
To find which application is listening on a particular port, run lsof in this form.
That’s all! In this article, we have explained four ways to check open ports in Linux. We also showed how to check which processes are bound upon particular ports. You can share your thoughts or ask any questions via the feedback form below.
How to Check (Scan) for Open Ports in Linux
In this tutorial, we will discuss many methods for determining which ports on your Linux system are available to the outside world.
Introduction
One of the first things to check when troubleshooting network connectivity issues or establishing a firewall is whether ports are truly open on your machine.
In this tutorial, we will discuss many methods for determining which ports on your Linux system are available to the outside world.
What is Open Port?
A program that listens on a network port is known as a listening port. You may retrieve a list of your system’s listening ports by using tools like ss , netstat , or lsof to query the network stack. Using a firewall, each listening port can be opened or blocked (filtered).
A network port that admits incoming packets from faraway destinations is known as an open port.
For instance, if your web server listens on ports 80 and 443 and those ports are open on your firewall, anyone (excluding blocked ips) can use his browser to view websites housed on your web server. Both ports 80 and 443 are open in this scenario.
Open ports can be a security issue since attackers can use them to exploit vulnerabilities or carry out other types of attacks. All other ports should be closed and just the ports required for your application’s operation should be exposed.
Check Open Ports with nmap
Nmap is a network scanning program capable of scanning both single hosts and big networks. It’s mostly used for penetration testing and security assessments.
When it comes to port scanning, nmap should be your first choice if it is available. Nmap can determine the Mac address, OS type, kernel versions, and much more in addition to port scanning.
Which ports are listening for TCP connections from the network can be determined by using the following command from the console:
The -sT option instructs nmap to scan for TCP ports, whereas the -p- option instructs it to scan for all 65535 ports. If the -p- option is not specified, nmap will only scan the 1000 most popular ports.
Output Starting Nmap 7.60 ( https://nmap.org ) at 2019-07-09 23:10 CEST Nmap scan report for 10.10.8.8 Host is up (0.0012s latency). Not shown: 998 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 08:00:27:05:49:23 (Oracle VirtualBox virtual NIC) Nmap done: 1 IP address (1 host up) scanned in 0.41 seconds Only ports 22 , 80 , and 8069 are open on the target system, according to the output.
Instead of -sT , use -sU to scan for UDP ports:
Visit the nmap man page for more information and to learn about all of this tool’s other useful features.
Check Open Ports with netcat
Netcat (or nc ) is a command-line utility that uses the TCP or UDP protocols to read and write data across network connections.
Netcat can scan a single port or a range of ports.
To search for open TCP ports on a distant system with IP address 10.10.8.8 in the range 20-80 , for example, execute the command:
The -z option instructs nc to scan only for open ports and not transfer any data, whereas the -v option provides more detailed information.
This is what the output will look like:
Output The -z option instructs nc to scan only for open ports and not transfer any data, whereas the -v option provides more detailed information. This is what the final product will look like: If you just want the lines with open ports written on the screen, use the grep command to filter the results.
nc -z -v 10.10.8.8 20-80 2>&1 | grep succeeded Output Connection to 10.10.8.8 22 port [tcp/ssh] succeeded! Connection to 10.10.8.8 80 port [tcp/http] succeeded! Pass the -u argument to the nc command to scan for UDP ports:
nc -z -v -u 10.10.8.8 20-80 2>&1 | grep succeeded Check Open Ports using Bash Pseudo Device
The Bash shell /dev/tcp/.. or /dev/udp/.. pseudo-device can also be used to determine whether a port is open or closed.
Bash will open a TCP or UDP connection to the specified host on the specified port when a command is run on a /dev/$PROTOCOL/$HOST/$IP pseudo-device.
The if..else statement below will check if port 443 on kernel.org is open:
if timeout 5 bash -c '/dev/null' then echo "Port is open" else echo "Port is closed" fi What is the purpose of the code above?
Because the default timeout when connecting to a port via a pseudo-device is so long, we’re utilizing the timeout command to kill the test command after 5 seconds. The test command will return true if the connection to kernel.org port 443 is established.
Use the for loop to check for a port range:
for PORT in ; do timeout 1 bash -c "/dev/null" && echo "port $PORT is open" done You will get an output like below:
Output port 22 is open port 80 is open Conclusion
We’ve taught you how to scan for open ports with a variety of tools. You can also check for open ports using other utilities and methods, such as the Python socket module, curl , telnet , or wget .
If you have any queries, please leave a comment below and we’ll be happy to respond to them.
5 ways to check if a Port is open on a remote Linux PC
T here is an ample number of ways to check for any open ports on a remote Linux PC. Knowing open ports on a Linux machine helps system administrators to connect to the remote PC for troubleshooting system and cloud server issues.
TCP and UDP ports
TCP stands for Transmission Control Protocol. In this method, the computers get connected directly until the data transfer is taking place. Therefore, with this method, the data transfer is guaranteed and is reliable but puts a higher load on the server as it has to monitor the connection and the data transfer too.
UDP stands for User Datagram Protocol. Using this method, the data is sent in the form of little packages into the network with the hope that it reaches the final destination. It means the two computers are not connected directly to each other. This method does not provide any guarantee that the data you send will ever reach its destination. Load on the server is less, and so this method is used commonly by the system administrators first to try something that’s not so important.
Now that you know the types are ports on a Linux system, let’s get started with ways of finding the ones that are open.
Best ways to check if a Port is open on a Linux PC
There are multiple ways you can do it. However, the most reliable way to do this is by using the following commands:
- nc: netcat command
- nmap: network mapper tool
- telnet: telnet command
- echo > /dev/tcp/..
- netstat – tuplen
Let’s go through each method one by one.
1. netcat command
netcat is a simple Unix utility that can be used to write and read data using UDP and TCP protocol across network connections.
The primary reason for its design is to provide a back-end tool that works with the scripts and programs. It is also an exploration and network debugging tool that offers tons of features.
To use it, you need to install it in your distro using the respective installation commands.