- FTP Server
- vsftpd — FTP Server Installation
- Anonymous FTP Configuration
- User Authenticated FTP Configuration
- Securing FTP
- References
- Ftp and sftp in linux
- Learn Latest Tutorials
- Preparation
- Trending Technologies
- B.Tech / MCA
- Javatpoint Services
- Training For College Campus
- Umftpd – Super Easy Way to Create FTP/SFTP Server in Linux Desktop
- Step 1: Install umftpd
- Step 2: Start a FTP/SFTP/FTPS Server
- Step 3: Access the FTP/SFTP/FTPS Server
- Step 4: Access the Server outside of Local Network
FTP Server
File Transfer Protocol (FTP) is a TCP protocol for downloading files between computers. In the past, it has also been used for uploading but, as that method does not use encryption, user credentials as well as data transferred in the clear and are easily intercepted. So if you are here looking for a way to upload and download files securely, see the OpenSSH documentation instead.
FTP works on a client/server model. The server component is called an FTP daemon. It continuously listens for FTP requests from remote clients. When a request is received, it manages the login and sets up the connection. For the duration of the session it executes any of commands sent by the FTP client.
Access to an FTP server can be managed in two ways:
In the Anonymous mode, remote clients can access the FTP server by using the default user account called “anonymous” or “ftp” and sending an email address as the password. In the Authenticated mode a user must have an account and a password. This latter choice is very insecure and should not be used except in special circumstances. If you are looking to transfer files securely see SFTP in the section on OpenSSH-Server. User access to the FTP server directories and files is dependent on the permissions defined for the account used at login. As a general rule, the FTP daemon will hide the root directory of the FTP server and change it to the FTP Home directory. This hides the rest of the file system from remote sessions.
vsftpd — FTP Server Installation
vsftpd is an FTP daemon available in Ubuntu. It is easy to install, set up, and maintain. To install vsftpd you can run the following command:
Anonymous FTP Configuration
By default vsftpd is not configured to allow anonymous download. If you wish to enable anonymous download edit /etc/vsftpd.conf by changing:
During installation a ftp user is created with a home directory of /srv/ftp . This is the default FTP directory.
If you wish to change this location, to /srv/files/ftp for example, simply create a directory in another location and change the ftp user’s home directory:
sudo mkdir -p /srv/files/ftp sudo usermod -d /srv/files/ftp ftp After making the change restart vsftpd:
sudo systemctl restart vsftpd.service Finally, copy any files and directories you would like to make available through anonymous FTP to /srv/files/ftp , or /srv/ftp if you wish to use the default.
User Authenticated FTP Configuration
By default vsftpd is configured to authenticate system users and allow them to download files. If you want users to be able to upload files, edit /etc/vsftpd.conf :
sudo systemctl restart vsftpd.service Now when system users login to FTP they will start in their home directories where they can download, upload, create directories, etc.
Similarly, by default, anonymous users are not allowed to upload files to FTP server. To change this setting, you should uncomment the following line, and restart vsftpd:
Warning
Enabling anonymous FTP upload can be an extreme security risk. It is best to not enable anonymous upload on servers accessed directly from the Internet.
The configuration file consists of many configuration parameters. The information about each parameter is available in the configuration file. Alternatively, you can refer to the man page, man 5 vsftpd.conf for details of each parameter.
Securing FTP
There are options in /etc/vsftpd.conf to help make vsftpd more secure. For example users can be limited to their home directories by uncommenting:
You can also limit a specific list of users to just their home directories:
chroot_list_enable=YES chroot_list_file=/etc/vsftpd.chroot_list After uncommenting the above options, create a /etc/vsftpd.chroot_list containing a list of users one per line. Then restart vsftpd:
sudo systemctl restart vsftpd.service Also, the /etc/ftpusers file is a list of users that are disallowed FTP access. The default list includes root, daemon, nobody, etc. To disable FTP access for additional users simply add them to the list.
FTP can also be encrypted using FTPS. Different from SFTP, FTPS is FTP over Secure Socket Layer (SSL). SFTP is a FTP like session over an encrypted SSH connection. A major difference is that users of SFTP need to have a shell account on the system, instead of a nologin shell. Providing all users with a shell may not be ideal for some environments, such as a shared web host. However, it is possible to restrict such accounts to only SFTP and disable shell interaction.
To configure FTPS, edit /etc/vsftpd.conf and at the bottom add:
Also, notice the certificate and key related options:
rsa_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem rsa_private_key_file=/etc/ssl/private/ssl-cert-snakeoil.key By default these options are set to the certificate and key provided by the ssl-cert package. In a production environment these should be replaced with a certificate and key generated for the specific host. For more information on certificates see Security — Certificates.
Now restart vsftpd, and non-anonymous users will be forced to use FTPS:
sudo systemctl restart vsftpd.service To allow users with a shell of /usr/sbin/nologin access to FTP, but have no shell access, edit /etc/shells adding the nologin shell:
# /etc/shells: valid login shells /bin/csh /bin/sh /usr/bin/es /usr/bin/ksh /bin/ksh /usr/bin/rc /usr/bin/tcsh /bin/tcsh /usr/bin/esh /bin/dash /bin/bash /bin/rbash /usr/bin/screen /usr/sbin/nologin This is necessary because, by default vsftpd uses PAM for authentication, and the /etc/pam.d/vsftpd configuration file contains:
auth required pam_shells.so The shells PAM module restricts access to shells listed in the /etc/shells file.
Most popular FTP clients can be configured to connect using FTPS. The lftp command line FTP client has the ability to use FTPS as well.
References
Ftp and sftp in linux
Learn Latest Tutorials
Preparation
Trending Technologies
B.Tech / MCA
Javatpoint Services
JavaTpoint offers too many high quality services. Mail us on h[email protected], to get more information about given services.
- Website Designing
- Website Development
- Java Development
- PHP Development
- WordPress
- Graphic Designing
- Logo
- Digital Marketing
- On Page and Off Page SEO
- PPC
- Content Development
- Corporate Training
- Classroom and Online Training
- Data Entry
Training For College Campus
JavaTpoint offers college campus training on Core Java, Advance Java, .Net, Android, Hadoop, PHP, Web Technology and Python. Please mail your requirement at [email protected].
Duration: 1 week to 2 week
Like/Subscribe us for latest updates or newsletter 




Umftpd – Super Easy Way to Create FTP/SFTP Server in Linux Desktop
FTP, File Transfer Protocol, is specially designed for transferring large files from a server to a client. FTPS adds a layer to the FTP protocol to make it more sure. And, SFTP is another protocol based on SSH (Secure Shell).
For Linux server without GUI, user has to struggle with Linux commands and configurations to setup a FTP/SFTP server. Which, is always painful for beginners. But, once you got a desktop environment, things will be quite easy via ‘umftpd’!
It’s a free open-source GTK4 tool that uses the lightweight, fast and scalable Python FTP server library (pyftpdlib) to provide the service. With it, user can access the server files from anywhere with a file manager or FTP client.
Tip: For smaller files, a HTTP server could be more efficient! And, you may create http server via single command in Linux for temporary use.
Step 1: Install umftpd
Usermode FTP Server, umftpd in short, is available as Flatpak package that works in most Linux system.
1. First, install the flatpak daemon. Ubuntu user can press Ctrl+Alt+T on keyboard and run the command below to get it:
Fedora, Linux Mint, Pop! OS, etc have Flatpak support out-of-the-box. Other Linux can follow the official setup guide to get it:
2. After that, run the single command in a terminal window to install the app:
flatpak install https://dl.flathub.org/repo/appstream/eu.ithz.umftpd.flatpakref
Step 2: Start a FTP/SFTP/FTPS Server
After installation, launch the app either from system start menu or ‘Activities’ overview depends on your desktop environment.
The UI is quite easy to use, simply set a ‘username’ and ‘password’ for authentication in client machines. Choose a folder to serve the files, enable “Read-only” if you don’t want others to upload or edit anything. Select a protocol that you prefer, and change the port if you want.
Once you click on “Start Server“, it goes to new page indicates that server is ready and provides the address, and other information in next screen.
NOTE: The server persists as long as you keep the app screen (see the last screenshot). As it does not run as service in background, it could be only good choice for temporary use.
Step 3: Access the FTP/SFTP/FTPS Server
You can access anywhere with a client or media player with FTP support.
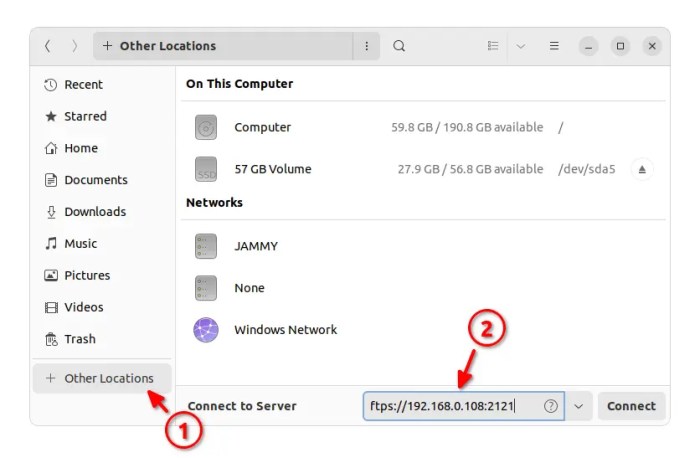
For Linux user, system default file manager usually support it out-of-box. For example, Ubuntu, Fedora, and other Linux with GNOME can access by clicking ‘Other Locations‘ in file manager and type ftp address in the bottom box.
Microsoft Windows 10 & 11 also support accessing FTP out-of-the-box. Simply open File Explorer, type the ftp url in address bar and hit Enter. On macOS, open Finder and select “Go > Connect to Server” to connect.
Step 4: Access the Server outside of Local Network
If your Linux machine is running behind a router in home network, you have to setup port forwarding or DMZ host to be able to access from machine outside your local network.
To do the settings, you have to first login your router by visiting its IP address (usually 192.168.0.1 or 192.168.1.1 ) in web browser. The settings page looks quite different depends on the device manufacturer. So, there won’t be a detailed guide here.
DMZ host is usually an option in advanced or additional settings, allows to set a local IP as host. With it enabled, all external access will go directly to that machine you specified.
Port forwarding only maps a certain port of local machine to external port. Only external IP plus that port will go to the machine you specified.
To stop the FTP/SFTP server, simply go back via app header bar “