- How do I check the SHA1 hash of a file?
- 6 Answers 6
- Python
- Test run:
- How to Verify Checksum on Linux [Beginner Guide]
- How is a Checksum generated?
- Installing GtkHash on Ubuntu
- Using GtkHash
- Verify checksums via Linux command line
- Generating and Verifying SHA256 Checksum with sha256sum
- How accurately does this work?
How do I check the SHA1 hash of a file?
adding this note to whom it may concern: SHA-1 is now compromised, proven by a Google-CWI joint research. TL;DR Don’t use it anywhere carrying any value.
Just to add, while it is compromised, meaning it is not to be used for anything that needs to be cryptographically secure, it’s still a good way to checksum things if security is not a factor
6 Answers 6
Print or check SHA1 (160-bit) checksums. With no FILE, or when FILE is -, read standard input.
If you want to send the file together with its sha1sum output redirect the output to a file:
Send both files and the other party can do a.
It should show OK if the sha1 is correct.
Great! But how do you run sha1sum -c when
or shasum — the default SHA is (if I am correct) SHA1. Also you set it with -a, —algorithm option: shasum -a 1
@PiotrFindeisen — The output of sha1sum is
Without creating local file:
$ sha1sum filename 8dd10000eb1b768800000e1d2fe1c3100005d2dc *filename For checking, go to the directory that contains filename and run this command:
echo "8dd10000eb1b768800000e1d2fe1c3100005d2dc *filename" | sha1sum -c - Thanks, though I don’t think you should have the * in there. Here’s a concrete example: echo ‘b78bb50bdac5ec8c108f34104f788e214ac23635 raspbian.zip’ | sha1sum -c — That will check a file name raspbian.zip in the current directory.
Just in case anyone gets here and is on a mac, there are two spaces between the filename and the output of shasum as of OSX 10.13.3. When I used just one, I got a incorrect formatting error for shasum -c
Navigate to the terminal and key in:
The check argument generates the sha1 hash of filename and compares it with the value stored in filename.sha1 . If it matches OK is displayed and the exit code for the command is 0
@AlexanderMills confirming the sha1 hash tells you that the file you downloaded matches with what the server says it’s offering. So it confirms that you indeed received what you wanted to, instead of a malicious person sending you the wrong file.
For those who are on mac and don’t have coreutils/sha1sum installed.
$ openssl sha1 `mktemp` SHA1(/tmp/tmp.jkyfOWma3t)= da39a3ee5e6b4b0d3255bfef95601890afd80709 this is askubunutu, so being on a Mac would be off-topic 😉 but this should work on ubuntu too, so +1
What are you people talking about? Yes, I get the concept behind sha1sum, but the info above is confusing to say the best. First, Ubuntu does not seem to have sha1sum files — just strings on a web page such as this for Mate 16.04 Beta 1:
bfba577970d573e0ba5095fbb72787de97f88b4b *ubuntu-mate-16.04-beta1-desktop-amd64.iso efcbbc70b10173cea203df30396d0848ba8fa0d8 *ubuntu-mate-16.04-beta1-desktop-i386.iso 8563fec4d66bce851b0800f5ac746f38e4041a6a *ubuntu-mate-16.04-beta1-desktop-powerpc.iso To check the integrity of a downloaded .iso, one opens the terminal program, does «cd Downloads», then sha1sum . After a bit, the terminal will produce a hash such as
efcbbc70b10173cea203df30396d0848ba8fa0d8 ubuntu-mate-16.04-beta1-desktop-i386.iso Next, we have to go to the web page and compare the strings to verify that the verification works. Not nearly as easy as it could be.
Python
Python has excellent hashlib library, that allows calculating multiple hashsums, including sha1 . Here’s a simple script that can do the job:
#!/usr/bin/env python3 import sys import hashlib import os from collections import OrderedDict as od def get_hashsums(file_path): hash_sums = od() hash_sums['md5sum'] = hashlib.md5() hash_sums['sha1sum'] = hashlib.sha1() hash_sums['sha224sum'] = hashlib.sha224() hash_sums['sha256sum'] = hashlib.sha256() hash_sums['sha384sum'] = hashlib.sha384() hash_sums['sha512sum'] = hashlib.sha512() with open(file_path, 'rb') as fd: data_chunk = fd.read(1024) while data_chunk: for hashsum in hash_sums.keys(): hash_sums[hashsum].update(data_chunk) data_chunk = fd.read(1024) results = od() for key,value in hash_sums.items(): resultsGet file checksum linux = value.hexdigest() return results def main(): for path in sys.argv[1:]: print(">>> ",path) for key,value in get_hashsums(path).items(): print(key,value) if __name__ == '__main__': main() Test run:
$ ./hash_sums.py /etc/passwd >>> /etc/passwd md5sum ce5f247e016ba2bb92049fc86158376a sha1sum b8abadf4618b09bd3eebb6064fc2df5b90e5ae03 sha224sum 044579d46e0d969a860602216ea4764465e5618ed714109cf782ff50 sha256sum 53f2ff8997625c958f77aef034f9c96d9fcfc8bcb4bb8a96fd8ac89a5ed5adf6 sha384sum b84b6cafa178147614e6b7903e1b7a342e09d95e3101e55c6a3b5b093a22190f2d367c69b1ee12b1ec59726337a40e9c sha512sum edacca8237d3be5095f392c9d347dce3a5249c79d09f9b99a055b796edd74541b4529c499ff0e4f25e817b702c206073bfe5b0fccae6773680c79ea1e0efa9e2 $ ./hash_sums.py * >>> 3-4-placement.py md5sum a81dd2a6eb122176204cacd92d76d08c sha1sum 4972f8cf08701cdfc6308def05d3ec2eedfcdd9a sha224sum 32c4dad60f59584ba39ce73c1a1c96d4da36ee6fe3fd291145692b2b sha256sum 7460ebf8736b0d6e7be8a1025743d0498871c7013cf5ad4463366fd95fe7576a sha384sum 77de28b4b185d9a5d7d49aef0aad432d37145b914557dc6ecf3e6cdcbd6cd4a1999d717c027489ac99751f066050199b sha512sum 7bf6a8059601c72e1278e321f225fef82f12a7bad73e1e8c5c43c1fcbdc2243934bf7d1ad07534bdbf10e2dd9ea9265e1debcbdf6603bec24ede665d2f651cf5 >>> SHA256SUMS md5sum 3c37318d45676c1db2598aa817b37679 sha1sum 8338b8ae5f749551d131dc28aebb80a2b125d651 sha224sum e89ad392f10a77b0940792a03470f3a23df2f2df9c8b6a91a1c496e0 sha256sum dd4a53f7da270f3b6ab691841ca911a231e20af53d7fabc5a39059b9dbdb036d sha384sum aadfb55856730eb5b7e4192111bfb8fc4c022396a5809cb37fdd8e8b6ac8dbb3b7e462266cde2b34f90d7015fb42fe2b sha512sum baba0ed86ad781daffb5905512459e353b7ca7da7b04cf67a26cfb320906041da2d4bc73673926aab7c98869f25bc2fd6ea0116c21c40c07188e6dcbbba3dbcf >>> answer.md md5sum b6111facdba5978e6cf3a200706ba6fd sha1sum 5c2eb00c4c0c4799d4457d3a84eea283a3a0d249 sha224sum 7172f877ab579e1ee845c723e0d42ff3acb96859cc43a56aebc39f59 sha256sum dc6ac7365f680e98b9f1279d2e22ed21b9b82c988b99b0facd5e8a98ff50ddd6 sha384sum 5082b3b62d677c5b1b8938f871da16c595be16a540bd76bc9c25ea6572dc9020f236237ec310cfa78fdaa1d0c0a51b0f sha512sum 81f21316ab6c5a4038cdcde528766e620988a0ccf53bf2e9932399f4534c070468949a5a43ea68629c07e622404574e46bb20cf60c51da4e2a7a44a1df71d920 How to Verify Checksum on Linux [Beginner Guide]
A checksum is a small-sized datum from a block of digital data for the purpose of detecting errors which may have been introduced during its transmission or storage.
So a checksum is a long string of data containing various letters and numbers. You’ll generally find them when downloading files from the web, e.g. Linux distribution images, software packages, etc.
The most common use of checksums is for checking if a downloaded file is corrupted.
For instance, the Ubuntu MATE download page includes an SHA-256 checksum for every image it makes available. So after you’ve downloaded an image, you can generate an SHA-256 checksum for it and verify that the checksum value matches the one listed on the site.
If it doesn’t, that means your downloaded image’s integrity is compromised (maybe it was corrupted during the download process). We will use an Ubuntu MATE “ubuntu-mate-16.10-desktop-amd64.iso” image file for this guide.
How is a Checksum generated?
Each checksum is generated by a checksum algorithm. Without going into the technical details let’s just say it takes a file as input and outputs the checksum value of that file. There are various algorithms for generating checksums. The most popular checksum algorithms are:
Let’s see how to verify a checksum on Linux.
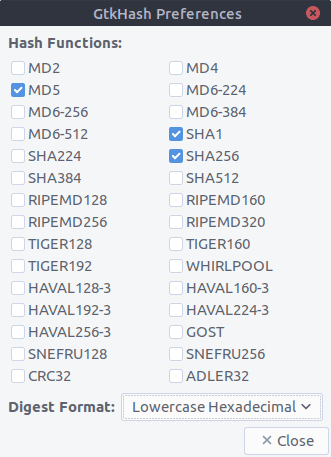
Installing GtkHash on Ubuntu
To install GtkHash on your Ubuntu system, simply run the following command:
That’s it. Then select the checksum algorithms to use:
- Go to Edit >Preferences in the menu.
- Select the ones you’d like to use.
- Hit the Close button.
By default, MD5, SHA-1 and SHA256 are selected.
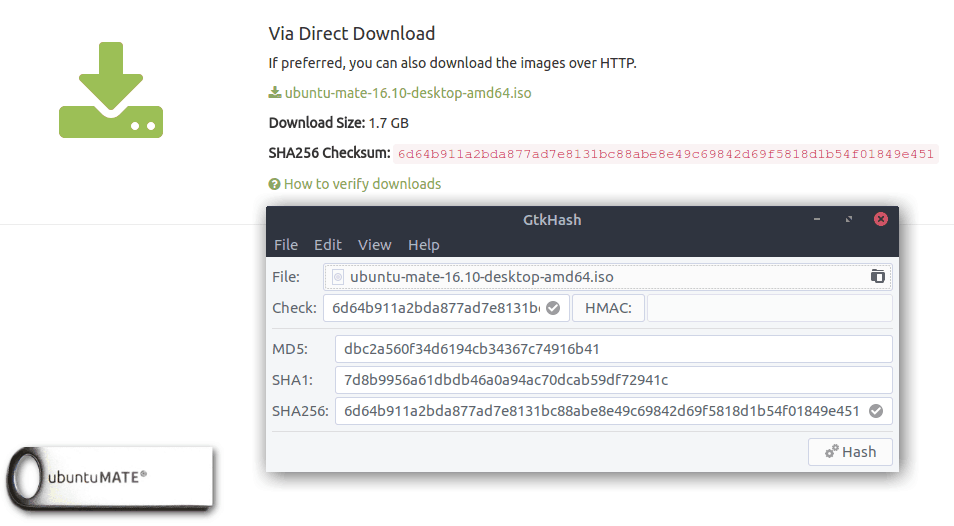
Using GtkHash
Using it is quite straight-forward.
- Select the file you want to check.
- Get the Checksum value from the website and put it in the Check box.
- Click the Hash button.
- This will generate the checksum values with the algorithms you selected.
- If any one of them matches with the Check box, it will show a small tick sign beside it.
Here’s an example showing GtkHash generating a checksum for the Ubuntu MATE iso image (ubuntu-mate-16.10-desktop-amd64.iso):
Verify checksums via Linux command line
Every Linux distribution comes with tools for various checksum algorithms. You can generate and verify checksums with them. The command-line checksum tools are the following:
- MD5 checksum tool is called md5sum
- SHA-1 checksum tool is called sha1sum
- SHA-256 checksum tool is called sha256sum
There are some more available, e.g. sha224sum, sha384sum, etc. All of them use similar command formats. Let’s see an example using sha256sum. We’ll use the same “ubuntu-mate-16.10-desktop-amd64.iso” image file that we used before.
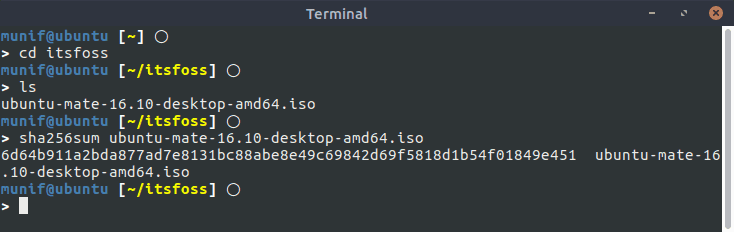
Generating and Verifying SHA256 Checksum with sha256sum
First go to the directory where the .iso image is stored:
Now, to generate the SHA-256 checksum, enter the following command:
sha256sum ubuntu-mate-16.10-desktop-amd64.isoYou’ll see the SHA-256 checksum in your terminal window! Easy, isn’t it?
If the generated checksum matches the one provided on the Ubuntu MATE download page, that will mean no data was changed while you downloaded the file – in other words, your downloaded file is not corrupted.
The other tools mentioned work similarly.
How accurately does this work?
If you’re wondering how accurately these checksums detect corrupted files – if you delete or change even one character from any one of the text files inside the iso image, the checksum algorithm will generate a totally different value for that changed image. And that will definitely not match the checksum provided on the download page.
Do you checksum?
One of the suggested steps while installing Linux is to verify the checksum of your Linux ISO. Do you always follow this step or do you do it only when something goes wrong with the installation?
Was this guide helpful? If you have any questions, let us know! And if you need a similar guide for something else, reach out to us, we’re here to help.