- How to Verify SHA256 Checksum of File in Linux
- What is a SHA256 Checksum?
- Verifying SHA256 Checksum of a File in Linux
- How to verify the sha256 checksum of a file on Linux
- Prerequisites
- What is SHA256?
- What is SHA256 Checksum?
- How to Generate Sha256 Checksum?
- How to Verify SHA256 Checksum with sha256sum
- Command-Line Method
- GUI Method
- Conclusion
- About the author
- Prateek Jangid
- How to Get md5 Hash Of A File
- Install md5sum
- Generate Md5sum of a File
- Verify Online Files
- Conclusion
- Exercise
- About the author
- John Otieno
How to Verify SHA256 Checksum of File in Linux
Internet security is one of the most important aspects when it comes to the world wide web. There has been constant research and development to improve the security of applications and files on the Internet and thus to prevent malicious use.
Downloadable files over the Internet are often the target of attacks on the Internet. As thousands and thousands of people download these files regularly, it becomes especially important to protect such files.
In this article, we will learn about checksums and how they can be used to authenticate a downloaded file from the Internet.
What is a SHA256 Checksum?
A Checksum is a cryptographic signature of a file. It is basically a string that uniquely represents the file; thus if a file is ‘tampered‘ with or ‘modified‘, its checksum value will change and the user will know that the file has been changed.
There are a number of mathematical algorithms for generating Checksum for a file in Linux. One such algorithm which is very popularly used is SHA256, which stands for ‘Secure Hash Algorithm 256‘ and was developed by the United States National Security Agency.
This algorithm breaks down the data of the file into small-sized parts and creates and combines the hash values for each part to create the checksum value. The SHA256 Checksum is usually provided in a text file or directly as a string along with the main file, in its download section on the Internet.
Verifying SHA256 Checksum of a File in Linux
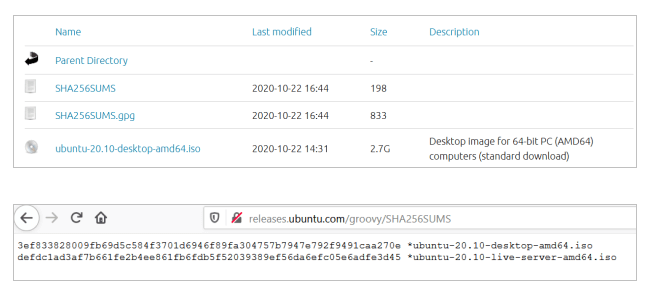
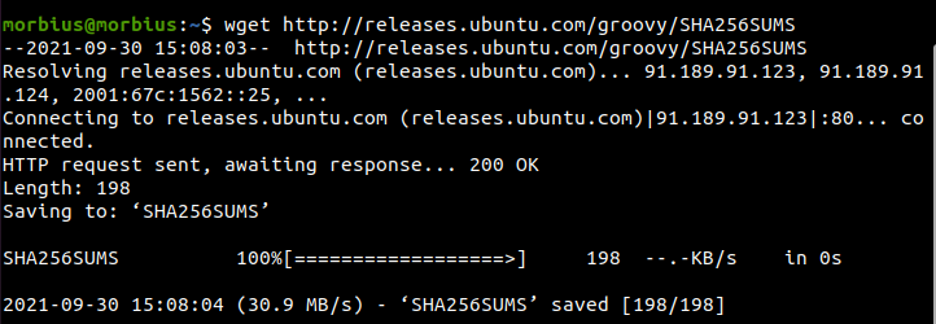
Let’s take an example of Ubuntu Groovy (20.10) ISO file download and try to verify its checksum. Note that along with the ISO files, the text file ‘SHA256SUMS‘ is provided which contains the checksum values.
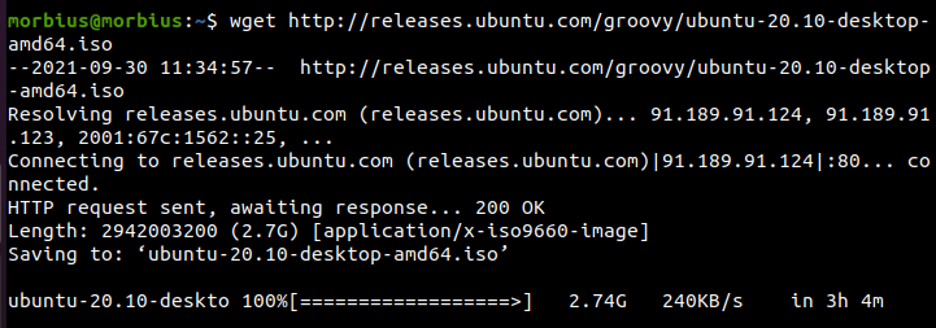
Download the ISO file for Ubuntu 20.10 desktop and the file SHA256SUMS in the same folder and go to the folder where they are downloaded.
$ wget http://releases.ubuntu.com/groovy/ubuntu-20.10-desktop-amd64.iso $ wget http://releases.ubuntu.com/groovy/SHA256SUMS $ cd ~/Downloads
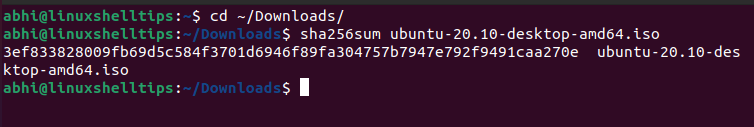
To generate a checksum of the ISO file, run the following:
$ sha256sum ubuntu-20.10-desktop-amd64.iso
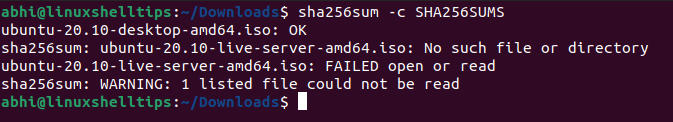
To compare the checksum to the value in the file SHA256SUMS, run the command with the ‘-c’ flag. This will take all the checksums in the file, compare them with the corresponding filename, and print the filename that matches the checksum.
As seen above, the ISO file matches the original checksum, and hence we can be sure that the file was not modified or tampered with in any way during the download.
The other output is regarding the 2nd checksum in the file: for the live server ISO file which is not downloaded and hence the command prints those errors.
Conclusion
Today we learned how to verify the sha256 checksum of a file in Linux. Make sure you check out the manual page of sha256sum (by running ‘man sha256sum‘) to learn more in-depth about the command.
Thanks for reading and let us know your thoughts or questions in the comments below!
How to verify the sha256 checksum of a file on Linux
An important element of internet safety is its security. Continuous development and research are being done to prevent malicious use and improve internet files and applications.
It is often unsafe to download files from the internet, which is often dangerous. It is also necessary to download these files for some vital work. Thousands of such files are also downloaded by millions of people. Therefore, such files ought to be protected especially well.
This article will learn about checksum and verify the sha256 checksum of a file on Linux.
Prerequisites
- Terminal (non-sudoers can easily work there)
- Validate the checksum file (it is necessary)
- ISO file (downloaded)
What is SHA256?
According to the U.S. National Security Agency, this algorithm is part of the SHA2 family of algorithms. The acronym SHA stands for ‘Secure Hash Algorithm,’ and 256 is the number of bits used in these algorithms.
What is SHA256 Checksum?
It is a cryptographic signature of any file that it can use to identify or detect errors introduced during transmission or storage. A checksum measures the size of a block of digital data. It uniquely represents a file that is a string. Linux has several mathematical algorithms to generate a checksum for a file.
Typically, on the internet, the SHA256 checksum is provided as a string directly in the main file or as a text file in the download section. Through the original checksum file, we can verify the checksum with the Checksum Utility tool.
How to Generate Sha256 Checksum?
A checksum algorithm generates a checksum. There are various checksum algorithms.
The secure hash algorithm generates a checksum value by breaking the file’s data into smaller chunks, creating a hash value for each part, and adding them.
SHA256 creates the digest or hash value of the file, and once the file is tampered with or modified, the original SHA256 digest value is changed.
How to Verify SHA256 Checksum with sha256sum
We can verify sha256 checksum in two ways,
Command-Line Method
There are tools available in each Linux distribution for different checksum algorithms. We can verify and generate the checksum using these tools. Some command-line checksums are as follows.
Apart from all this, sha384sum, sha224sum, etc., are also available, which use similar command formats. Here we will verify the checksum with the help of sha256sum using “OpenSUSE Leap 15.2”.
Command-Line utility SHA256sum
We do not need to perform any installation for sha256sum as it is a part of GNU Coreutils. Checksum files are available for download from most distributions with ISO files.
We will download the OpenSUSE Leap 15.2 ISO file first and then download its checksum with the help of the wget command. It is worth noting that along with ISO files, the text file ‘SHA256SUMS’ is also provided and contains checksum values.
Once the checksum is downloaded, we can generate the checksum with the help of the below-mentioned command.
sha256sum openSUSE-Leap-15.2-DVD-x86_64.iso
0fd2d4e630b6579b933b5cb4930a8100acca6b4e29cd2738c4b7a9b2f76d80e4 openSUSE-Leap-15.2-DVD-x86_64.iso
The command with the ‘-c’ flag is run to compare the checksum with the value in the SHA256SUMS file. The filename and checksum compare all the files in the directory with the corresponding filename and calculate each file’s checksum.
$ sha256sum -c openSUSE-Leap-15.2-DVD-x86_64.iso.sha256
openSUSE-Leap-15.2-DVD-x86_64.iso: OK
sha256sum: WARNING: 14 lines are improperly formatted
Based on the ISO file’s checksum, we can see it matches the original file. We received OK in the output, which means that the file downloaded is not corrupted and tampered with. As a result, we can see that no files have been tampered with or modified during the download.
If ‘Fail’ is written in the output instead of ‘OK,’ it shows that our file is corrupted and tampered with while downloading it. We have to download the file back; otherwise, we cannot download the respective distribution.
GUI Method
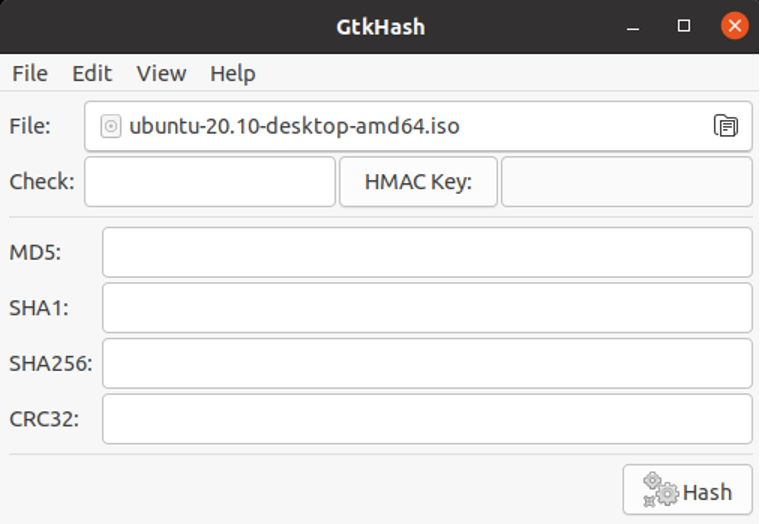
With the help of GtkHash, we can use a graphical method to verify the checksum. It can verify checksums by using GtkHash, which supports MD5, SHA, and other checksum algorithms.
Installing GtkHash on Ubuntu
We can easily install GtkHash in our Ubuntu system by simply running the command written below:
That’s all we need to do. Select the checksum algorithm of our choice.
- In the menu, select Edit > Preferences.
- Choose the ones we want to use.
- Click the Close button.
Using GtkHash
The application is relatively easy to use.
- The first thing we need to do is select the file to be reviewed.
- Afterward, enter the checksum value found on the website in the check box.
- Press the Hash button.
- It generates the checksum value with our chosen algorithm.
- If the check box matches any of them, it shows a small tick mark next to it.
Conclusion
In this article, we have seen how checksum accurately detects corrupt files. It is so accurate that if we replace or delete a character from any text file inside the ISO image, the checksum algorithm generates an entirely different value for that changed image. We hope that you have understood everything well from this article.
About the author
Prateek Jangid
A passionate Linux user for personal and professional reasons, always exploring what is new in the world of Linux and sharing with my readers.
How to Get md5 Hash Of A File
Message-Digest algorithm, commonly known as md5 hash, is a type of cryptographic hash function mainly used to verify the integrity of files. Md5 is a 128-bit message digest produced after running the MD5 function against a file.
Md5 has its flaws and is therefore not a very good choice for certain encryption methods, but it is very well suited for file verification. It works by creating a checksum of a file and comparing the result to the original. That means if there are changes to a file, there is no way it can produce a digest value similar to the original. The value stays constant no matter where generated or how many times as long as the file remains unchanged.
For this guide, we shall look at ways to generate an md5 hash value of a file. That will allow you to verify the integrity of files either from remote locations or on your local machine.
Install md5sum
In Linux and almost major Unix and Unix-Like systems, they come pre-installed with an md5 tool. The most common one is md5sum. By default, you should find it available in your system.
If you do not have the tool installed, you can use the package manager of your system.
Debian/Ubuntu
On Ubuntu and other Debian based distributions, use apt as:
REHL/CentOS
On REHL and CentOS, use yum as:
Arch/Manjaro
If you are on Manjaro or other arch based distributions, use Pacman using the command:
Fedora
Finally, on Fedora systems, use the dnf command as:
Generate Md5sum of a File
With the tool installed, we can proceed and generate a md5sum for a file. You can use any basic file available in your system. In my example, I am using the /etc/hosts available in Linux systems.
To generate the md5sum of a file, simply use the md5sum command followed by the filename, which you can see in the command below:
The above command should generate a hash value of the file as shown in the output below:
Once the contents of the file change, the md5sum value becomes completely different. For example, add a value to the/etc/hosts file.
Add the following entry to the file (feel free to change to any way you see fit).
If you try to calculate the md5 value of the file with the new contents as:
The hash value is different as shown in the output below:
If you revert the file to its original contents, the md5sum value is similar to the original, allowing you to know when a file has changed.
NOTE: The md5 value will be similar to the original even if the file gets renamed. This is because md5 is calculated based on file contents and not filename.
Verify Online Files
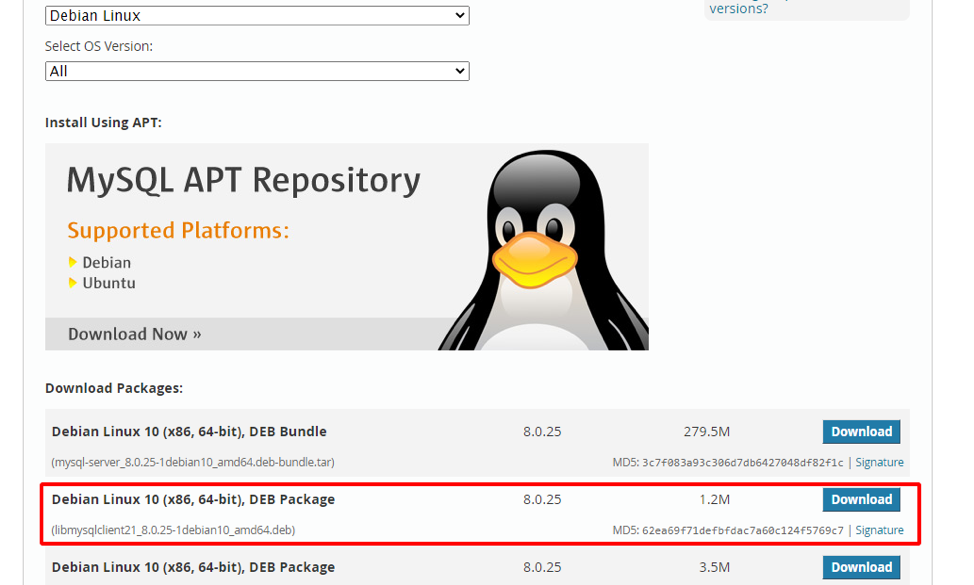
Suppose you want to verify the integrity of a file and ensure it is tamper-proof. To do this, all you need is the original md5 value. In my example, I am using a simple deb package of MySQL from the resource below:
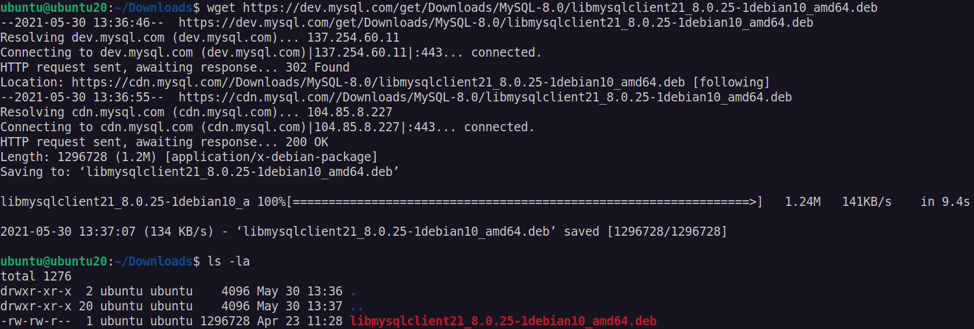
Download the file with wget using the command as:
Once the file has downloaded:
Let us now verify the md5 value using a command:
If the file has not been modified in any way, you should get a similar value as the original as shown:
Conclusion
This tutorial looked at a simple method to verify the md5 checksum of files and verify their modification state.
Here is a quick exercise for you.
Exercise
Create a simple bash script that checks if a file md5 value has any recorded modification every 5 minutes. If the file has changed, delete the file and shut down the system.
That should be a fun exercise!
About the author
John Otieno
My name is John and am a fellow geek like you. I am passionate about all things computers from Hardware, Operating systems to Programming. My dream is to share my knowledge with the world and help out fellow geeks. Follow my content by subscribing to LinuxHint mailing list