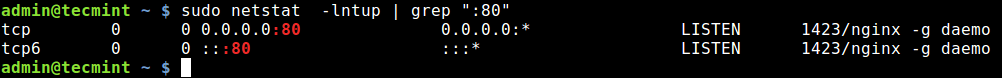- How can I see what ports are open on my machine?
- 10 Answers 10
- nmap (install)
- How to find ports opened by process ID in Linux?
- -p (Linux):
- How to Check Ports in Use in Linux (Listening Ports)
- 1. Using ss Command
- 2. Using Netstat Command
- 3. Using lsof Command
- Conclusion
- About The Author
- James Kiarie
- 4 Ways to Find Out What Ports Are Listening in Linux
- 1. Using Netstat Command
- 2. Using ss Command
- 3. Using Nmap Command
- 4. Using lsof Command
How can I see what ports are open on my machine?
I would like to see what ports are open on my machine, e.g. what ports my machine is listening on. E.g. port 80 if I have installed a web server, and so on. Is there any command for this?
10 Answers 10
If the netstat command is not available, install it with:
sudo apt install net-tools -l already filters for listening. grep LISTEN won’t help beyond hiding 2 lines of header information.
-t : tcp, -l : listening socket, -p : show pid and program name, -n : print 127.0.0.1:80 instead of localhost:http . Reference: linux.die.net/man/8/netstat
The expanded command is sudo netstat —tcp —listening —programs —numeric . There’s no need to use grep unless you want to eliminate column headers.
nmap (install)
Nmap («Network Mapper») is a free and open source utility for network exploration or security auditing.
Use nmap 192.168.1.33 for internal PC or nmap external IP address .
More information man nmap .
Zenmap is the official GUI frontend.
Remember that there is a difference between nmap localhost and nmap 192.168.0.3 (or what ever you machine IP is)
I think netstat is a better answer to this. netstat will list what the system is listening on directly, and without using an additional application or doing unnecessary calls over localhost or thought the network.
This is stupid. If you have access to the computer, just use netstat -ln . You’ll instantly see all the open ports.
nmap localhost didn’t find services that were bound only to localhost. For example, I run influxd with bind-address:localhost:8086 . That didn’t show up in sudo nmap localhost , but did show up in sudo netstat -tulpn .
Other good ways to find out what ports are listenting and what your firewall rules are:
To list open ports use the netstat command.
$ sudo netstat -tulpn | grep LISTEN tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 5452/dnsmasq tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1037/cupsd tcp6 0 0 ::1:631 . * LISTEN 1037/cupsd In the above example three services are bound to the loopback address.
IPv4 services bound to the loopback address «127.0.0.1» are only available on the local machine. The equivalent loopback address for IPv6 is «::1». The IPv4 address «0.0.0.0» means «any IP address», which would mean that other machines could potentially connect to any of the locally configured network interfaces on the specific port.
Another method is to use the lsof command:
$ sudo lsof -nP -i | grep LISTEN cupsd 1037 root 9u IPv6 11276 0t0 TCP [::1]:631 (LISTEN) cupsd 1037 root 10u IPv4 11277 0t0 TCP 127.0.0.1:631 (LISTEN) dnsmasq 5452 nobody 5u IPv4 212707 0t0 TCP 127.0.0.1:53 (LISTEN) For more details see man netstat or man lsof .
How to find ports opened by process ID in Linux?
Hmm..I don’t seem to have the —all and —program options. I’m using OSX. Brew doesn’t seem to have a formula for it either.
-n will dramatically speed things up by not resolving hostnames. netsta -tupan is a good default command all and easy to remember.
You can use the command below:
As a side note, netstat -ao will read the /proc/PID/tcp etc to see the ports opened by the process. This means that its reading information supplied by the system (the linux KERNEL), and is in no way directly looking on the network interface or other means. Same goes for lsof.
If you are doing this as a security measure, you failed. You should never (NEVER EVER) trust the output of netstat, even if you are 100% sure you are in fact running a real netstat program (as opposed to a trojaned version) or any other program that reads the /proc filesystem. Some people seem to think that netstat, ls, ps or any other of the standard unix tools do some sort of magic and poll information from the sources, the truth is all of them rely on the /proc filesystem to get all of their data, which can be easily subverted by a rootkit or hypervisor.
If you’re dealing with a rootkitted system or a compromised hypervisor, you can’t trust anything, including something that purports to look directly at the network interface.
You can use the netstat command line tool with the -p command line argument:
-p (Linux):
Process: Show which processes are using which sockets (similar to -b under Windows). You must be root to do this.
To display all ports open by a process with id $PID :
In some embedded devices or with old version of Linux, the problem is netstat do not have —process or -p options available.
The following script shows process with its IP and port, you must be root.
#!/bin/bash for protocol in tcp udp ; do #echo "protocol $protocol" ; for ipportinode in `cat /proc/net/$ | awk '/.*:.*:.*/'` ; do #echo "#ipportinode=$ipportinode" inode=`echo "$ipportinode" | cut -d"|" -f3` ; if [ "#$inode" = "#" ] ; then continue ; fi lspid=`ls -l /proc/*/fd/* 2>/dev/null | grep "socket:\[$inode\]" 2>/dev/null` ; pid=`echo "lspid=$lspid" | awk 'BEGIN /socket/'` ; if [ "#$pid" = "#" ] ; then continue ; fi exefile=`ls -l /proc/$pid/exe | awk 'BEGIN ">/->/'` #echo "$protocol|$pid|$ipportinode" echo "$protocol|$pid|$ipportinode|$exefile" | awk ' BEGIN function iphex2dec(ipport) < ret=sprintf("%d.%d.%d.%d: %d","0x"substr(ipport,1,2),"0x"substr(ipport,3,2), "0x"substr(ipport,5,2),"0x"substr(ipport,7,2),"0x"substr(ipport,10,4)) ; if( ret == "0.0.0.0:0" ) #compatibility others awk versions < ret= strtonum("0x"substr(ipport,1,2)) ; ret=ret "." strtonum("0x"substr(ipport,3,2)) ; ret=ret "." strtonum("0x"substr(ipport,5,2)) ; ret=ret "." strtonum("0x"substr(ipport,7,2)) ; ret=ret ":" strtonum("0x"substr(ipport,10)) ; >return ret ; > < print $1" pid:"$2" local="iphex2dec($3)" remote="iphex2dec($4)" inode:"$5" exe=" $6 ; >' ; #ls -l /proc/$pid/exe ; done ; done tcp pid:1454 local=1.0.0.127:5939 remote=0.0.0.0:0 inode:13955 exe=/opt/teamviewer/tv_bin/teamviewerd tcp pid:1468 local=1.1.0.127:53 remote=0.0.0.0:0 inode:12757 exe=/usr/sbin/dnsmasq tcp pid:1292 local=0.0.0.0:22 remote=0.0.0.0:0 inode:12599 exe=/usr/sbin/sshd tcp pid:4361 local=1.0.0.127:631 remote=0.0.0.0:0 inode:30576 exe=/usr/sbin/cupsd tcp pid:1375 local=1.0.0.127:5432 remote=0.0.0.0:0 inode:12650 exe=/usr/lib/postgresql/9.3/bin/postgres With ls you can know the process route.
The fuser command says that the process is: 2054
I’ve added IPv6 support and made a few fixes. Additionally on my system the octets of the IP address are reversed. Dependencies are only to posix shell, awk and cut.
My Version can be found on Github
#!/bin/sh # prints all open ports from /proc/net/* # # for pretty output (if available) start with # ./linux-get-programm-to-port.sh | column -t -s $'\t' #set -x ip4hex2dec () < local ip4_1octet="0x$" local ip4_2octet="$" ip4_2octet="0x$" local ip4_3octet="$" ip4_3octet="0x$" local ip4_4octet="$" ip4_4octet="0x$" local ip4_port="0x$" # if not used inverse #printf "%d.%d.%d.%d:%d" "$ip4_1octet" "$ip4_2octet" "$ip4_3octet" "$ip4_4octet" "$ip4_port" printf "%d.%d.%d.%d:%d" "$ip4_4octet" "$ip4_3octet" "$ip4_2octet" "$ip4_1octet" "$ip4_port" > # reoder bytes, byte4 is byte1 byte2 is byte3 . reorderByte() < if [ $-ne 8 ]; then echo "missuse of function reorderByte"; exit; fi local byte1="$" local byte2="$" byte2="$" local byte3="$" byte3="$" local byte4="$" echo "$byte4$byte3:$byte2$byte1" > # on normal intel platform the byte order of the ipv6 address in /proc/net/*6 has to be reordered. ip6hex2dec()< local ip_str="$" local ip6_port="0x$" local ipv6="$(reorderByte $)" local shiftmask="$" ipv6="$ipv6:$(reorderByte $)" shiftmask="$" ipv6="$ipv6:$(reorderByte $)" ipv6="$ipv6:$(reorderByte $)" ipv6=$(echo $ipv6 | awk '< gsub(/(:0|^0)/, ":"); sub(/(:0)+:/, "::");print>') printf "%s:%d" "$ipv6" "$ip6_port" > for protocol in tcp tcp6 udp udp6 raw raw6; do #echo "protocol $protocol" ; for ipportinode in `cat /proc/net/$protocol | awk '/.*:.*:.*/'` ; do #echo "#ipportinode=$ipportinode" inode=$ if [ "#$inode" = "#" ] ; then continue ; fi lspid=`ls -l /proc/*/fd/* 2>/dev/null | grep "socket:\[$inode\]" 2>/dev/null` ; pids=`echo "$lspid" | awk 'BEGIN /socket/ END>'` ; # removes duplicats for this pid #echo "#lspid:$lspid #pids:$pids" for pid in $pids; do if [ "#$pid" = "#" ] ; then continue ; fi exefile=`ls -l /proc/$pid/exe | awk 'BEGIN ">/->/'`; cmdline=`cat /proc/$pid/cmdline` local_adr_hex=$ remote_adr_hex=$ remote_adr_hex=$ if [ "#$" = "#6" ]; then local_adr=$(ip6hex2dec $local_adr_hex) remote_adr=$(ip6hex2dec $remote_adr_hex) else local_adr=$(ip4hex2dec $local_adr_hex) remote_adr=$(ip4hex2dec $remote_adr_hex) fi echo "$protocol pid:$pid \t$local_adr \t$remote_adr \tinode:$inode \t$exefile $cmdline" done done done How to Check Ports in Use in Linux (Listening Ports)
A listening port is a network port on which an application or process waiting for a connection or has established a connection. This helps the kernel to act when receiving packets with this specific port number.
The listening port could be closed, listening, or in established states. Once service is started and listening to a port no other applications or services can use that port.
In this guide, we learn how to check ports in use in Linux (Listening Ports). You can do this using ss, netstat, and lsof.
For these tools to list process-related information use sudo or root account, for non root account the output may vary.
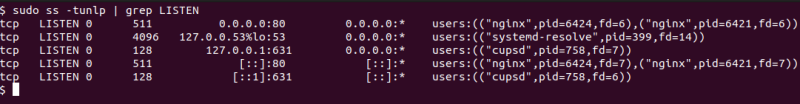
1. Using ss Command
ss is a tool used to investigate sockets in Linux and Unix systems. ss is the new command to replace netstat. It provides similar information to netstat but not all.
To list all listening ports using ss, type:
sudo ss -tunlp | grep LISTENorsudo ss -tulw
- -t : Display only TCP ports.
- -u : Display only UDP ports.
- -n : Display numerical address.
- -l : Display only listening ports.
- -p : Display the process name (PID) that opened the port.
- -w : Display RAW sockets.
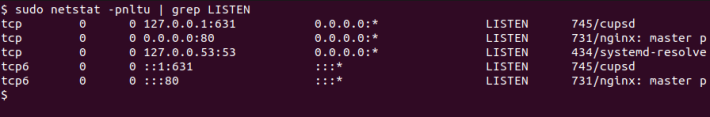
2. Using Netstat Command
Nestat command is a tool used for checking active network connections, interface statistics as well as the routing table. It’s available in all Linux distributions.
To list all listening ports using netstat command, type:
sudo netstat -pnltu | grep LISTEN- -p : Gives the process ID and the process name.
- -n : Displays numerical addresses.
- -l : Displays listening sockets.
- -t : Shows TCP connections.
- -u : Shows UDP connections.
You may use grep to filter the output using a pattern to find a specific service or port.
netstat -pnltu | grep -i "80"netstat -pnltu | grep -i "httpd"
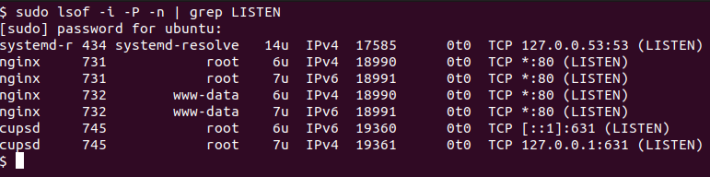
3. Using lsof Command
The lsof command stands for list open files, is used to list all open files and directories. This command helps you find out which files are opened by various processes, the user’s process list, and the list of processes listening on a particular port.
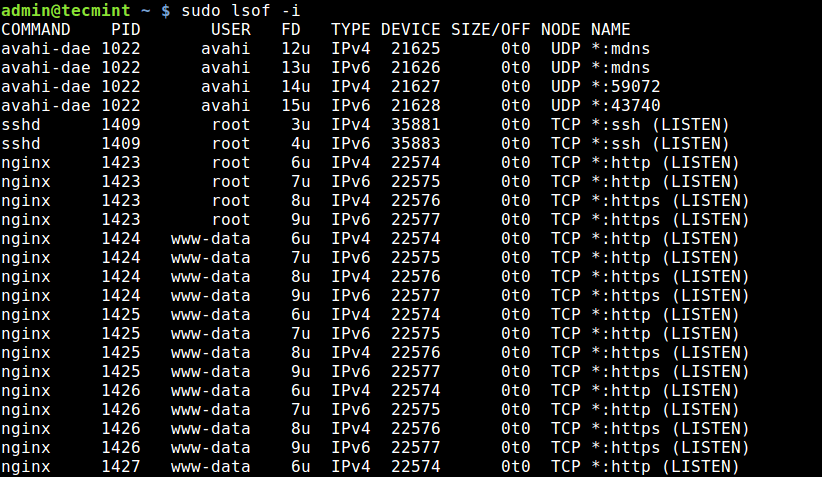
To check all listening ports with lsof, type:
sudo lsof -i -P -n | grep LISTEN- -i : list network files. For specific could add -iTCP -sTCP:LISTEN.
- -P : inhibits the conversion of port numbers to port names for network files.
- -n : inhibits the conversion of network numbers to host names for network files.
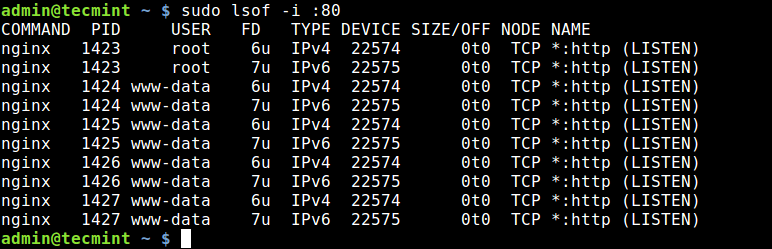
To check a specific port using lsof:
Conclusion
In this guide, we learned how to list listening ports in Linux using ss, nestat, and lsof.
Thanks for reading, please add your feedback and suggestions in the comment section below.
If this resource helped you, let us know your care by a Thanks Tweet. Tweet a thanks
About The Author
James Kiarie
James is a certified LPIC Linux administrator and passionate Linux technical writer. He has over 4 years of penning down technical guides in Linux administration with ample experience in a range of distributions such as Ubuntu, CentOS, RHEL, Fedora, Rocky, and AlmaLinux to mention a few. In addition, he has also spread his wings wider to cloud computing and DevOps tools such as Terraform, Docker, and Kubernetes. During his free time, I love swimming, listening to music, reading books, and taking evening runs after a busy day.
4 Ways to Find Out What Ports Are Listening in Linux
The state of a port is either open, filtered, closed, or unfiltered. A port is said to be open if an application on the target machine is listening for connections/packets on that port.
In this article, we will explain four ways to check open ports and also will show you how to find which application is listening on what port in Linux.
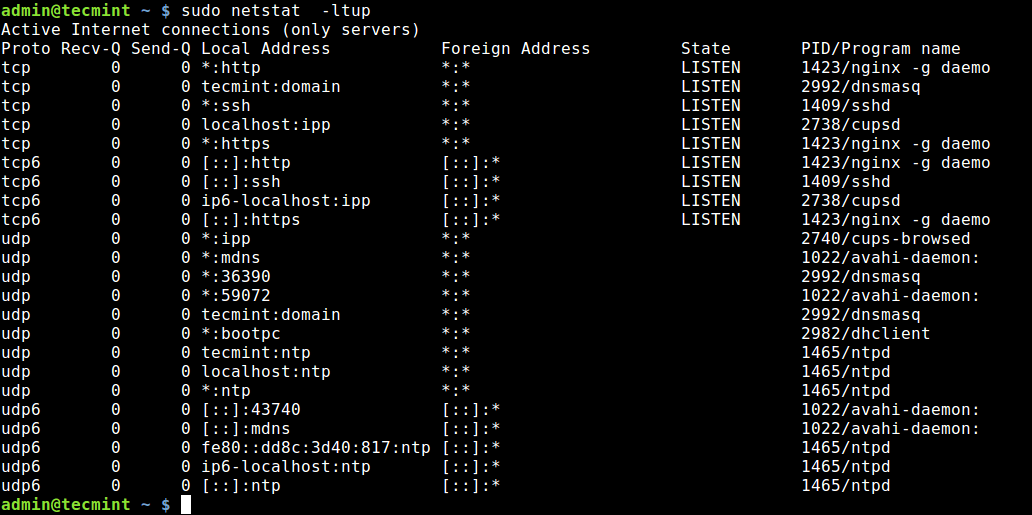
1. Using Netstat Command
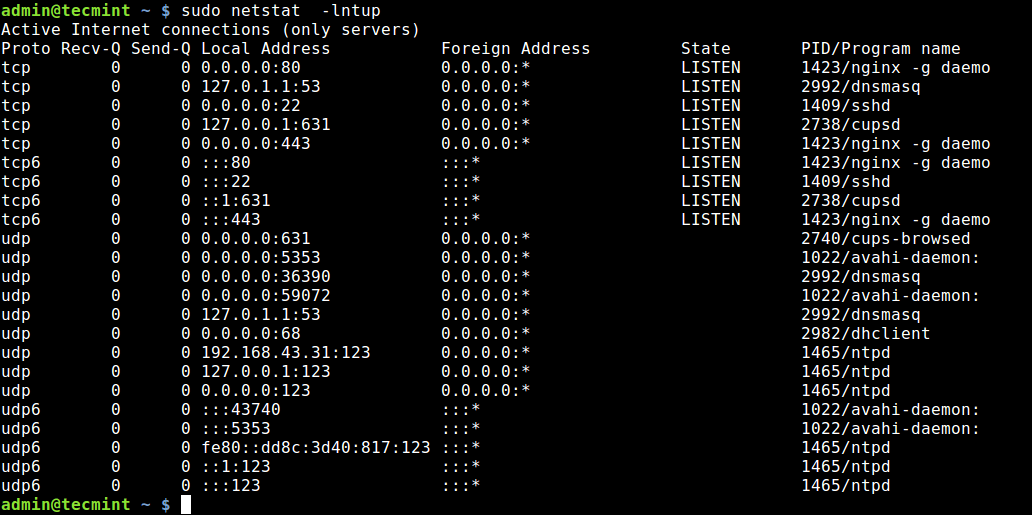
Netstat is a widely used tool for querying information about the Linux networking subsystem. You can use it to print all open ports like this:
The flag -l tells netstat to print all listening sockets, -t shows all TCP connections, -u displays all UDP connections and -p enables printing of application/program name listening on the port.
To print numeric values rather than service names, add the -n flag.
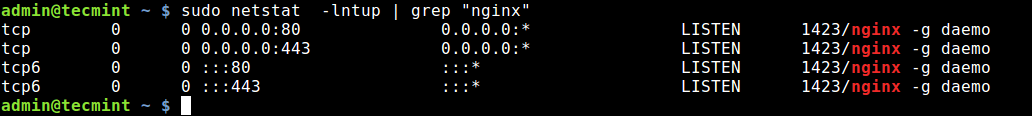
You can also use grep command to find out which application is listening on a particular port, for example.
$ sudo netstat -lntup | grep "nginx"
Alternatively, you can specify the port and find the application bound to, as shown.
$ sudo netstat -lntup | grep ":80"
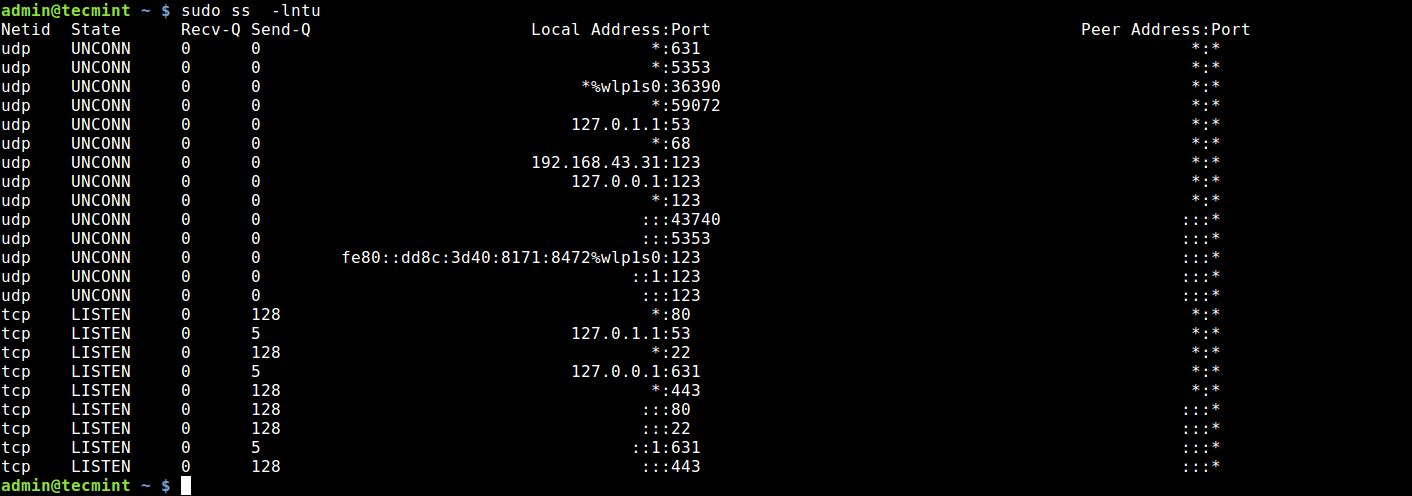
2. Using ss Command
ss command is another useful tool for displaying information about sockets. It’s output looks similar to that of netstat. The following command will show all listening ports for TCP and UDP connections in numeric value.
3. Using Nmap Command
Nmap is a powerful and popular network exploration tool and port scanner. To install nmap on your system, use your default package manager as shown.
$ sudo apt install nmap [On Debian/Ubuntu] $ sudo yum install nmap [On CentOS/RHEL] $ sudo dnf install nmap [On Fedora 22+]
To scan all open/listening ports in your Linux system, run the following command (which should take a long time to complete).
$ sudo nmap -n -PN -sT -sU -p- localhost
4. Using lsof Command
The final tool we will cover for querying open ports is lsof command, which is used to list open files in Linux. Since everything is a file in Unix/Linux, an open file may be a stream or a network file.
To list all Internet and network files, use the -i option. Note that this command shows a mix of service names and numeric ports.
To find which application is listening on a particular port, run lsof in this form.
That’s all! In this article, we have explained four ways to check open ports in Linux. We also showed how to check which processes are bound upon particular ports. You can share your thoughts or ask any questions via the feedback form below.