- How to Use the id Command in Linux: 5 Useful Examples
- id command in Linux
- Examples of id command
- Real vs Effective user and group ID?
- 1. Print the UID and GID of a certain user
- 2. Print only the UID of a user
- 3. Print only the GID of a user
- 4. Print the IDs of all other groups the user belongs to
- 5. Print names instead of the numeric IDs
- Bonus Tip: Print the real IDs
- Everything Important You Need to Know About UID in Linux
- What is UID in Linux?
- How to find the UID of a user in Linux?
- How to change UID of a user in Linux?
- How does UID associate with different system resources? [for advanced users]
- UID and files
- UID and processes
- Как узнать id пользователя Linux
- Как узнать id пользователя в Linux
- Выводы
How to Use the id Command in Linux: 5 Useful Examples
Every user in Linux has a unique, numeric user ID and a default group with a unique numeric group ID. The id command prints this information.
The id command in Linux is used for displaying the real and effective user ID and group ID of a user.
In this tutorial, I’ll show you how to use id command in Linux with some of the most common and useful examples.
id command in Linux
This is the syntax for the id command:
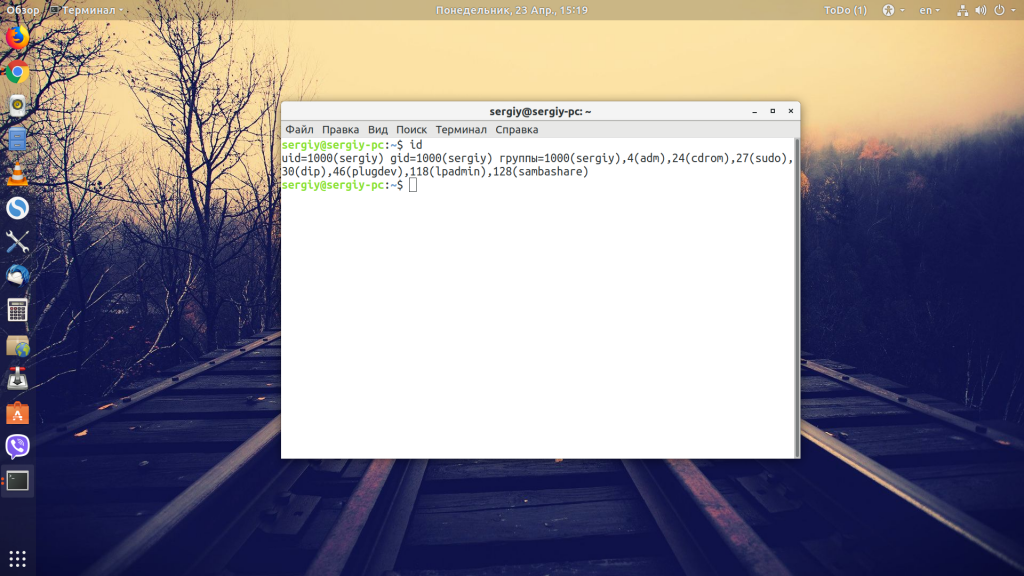
If you don’t provide a username, the command displays the details about the currently logged-in user.
Here’s the output it displayed for me in Ubuntu Linux.
[email protected]:~$ id uid=1000(abhishek) gid=1000(abhishek) groups=1000(abhishek),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),119(lpadmin),130(lxd),131(sambashare)In the above output, user abhishek has uid 1000 and gid 1000. That’s the primary group the user abhishek belongs to by default.
Apart from that, the user abhishek is also member of certain other groups and those groups have also been displayed in the output.
Examples of id command
Here are the most common options for the id command:
| Option | Description |
|---|---|
| -u | Print the effective user id |
| -g | Print the effective group id |
| -G | Print the IDs of all groups user belongs to |
| -n | Print names instead of IDs (must be combined with -u, -g or -G) |
| -r | Print real ID instead of effective IDs (must be combined with -u, -g or -G) |
Real vs Effective user and group ID?
This could be confusing for you. When a user is created, it is given a username, a user ID (uid), a default group and the id of that default group is the gid for that user. This is the ‘real’ user and group ID.
Since in Linux, processes can be run as other user and group, there is also a second set of IDs called effective IDs.
Most of the time the real and effective UIDs and GIDs are the same. But there are situations when a regular user has to modify a privileged file. This is where the effective ID concept is used. Most common example is the using passwd command to change the password which modifies the /etc/passwd file owned by root.
I cannot go in detail here but I recommend reading about it here. You should also read about SUID, GUID and sticky bit permissions in Linux.
1. Print the UID and GID of a certain user
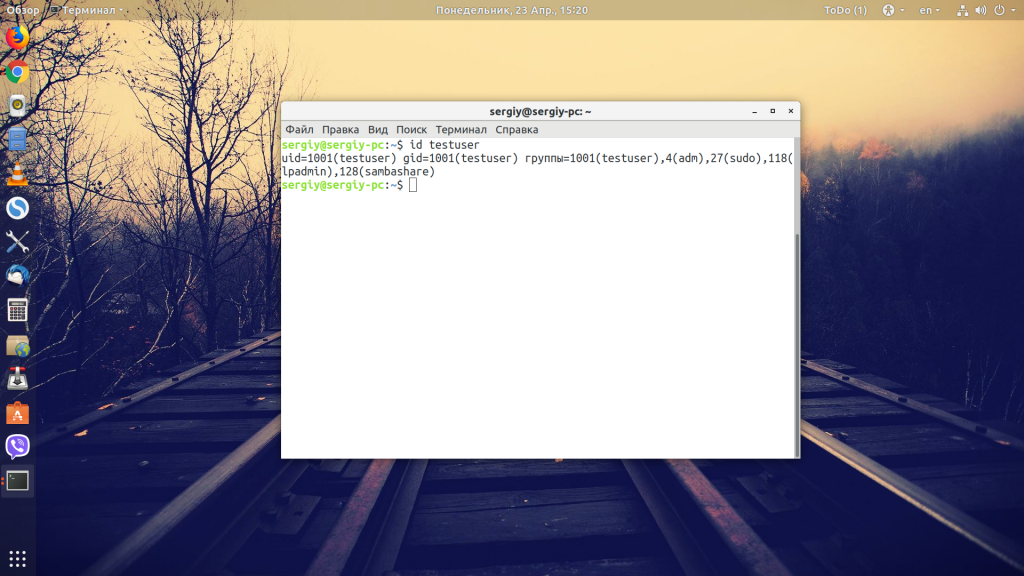
To print the uid and gid and all the other group IDs of a user, you just have to specify the username:
You can list all the users in your Linux system to get the desired user name.
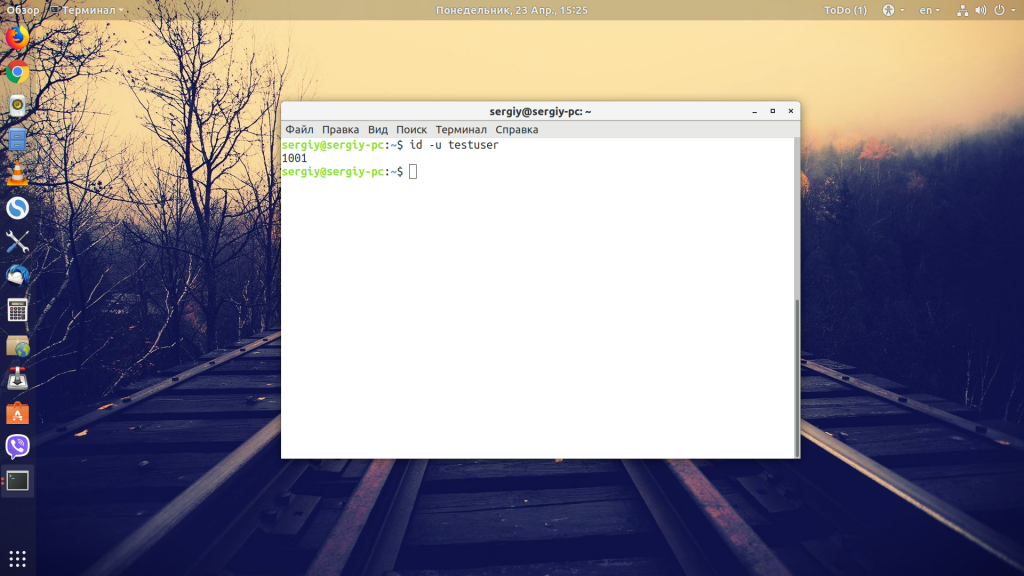
2. Print only the UID of a user
You can use the -u option to print the UID in Linux. As mentioned previously, if you omit the username, it displays the information about the logged-in user.
Keep in mind that it displays only the UID, the numeric value, not the name.
3. Print only the GID of a user
Similarly, you can use the option -g to print the GID of a user. When I say GID, it’s the numeric ID of the default group the user belongs to.
Again, it will only display the numeric ID of the group.
4. Print the IDs of all other groups the user belongs to
A user can belong to several groups. This is basic feature of the Linux filesystem. You can use the usermod command and add it to sudo group to give it root privileges.
You can use the -G option to display the IDs of all the groups the user belongs to.
This too displays the ID only.
[email protected]:~$ id -G abhishek 1000 4 24 27 30 46 119 130 1315. Print names instead of the numeric IDs
The numeric IDs only can be confusing. If you want the names, you can combine the -n option with -u , -g or -G to display the names.
For example, if you want to display all the groups a user belongs to, you can use it like this:
If I use the previous example with option -n here’s what it shows:
[email protected]:~$ id -nG abhishek abhishek adm cdrom sudo dip plugdev lpadmin lxd sambashareBonus Tip: Print the real IDs
All the above examples display the effective IDs. Almost all the time it will be the real ID.
However, if you want to make sure to get the real ID, you can combine option -r with -u , -g or -G .
Alright! I think you know enough about the id command now. If you have questions or suggestions, feel free to leave a comment.
Everything Important You Need to Know About UID in Linux
This Linux Basics guide teaches you everything important associated with UID in Linux.
What is UID in Linux?
UID stands for user identifier. A UID is a number assigned to each Linux user. It is the user’s representation in the Linux kernel. The UID is used for identifying the user within the system and for determining which system resources the user can access. This is why the user ID should be unique.
You can find UID stored in the /etc/passwd file. This is the same file that can be used to list all the users in a Linux system.
Use a Linux command to view text file and you’ll see various information about the users present on your system.
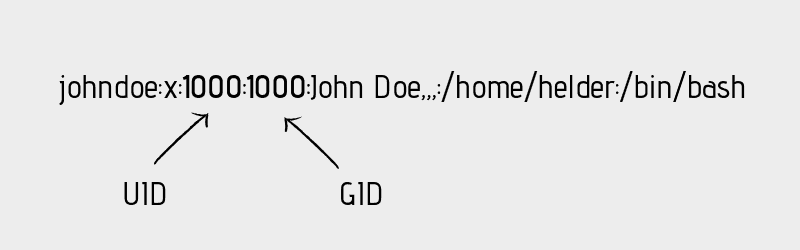
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin johndoe:x:1000:1000:John Doe. /home/helder:/bin/bash davmail:x:127:65534::/var/lib/davmail:/usr/sbin/nologin statd:x:128:65534::/var/lib/nfs:/usr/sbin/nologinThe third field here represents the user ID or UID.
Do note that in most Linux distributions, UID 1-500 are usually reserved for system users. In Ubuntu and Fedora, UID for new users start from 1000.
For example, if you use adduser or useradd command to create a new user, it will get the next available number after 1000 as its UID.
How to find the UID of a user in Linux?
You can always rely on the /etc/passwd file to get the UID of a user. That’s not the only way to get the UID information in Linux.
The id command in Linux will display the UID, GID and groups your current user belongs to:
id uid=1000(abhishek) gid=1000(abhishek) groups=1000(abhishek),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lpadmin),126(sambashare),127(kvm)You can also specify the user names with the id command to get the UID of any Linux user:
id standard uid=1001(standard) gid=1001(standard) groups=1001(standard)How to change UID of a user in Linux?
Suppose you had several users on your Linux system. You had to delete a user because he/she left the organization. Now you want its UID to be taken by another user already on the system.
You can change the UID by modifying the user using usermod command like this:
You need to have superuser privilege to execute the above command.
Do you remember the file permission and ownership concept in Linux? The ownership of a file is determined by the UID of the owner user.
When you update the UID of a user, what happens to the files owned by this user?While all the files in the home directory of user_2 will have their associated UID changed, you’ll have to manually update the associated UID of other files outside the home directory.
What you can do is manually update the ownership of the files associated with the old UID of the user_2.
find / -user old_uid_of_user_2 -exec chown -h user_2 <> \;How does UID associate with different system resources? [for advanced users]
UIDs are unique to one another and thus they can also be used to identify ownership of different system resources such as files and processes.
UID and files
I hope you are familiar with the file permission concept in Linux. When you’re creating a file, you’re the owner of this file. Now you can decide who gets to do what with this file. This is part of Linux’s DAC mechanism where each file is left at its owner’s discretion.
You can read a file’s ownership by using either ls or stat command. Let’s do it with the popular ls command and check the ownership of either the binary sleep or passwd .
As you can see, the file /usr/bin/sleep belongs to root:
ls -l $(which sleep) -rwxr-xr-x 1 root root 39048 Mar 6 2020 /usr/bin/sleepLet’s force it to map the ownership with UID instead of username:
ls -lhn $(which sleep) -rwxr-xr-x 1 0 0 39K Mar 6 2020 /usr/bin/sleepHere’s fun information. Your operating system doesn’t understand «usernames». Whenever a program needs to work with usernames or needs to print such, it refers to the /etc/passwd file to extract the information.
You don’t have to take my words for it. See it yourself with strace program which prints all the system calls made by a program.
strace ls -lhn $(which sleep) 2>&1 | grep passwd What you are trying to see is whether ls command is trying to read the /etc/passwd file or not.
strace ls -lh $(which sleep) 2>&1 | grep passwd openat(AT_FDCWD, "/etc/passwd", O_RDONLY|O_CLOEXEC) = 6UID and processes
Processes have owners too, just like files. Only the owner (or the root user) of a process can send process signals to it. This is where the UID comes into play.
If a normal user tries to kill a process owned by another user, it will result in error:
kill 3708 bash: kill: (3708) - Operation not permittedOnly the owner of the process or the root can do this.
A process must be regulated. Regulated as in you need to have a way to limit or know how much a process is allowed to do. This is determined by its UID(s).
There are three types of UIDs associated with a process.
- Real UID: Real UID is the UID that a process adopts from its parent. In easier terms, whoever starts a process, the UID of that user is the real UID of the process. This is helpful in identifying who a process really belongs to. This is essential especially when the effective UID is not the same as the real UID which I’m going to talk about next.
- Effective UID: This is what mostly determines what permissions a certain process really has. While a user can start the process, it can run with a different user’s available permissions. The command passwd is one example of this. This program edits the file /etc/shadow , which is root owned. Therefore, a normal user shouldn’t be able to run this command or change his/her password. Luckily, the binary runs with an effective UID of 0 (i.e. root), which enables it to have enough privilege to edit the /etc/shadow file. Real and effective UIDs are mostly the same except in the case of SUID bit enabled binaries.
- Saved UID: UID that’s available at a process’s disposal. This one is not normally used, but is still there in case the process knows it’s not going to perform any privileged work, so it can change its effective UID to something that’s unprivileged. This reduces the surface of an unintentional misbehavior.
That’s it. I hope you have a better idea about UID in Linux now. Don’t hesitate to ask your questions, if any.
As a pro Linux user, if you think I missed some important concept about UID, please let me know in the comment section.
Как узнать id пользователя Linux
Иногда возникает необходимость узнать id пользователя Linux. Это может понадобиться, если вы хотите вручную добавить группу для пользователя или вам нужно выполнить другие операции с файлами /etc/passwd или /etc/shadow.
В этой небольшой заметке мы поговорим о том, как посмотреть id пользователя с помощью различных команд в Linux.
Как узнать id пользователя в Linux
Самый простой способ посмотреть идентификатор текущего пользователя — использовать команду id, она выводит не только сам UID, но и идентификатор группы пользователя, а также основные группы этого пользователя:
Первым выводится именно id пользовтеля. Если вам нужно узнать информацию о другом пользователе, вы можете передать его имя в параметры утилиты:
Когда необходимо вывести только id пользователя:
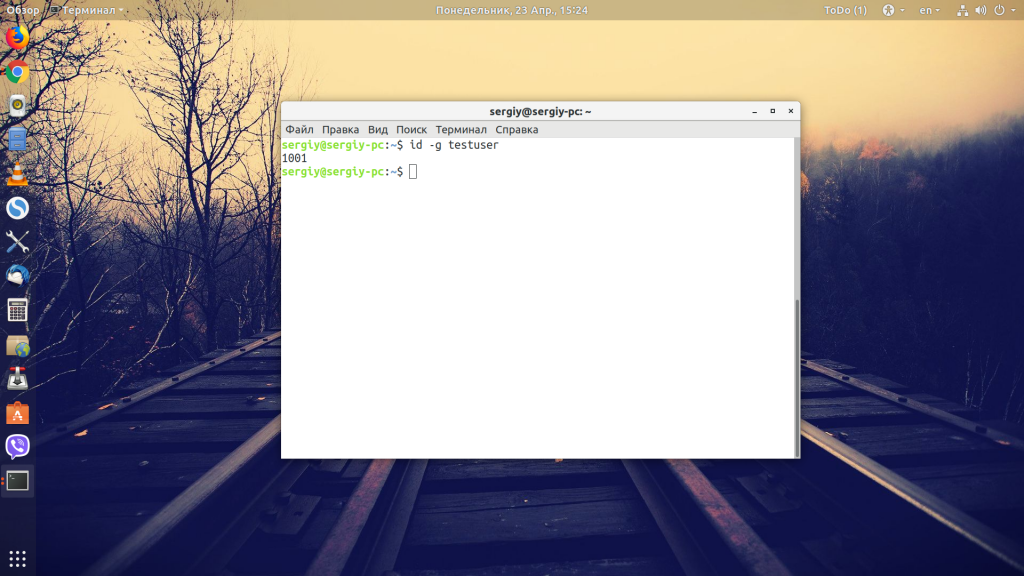
Если вам надо узнать только id группы определенного пользователя, то используйте опцию -g:
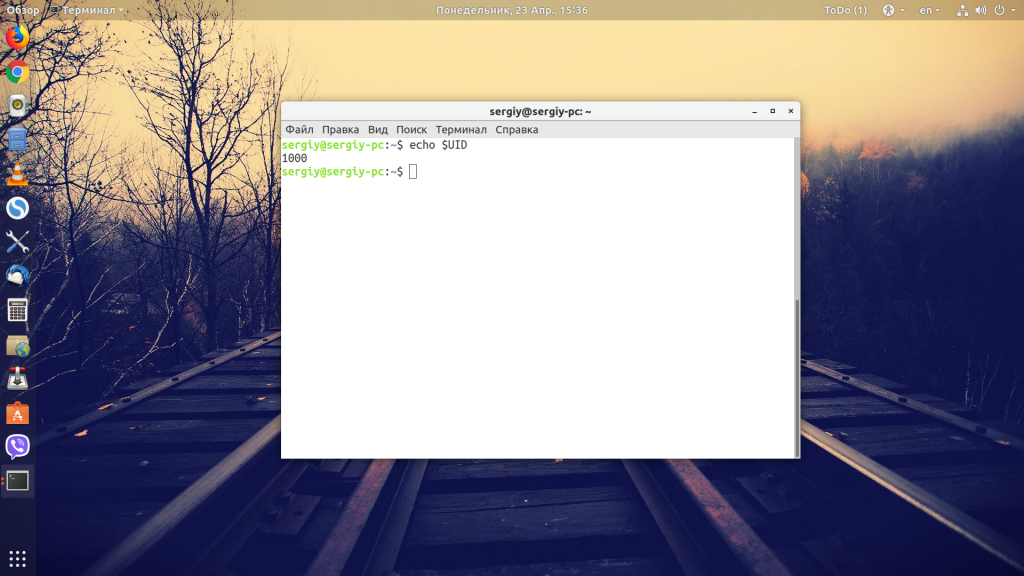
Есть ещё несколько способов посмотреть id. Например, для текущего пользователя его можно найти в переменной окружения UID:
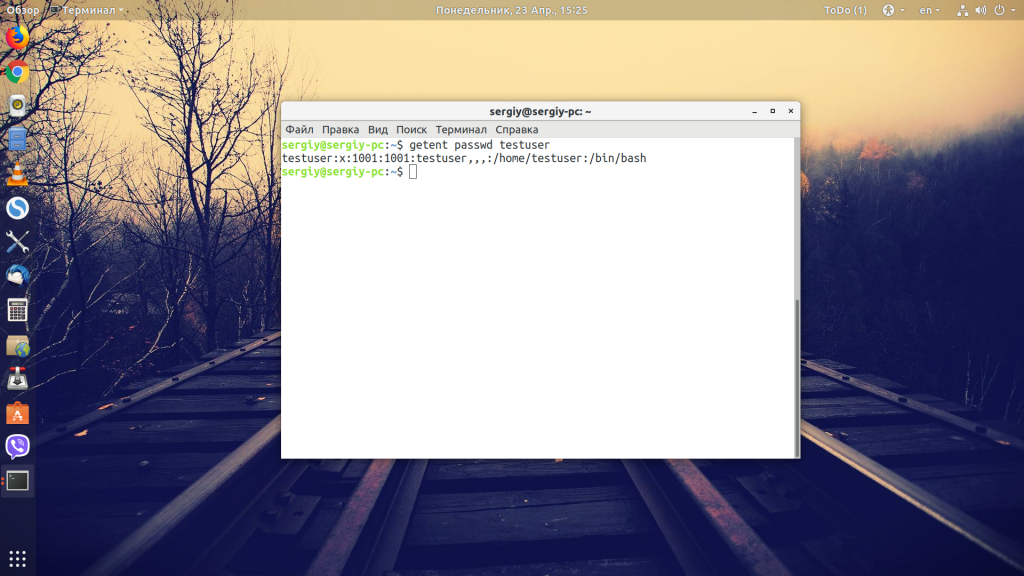
Ещё один вариант — утилита getent:
getent passwd имя_пользователя
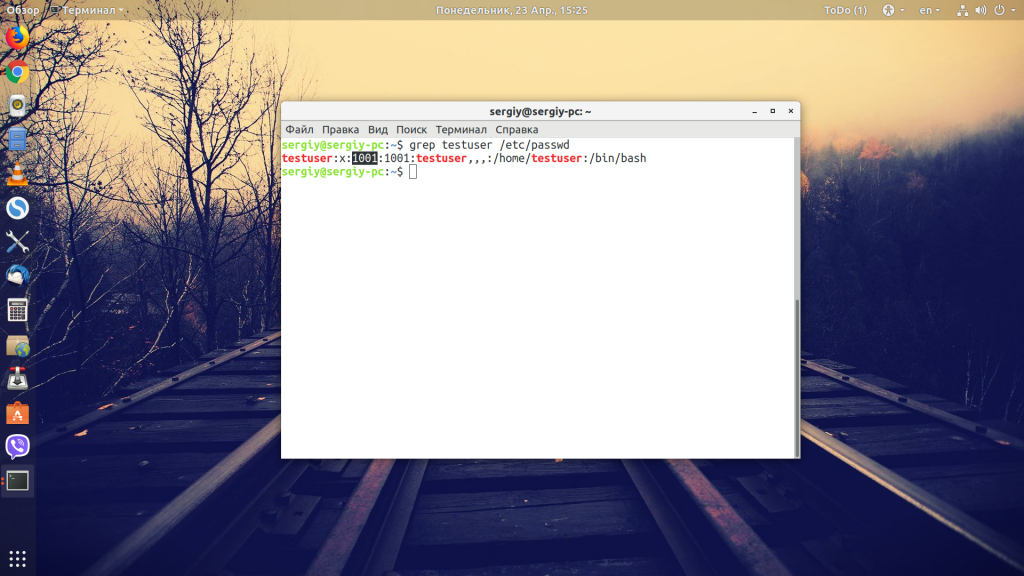
Или смотрим содержимое файла /etc/passwd с помощью команды grep:
grep имя_пользователя /etc/passwd
Здесь первый цифровой параметр — это сам id, а второй, который расположен за двоеточием, — это GID.
Выводы
В этой небольшой статье мы рассмотрели, как узнать id пользователя Linux. Если у вас остались вопросы, спрашивайте в комментариях!

Обнаружили ошибку в тексте? Сообщите мне об этом. Выделите текст с ошибкой и нажмите Ctrl+Enter.