- Grant sudo on linux
- About Administrative Access on Oracle Linux
- Using the sudo Command
- Using the visudo Command
- Adding User Authorizations in the sudoers.d Directory
- Adding User Authorizations in the sudoers File
- Using Groups to Manage User Authorizations
- How To Add User To Sudoers & Add User To Sudo Group on Ubuntu
- Steps to Add Sudo User on Ubuntu
- Step 1: Create New User
- Step 2: Add User to Sudo Group
- Step 3: Verify User Belongs to Sudo Group
- Step 4: Verify Sudo Access
Grant sudo on linux
In Oracle Linux, only administrators can perform privileged tasks on the system.
To grant users additional privileges, an administrator can use the visudo command to either create a new configuration file in the /etc/sudoers.d directory or modify the /etc/sudoers file.
Privileges that an administrator assigns by using configuration files in the /etc/sudoers.d directory are preserved between system upgrades and skipped automatically by the sudo command if they are invalid. Administrators can also change file ownership and permissions for each configuration file. For more information, see Adding User Authorizations in the sudoers.d Directory.
Alternatively, an administrator can assign privileges directly in the /etc/sudoers file by using the visudo command. For more information, see Adding User Authorizations in the sudoers File.
About Administrative Access on Oracle Linux
By default, any user can elevate to a root shell by running the su command and provide the root user password:
Any user can also perform single administrative tasks in the same shell, but those commands cannot be executed until that user provides the root user password:
Elevating to a root shell by using the su command can work well for single user environments and workstations because only one person needs to administer the system and know the root user password. However, that does not scale well for shared systems with multiple users and administrators that require varying levels of access.
Oracle strongly recommends against sharing your root user password with anyone else or allowing remote users to sign in as the root user, both of which constitute poor and highly risky security practice.
The sudo command is better suited for shared systems because any user can supply their own credentials when they elevate to a root shell:
Users can subsequently terminate their root shell in the same way they would have if they had elevated directly with the su command and provided the root user password:
In addition, users can run the sudo command to perform single administrative tasks with elevated permissions:
For more information, see the su(1) , sudo(8) and sudoers(5) manual pages.
You can optionally disable the root user during the Oracle Linux 8 installation process and grant sudo administrator privileges to the first user. For more information, see Oracle Linux 8: Installing Oracle Linux.
Using the sudo Command
If your user has been granted sudo access then you can run administrative commands with elevated privileges:
Depending on your sudoer configuration, you may also be prompted for a password.
In some situations, you may have set environment variables that you want to reuse or preserve while running elevated commands, and you can do so by using the -E option.
For example, you may have connected your Oracle Linux system to an enterprise intranet or virtual private network (VPN) for which you also need proxy settings for outbound Internet access.
The environment variables on which terminal commands rely for proxy access are http_proxy , https_proxy and no_proxy , and you can set them in your ~/.bashrc configuration file:
export http_proxy=http://example.com export https_proxy=https://example.com export no_proxy=localhost,127.0.0.1
Run the source command to refresh your environment variables without signing out:
You can now safely pass those proxy settings to elevated commands. For example, to run the curl command with administrative privileges:
sudo -E curl https://docs.oracle.com
An administrator can optionally set system-wide proxy environment variables by configuring them in a shell script and then saving that file in the /etc/profile.d/ directory.
You can also use sudo access to start an elevated root shell. The -s option elevates your user to a root shell as the root user and the -i option to elevates your user to a root shell while preserving your user profile and shell configuration:
When you have finished running administrative commands, terminate the root shell and return to your usual privilege level by using the exit command.
For more information about configuring network settings, see Oracle Linux 8: Setting Up Networking.
Using the visudo Command
To edit the /etc/sudoers file in the vi text editor without risking any change conflicts from other users on the system, use the visudo command:
To learn more about how to configure the the /etc/sudoers file, see Adding User Authorizations in the sudoers File and the visudo(8) manual page.
Administrators can also use the visudo command to manage permission files for individual users in the /etc/sudoers.d/ directory. For more information, see Adding User Authorizations in the sudoers.d Directory.
Adding User Authorizations in the sudoers.d Directory
To set privileges for a specific user, add a file for them in the /etc/sudoers.d directory. For example, to set sudo permissions for the user alice :
sudo visudo -f /etc/sudoers.d/alice
You can append permissions to /etc/sudoers.d/alice in the following format:
username is the name of the user, hostname is the name of any hosts for which you are defining permissions, and command is the permitted command with full executable path and options. If you do not specify options, then the user can run the command with full options.
For example, to grant the user alice permission to install packages with the sudo dnf command on all hosts:
You can also add several comma separated commands on the same line. To allow the user alice to run both the sudo dnf and sudo yum commands on all hosts:
alice ALL = /usr/bin/dnf, /usr/bin/yum
The alice user still needs to use sudo when they run privileged commands:
Adding User Authorizations in the sudoers File
To set user privileges directly in the /etc/sudoers file, run the visudo command without specifying a file location:
You can append permissions to the /etc/sudoers file in exactly the same format that you would if you were adding those permissions to user files in the /etc/sudoers.d/ directory.
In both cases, you can use aliases to permit broader permission categories instead of specifying each command individually. The ALL alias functions as a wildcard for all permissions, so to set the user bob to have sudo permission for all commands on all hosts:
Additional aliased categories are listed in the /etc/sudoers file and the sudoers(5) manual page. You can create your own aliases in the following format:
Cmnd_Alias ALIAS = command
In addition, you can also add several comma separated aliases on the same line. For example, to grant the user alice permission to manage system services and software packages:
Cmnd_Alias SOFTWARE = /bin/rpm, /usr/bin/up2date, /usr/bin/yum Cmnd_Alias SERVICES = /sbin/service, /sbin/chkconfig, /usr/bin/systemctl start, /usr/bin/systemctl stop, /usr/bin/systemctl reload, /usr/bin/systemctl restart, /usr/bin/systemctl status, /usr/bin/systemctl enable, /usr/bin/systemctl disable alice ALL= SERVICES, SOFTWARE
Both users still need to use sudo when they run privileged commands:
sudo systemctl restart service Using Groups to Manage User Authorizations
Instead of specifying different levels of sudo access for each individual user you can optionally manage sudo access at group level by adding the % symbol to the group name.
For example, to define permissions for an existing group called example in the /etc/sudoers.d/ directory and then add the user alice to that group:
- Create the /etc/sudoers.d/example file by using the visudo command:
sudo visudo /etc/sudoers.d/example
%example ALL= SERVICES, SOFTWARE
sudo usermod -aG example alice
Alternatively, you can set group permissions directly in the /etc/sudoers file. For example, to grant the user bob full sudo access on all hosts, enable the existing group wheel , and then add the user bob to it:
- Open the /etc/sudoers file by using the visudo command:
sudo usermod -aG wheel bob
How To Add User To Sudoers & Add User To Sudo Group on Ubuntu
The sudo command is the preferred means to handle elevated permissions. In supported versions of Ubuntu, using the sudo command will grant elevated permissions for 15 minutes.
Standard user accounts are restricted from performing sensitive tasks, such as viewing the contents of the /root directory. This prevents the accidental use of commands with massive consequences. It also makes it more difficult for intruders to compromise a system. However, sometimes you need to run an administrative command. Sudo – or Super User Do – grants you privileges to run sensitive tasks.
This simple tutorial will show you how to add a new user on Ubuntu and provide sudo access.
- A system running a supported version of Ubuntu
- Access to a root user account or another account with sudo privileges
- Access to a terminal window/command line (Ctrl–Alt–T)
Note: Linux Sudo Command tutorials also available for CentOS and Debian.
Steps to Add Sudo User on Ubuntu
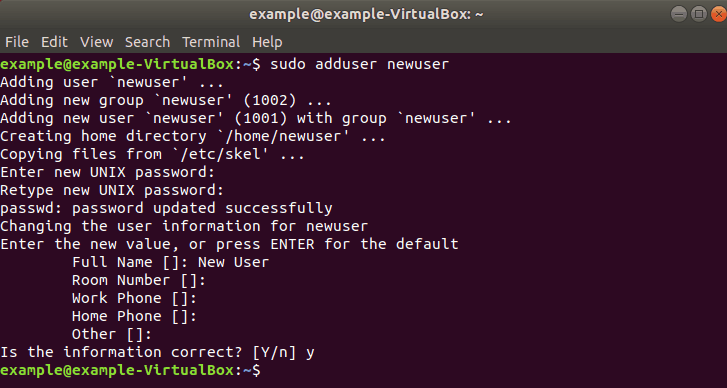
Step 1: Create New User
1. Log into the system with a root user or an account with sudo privileges.
2. Open a terminal window and add a new user with the command:
The adduser command creates a new user, plus a group and home directory for that user.
You may get an error message that you have insufficient privileges. (This typically only happens for non-root users.) Get around it by entering:
3. You can replace newuser with any username you wish. The system will add the new user; then prompt you to enter a password. Enter a great secure password, then retype it to confirm.
4. The system will prompt you to enter additional information about the user. This includes a name, phone numbers, etc. – these fields are optional, and can be skipped by pressing Enter.
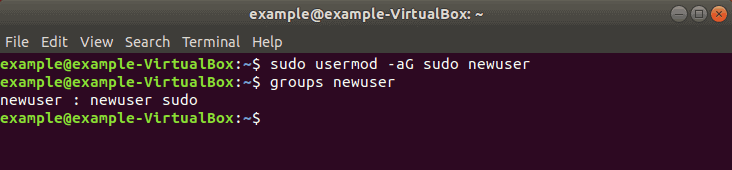
Step 2: Add User to Sudo Group
Most Linux systems, including Ubuntu, have a user group for sudo users. To grant the new user elevated privileges, add them to the sudo group.
In a terminal, enter the command:
Replace newuser with the username that you entered in Step 1.
Again, if you get an error, run the command with sudo as follows:
sudo usermod -aG sudo newuserThe -aG option tells the system to append the user to the specified group. (The -a option is only used with G .)
Note: Usermod command is a useful tool for user management. To learn more about its options, refer to our guide How To Use The Usermod Command In Linux.
Step 3: Verify User Belongs to Sudo Group
Enter the following to view the groups a user belongs to:
The system will respond by listing the username and all groups it belongs to, for example: newuser : newuser sudo
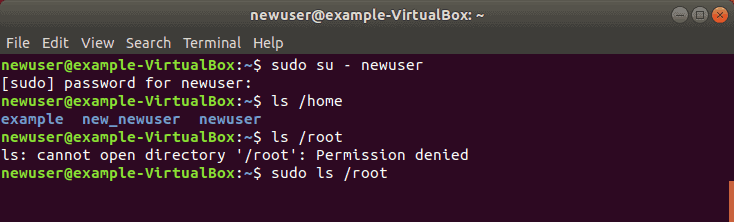
Step 4: Verify Sudo Access
Replace newuser with the username you entered in Step 1. Enter your password when prompted. You can run commands as normal, just by typing them.
However, some commands or locations require elevated privileges. If you try to list the contents of the /root directory, you’ll get an access denied error: ls /root
The command can be executed with:
The system will prompt for your password. Use the same password you set in Step 1. You should now see the contents of the /root directory.
Now you know how to add and create a user with sudo privileges on Ubuntu.
Before sudo, users would log in to their systems with full permissions over the entire system with the su command. This was risky as users could be exploited by tricking them into entering malicious commands. These vulnerabilities were solved by limiting account privileges. However, administrators still had to log out of their account and into an admin account to perform routine tasks.
The sudo command in Ubuntu strikes a balance – protecting user accounts from malicious or inadvertent damage while allowing a privileged user to run administrative tasks. To learn more about the difference between these commands, check out Sudo vs. Su.