- Top 15 Best Hacking Tools For Linux
- Top 15 Best Hacking Tools For Linux
- List Of Best Hacking and Security Software Tools for Linux:
- #1 Aircrack
- #2 John the Ripper
- #3 Metasploit Framework
- #4 Netcat
- #5 Nmap (“Network Mapper”)
- #6 Nessus
- #7 WireShark
- #8 Snort
- #9 Kismet
- #10 Nikto
- #11 Yersinia
- #12 Burp Suite
- #13 THC Hydra
- #14 oclHashcat
- #15 Maltego
- Hacking Linux OS: Hacking with Ubuntu (Commands Tutorial)
- Topics covered in this tutorial
- Quick Note on Linux
- Linux Hacking Tools
- How to prevent Linux hacks
- Hacking Activity: Hack a Ubuntu Linux System using PHP
- Summary
Top 15 Best Hacking Tools For Linux
Linux OS is one that provides you privacy and security from the vulnerabilities that other OS have in it. Today we will be discussing some of the best tools that you can use in your Linux OS to perform various hacks in it. Go through the post to know about it.
[dropcap]L[/dropcap]inux is one of the best OS for pentesting and also best for various hackings attacks. Linux OS is one that provides you privacy and security from the vulnerabilities that other OS have in it. Mostly all the good hackers of the cyber world use Linux operating system because this OS is one of the best for network testing. And now we are here with the discussion on some of the best tools that you can use in your Linux OS to perform various hacks in it. You can also test various network vulnerabilities using these tools. So have a look on the complete guide below to proceed.
Top 15 Best Hacking Tools For Linux
Here are the best softwares that will work on your Linux OS and then you can also create a virtual dummy network to perform various hacks. So have a look on these tools below.
List Of Best Hacking and Security Software Tools for Linux:
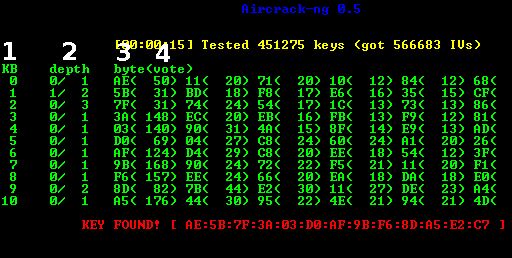
#1 Aircrack
The well-known wifi hacking tool is Aircrack that is being used by lots of hackers to crack the wifi password. This tool is used to find the vulnerability of any network and then finding the way to get into a network. Must try out this app in your Linux OS.
#2 John the Ripper
John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords very easily.
#3 Metasploit Framework
Metasploit took the security world by storm when it was released in 2004 and is being used till now. No other new tool even broke into the top 15 of this list of this tool, yet Metasploit comes in at #5, ahead of many well-loved tools that have been developed for more than a decade.
#4 Netcat
This is one the best tool that is used to read the data on TCP or UDP network connections. The main working of this tool is hijacking the network by getting access to its main server.
#5 Nmap (“Network Mapper”)
The well-known Linux tool that is being used by lots of security testers and mainly by lots of gray and white hackers. This tool is a free and open source (license) utility for network exploration or security auditing.
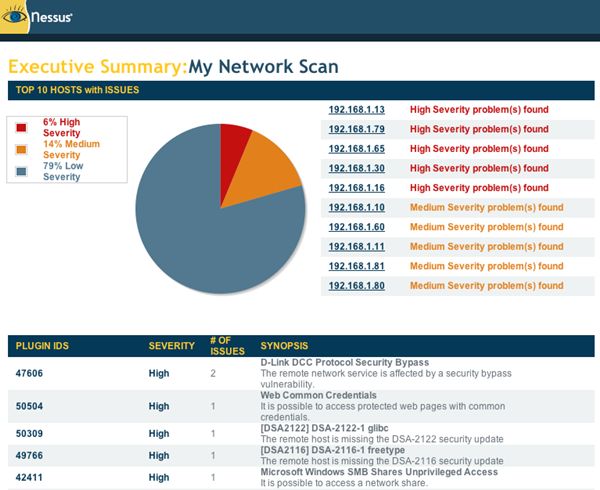
#6 Nessus
Nessus, the market defining vulnerability scanner for auditors and security analysts. Tenable offers different versions of Nessus for different types of users and the networks.
#7 WireShark
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development and lots more that you will get to know after using this tool.
#8 Snort
Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS) created by Martin Roesch in 1998.
#9 Kismet
Kismet is a network detector, packet sniffer, and intrusion detection system for 802.11 wireless LANs. Kismet will work with any wireless card which supports raw monitoring mode.
#10 Nikto
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers.
#11 Yersinia
Yersinia is a network tool designed to take advantage of some weakness in different network protocols. It pretends to be a solid framework for analyzing and testing the deployed networks and systems.
#12 Burp Suite
Burp Suite is an integrated platform for performing security testing of web applications. It is not a point-and-click tool but is designed to be used by hands-on testers to support the testing process. With a little bit of effort, anyone can start using the core features of Burp to test the security of their applications.
#13 THC Hydra
When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more than 50 protocols, including telnet, FTP, HTTP, https, smb, several databases, and much more.
#14 oclHashcat
If you love to do password cracking then Oclhashcat might be what you are looking for. It is the most advanced password cracking tool and it is a CPU-based password cracking tool. The Advance version of oclHashcat uses the power of your GPU. oclHashcat is an open source tool under MIT license that allows an easy integration or packaging of the common Linux distros.
#15 Maltego
Maltego is an interactive data mining tool that renders directed graphs for link analysis. The tool is used in online investigations for finding relationships between pieces of information from various sources located on the Internet.
So above are the 10 Best Hacking Tools For Linux. With these tools, you can easily do lots of security testing and lots of vulnerabilities in this cyber world. So try out these tools in Linux today and share this post with others too. Leave a comment below if you have any related queries with this.
Hacking Linux OS: Hacking with Ubuntu (Commands Tutorial)
Linux is the most widely used server operating system, especially for web servers. It is open source; this means anybody can have access to the source code. This makes it less secure compared to other operating systems as attackers can study the source code to find vulnerabilities. Linux for Hackers is about exploiting these vulnerabilities to gain unauthorized access to a system.
In this article, we will introduce you to what Linux is, its security vulnerabilities, hacking with Ubuntu and the counter measures you can put in place.
Topics covered in this tutorial
Quick Note on Linux
Linux is an open source operating system. There are many distributions of Linux-based operating systems such as Redhat, Fedora, and Ubuntu, etc. Unlike other operating system, Linux is less secure when it comes to security. This is because the source code is available freely, so it is easy to study it for vulnerabilities and exploit them compared to other operating systems that are not open source. Linux can be used as a server, desktop, tablet, or mobile device operating system.
Linux programs can be operated using either GUI or commands. The Linux commands for Kali Linux hacking are more effective and efficient compared to using the GUI. For this reason, it helps to know basic Linux commands for hacking.
Refer to these tutorials https://www.guru99.com/unix-linux-tutorial.html on how to get started with Kali Linux hacks.
Linux Hacking Tools
- Nessus– this tool can be used for Ubuntu hack, scan configuration settings, patches, and networks etc. it can be found at https://www.tenable.com/products/nessus
- NMap. This tool can be used to monitor hosts that are running on the server and the services that they are utilizing. It can also be used to scan for ports. It can be found at https://nmap.org/
- SARA – SARA is the acronym for Security Auditor’s Research Assistant. As the name implies, this tool can be used to audit networks against threats such as SQL Injection, XSS etc. it can be found at http://www-arc.com/sara/sara.html
The above list is not exhaustive; it gives you an idea of the tools available for Ubuntu hacking and hacking Linux systems.
How to prevent Linux hacks
Linux Hacking takes advantage of the vulnerabilities in the operating system. An organization can adopt the following policy to protect itself against such attacks.
- Patch management– patches fix bugs that attackers exploit to compromise a system. A good patch management policy will ensure that you constantly apply relevant patches to your system.
- Proper OS configuration– other exploits take advantage of the weaknesses in the configuration of the server. Inactive user names and daemons should be disabled. Default settings such as common passwords to application, default user names and some port numbers should be changed.
- Intrusion Detection System– such tools can be used to detect unauthorized access to the system. Some tools have the ability to detect and prevent such attacks.
Hacking Activity: Hack a Ubuntu Linux System using PHP
In this practical scenario, we will learn how to hack with Ubuntu and we will provide you with basic information on how you can use PHP to compromise a Linux. We are not going to target any victim. If you want to try it out, you can install LAMPP on your local machine.
PHP comes with two functions that can be used to execute Linux hacking commands. It has exec() and shell_exec() functions. The function exec() returns the last line of the command output while the shell_exec() returns the whole result of the command as a string.
For demonstration purposes, let’s assume the attacker managers to upload the following file on a web server.
$cmd
"; $output = shell_exec($cmd); echo "$output"; ?>
The above script gets the command from the GET variable named cmd. The command is executed using shell_exec() and the results returned in the browser.
The above code can be exploited using the following URL
The command in Ubuntu for hacking against the server will be executed as
Executing the above code on a web server gives results similar to the following.
The above command simply displays the files in the current directory and the permissions
Let’s suppose the attacker passes the following command
- “rm” removes the files
- “rf” makes the rm command run in a recursive mode. Deleting all the folders and files
- “/” instructs the command to start deleting files from the root directory
The attack URL would look something like this
Summary
- Linux is a popular operating system for servers, desktops, tablets and mobile devices.
- Linux is open source, and the source code can be obtained by anyone. This makes it easy to spot the vulnerabilities. It is one of the best OS for hackers.
- Basic and networking hacking commands in Ubuntu are valuable to Linux hackers.
- Vulnerabilities are a weakness that can be exploited to compromise a system.
- A good security can help to protect a system from been compromised by an attacker.
Invicti, the developers of Proof Based Scanning technology, have sponsored the Guru99 project to help raise web application security awareness and allow more developers to learn about writing secure code