How To Install hashcat on Kali Linux
In this tutorial we learn how to install hashcat on Kali Linux.
What is hashcat
Hashcat supports five unique modes of attack for over 300 highly-optimized hashing algorithms. hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, and has facilities to help enable distributed password cracking.
Examples of hashcat supported hashing algorithms are: MD5, HMAC-MD5, SHA1, HMAC-SHA1, MySQL323, MySQL4.1/MySQL5, phpass, MD5(WordPress), MD5(phpBB3), MD5(Joomla), md5crypt, MD5(Unix), FreeBSD MD5, Cisco-IOS, MD4, NTLM, Domain Cached Credentials (DCC), MS Cache, SHA256, HMAC-SHA256, md5apr1, MD5(APR), Apache MD5, SHA512, HMAC-SHA512, Cisco-PIX, Cisco-ASA, WPA/WPA2, Double MD5, bcrypt, Blowfish(OpenBSD), MD5(Sun), Double SHA1, SHA-3(Keccak),Half MD5, Password Safe SHA-256, IKE-PSK MD5, IKE-PSK SHA1, NetNTLMv1-VANILLA/NetNTLMv1-ESS, NetNTLMv2, Cisco-IOS SHA256, Android PIN, AIX , AIX , AIX , AIX , GOST, GOST R 34, Fortigate (FortiOS), OS X v10.8+, GRUB 2, IPMI2, RAKP, HMAC-SHA1, sha256crypt, SHA256(Unix), Drupal7, WBB3, scrypt, Cisco $8$, Cisco $9$, Radmin2, Django (PBKDF2-SHA256), Cram MD5, SAP, iSSHA-1, PrestaShop, PostgreSQL, Challenge-Response Authentication (MD5), MySQL Challenge-Response, Authentication (SHA1), SIP digest authentication (MD5), Plaintext, Joomla < 2.5.18, PostgreSQL, osCommerce, xt:Commerce, Skype, nsldap, Netscape, LDAP, nsldaps, SSHA-1(Base64), Oracle S: Type (Oracle 11+), SMF >v1.1, OS X v10.4, v10.5, v10.6, EPi, Django (SHA-1), MSSQL(2000), MSSQL(2005), PeopleSoft, EPiServer 6.x < v4, hMailServer, SSHA-512(Base64), LDAP , OS X v10.7, MSSQL(2012 & 2014), vBulletin < v3.8.5, PHPS, vBulletin >v3.8.5, IPB2+, MyBB1.2+, Mediawiki B type, WebEdition CMS, Redmine.
Hashcat offers multiple attack modes for obtaining effective and complex coverage over a hash’s keyspace. These modes are:
Hashcat — Crack Passwords in Minutes
Hashcat is an advanced free (License: MIT) multi-threaded password recovery tool and it is world’s fastest password cracker and recovery utility, which supports multiple unique attack modes of attacks for more than 200 highly optimized hashing algorithms. Hashcat currently supports CPUs and GPUs and other hardware accelerators on Linux, Windows, and OSX, and has facilities to help enable distributed password cracking.
Hashcat comes pre-installed on our Kali Linux system, So we don’t need to install it, but if installation is required we can use sudo apt install hashcat command.
Features of Hashcat
- World’s fastest password cracker.
- World’s first and only in-kernel rule engine.
- Free and open source.
- Multi-OS (Linux, Windows and macOS).
- Multi-Platform (CPU, GPU, APU, etc., everything that comes with an OpenCL runtime).
- Multi-Hash (Cracking multiple hashes at the same time).
- Multi-Devices (Utilizing multiple devices in same system).
- Multi-Device-Types (Utilizing mixed device types in same system).
- Supports password candidate brain functionality.
- Supports distributed cracking networks (using overlay).
- Supports interactive pause / resume.
- Supports sessions.
- Supports restore.
- Supports reading password candidates from file and stdin.
- Supports hex-salt and hex-charset.
- Supports automatic performance tuning.
- Supports automatic keyspace ordering markov-chains.
- Built-in benchmarking system.
- Integrated thermal watchdog.
- 350+ Hash-types implemented with performance in mind.
- . and much more.
Hashcat offers multiple unique attack modes for cracking passwords. Those are following:
- Brute-Force attack
- Combinator attack
- Dictionary attack
- Fingerprint attack
- Hybrid attack
- Mask attack
- Permutation attack
- Rule-based attack
- Table-Lookup attack
- Toggle-Case attack
- PRINCE attack
Now without wasting any more time lets dive into Hashcat.
Hashcat on Kali Linux
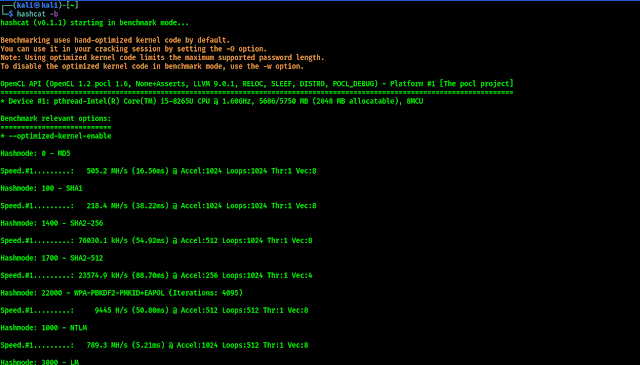
As we told Hashcat comes pre-installed with a Kali Linux and it is multi-threaded so first let we benchmark our system by using following command:
In the following screenshot we can see the benchmark of our system and get an idea how it can perform while cracking various types of hashes.
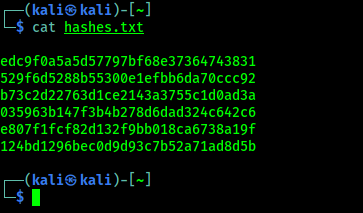
Here we can get an idea about the performance of our system. Let’s run this tool to crack some hashes. Here we have collected some hashed on a text file. For educational purposes we just generated these hashed not collected from any website’s database.
Now we can crack these using Hashcat, and store the output in a craced.txt file by applying following command:
hashcat -m 0 -a 0 -o cracked.txt hashes.txt /usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt
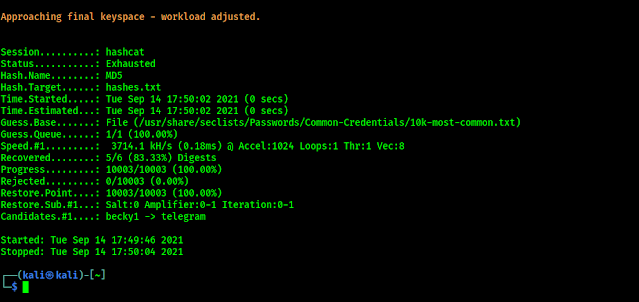
Let’s discuss about the above command, in this command we have used -m flag to specify the hash type, -a for attack mode and -o for output file, here we named our output file ‘cracked.txt’, then we give the target hash file to crack named ‘hashes.txt’, at last we specify the wordlist file to be used. In the following screenshot we can see that hashcat finishes the cracking job.
Let’s see our output file (cracked.txt).
In the above screenshot we can see that hashcat cracked the hashes. Here for the new readers, in this attack mode we can crack those password hashes if the plaintext of the hashes is available in the wordlist file. Using bigger wordlist file will increase the chance to crack hashes.
Hashcat & Type of Hashes & Attacks
In the above we saw that we need to specify our attack modes and type of hashes we want to crack. These attack modes and hashes are refereed by numbers. Here we are giving hashcat supported all numbers that referees to the attack modes and the type of hashes (as Sep 2021, update of Hashcat tool may include some new things).
Attack Types of Hashcat
0 | Straight
1 | Combination
3 | Brute-force
6 | Hybrid Wordlist + Mask
7 | Hybrid Mask + Wordlist
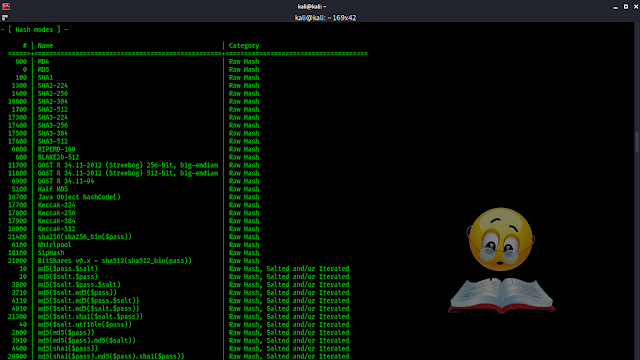
Hash types in Hashcat
Hashcat supports so much types of hashes if we include all them here then this article will very lengthy. We encourage to use hashcat — h command on our Kali Linux system to get all the numbers corresponding to the hash type (Uff.. It’s really large 😫).
Whenever we are trying to crack a hash we have to know the type of the hash. We can use hash-id tool to know the type of hash. Then we need to choose our attack type and wordlist. That’s all it’s not hard.
This is all about Hashcat, and how we can use Hashcat to crack passwords on our Kali Linux. Hashcat (#🐈) is really a very widely used tool for cracking passwords.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group . We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section . As we know our comment section is always open to everyone. We read each and every comment and we always reply .