- How can I check Internet connectivity in a console?
- 6 commands to check and list active SSH connections in Linux
- Check active SSH connections
- 1. Using ss command
- 2. Using last command
- 3. Using who command
- 4. Using w command
- 5. Using netstat command
- 6. Using ps command
- Check ssh connection history
- 12 ss Command Examples to Monitor Network Connections
- 1. Listing all Connections
- 2. Listing Listening and Non-listening Ports
- 3. Listing Listening Sockets
- 4. List all TCP Connections
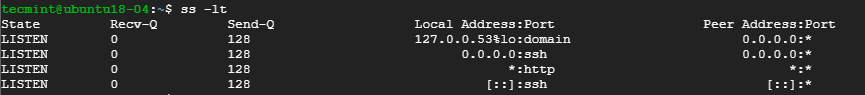
- 5. List all Listening TCP Connections
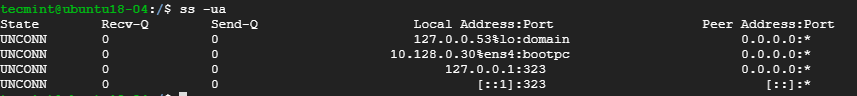
- 6. List all UDP Connections
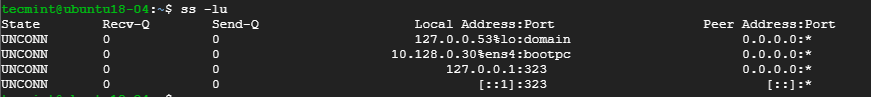
- 7. List all Listening UDP Connections
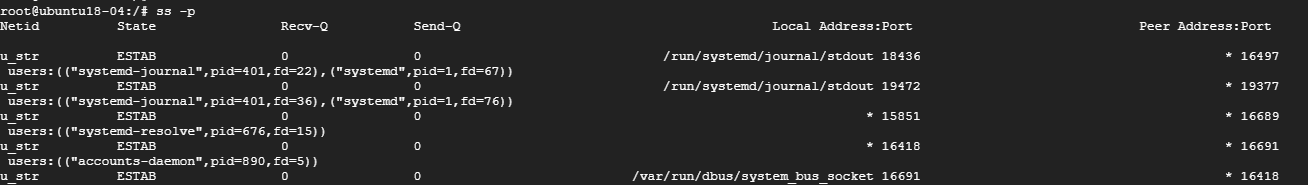
- 8. Display PID (Process IDs) of Sockets
- 9. Display Summary Statistics
- 10. Display IPv4 and IPv6 Socket Connections
- 11. Filter Connections by Port Number
- 12. Check Man Pages for ss Command
How can I check Internet connectivity in a console?
Is there an easy way to check Internet connectivity from console? I am trying to play around in a shell script. One idea I seem is to wget —spider http://www.google.co.in/ and check the HTTP response code to interpret if the Internet connection is working fine. But I think there must be easy way without the need of checking a site that never crash 😉 Edit: Seems like there can be a lot of factors which can be individually examined, good thing. My intention at the moment is to check if my blog is down. I have setup cron to check it every minute. For this, I am checking the HTTP response code of wget —spider to my blog. If its not 200, it notifies me (I believe this will be better than just pinging it, as the site may under be heavy load and may be timing out or respond very late). Now yesterday, there was some problem with my Internet. LAN was connected fine but just I couldn’t access any site. So I keep on getting notifications as the script couldn’t find 200 in the wget response. Now I want to make sure that it displays me notification when I do have internet connectivity. So, checking for DNS and LAN connectivity is a bit overkill for me as I don’t have that much specific need to figure out what problem it is. So what do you suggest how I do it? Here is my script to keep checking downtime for my blog:
#!/bin/bash # Sending the output of the wget in a variable and not what wget fetches RESULT=`wget --spider http://blog.ashfame.com 2>&1` FLAG=0 # Traverse the string considering it as an array of words for x in $RESULT; do if [ "$x" = '200' ]; then FLAG=1 # This means all good fi done if [ $FLAG -eq '0' ]; then # A good point is to check if the internet is working or not # Check if we have internet connectivity by some other site RESULT=`wget --spider http://www.facebook.com 2>&1` for x in $RESULT; do if [ "$x" = '200' ]; then FLAG=1 # This means we do have internet connectivity and the blog is actually down fi done if [ $FLAG -eq '1' ]; then DISPLAY=:0 notify-send -t 2000 -i /home/ashfame/Dropbox/Ubuntu/icons/network-idle.png "Downtime Alert!" "http://blog.ashfame.com/ is down." fi fi exit This way I need to check for internet connectivity only where there is an issue with my blog response code. Its a bit heavy (as I am not using ping) but should not give any false positives. Right? Also how can I randomize pinging to a different site everytime, like facebook, google, yahoo etc. Also (I was trying to avoid any I/O) I can write to a log file by which I can check the count of downtime checks and then skip further checks till the site is down or cause longer checks (10mins instead of every min). What do you think?
6 commands to check and list active SSH connections in Linux
How to check active SSH connections in Linux. Show SSH connection history. How to show active ssh sessions in Linux. List all the active SSH connections in Unix. Find out all the currently active ssh connections on any Linux node. Which all tools can be used to list all the active ssh connections in Linux. Show active SSH sessions. Check ssh connection history using log files in Linux.
Some more more articles you may be interested on similar topics:
Check active SSH connections
There are various commands and tools available in Linux which can be used to check active SSH connections or sessions on your Linux node. In this article I will share a list of tools which can be used to get the list of active SSH connections. If you are aware of any more commands to show active ssh sessions then please let me know via comment section.
1. Using ss command
ss is used to dump socket statistics. It allows showing information similar to netstat . It can display more TCP and state information than other tools. We will use grep function to only get the list of active SSH sessions on our local host
[root@node3 ~]# ss | grep -i ssh tcp ESTAB 0 0 10.0.2.32:ssh 10.0.2.31:37802 tcp ESTAB 0 64 10.0.2.32:ssh 10.0.2.2:49966 tcp ESTAB 0 0 10.0.2.32:ssh 10.0.2.30:56088
From the above example we know that there are three hosts which are currently connected to our node3. We have active SSH connections from 10.0.2.31, 10.0.2.30 and 10.0.2.2
2. Using last command
last searches back through the file /var/log/wtmp (or the file designated by the -f flag) and displays a list of all users logged in (and out) since that file was created. Names of users and tty’s can be given, in which case last will show only those entries matching the arguments.
Using this command you can also get the information about the user using which the SSH connection was created between server and client. So below we know the connection from 10.0.2.31 is done using ‘deepak‘ user, while for other two hosts, ‘root‘ user was used for connecting to node3.
[root@node3 ~]# last -a | grep -i still deepak pts/1 Fri May 31 16:58 still logged in 10.0.2.31 root pts/2 Fri May 31 16:50 still logged in 10.0.2.30 root pts/0 Fri May 31 09:17 still logged in 10.0.2.2
Here I am grepping for a string «still» to get all the patterns with » still logged in «. So now we know we have three active SSH connections from 10.0.2.31, 10.0.2.30 and 10.0.2.2
3. Using who command
who is used to show who is logged on on your Linux host. This tool can also give this information
[root@node3 ~]# who root pts/0 2019-05-31 09:17 (10.0.2.2) root pts/1 2019-05-31 16:47 (10.0.2.31) root pts/2 2019-05-31 16:50 (10.0.2.30)
Using this command we also get similar information as from last command. Now you get the user details used for connecting to node3 from source host, also we have terminal information on which the session is still active.
4. Using w command
w displays information about the users currently on the machine, and their processes. This gives more information than who and last command and also serves our purpose to get the list of active SSH connections. Additionally it also gives us the information of the running process on those sessions.
Using w command you will also get the idle time details, i.e. for how long the session is idle. If the SSH session is idle for long period then it is a security breach and it is recommended that such idle SSH session must be killed, you can configure your Linux host to automatically kill such idle SSH session.
[root@node3 ~]# w 17:01:41 up 7:44, 3 users, load average: 0.00, 0.01, 0.05 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT root pts/0 10.0.2.2 09:17 9:41 0.31s 0.00s less -s deepak pts/1 10.0.2.31 16:58 3:06 0.03s 0.03s -bash root pts/2 10.0.2.30 16:50 5.00s 0.07s 0.02s w
5. Using netstat command
Similar to ss we have netstat command to show active ssh sessions. Actually we can also say that ss is the new version of netstat. Here we can see all the ESTABLISHED SSH sessions from remote hosts to our localhost node3. it is also possible that one or some of these active ssh connections are in hung state so you can configure your host to automatically disconnect or kill these hung or unresponsive ssh sessions in Linux.
[root@node3 ~]# netstat -tnpa | grep 'ESTABLISHED.*sshd' tcp 0 0 10.0.2.32:22 10.0.2.31:37806 ESTABLISHED 10295/sshd: deepak tcp 0 0 10.0.2.32:22 10.0.2.2:49966 ESTABLISHED 4329/sshd: root@pts tcp 0 0 10.0.2.32:22 10.0.2.30:56088 ESTABLISHED 10125/sshd: root@pt
6. Using ps command
Now to show active ssh sessions, ps command may not give you accurate results like other commands we discussed in this article but it can give you some more additional information i.e. PID of the SSHD process which are currently active and connected.
# ps auxwww | grep sshd: | grep -v grep root 4329 0.0 0.1 154648 5512 ? Ss 09:17 0:00 sshd: root@pts/0 root 10125 0.0 0.1 154648 5532 ? Ss 16:50 0:00 sshd: root@pts/2 root 10295 0.0 0.1 154648 5480 ? Ss 16:58 0:00 sshd: deepak [priv] deepak 10301 0.0 0.0 156732 2964 ? S 16:58 0:00 sshd: deepak@pts/1
Check ssh connection history
To get the ssh connection history you can always check your SSHD logs for more information on connected or disconnected SSH session. Now the sshd log file may vary from distribution to distribution. On my RHEL 7.4 my sshd logs are stored inside /var/log/sshd
Lastly I hope the steps from the article to check active SSH connections and ssh connection history in Linux was helpful. So, let me know your suggestions and feedback using the comment section.
Didn’t find what you were looking for? Perform a quick search across GoLinuxCloud
If my articles on GoLinuxCloud has helped you, kindly consider buying me a coffee as a token of appreciation.

For any other feedbacks or questions you can either use the comments section or contact me form.
Thank You for your support!!
12 ss Command Examples to Monitor Network Connections
ss command is a tool that is used for displaying network socket related information on a Linux system. The tool displays more detailed information that the netstat command which is used for displaying active socket connections.
In this guide, we delve in and see how the ss command can be used to display varied socket connection information in Linux.
1. Listing all Connections
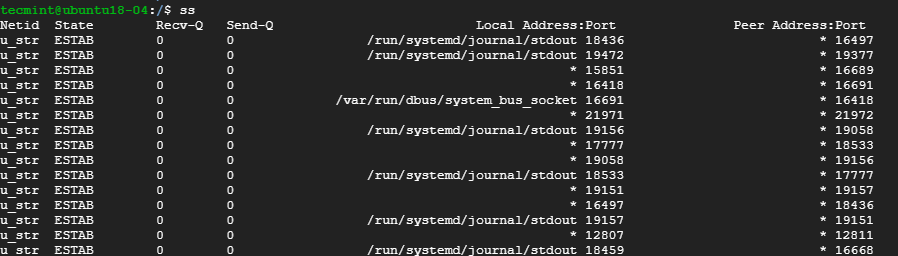
The basic ss command without any options simply lists all the connections regardless of the state they are in.
2. Listing Listening and Non-listening Ports
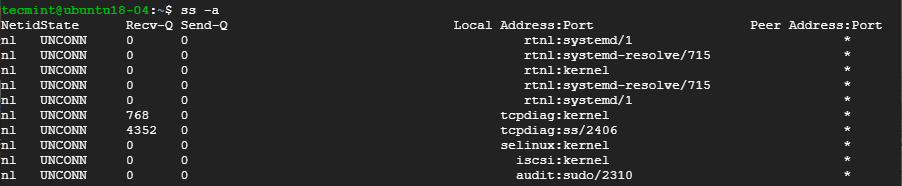
You can retrieve a list of both listening and non-listening ports using the -a option as shown below.
3. Listing Listening Sockets
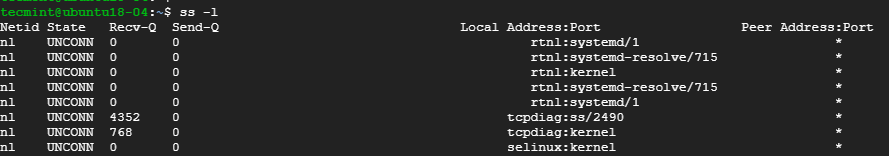
To display listening sockets only, use the -l flag as shown.
4. List all TCP Connections
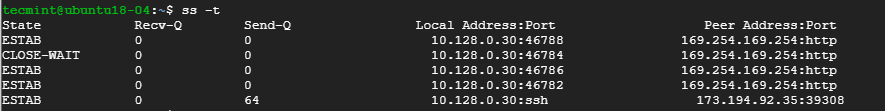
To display all TCP connection, use the -t option as shown.
5. List all Listening TCP Connections
To have a view of all the listening TCP socket connection use the -lt combination as shown.
6. List all UDP Connections
To view all the UDP socket connections use the -ua option as shown.
7. List all Listening UDP Connections
To list listening UDP connections use the -lu option.
8. Display PID (Process IDs) of Sockets
To display the Process IDs related to socket connections, use the -p flag as shown.
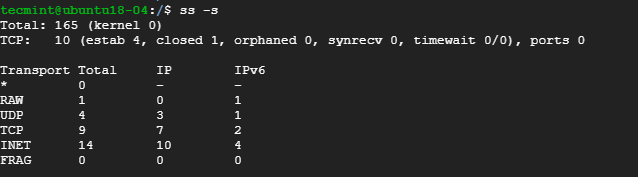
9. Display Summary Statistics
To list the summary statistics, use the -s option.
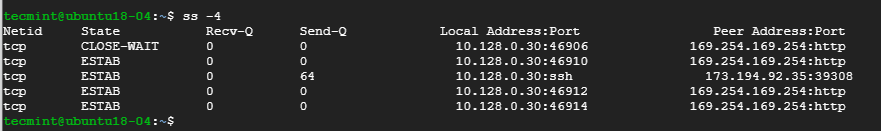
10. Display IPv4 and IPv6 Socket Connections
If you are curious about the IPv4 socket connections use the -4 option.
To display IPv6 connections, use the -6 option.
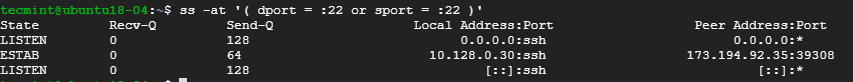
11. Filter Connections by Port Number
ss command also lets you filter socket port number or address number. For example, to display all socket connections with a destination or source port of ssh run the command.
$ ss -at '( dport = :22 or sport = :22 )'
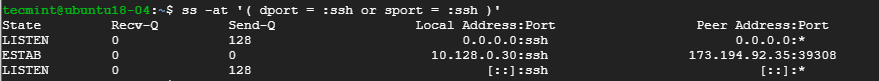
Alternatively, you can run the command.
$ ss -at '( dport = :ssh or sport = :ssh )'
12. Check Man Pages for ss Command
To get more insights into the ss command usage, check the man pages using the command.
Those are some of the commonly used options that are used with ss command. The command is considered more superior to netstat command and provide detailed information about network connections.