- How to Verify SHA256 Checksum of File in Linux
- What is a SHA256 Checksum?
- Verifying SHA256 Checksum of a File in Linux
- DESCRIPTION
- The following five options are useful only when verifying checksums:
- AUTHOR
- REPORTING BUGS
- COPYRIGHT
- SEE ALSO
- How to Verify Checksum on Linux [Beginner Guide]
- How is a Checksum generated?
- Installing GtkHash on Ubuntu
- Using GtkHash
- Verify checksums via Linux command line
- Generating and Verifying SHA256 Checksum with sha256sum
- How accurately does this work?
How to Verify SHA256 Checksum of File in Linux
Internet security is one of the most important aspects when it comes to the world wide web. There has been constant research and development to improve the security of applications and files on the Internet and thus to prevent malicious use.
Downloadable files over the Internet are often the target of attacks on the Internet. As thousands and thousands of people download these files regularly, it becomes especially important to protect such files.
In this article, we will learn about checksums and how they can be used to authenticate a downloaded file from the Internet.
What is a SHA256 Checksum?
A Checksum is a cryptographic signature of a file. It is basically a string that uniquely represents the file; thus if a file is ‘tampered‘ with or ‘modified‘, its checksum value will change and the user will know that the file has been changed.
There are a number of mathematical algorithms for generating Checksum for a file in Linux. One such algorithm which is very popularly used is SHA256, which stands for ‘Secure Hash Algorithm 256‘ and was developed by the United States National Security Agency.
This algorithm breaks down the data of the file into small-sized parts and creates and combines the hash values for each part to create the checksum value. The SHA256 Checksum is usually provided in a text file or directly as a string along with the main file, in its download section on the Internet.
Verifying SHA256 Checksum of a File in Linux
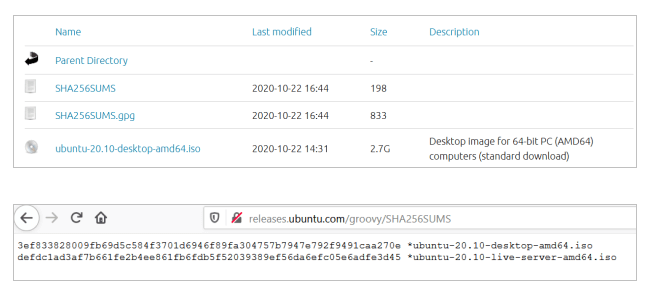
Let’s take an example of Ubuntu Groovy (20.10) ISO file download and try to verify its checksum. Note that along with the ISO files, the text file ‘SHA256SUMS‘ is provided which contains the checksum values.
Download the ISO file for Ubuntu 20.10 desktop and the file SHA256SUMS in the same folder and go to the folder where they are downloaded.
$ wget http://releases.ubuntu.com/groovy/ubuntu-20.10-desktop-amd64.iso $ wget http://releases.ubuntu.com/groovy/SHA256SUMS $ cd ~/Downloads
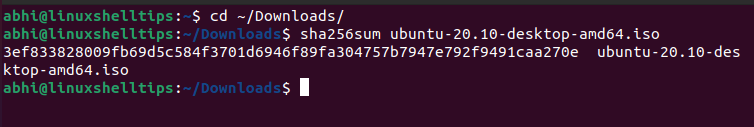
To generate a checksum of the ISO file, run the following:
$ sha256sum ubuntu-20.10-desktop-amd64.iso
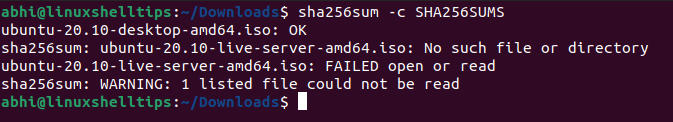
To compare the checksum to the value in the file SHA256SUMS, run the command with the ‘-c’ flag. This will take all the checksums in the file, compare them with the corresponding filename, and print the filename that matches the checksum.
As seen above, the ISO file matches the original checksum, and hence we can be sure that the file was not modified or tampered with in any way during the download.
The other output is regarding the 2nd checksum in the file: for the live server ISO file which is not downloaded and hence the command prints those errors.
Conclusion
Today we learned how to verify the sha256 checksum of a file in Linux. Make sure you check out the manual page of sha256sum (by running ‘man sha256sum‘) to learn more in-depth about the command.
Thanks for reading and let us know your thoughts or questions in the comments below!
DESCRIPTION
With no FILE, or when FILE is -, read standard input.
-b, —binary read in binary mode -c, —check read checksums from the FILEs and check them —tag create a BSD-style checksum -t, —text read in text mode (default) -z, —zero end each output line with NUL, not newline, and disable file name escaping
The following five options are useful only when verifying checksums:
—ignore-missing don’t fail or report status for missing files —quiet don’t print OK for each successfully verified file —status don’t output anything, status code shows success —strict exit non-zero for improperly formatted checksum lines -w, —warn warn about improperly formatted checksum lines —help display this help and exit —version output version information and exit
The sums are computed as described in FIPS-180-2. When checking, the input should be a former output of this program. The default mode is to print a line with: checksum, a space, a character indicating input mode (‘*’ for binary, ‘ ‘ for text or where binary is insignificant), and name for each FILE.
Note: There is no difference between binary mode and text mode on GNU systems.
AUTHOR
Written by Ulrich Drepper, Scott Miller, and David Madore.
REPORTING BUGS
COPYRIGHT
Copyright © 2023 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later https://gnu.org/licenses/gpl.html.
This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law.
SEE ALSO
Full documentation https://www.gnu.org/software/coreutils/sha256sum
or available locally via: info ‘(coreutils) sha2 utilities’
Powered by archmanweb, using mandoc for the conversion of manual pages.
The website is available under the terms of the GPL-3.0 license, except for the contents of the manual pages, which have their own license specified in the corresponding Arch Linux package.
How to Verify Checksum on Linux [Beginner Guide]
A checksum is a small-sized datum from a block of digital data for the purpose of detecting errors which may have been introduced during its transmission or storage.
So a checksum is a long string of data containing various letters and numbers. You’ll generally find them when downloading files from the web, e.g. Linux distribution images, software packages, etc.
The most common use of checksums is for checking if a downloaded file is corrupted.
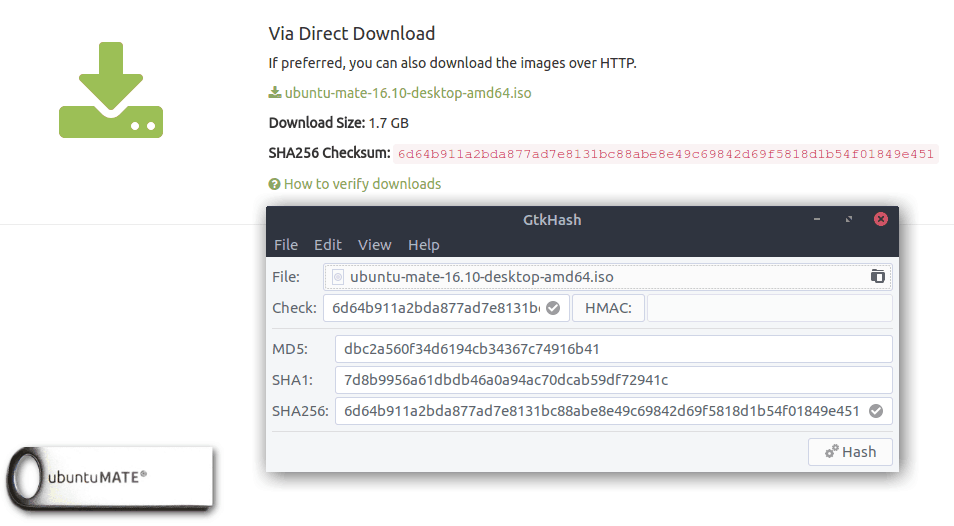
For instance, the Ubuntu MATE download page includes an SHA-256 checksum for every image it makes available. So after you’ve downloaded an image, you can generate an SHA-256 checksum for it and verify that the checksum value matches the one listed on the site.
If it doesn’t, that means your downloaded image’s integrity is compromised (maybe it was corrupted during the download process). We will use an Ubuntu MATE “ubuntu-mate-16.10-desktop-amd64.iso” image file for this guide.
How is a Checksum generated?
Each checksum is generated by a checksum algorithm. Without going into the technical details let’s just say it takes a file as input and outputs the checksum value of that file. There are various algorithms for generating checksums. The most popular checksum algorithms are:
Let’s see how to verify a checksum on Linux.
Installing GtkHash on Ubuntu
To install GtkHash on your Ubuntu system, simply run the following command:
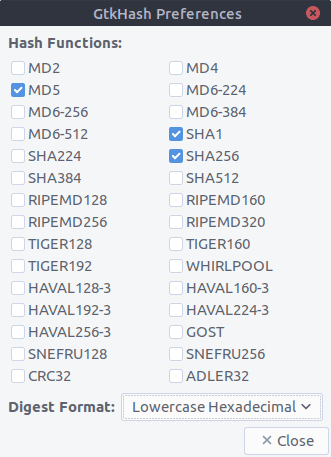
That’s it. Then select the checksum algorithms to use:
- Go to Edit >Preferences in the menu.
- Select the ones you’d like to use.
- Hit the Close button.
By default, MD5, SHA-1 and SHA256 are selected.
Using GtkHash
Using it is quite straight-forward.
- Select the file you want to check.
- Get the Checksum value from the website and put it in the Check box.
- Click the Hash button.
- This will generate the checksum values with the algorithms you selected.
- If any one of them matches with the Check box, it will show a small tick sign beside it.
Here’s an example showing GtkHash generating a checksum for the Ubuntu MATE iso image (ubuntu-mate-16.10-desktop-amd64.iso):
Verify checksums via Linux command line
Every Linux distribution comes with tools for various checksum algorithms. You can generate and verify checksums with them. The command-line checksum tools are the following:
- MD5 checksum tool is called md5sum
- SHA-1 checksum tool is called sha1sum
- SHA-256 checksum tool is called sha256sum
There are some more available, e.g. sha224sum, sha384sum, etc. All of them use similar command formats. Let’s see an example using sha256sum. We’ll use the same “ubuntu-mate-16.10-desktop-amd64.iso” image file that we used before.
Generating and Verifying SHA256 Checksum with sha256sum
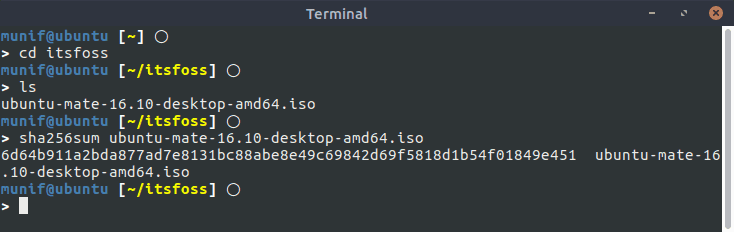
First go to the directory where the .iso image is stored:
Now, to generate the SHA-256 checksum, enter the following command:
sha256sum ubuntu-mate-16.10-desktop-amd64.isoYou’ll see the SHA-256 checksum in your terminal window! Easy, isn’t it?
If the generated checksum matches the one provided on the Ubuntu MATE download page, that will mean no data was changed while you downloaded the file – in other words, your downloaded file is not corrupted.
The other tools mentioned work similarly.
How accurately does this work?
If you’re wondering how accurately these checksums detect corrupted files – if you delete or change even one character from any one of the text files inside the iso image, the checksum algorithm will generate a totally different value for that changed image. And that will definitely not match the checksum provided on the download page.
Do you checksum?
One of the suggested steps while installing Linux is to verify the checksum of your Linux ISO. Do you always follow this step or do you do it only when something goes wrong with the installation?
Was this guide helpful? If you have any questions, let us know! And if you need a similar guide for something else, reach out to us, we’re here to help.