- How to disable all password prompts?
- 1 Answer 1
- Q. How can I disable or lock a password for a User in Linux?
- Surendra Anne
- Latest posts by Surendra Anne (see all)
- How to disable password login on Linux
- Disabling ssh password login:
- Enabling ssh key authentication:
- Sharing or copying the public key to the server:
- Removing the ssh service:
- Conclusion:
- About the author
- David Adams
- Disable password on linux user with command
- 2 Answers 2
- You must log in to answer this question.
- Linked
- Related
- Hot Network Questions
- Subscribe to RSS
How to disable all password prompts?
Anything I want to download or to perform the easiest tasks, I am prompted for my password. All though this is an excellent security feature, it is a real inconvenience. I tried sudo visudo and changed %ALL=(ALL) ALL to NOPASSWD:ALL saved and exit to no avail. Need suggestions.
Could you give some examples of «the easiest tasks»? There is no definite answer, as there are many different layers of authentication and password prompting when working with a system.
You want to run your system as root. You can find out how to do that at these links. How to enable root login? How do I login as root?
1 Answer 1
Run as root? (Just kidding, you shouldn’t do this.)
Others might have a way to do this, but I think you should consider not doing it. The permission scheme set up on Linux systems has been very well thought out, and it goes deep into the system. You can really do a lot of damage to your system very easily, and the point of having you enter a password is to make sure you want change your system in some way.
Another possibility is that some malicious piece of software tries to damage your system. This has been a huge problem on Windows systems for years. On Linux, it’s very difficult to do something like this because all major changes to your system need to be authenticated.
In the end, how often do you need to enter your password? Installing software should only happen once, and then it’s set up. You’ll need it to make changes to the system, but again, you’re probably not going to do this very often and it’s easy to make a typo and break your system.
In the end, it’s up to you, but I urge you to consider how inconvenient entering a password is, and how much you gain from having that extra layer of security.
Q. How can I disable or lock a password for a User in Linux?
Some times it’s required to lock user not to login to the machine. This can be done by using passwd command. this command should be executed by root or super user. Execute below command lock a user.
passwd -l username
passwd -l surendra.
The above command will lock the user surendra prominently so that he can not login to the machine.
Once the password is locked or disabled !(negation sybol) will be added to password field in /etc/shadow file for that user.
Before password lock implemented, the entry for surendra as below.
surendra:$6$rZnP7SSN$emBz/./WkjSa9B:15615:0:99999:7.
After setting password lock:
surendra: ! $6$rZnP7SSN$emBz/./WkjSa9B:15615:0:99999:7.
If you try to login, you will get “Login incorrect“, This error is because ! in the password field of /etc/shadow file for user surendra.
Please follow our next post on unlocking the password.
Surendra Anne
Mr Surendra Anne is from Vijayawada, Andhra Pradesh, India. He is a Linux/Open source supporter who believes in Hard work, A down to earth person, Likes to share knowledge with others, Loves dogs, Likes photography. He works as Devops Engineer with Taggle systems, an IOT automatic water metering company, Sydney . You can contact him at surendra (@) linuxnix dot com.
Latest posts by Surendra Anne (see all)
- Docker: How to copy files to/from docker container — June 30, 2020
- Anisble: ERROR! unexpected parameter type in action: Fix — June 29, 2020
- FREE: JOIN OUR DEVOPS TELEGRAM GROUPS — August 2, 2019
- Review: Whizlabs Practice Tests for AWS Certified Solutions Architect Professional (CSAP) — August 27, 2018
- How to use ohai/chef-shell to get node attributes — July 19, 2018
How to disable password login on Linux
After reading this tutorial, you will know how to disable ssh password login enabling key authentication instead, increasing your system security. If you are looking for a way to disable the root login only, check this tutorial instead.
Disabling ssh password login:
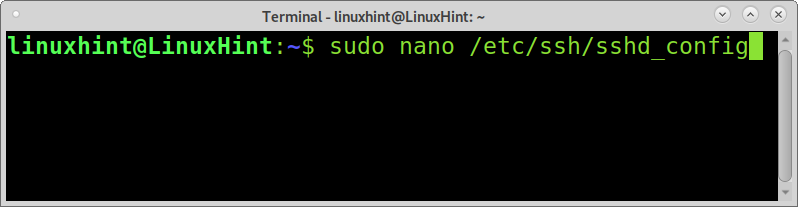
The section of this tutorial about ssh focuses on the configuration file /etc/ssh/sshd_config, which like any other system configuration file, must be edited with root privileges.
Open the file /etc/ssh/sshd_config with root privileges. The command below can be used to open sshd_config using a nano text editor.
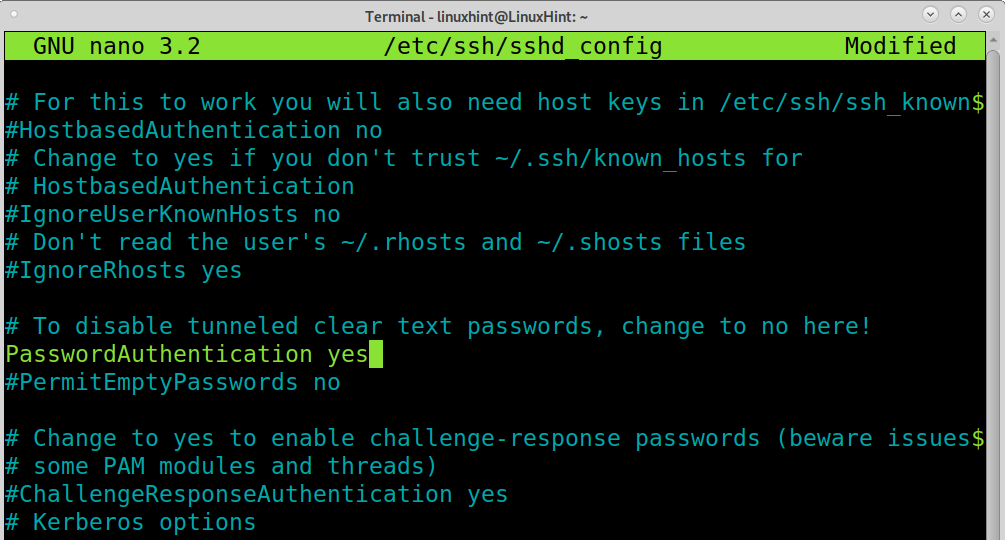
Scroll down the file and find the line containing “PasswordAuthentication yes” shown in the screenshot below. You can use the nano CTRL+W (Where) key combination to search the line containing “PasswordAuthentication”.
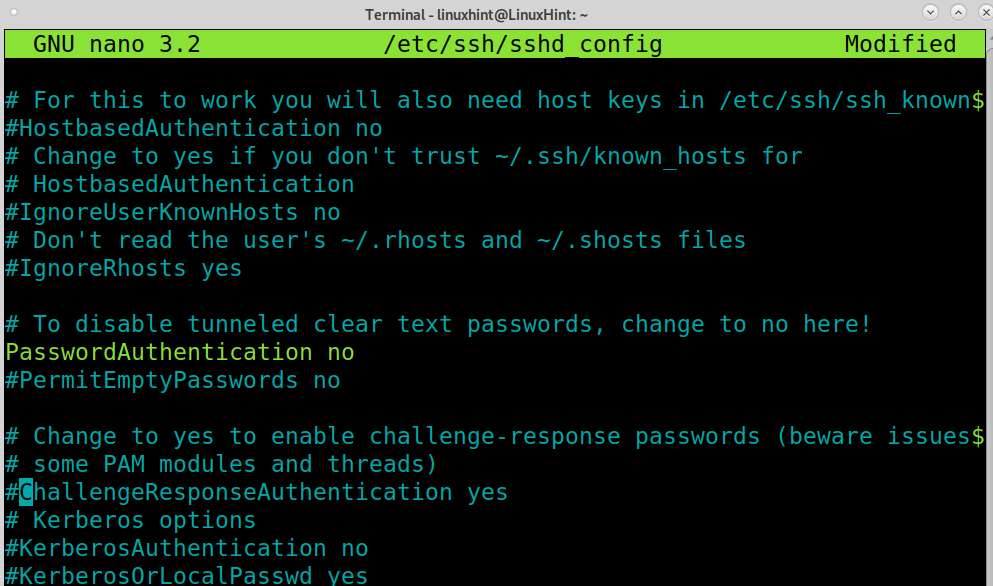
Edit the line leaving it as shown in the screenshot below, replacing yes with no.
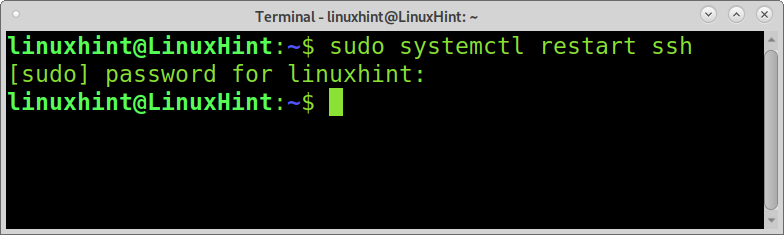
Now your ssh password login is configured to be disabled after you save the file and restart the ssh service. You can exit the file edition saving settings by pressing CTRL+X.
To restart the ssh service and apply changes, run the following command.
Now the password authentication is disabled for incoming ssh connections.
Note: If you only want to disable the password authentication method, you may probably prefer to delete the ssh service; if that’s what you want, there are instructions at the end of this section.
Enabling ssh key authentication:
Key authentication is different from the password authentication method. Depending on the environment, it has advantages and disadvantages over the default password login method.
When using key authentication, we talk about a technique including two different keys: a public key and a private key. In this case, the public key is stored in the server accepting logins; this public key can be decrypted only with the private key, stored in devices allowed to connect through ssh (clients).
Both public and private keys are generated simultaneously by the same device. In this tutorial, both public and private keys are generated by the client, and the public key is shared with the server. Before starting with this tutorial’s section, let’s numerate key authentication benefits over default password login.
Key authentication advantages:
- Strong generated key by default, stronger than most used human-made passwords
- The private key remains in the client; contrary to passwords, it can’t be sniffed
- Only devices storing the private key can connect (this can be considered a disadvantage too)
Password advantages over key authentication:
- You can connect from any device without a private key
- If the device is locally accessed, the password isn’t stored to be cracked
- Easier to distribute when allowing access to multiple accounts
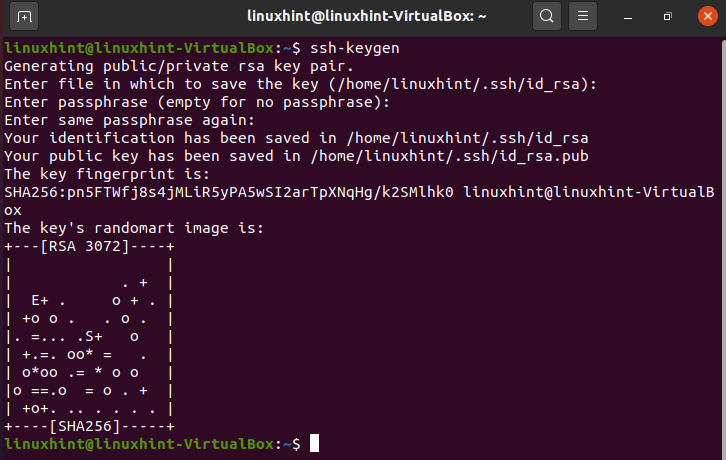
To generate the public and private keys, login as the user you want to provide ssh access and generate the keys by running the command below.
After running ssh-keygen, you will be requested to type a passphrase to encrypt your private key. Most ssh accessible devices do not have a passphrase; you can leave it empty or type a passphrase encrypting your private key if it’s leaked.
As you can see in the screenshot above, the private key is saved in the ~/.ssh/id_rsa file by default, located in the user’s home directory when creating the keys. The public key is stored in the file ~/.ssh/id_rsa.pub located in the same user directory.
Sharing or copying the public key to the server:
Now you have both public and private keys on your client device, and you need to transfer the public key to the server you want to connect to through key authentication.
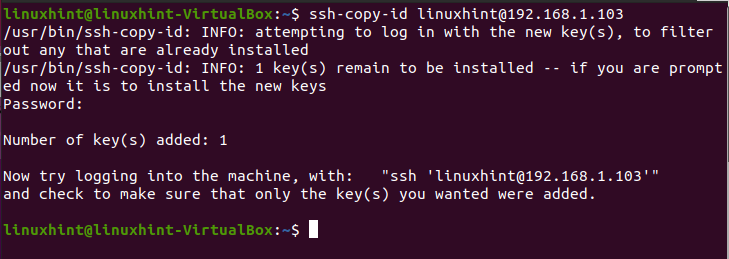
You can copy the file in any way you prefer; this tutorial shows how to use the ssh-copy-id command to achieve it.
Once the keys are generated, run the command below, replacing linuxhint with your username and 192.168.1.103 with your server IP address, this will copy the generated public key to the server’s user ~/.ssh directory. You will be asked for the user password to save the public key, type it, and press ENTER.
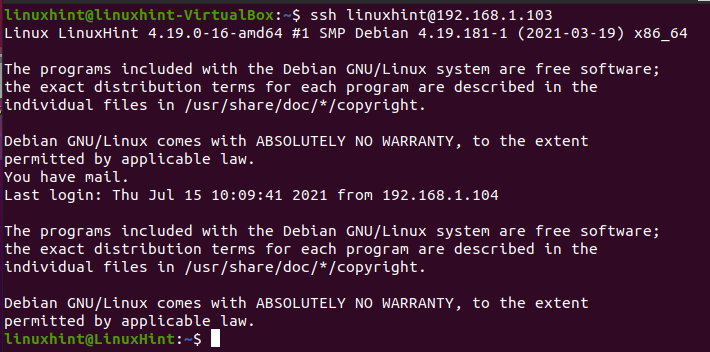
Once the public key was copied, you can connect to your server without a password by running the following command (replace username and password for yours).
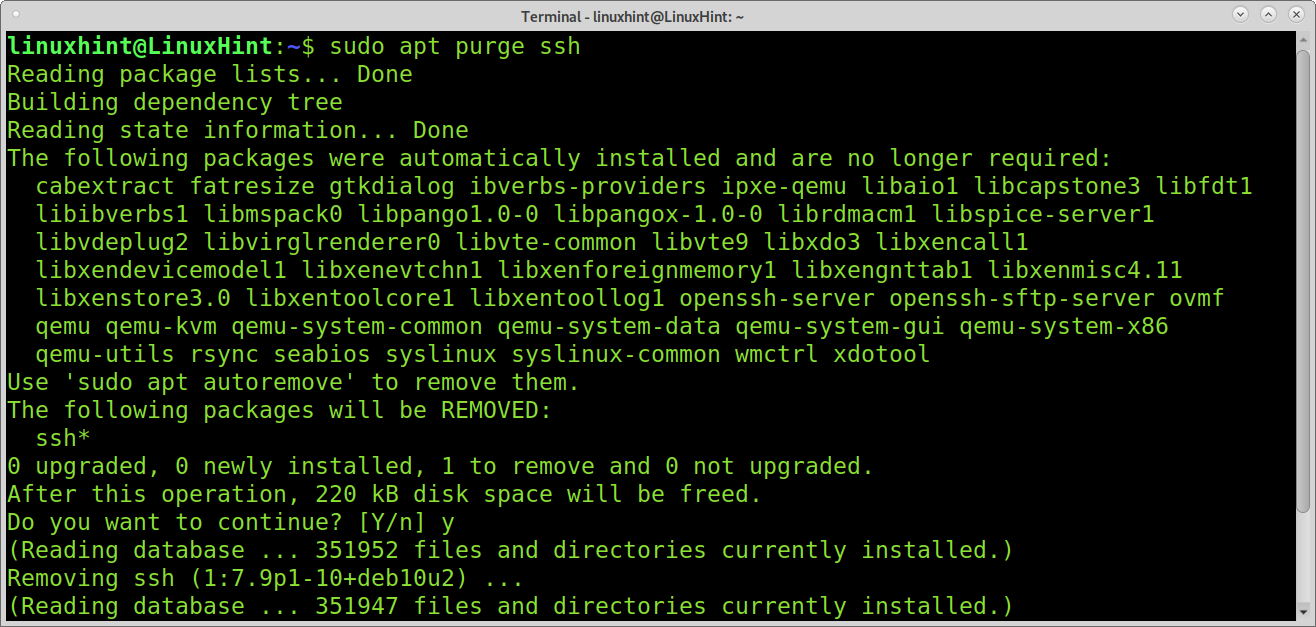
Removing the ssh service:
Probably you want to remove the ssh at all; in such a case removing the service would be an option.
NOTE: After running the commands below on a remote system, you will lose ssh access.
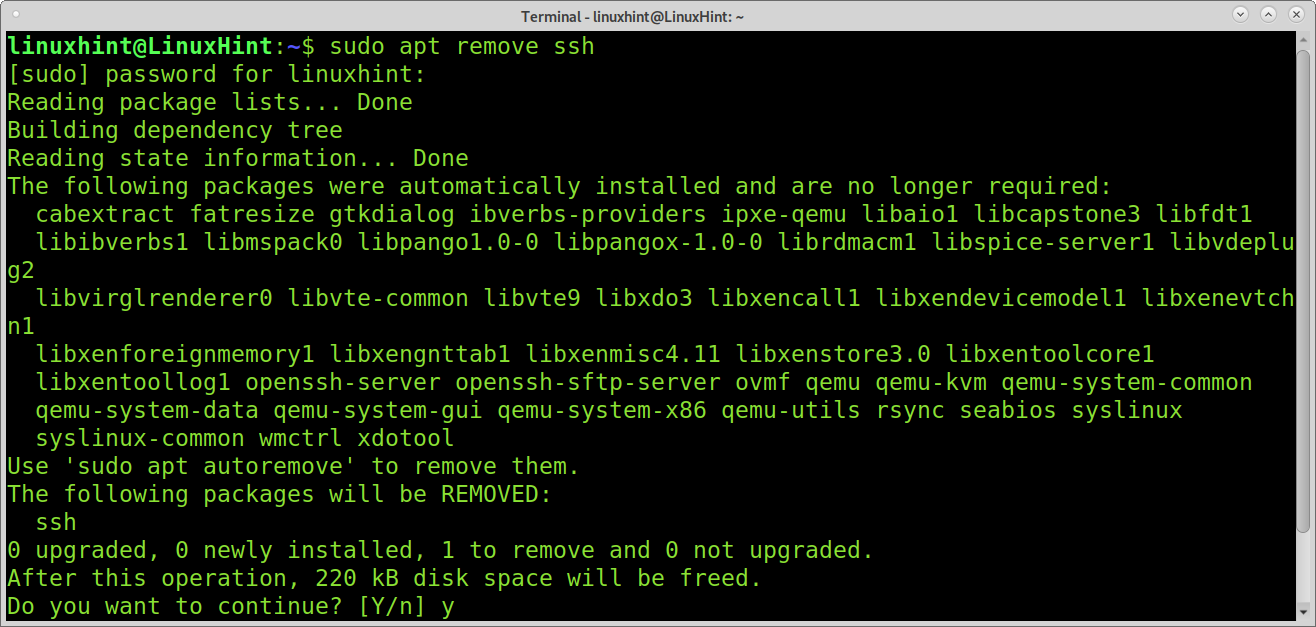
To remove the ssh service, you can run the command below:
If you want to remove the ssh service, including configuration files run:
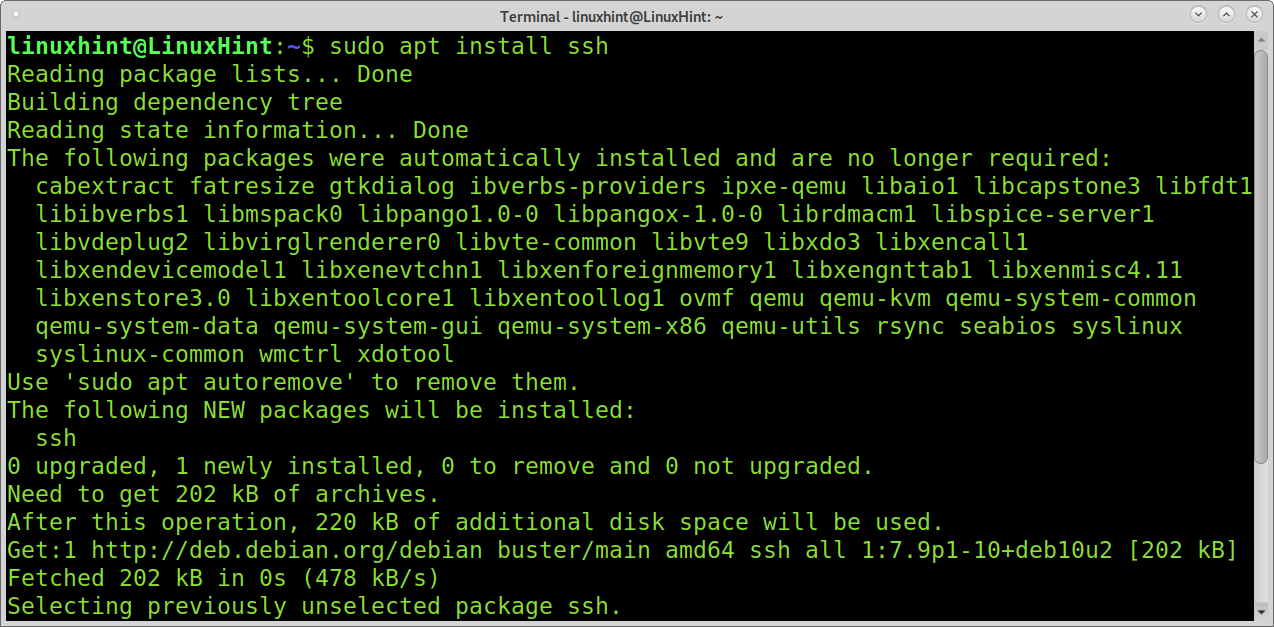
You can reinstall the ssh service by running:
Now your ssh service is back. Other methods to protect your ssh access may include changing the default ssh port, implementing firewall rules to filter the ssh port, and using TCP wrappers to filter clients.
Conclusion:
Depending on your physical environment and other factors like your security policy, the ssh key authentication method may be recommendable over password login. Since the password isn’t sent to the server to authenticate, this method is safer before Man in the Middle or sniffing attacks; it is also a great way to prevent ssh brute force attacks. The main problem of key authentication is the device must store the private key; it may be uncomfortable if you need to log in from new devices. On the other hand, this may be seen as a security advantage.
Additionally, administrators can use TCP wrappers, iptables, or UFW rules to define allowed or unallowed clients and change the default ssh port.
Some system administrators still prefer password authentication because it is faster to create and distribute between multiple users.
Users who never access the system through ssh may opt to remove this and all unused services.
I hope this tutorial showing how to disable password login in Linux was useful. Keep following Linux Hint for more Linux tips and tutorials.
About the author
David Adams
David Adams is a System Admin and writer that is focused on open source technologies, security software, and computer systems.
Disable password on linux user with command
If the password field contains some string that is not a valid result of crypt(3), for instance ! or *, the user will not be able to use a unix password to log in (but the user may log in the system by other means).
My question is whether there is a linux command to disable the user password,i.e. set a «*» or a «!» on password field.
2 Answers 2
You are looking for passwd -l user .
Options:
[. ]
-l, —lock lock the password of the named account. This option disables a password by changing it to a value which matches no possible encrypted value (it adds a ‘!’ at the beginning of the password).
You can simply disable password by just deleting it. You must have sudo privilege! use command:
Here is an coloum from man passwd:
-d, —delete Delete a user’s password (make it empty). This is a quick way to disable a password for an account. It will set the named account passwordless.
You must log in to answer this question.
Linked
Related
Hot Network Questions
Subscribe to RSS
To subscribe to this RSS feed, copy and paste this URL into your RSS reader.
Site design / logo © 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA . rev 2023.7.14.43533
Linux is a registered trademark of Linus Torvalds. UNIX is a registered trademark of The Open Group.
This site is not affiliated with Linus Torvalds or The Open Group in any way.
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.