- How To Install OpenLDAP Server for Centralized Authentication
- Step 1: Installing LDAP Server
- Step 2: Configuring LDAP Server
- Step 3: Configuring LDAP Database
- Install and Configure Linux LDAP
- Step 1: Set Hostname and IP for the Ubuntu Server
- Step 2: Install the OpenLDAP Server to the Ubuntu 22.04 System
- Step 3: Confirm If the Installation Is Successful
- Step 4: Add a Base DN for all the Users and Groups
- Step 5: Configure the LDAP Server by Adding User Accounts and Groups
- Step 6: Configure the LDAP Database
- Conclusion
- About the author
- Kennedy Brian
How To Install OpenLDAP Server for Centralized Authentication
Lightweight Directory Access Protocol (LDAP in short) is an industry standard, lightweight, widely used set of protocols for accessing directory services. A directory service is a shared information infrastructure for accessing, managing, organizing, and updating everyday items and network resources, such as users, groups, devices, emails addresses, telephone numbers, volumes and many other objects.
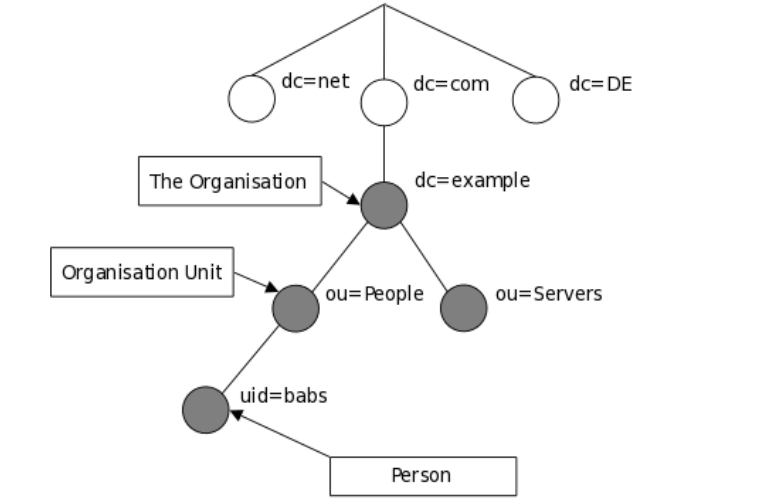
The LDAP information model is based on entries. An entry in a LDAP directory represents a single unit or information and is uniquely identified by what is called a Distinguished Name (DN). Each of the entry’s attributes has a type and one or more values.
An attribute is a piece of information associated with an entry. The types are typically mnemonic strings, such as “cn” for common name, or “mail” for email address. Each attribute is assigned one or more values consisting in a space-separated list.
The following is an illustration of how information is arranged in the LDAP directory.
In this article, we will show how to install and configure OpenLDAP server for centralized authentication in Ubuntu 16.04/18.04 and CentOS 7.
Step 1: Installing LDAP Server
1. First start by installing OpenLDAP, an open source implementation of LDAP and some traditional LDAP management utilities using the following commands.
# yum install openldap openldap-servers #CentOS 7 $ sudo apt install slapd ldap-utils #Ubuntu 16.04/18.04
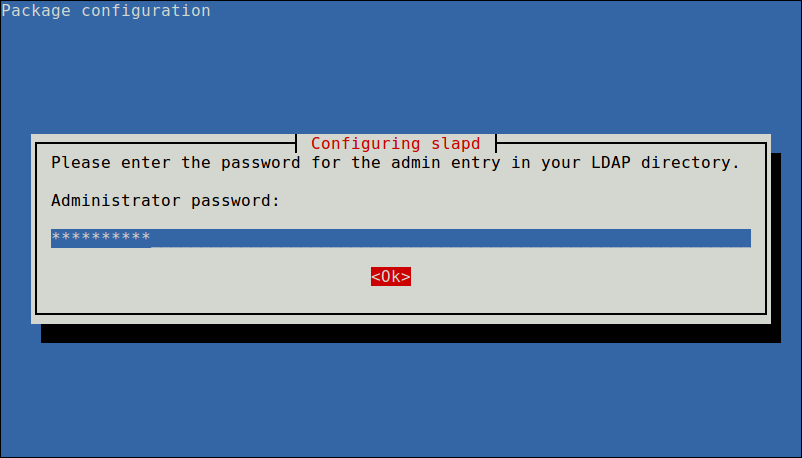
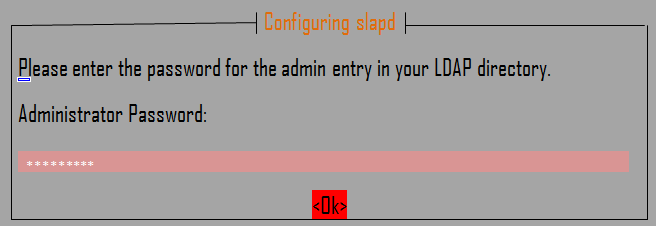
On Ubuntu, during the package installation, you will be prompted to enter the password for the admin entry in your LDAP directory, set a secure password and confirm it.
When the installation is complete, you can start the service as explained next.
2. On CentOS 7, run the following commands to start the openldap server daemon, enable it to auto-start at boot time and check if its up and running (on Ubuntu the service should be auto-started under systemd, you can simply check its status):
$ sudo systemctl start slapd $ sudo systemctl enable slapd $ sudo systemctl status slapd
3. Next, allow requests to the LDAP server daemon through the firewall as shown.
# firewall-cmd --add-service=ldap #CentOS 7 $ sudo ufw allow ldap #Ubuntu 16.04/18.04
Step 2: Configuring LDAP Server
Note: It is not recommended to manually edit the LDAP configuration, you need to add the configurations in a file and use the ldapadd or ldapmodify command to load them to the LDAP directory as shown below.
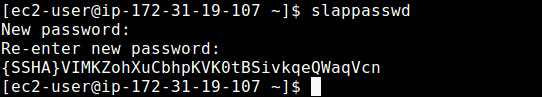
4. Now create a OpenLDAP administrative user and assign a password for that user. In the below command, a hashed value is created for the given password, take note of it, you will use it in the LDAP configuration file.
5. Then create an LDIF file (ldaprootpasswd.ldif) which is used to add an entry to the LDAP directory.
$ sudo vim ldaprootpasswd.ldif
Add the following contents in it:
dn: olcDatabase=config,cn=config changetype: modify add: olcRootPW olcRootPW: PASSWORD_CREATED
explaining the attribute-value pairs above:
- olcDatabase: indicates a specific database instance name and can be typically found inside /etc/openldap/slapd.d/cn=config.
- cn=config: indicates global config options.
- PASSWORD: is the hashed string obtained while creating the administrative user.
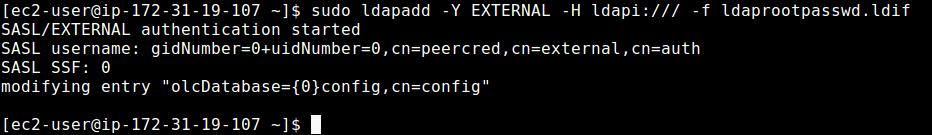
6. Next, add the corresponding LDAP entry by specifying the URI referring to the ldap server and the file above.
$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f ldaprootpasswd.ldif
Step 3: Configuring LDAP Database
7. Now copy the sample database configuration file for slapd into the /var/lib/ldap directory, and set the correct permissions on the file.
$ sudo cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG $ sudo chown -R ldap:ldap /var/lib/ldap/DB_CONFIG $ sudo systemctl restart slapd
8. Next, import some basic LDAP schemas from the /etc/openldap/schema directory as follows.
$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif $ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif $ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
9. Now add your domain in the LDAP database and create a file called ldapdomain.ldif for your domain.
Add the following content in it (replace example with your domain and PASSWORD with the hashed value obtained before):
dn: olcDatabase=monitor,cn=config changetype: modify replace: olcAccess olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.base read by * none dn: olcDatabase=hdb,cn=config changetype: modify replace: olcSuffix olcSuffix: dc=example,dc=com dn: olcDatabase=hdb,cn=config changetype: modify replace: olcRootDN olcRootDN: cn=Manager,dc=example,dc=com dn: olcDatabase=hdb,cn=config changetype: modify add: olcRootPW olcRootPW: PASSWORD dn: olcDatabase=hdb,cn=config changetype: modify add: olcAccess olcAccess: to attrs=userPassword,shadowLastChange by dn write by anonymous auth by self write by * none olcAccess: to dn.base="" by * read olcAccess: to * by dn="cn=Manager,dc=example,dc=com" write by * read
10. Then add the above configuration to the LDAP database with the following command.
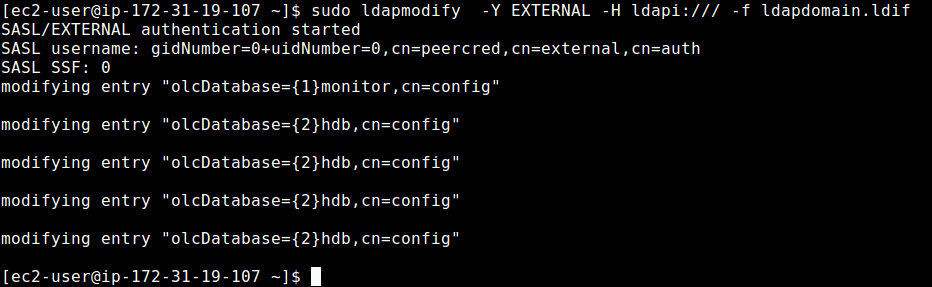
$ sudo ldapmodify -Y EXTERNAL -H ldapi:/// -f ldapdomain.ldif
11. In this step, we need to add some entries to our LDAP directory. Create another file called baseldapdomain.ldif with the following content.
dn: dc=example,dc=com objectClass: top objectClass: dcObject objectclass: organization o: example com dc: example dn: cn=Manager,dc=example,dc=com objectClass: organizationalRole cn: Manager description: Directory Manager dn: ou=People,dc=example,dc=com objectClass: organizationalUnit ou: People dn: ou=Group,dc=example,dc=com objectClass: organizationalUnit ou: Group
Save the file and then add the entries to the LDAP directory.
$ sudo ldapadd -Y EXTERNAL -x -D cn=Manager,dc=example,dc=com -W -f baseldapdomain.ldif
12. The next step is to create a LDAP user for example, tecmint, and set a password for this user as follows.
$ sudo useradd tecmint $ sudo passwd tecmint
13. Then create the definitions for a LDAP group in a file called ldapgroup.ldif with the following content.
dn: cn=Manager,ou=Group,dc=example,dc=com objectClass: top objectClass: posixGroup gidNumber: 1005
In the above configuration, gidNumber is the GID in /etc/group for tecmint and add it to the OpenLDAP directory.
$ sudo ldapadd -Y EXTERNAL -x -W -D "cn=Manager,dc=example,dc=com" -f ldapgroup.ldif
14. Next, create another LDIF file called ldapuser.ldif and add the definitions for user tecmint.
dn: uid=tecmint,ou=People,dc=example,dc=com objectClass: top objectClass: account objectClass: posixAccount objectClass: shadowAccount cn: tecmint uid: tecmint uidNumber: 1005 gidNumber: 1005 homeDirectory: /home/tecmint userPassword: PASSWORD_HERE loginShell: /bin/bash gecos: tecmint shadowLastChange: 0 shadowMax: 0 shadowWarning: 0
then load fthe configuration to the LDAP directory.
$ ldapadd -Y EXTERNAL -x -D cn=Manager,dc=example,dc=com -W -f ldapuser.ldif
Once you have setup a central server for authentication, the final part is to enable the client to authenticate using LDAP as explained in this guide:
For more information, see the appropriate documentation from OpenLDAP Software document catalog and Ubuntu users can refer to the OpenLDAP server guide.
Summary
OpenLDAP is a open source implementation of LDAP in Linux. In this article, we have shown how to install and configure OpenLDAP server for centralized authentication, in Ubuntu 16.04/18.04 and CentOS 7. If you have a question or thoughts to share, do not hesitate to reach us via the comment form below.
Install and Configure Linux LDAP
LDAP, or Lightweight Directory Access Protocol, is an open-vendor protocol for accessing directory information such as X.500 service containers. It is useable in Linux and other OS environments.
This write-up describes how to set up the LDAP directory on a Linux server. It will provide a step-by-step tutorial on installing, configuring, and testing the OpenLDAP server on Linux systems. It is an open-source implementation of LDAP.
This guide will use Ubuntu 22.04|20.04|18.04 LTS as our operating software.
Step 1: Set Hostname and IP for the Ubuntu Server
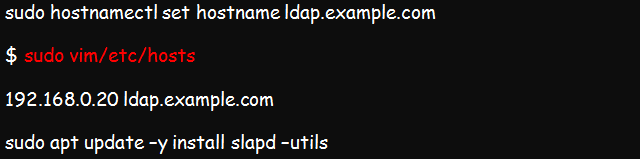
So, set a hostname for your system before beginning the installation process. This command should help:
As the host, you should proceed to add your IP address to the /etc/hosts file as shown below:
At this point, you can replace example.com with your valid hostname. For example, I may choose to use kenhint.com instead.
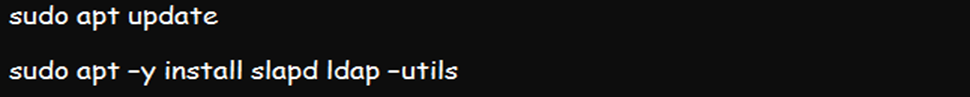
Step 2: Install the OpenLDAP Server to the Ubuntu 22.04 System
The actual installation begins at this point. And you will need to begin by installing LDAP alongside some of its management utilities and packages. This command will help you accomplish the installation on Ubuntu 22.04:
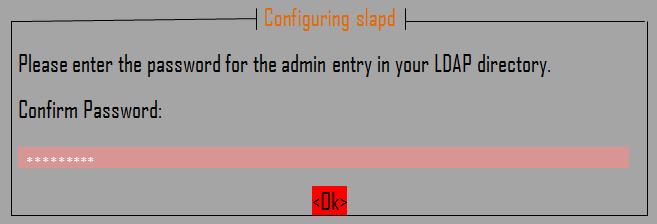
As part of the installation, you will see a prompt to set your LDAP administrator password. Enter your preferred password in the provided space and press to continue. This will be the interface on your screen:
The following interface will prompt you to enter the password. Key in your password again and press OK.
Step 3: Confirm If the Installation Is Successful
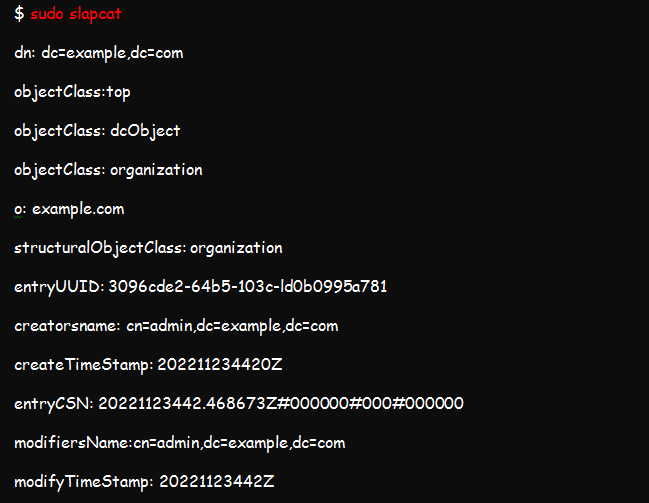
You can use the slapcat command to review the contents and packages in your installation. Expect an outcome similar to the ones in the screenshot below:
The result of the above command should read as shown in this illustration;
Step 4: Add a Base DN for all the Users and Groups
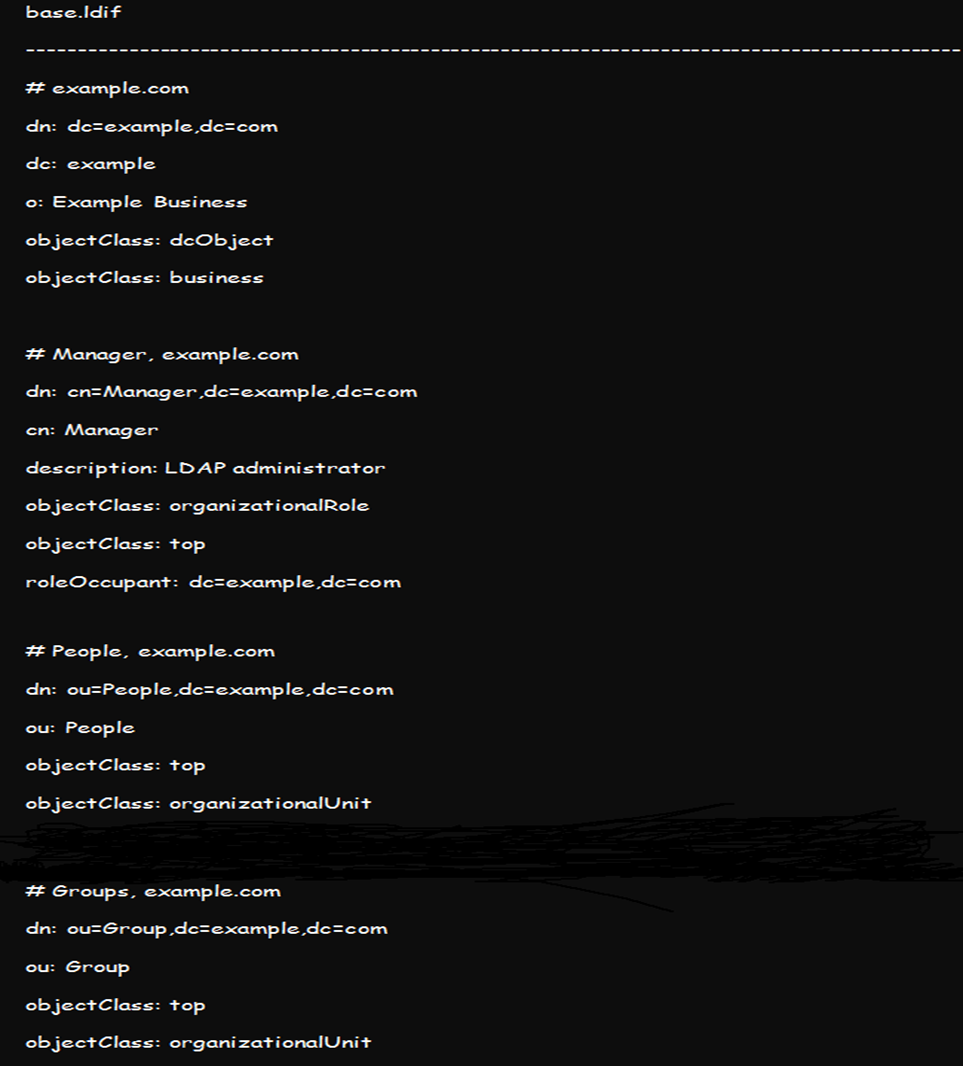
You can add a base DN for each user or group by creating a basedn.ldif file with the following contents:
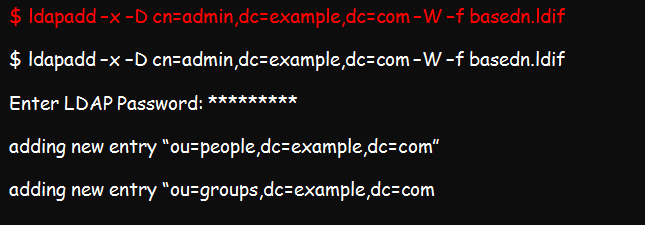
Create a similar base DN for groups using the above format and replace the example and com in the file with your correct domain credentials and add the base file by running this command:
Step 5: Configure the LDAP Server by Adding User Accounts and Groups
Firstly, it is not recommended to edit the LDAP configuration files manually. So, for better results, it is advisable to add your edits into the configuration file and either use ldapmodify or ldapadd commands to load them into the directory.
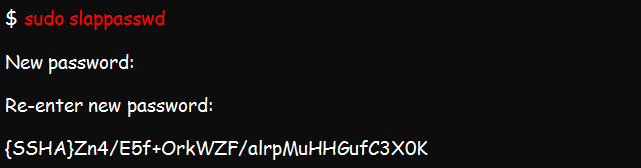
You can create an OpenLDAP user account and assign a password to the account with the slappasswd command.
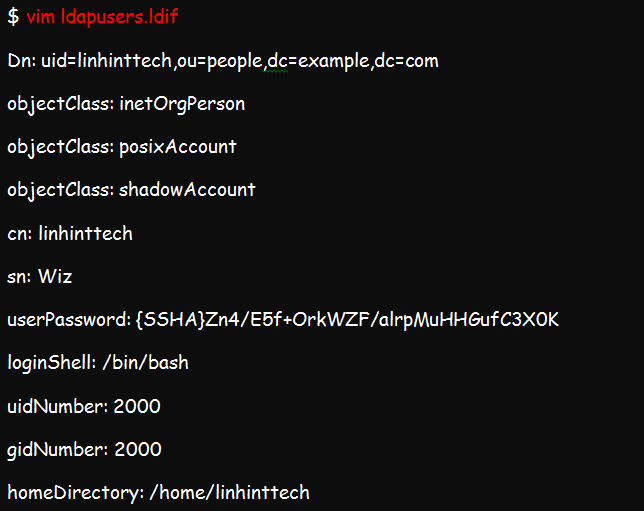
Proceed to create a ldif file which you will use for adding users.
We already talked about how you can replace example and com with the right domain credentials. Now, replace Zn4/E5f+Ork7WZF/alrpMuHHGufC3x0k with your password, cn and sn with the correct username values, and linhinttechs with the username you expect to add.
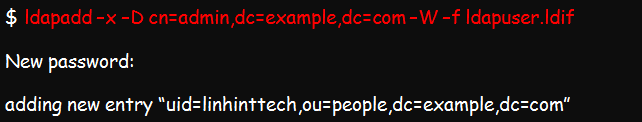
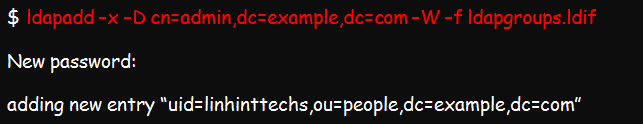
Once you are done editing, you are free to add the account by running this command:
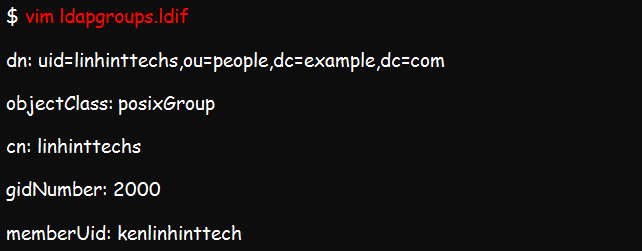
You can do the same to create a group account by first creating the ldif file. This file is what you will use for adding entries into the directory.
Now, add the group by running this command:
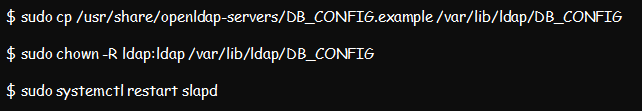
Step 6: Configure the LDAP Database
Configuring the LDAP database starts with copying the sample database of slapd file into the corresponding /var/lib/ldap directory. You can then set the recommended permissions as in the screenshot below:
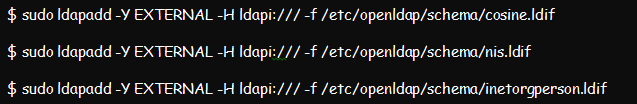
Import common LDAP protocol schemas from /etc/openldap/schema directory into the database. This example should help:
Add your domain to the database and create the ldapdomain.ldif, which will help you modify the credentials in the database. Create the file using the below command:
Add the following required information and replace the relevant sections as earlier advised and add the outcome into the database using the following command:
Conclusion
OpenLDAP is an open-vendor implementation of the LDAP protocol in Linux environments. The article demonstrates how to install and set up the OpenLDAP server and database for centralized authentication in Ubuntu.
About the author
Kennedy Brian
Brian is a computer scientist with a bias for software development, programming, and technical content development. He has been in the profession since 2015. He reads novels, jogs, or plays table tennis whenever not on gadgets. He is an expert in Python, SQL, Java, and data and network security.