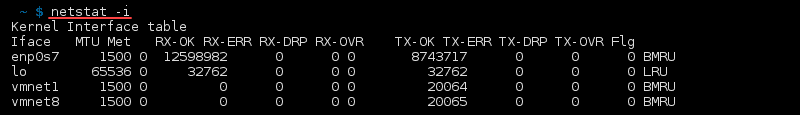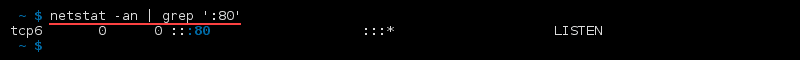- Learning Linux Commands: netstat
- Frequently used options
- Usage
- Examples
- Related Linux Tutorials:
- Netstat Command in Linux — 28 Commands with Examples
- How to Use netstat Command in Linux
- List All Ports and Connections
- List All TCP Ports
- List All UDP Ports
- List Only Listening Ports
- Display Statistics by Protocol
- List Network Interface Transactions
- Display Extended Kernel Interface Table
- Display Masqueraded Connections
- Display PID
- Find Listening Programs
- Display Kernel IP Routing Table
- Display IPv4 and IPv6 Group Membership
- Print netstat Info Continuously
- Find Unconfigured Address Families
- Display Numerical Addresses, Host Addresses, Port Numbers, and User IDs
- Find a Process That Is Using a Particular Port
- List All netstat Commands
Learning Linux Commands: netstat
netstat command is a useful command to reveal a network status of your system. It allows a system administrator to keep track of any network connections by querying their status, origin and destination.
Furthermore, netstat is the all-in-one networking monitoring tool as it can also be used to display route tables, interface statistics, masquerade connections, as well as multicast memberships. ss command is a future successor of the netstat command.
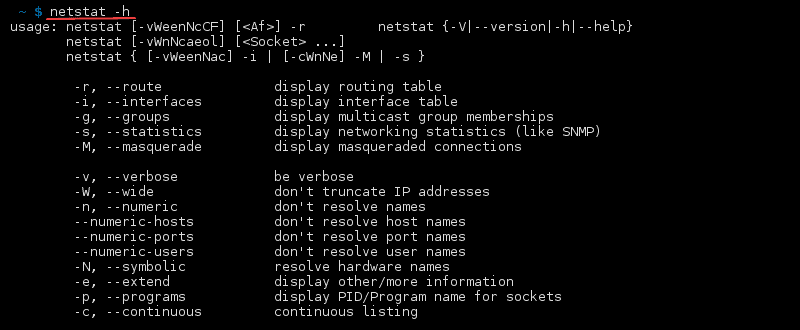
Frequently used options
Usage
The following lines will get you up the speed with some most popular netstat’s command line options. For most of the functions an administrative privileges are required to execute the netstat command:
Execution of the netstat command without any options or arguments displays all existing connections including their state, source address and local address. Additionally, active UNIX domain sockets and relevant information such as inode number and full path are part of the netstat’s default network reports. The netstat’s -i option brings up a table listing all configured network interfaces on the system:
# netstat -i Kernel Interface table Iface MTU RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg docker0 1500 0 0 0 0 0 0 0 0 BMU enp0s25 1500 148 0 0 0 1 0 0 0 BMU lo 65536 4752 0 0 0 4752 0 0 0 LRU wlp3s0 1500 148377 0 1 0 135793 0 0 0 BMRU
In case you prefer ifconfig’s format to provide you with a list all active network interfaces, # netstat -ei can accommodate your needs with an identical output. Another useful netstat’s command line options are -l and -t which are used displays all currently listening TCP sockets, that is to show all connections with LISTEN . This options might prove useful when performing a server hardening or firewall configuration. Alternatively add -u option to also include UDP connections:
# netstat -lt Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:http 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:ftp-data 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN tcp 0 0 localhost:ipp 0.0.0.0:* LISTEN tcp 0 0 localhost:smtp 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:https 0.0.0.0:* LISTEN tcp6 0 0 [::]:ssh [::]:* LISTEN tcp6 0 0 localhost:ipp [::]:* LISTEN tcp6 0 0 localhost:smtp [::]:* LISTEN
The above command showed local sockets eg. localhost:smtp with a human readable host name and service names. Using -n option this information is suppressed while numeric information is shown instead. Compare the below netstat’s output with the one above:
# netstat -ltn Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:20 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN tcp6 0 0 . 22 . * LISTEN tcp6 0 0 ::1:631 . * LISTEN tcp6 0 0 ::1:25 . * LISTEN
As already mentioned above the -l option only shows connections with the status “LISTEN”. The following netstat command shows all active TCP connections regardless of their status. To further enhance the above netstat command output, -p option can be used to show a program bind to any particular socket. This information may be useful to further harden your server and disable any unnecessary service. To demonstrate what -p option is capable of first open eg. port 20 for listing with netcat and list all connections with the “LISTEN” state and their relevant programs:
# netcat -l -p 20 & [1] 8941 # netstat -tlnp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 2891/nginx: master tcp 0 0 0.0.0.0:20 0.0.0.0:* LISTEN 8941/netcat tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 518/sshd tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 472/cupsd tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 2891/nginx: master tcp6 0 0 . 22 . * LISTEN 518/sshd tcp6 0 0 ::1:631 . * LISTEN 472/cupsd
Note that on the second line with socket 0.0.0.0:20 the netstat command also revealed a program and PID bind to that this socket, which in this case is netcat with PID 2891 . Using the -a option one could possibly monitor the entire TCP network connection handshake especially when coupled with -c option for a continuous listening.
# netstat -ant Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:20 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN tcp 1 0 10.1.1.8:36576 10.1.1.45:443 CLOSE_WAIT tcp 0 0 10.1.1.8:60186 10.1.1.11:443 ESTABLISHED tcp6 0 0 . 22 . * LISTEN tcp6 0 0 ::1:631 . * LISTEN tcp6 0 0 ::1:25 . * LISTEN
netstat command has a high number of options available to you disposal. Last two common options covered by in this guide are -r and -s . The first option -r is used to display a current system’s routing table.
# netstat -r Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface default gateway 0.0.0.0 UG 0 0 0 wlp3s0 10.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 wlp3s0 link-local 0.0.0.0 255.255.0.0 U 0 0 0 docker0 172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0
Once again the above output can be modified to suit your needs by -e and -n command line options. The last -s option is used to show detailed statistics :
Examples
| Command | Description |
|---|---|
| # netstat -st | Show a TCP protocol specific summary |
| # netstat -r | Display routing table |
| # netstat -ie | The equivalent to default ifconfig command to list all active network interfaces |
| # netstat -antc | Continuously monitor all TCP connection. use -u for UDP. |
| # netstat -ltp | Display all open TCP ports along with PID and program. |
| # netstat -atep | grep ssh | Show all SSH connection along with user name, program and corresponding PID. |
| # netstat -atnep | grep 443 | Show all connection on port 443 along with user ID, program and corresponding PID. |
| # netstat -s -w | Display raw network statistics |
Related Linux Tutorials:
Netstat Command in Linux — 28 Commands with Examples
The netstat command is a CLI tool for network statistics. It gives an overview of network activities and displays which ports are open or have established connections. The netstat tool is essential for discovering network problems.
This article shows 28 netstat commands for displaying port and internet statistics data on Linux.
Note: Though still widely used, netstat command is considered obsolete. Instead, the ss command is recommended as a faster and simpler tool. Learn more about the Linux ss command.
How to Use netstat Command in Linux
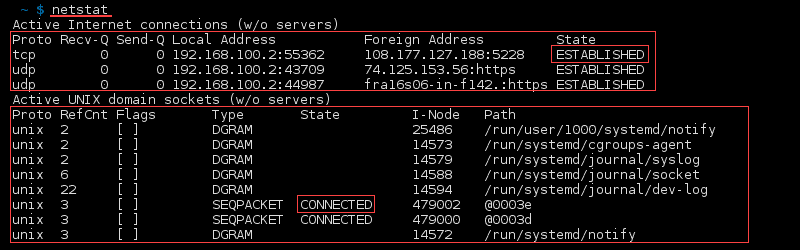
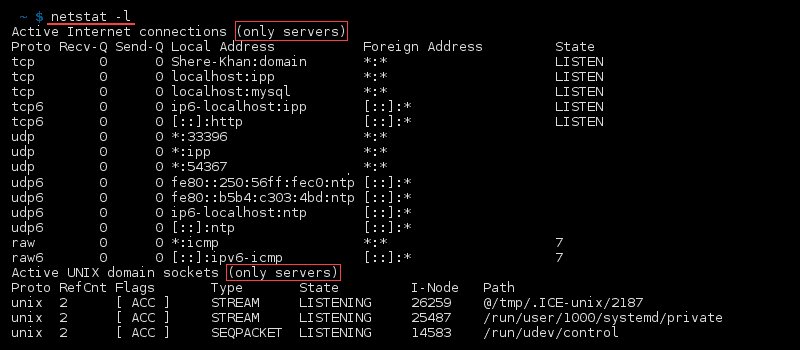
The primary usage of netstat is without any parameters:
The first list in the output displays active established internet connections on the computer. The following details are in the columns:
- Proto – Protocol of the connection (TCP, UDP).
- Recv-Q – Receive queue of bytes received or ready to be received.
- Send-Q – Send queue of bytes ready to be sent.
- Local address– Address details and port of the local connection. An asterisk (*) in the host indicates that the server is listening and if a port is not yet established.
- Foreign address– Address details and port of the remote end of the connection. An asterisk (*) appears if a port is not yet established.
- State– State of the local socket, most commonly ESTABLISHED,LISTENING, CLOSED or blank.
The second list shows all the active «Unix Domain» open sockets with the following details:
- Proto – Protocol used by the socket (always unix).
- RefCnt – Reference count of the number of attached processes to this socket.
- Flags – Usually ACC or blank.
- Type – The socket type.
- State – State of the socket, most often CONNECTED, LISTENING or blank.
- I-Node – File system inode (index node) associated with this socket.
- Path – System path to the socket.
For advanced usage, expand the netstat command with options:
Or list the options one by one:
netstat [option 1] [option 2] [option 3]The netstat options enable filtering of network information.
Note: If the network is slow, test the network speed.
List All Ports and Connections
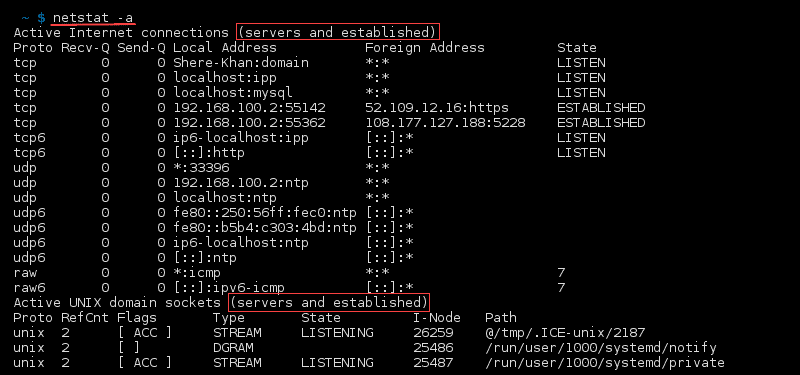
To list all ports and connections regardless of their state or protocol, use:
The output lists established connections along with servers which are open or listening.
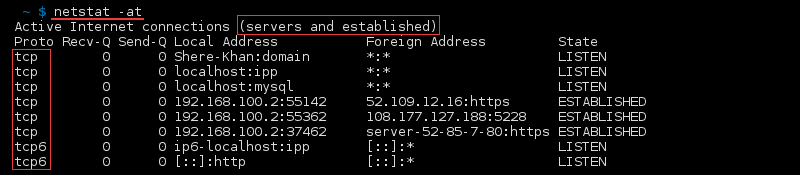
List All TCP Ports
List all TCP ports by running:
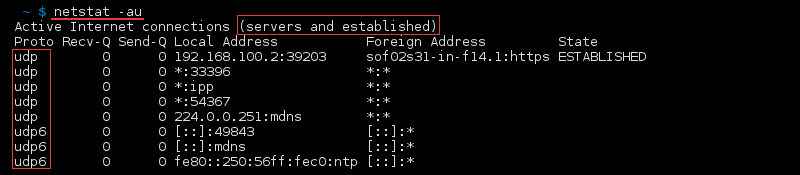
List All UDP Ports
List Only Listening Ports
To return a list of only listening ports for all protocols, use:
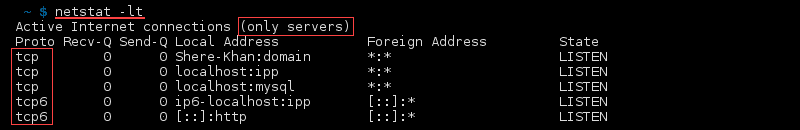
List TCP Listening Ports
List all listening TCP ports with:
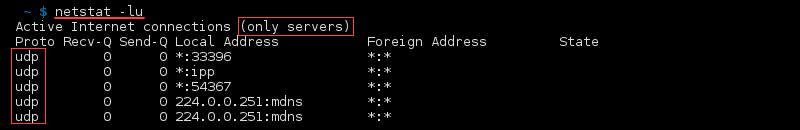
List UDP Listening Ports
Return only listening UDP ports by running:
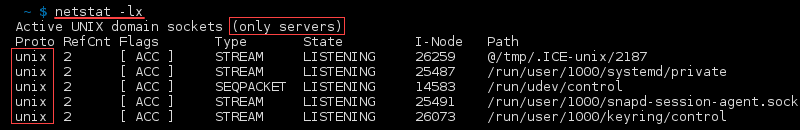
List UNIX Listening Ports
To list UNIX listening ports, use:
Note: Scan for open ports with nmap as an alternative.
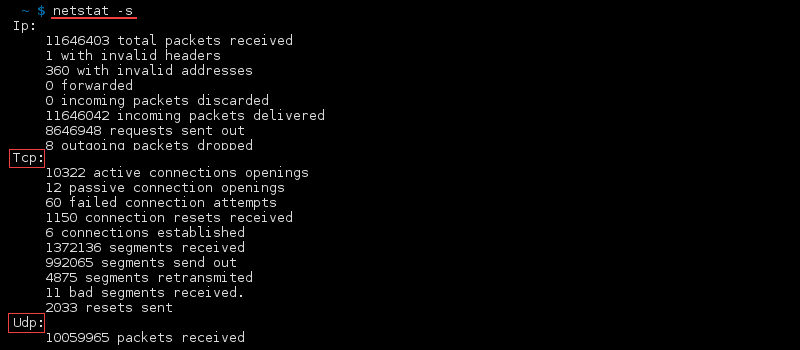
Display Statistics by Protocol
Display statistics for all ports regardless of the protocol with:
Statistics are also filterable by protocol.
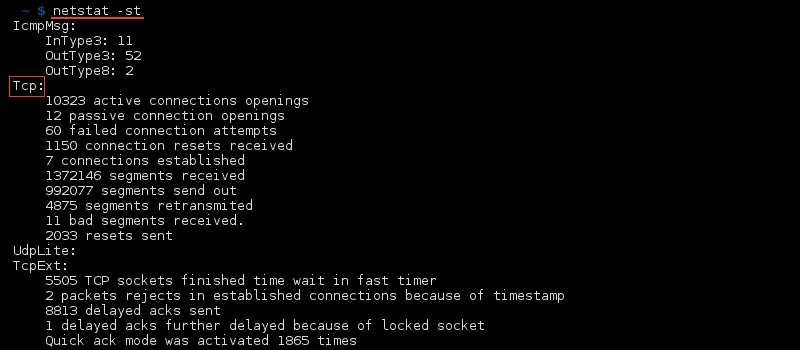
List Statistics for TCP Ports
List statistics for TCP ports only with:
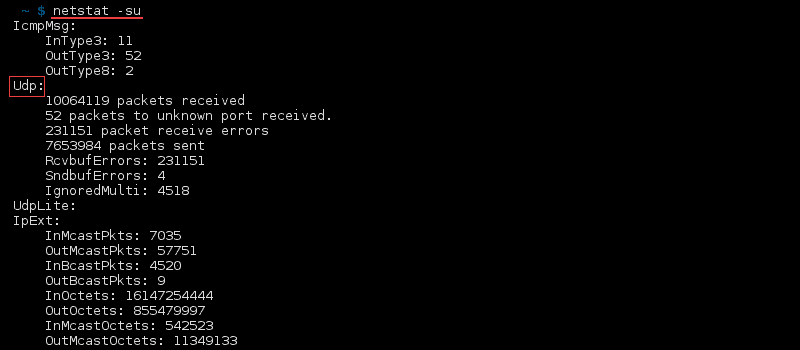
List Statistics for UDP Ports
To list statistics for UDP ports only, use:
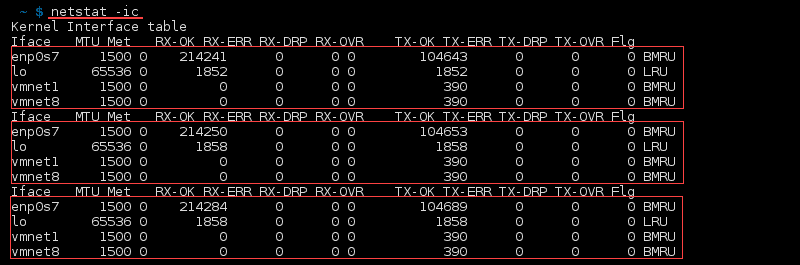
List Network Interface Transactions
To see transactions of MTU, receiving and transferring packets in the kernel interface table, use:
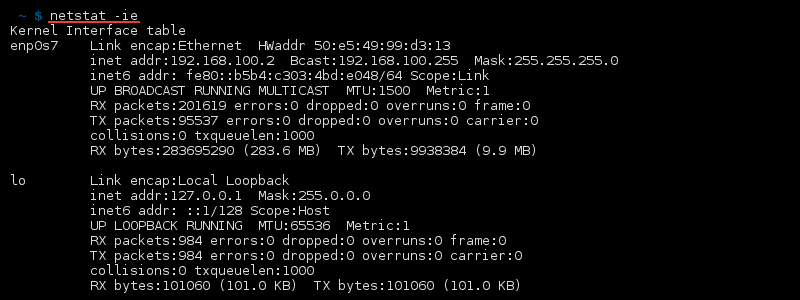
Display Extended Kernel Interface Table
Add the option -e to netstat -i to extend the details of the kernel interface table:
Display Masqueraded Connections
For displaying masqueraded connections, use:
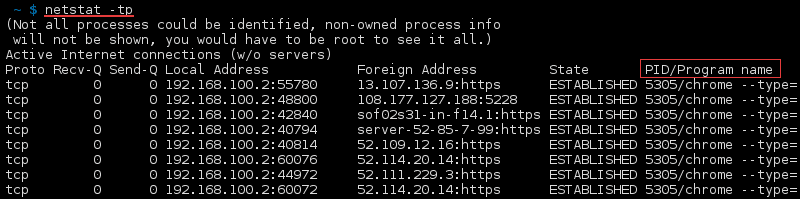
Display PID
Display the PID/Program name related to a specific connection by adding the -p option to netstat . For example, to view the TCP connections with the PID/Program name listed, use:
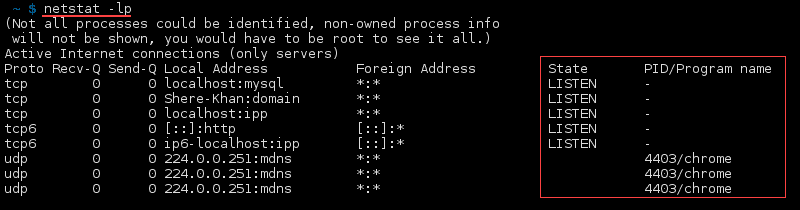
Find Listening Programs
Find all listening programs with:
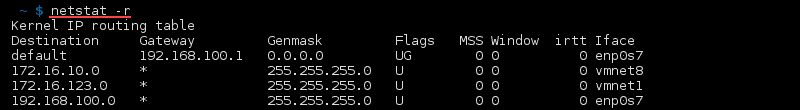
Display Kernel IP Routing Table
Display the kernel IP routing table with:
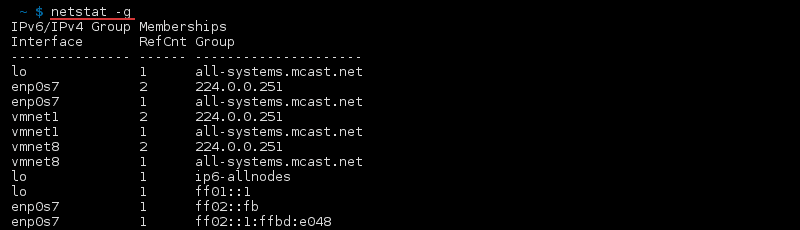
Display IPv4 and IPv6 Group Membership
Display group membership for IPv6/IPv4 with:
Print netstat Info Continuously
Add the -c option to the netstat command to print information every second:
For example, to print the kernel interface table continuously, run:
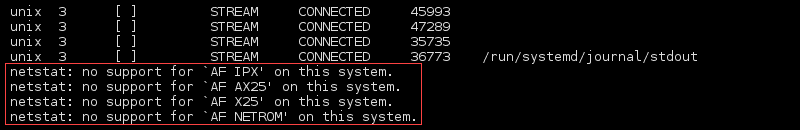
Find Unconfigured Address Families
List addresses without support on the system with:
The information is found at the end of the output:
Display Numerical Addresses, Host Addresses, Port Numbers, and User IDs
By default, addresses, port numbers, and user IDs are resolved into human-readable names when possible. Knowing the unresolved port number is important for tasks such as SSH port forwarding.
Display Numerical Addresses
Show numerical addresses with:
Display Numerical Host Addresses
To show only host addresses as numerical, run:
Display Numerical Port Numbers
Show only ports as numerical with:
Display Numerical User Ids
To display numerical user IDs, use:
Find a Process That Is Using a Particular Port
Make use of the grep command to filter the data from netstat . To find a process that is using a particular port number, run:
netstat -an | grep ':[port number]'List All netstat Commands
There are many netstat options available. Access the list of all the available commands and a short description using:
Note: Check out the Linux commands cheat sheet, which features the netstat command.
Netstat is an essential tool for network engineers, system administrators, and developers. Troubleshooting network problems and having an overview of all the network activities and port availability are just some use cases of this tool.
For further reading, find out about the best network security tools.
Milica Dancuk is a technical writer at phoenixNAP who is passionate about programming. Her background in Electrical Engineering and Computing combined with her teaching experience give her the ability to easily explain complex technical concepts through her content.
This article shows you numerous ways to test network speed in Linux via CLI. Learn how to install and use.
Configure CentOS network settings using the command line or the Network Manager TUI. This guide shows you how.
Nmap stands for Network Mapper. It is an open source tool for network exploration and security auditing.