- Configuring SSH Tunnels in Oracle Linux
- Objectives
- What Do You Need?
- Configuring SSH Tunneling
- Configuring SSH dynamic port forwarding
- Configuring SSH local port forwarding
- Video Demonstration
- More Learning Resources
- How to Create SSH Tunneling or Port Forwarding in Linux
- Testing Environment:
- Local SSH Port Forwarding
- Remote SSH Port Forwarding
- Dynamic SSH Port Forwarding
- How to setup SSH tunneling on Linux
- Perquisites
- Local Port Forwarding
- About the author
- John Otieno
- RELATED LINUX HINT POSTS
Configuring SSH Tunnels in Oracle Linux
This tutorial provides step by step procedures to configure SSH tunnels for network traffic. SSH tunnels or SSH forwarding encapsulates specific TCP traffic and enables it to traverse the network through an SSH connection. This tutorial is targeted at users of Oracle Linux 8 or later.
Objectives
This tutorial teaches you how to configure the following types of SSH tunneling:
What Do You Need?
- A remote SSH system with the some configured services, such as web services, VNC services, Cockpit, etc to be used by remote clients.
- A client system with appropriate software installed, such as a desktop viewer to use VNC services.
Configuring SSH Tunneling
Note: When using the free lab environment, see Oracle Linux Lab Basics for connection and other usage instructions.
Configuring SSH dynamic port forwarding
Dynamic port forwarding enables communications across a range of ports by making SSH act as a SOCKS proxy server.
Note: Unless instructed otherwise, you must run all the commands in this section from your SSH client desktop.
- If you are currently connected to ol8-server in a terminal window, type exit to disconnect from the instance. Alternatively, open a new tab for a separate terminal window.
- Open an ssh connection to ol8-server while using the -D option and specifying a port number to use locally. The -D option indicates that the connection uses dynamic port forwarding.
- -N prevents the execution of remote commands.
- -f indicates that the connection is forked into the background.
- sleep specifies a waiting period in seconds that the tunnel waits for a connection before the tunnel closes.
curl -w '\n' --socks5 localhost:8080 ifconfig.me By using the dynamic port forwarding service, you can redirect or forward TCP traffic from one system to another over a secure connection. This service functions as a rudimentary VPN. Thus, you can configure a local web browser to use the SOCKS proxy for forwarded browsing. Or, as an alternative, you can configure SOCKS proxy settings by defining a variable as follows, and then retest with the curl command.
export _proxy="socks5://localhost:8080" curl -w '\n' ifconfig.me Other mechanisms can be used to force all TCP traffic through your SSH connection. However, these are beyond the scope of this tutorial. In addition, alternative methods might be preferable than using SSH tunnels for this purpose.
Configuring SSH local port forwarding
Local port forwarding over SSH maps a local port on the client system to a remote port on the server system. This configuration enables you to access services on the remote system that are otherwise inaccessible because the services might be running behind a firewall or might not be listening on a public network interface.
Cockpit is a good example of such a service. Typically, if you want to run the Cockpit web console for a system that is connected to the Internet, the service would be exposed on a public facing network, which is not advisable.
For this demonstration, the ol8-server is configured for security as follows:
- The instance is preconfigured to run the Cockpit service.
- The instance is running a firewall service.
- The Cockpit port is not open.
Note: Unless instructed otherwise, all the commands must be typed from your SSH client desktop.
- If you are currently connected to the ol8-server in a terminal window, type exit to disconnect from the instance. Alternatively, open a new tab for a separate terminal window.
- Verify the inaccessibility of the Cockpit service. On a browser, open the Cockpit web console to ol8-server through its IP address. Note that the connection does not succeed. http://:9090/ The connection does not succeed.
- On the terminal window, open an SSH connection to ol8-server by using local port forwarding. The -L option maps a port on the local host to a port on the server.
ssh -L 9090:localhost:9090 oracle@
- -N prevents the execution of remote commands.
- -f indicates that the connection is forked into the background.
- sleep specifies a waiting period in seconds that the tunnel waits for a connection before the tunnel closes.
By using the Cockpit web console, you can remotely manage the instance even though the service itself is not exposed on any public facing network.
Video Demonstration
The video tutorial Using SSH Tunnels With Oracle Linux 8 gives more examples for configuring different types of SSH tunnels. Note that while the lab exercises demonstrated SSH tunneling by using the Cockpit service, this video uses VNC and web services for its examples. All of them together show how, through SSH port forwarding, you can access and avail of a remote system’s services.

More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Configuring SSH Tunnels in Oracle Linux
Copyright © 2021, Oracle and/or its affiliates.
How to Create SSH Tunneling or Port Forwarding in Linux
SSH tunneling (also referred to as SSH port forwarding) is simply routing the local network traffic through SSH to remote hosts. This implies that all your connections are secured using encryption. It provides an easy way of setting up a basic VPN (Virtual Private Network), useful for connecting to private networks over unsecure public networks like the Internet.
You may also be used to expose local servers behind NATs and firewalls to the Internet over secure tunnels, as implemented in ngrok.
SSH sessions permit tunneling network connections by default and there are three types of SSH port forwarding: local, remote and dynamic port forwarding.
In this article, we will demonstrate how to quickly and easily set up SSH tunneling or the different types of port forwarding in Linux.
Testing Environment:
For the purpose of this article, we are using the following setup:
- Local Host: 192.168.43.31
- Remote Host: Linode CentOS 7 VPS with hostname server1.example.com.
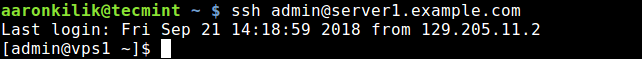
Usually, you can securely connect to a remote server using SSH as follows. In this example, I have configured passwordless SSH login between my local and remote hosts, so it has not asked for user admin’s password.
Local SSH Port Forwarding
This type of port forwarding lets you connect from your local computer to a remote server. Assuming you are behind a restrictive firewall or blocked by an outgoing firewall from accessing an application running on port 3000 on your remote server.
You can forward a local port (e.g 8080) which you can then use to access the application locally as follows. The -L flag defines the port forwarded to the remote host and remote port.
$ ssh [email protected] -L 8080:server1.example.com:3000
Adding the -N flag means do not execute a remote command, you will not get a shell in this case.
$ ssh -N [email protected] -L 8080:server1.example.com:3000
The -f switch instructs ssh to run in the background.
$ ssh -f -N [email protected] -L 8080:server1.example.com:3000
Now, on your local machine, open a browser, instead of accessing the remote application using the address server1.example.com:3000, you can simply use localhost:8080 or 192.168.43.31:8080 , as shown in the screenshot below.
Remote SSH Port Forwarding
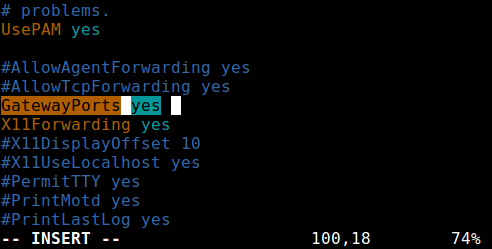
Remote port forwarding allows you to connect from your remote machine to the local computer. By default, SSH does not permit remote port forwarding. You can enable this using the GatewayPorts directive in your SSHD main configuration file /etc/ssh/sshd_config on the remote host.
Open the file for editing using your favorite command-line editor.
$ sudo vim /etc/ssh/sshd_config
Look for the required directive, uncomment it, and set its value to yes , as shown in the screenshot.
Save the changes and exit. Next, you need to restart sshd to apply the recent change you made.
$ sudo systemctl restart sshd OR $ sudo service sshd restart
Next run the following command to forward port 5000 on the remote machine to port 3000 on the local machine.
Once you understand this method of tunneling, you can easily and securely expose a local development server, especially behind NATs and firewalls to the Internet over secure tunnels. Tunnels such as Ngrok, pagekite, localtunnel, and many others work in a similar way.
Dynamic SSH Port Forwarding
This is the third type of port forwarding. Unlike local and remote port forwarding which allows communication with a single port, it makes possible, a full range of TCP communications across a range of ports. Dynamic port forwarding sets up your machine as a SOCKS proxy server that listens on port 1080, by default.
For starters, SOCKS is an Internet protocol that defines how a client can connect to a server via a proxy server (SSH in this case). You can enable dynamic port forwarding using the -D option.
The following command will start a SOCKS proxy on port 1080 allowing you to connect to the remote host.
From now on, you can make applications on your machine use this SSH proxy server by editing their settings and configuring them to use it, to connect to your remote server. Note that the SOCKS proxy will stop working after you close your SSH session.
Summary
In this article, we explained the various types of port forwarding from one machine to another, for tunneling traffic through the secure SSH connection. This is one of the very many uses of SSH. You can add your voice to this guide via the feedback form below.
Attention: SSH port forwarding has some considerable disadvantages, it can be abused: it can be used to bypass network monitoring and traffic filtering programs (or firewalls). Attackers can use it for malicious activities. In our next article, we will show how to disable SSH local port forwarding. Stay connected!
How to setup SSH tunneling on Linux
SSH tunneling commonly known as SSH port forwarding is a technique of routing local network traffic over through encrypted SSH on remote hosts. Routing network traffic via SSH tunnels ensure high level of data encryption and security, especially for unencrypted network protocols such as FTP. This is very useful especially when connected to unsecured networks.
This tutorial will explain how to set up an SSH tunnel and securely route your traffic via secure tunnels. We will discuss all three methods of SSH port forwarding:
Perquisites
For this tutorial, you are going to need:
Local Port Forwarding
This type of port forwarding allows you to forward a port on the local machine to a specific port on a remote machine which is then forwarded to the destination address.
Local port forwarding allows the local machine to listen on a given port and tunnel any traffic to the specific port to the port specified on the remote server. Once the remote server receives the traffic, it is forwarded to the set destination address.
To create a local port forward, we use the -L flag for the SSH command:
If you do not specify LOCAL_IP, the local SSH client will automatically bind to localhost. You also need to specify ports larger than 1024 as they are not restricted to root users only.
Assume you have a service running on the machine my.service on port 5000 and can only be accessed on machine access.machine. If you want to connect to the service from your local machine, you need to forward your connection as:
Once you execute the command, you will need to provide the SSH password for the specified user. For ease of use, you can set a password-less login using SSH keys.
You can now access the service from your local machine using the port specified (5555) where the access.machine acts as intermediate.
About the author
John Otieno
My name is John and am a fellow geek like you. I am passionate about all things computers from Hardware, Operating systems to Programming. My dream is to share my knowledge with the world and help out fellow geeks. Follow my content by subscribing to LinuxHint mailing list
RELATED LINUX HINT POSTS
Linux Hint LLC, editor@linuxhint.com
1309 S Mary Ave Suite 210, Sunnyvale, CA 94087
Privacy Policy and Terms of Use