- ⚡️🗄 10 лучших инструментов Kali Linux для взлома
- 2. Nmap
- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- Список инструментов Kali Linux
- Сбор информации
- Анализ уязвимостей
- Криминалистические инструменты
- Беспроводные атаки
- Стресс-тестирование
- Веб приложения
- Инструменты эксплуатации
- Sniffing и Spoofing
- Атаки на пароли
- Поддержка доступа
- Взлом оборудования
- Анонимность
- Шифрование данных и антикриминалистика
- Обратная инженерия
- Инструменты по составлению отчётов
- Уязвимые среды и программы для тренировки
- Top 10 Kali Linux Tools For Hacking
- 1. Nmap
- 2. Burp Suite
- 3. Wireshark
- 4. metasploit Framework
- 5. aircrack-ng
- 7. John the Ripper
- 8. sqlmap
- 9. Autopsy
- 10. Social Engineering Toolkit
⚡️🗄 10 лучших инструментов Kali Linux для взлома
Kali Linux — это дистрибутив Linux на основе Debian. Kali Linux была разработана Мати Ахарони и Девоном Кернсом. Это специально созданная операционная система для сетевых аналитиков, пентестеров и других специалистов, работающих в области кибербезопасности и анализа.
Официальный сайт Kali Linux — Kali.org. Он стал известен после появления в телесериале «Мистер Робот». Он не предназначен для публичного использования; скорее, он предназначен для профессионалов или людей, знакомых с Linux/Kali.
При выполнении тестирования на проникновение или взломе нам может потребоваться автоматизировать наши операции, так могут быть протестированы сотни условий и нагрузок, а тестирование их вручную утомительно. Чтобы сэкономить время, мы используем инструменты, которые предустановлены вместе с Kali Linux. Эти инструменты не только экономят наше время, но и собирают надежные данные и выдают точные результаты. В Kali Linux включено более 350 инструментов, которые можно использовать для взлома или тестирования на проникновение.
Ниже приведен список 10 лучших инструментов Kali Linux для взлома:
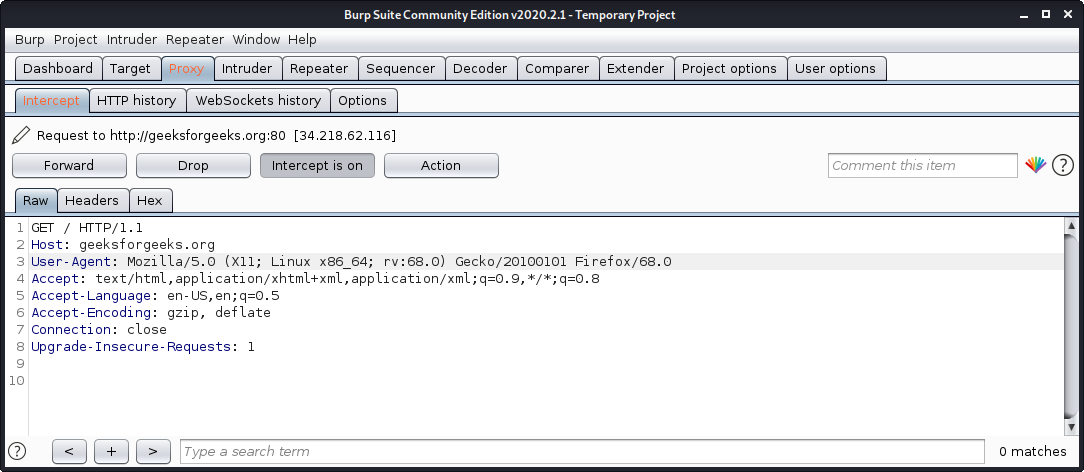
Одним из наиболее широко используемых инструментов тестирования безопасности веб-приложений является Burp Suite. Он используется как прокси, что означает, что все запросы от браузера прокси проходят через него. И, поскольку запрос проходит через пакет burp, мы можем вносить в него изменения по мере необходимости, что полезно для тестирования уязвимостей, таких как XSS и SQLi, и других проблем, связанных с Интернетом.
Версия Burp Suite Community Edition бесплатна для Kali Linux, но есть премиум-версия под названием burp Suite Professional, которая имеет гораздо больше функций, чем бесплатная версия.
Чтобы использовать Burpsuite:
Мы должны сделать следующие шаги :
Во-первых, мы должны научиться настраивать набор для Burpsuite.
Затем нам нужно открыть терминал и ввести «burpsuite».
Перейдите на вкладку «Прокси» и включите переключатель перехватчика.
Теперь посетите любой URL-адрес, и вы увидите, что запрос был перехвачен.
2. Nmap
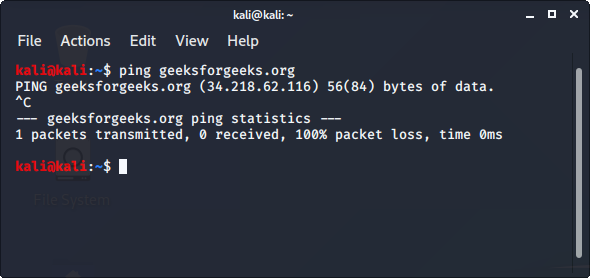
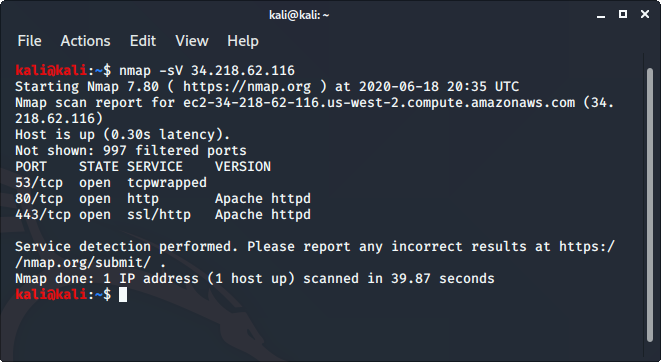
Nmap — это сетевой сканер с открытым исходным кодом для реконфигурации и сканирования сетей. Он используется для поиска портов, хостов и служб вместе с их версиями в сети. Он отправляет пакеты на хост, а затем проверяет ответы, чтобы получить ожидаемые результаты. Его также можно использовать для обнаружения хостов, обнаружения операционных систем и сканирования открытых портов. Это один из наиболее широко используемых разведывательных инструментов.
Мы должны использовать следующие шаги:
Во-первых, мы должны пропинговать хост с помощью команды ping, чтобы получить IP-адрес.
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
Список инструментов Kali Linux
Сбор информации
Анализ уязвимостей
- APT2
- BBQSQL
- BED
- cisco-auditing-tool
- cisco-global-exploiter
- cisco-ocs
- cisco-torch
- copy-router-config
- CrackMapExec
- DBPwAudit
- Doona
- DotDotPwn
- Greenbone Security Assistant
- GSD
- HexorBase
- Inguma
- jSQL Injection
- Lynis
- Nmap
- NoSQLMap
- ohrwurm
- openvas-administrator
- openvas-cli
- openvas-manager
- openvas-scanner
- Oscanner
- Powerfuzzer
- sfuzz
- SidGuesser
- SIPArmyKnife
- sqlmap
- Sqlninja
- sqlsus
- THC-IPV6
- tnscmd10g
- unix-privesc-check
- Yersinia
Криминалистические инструменты
Беспроводные атаки
Стресс-тестирование
- DHCPig
- FunkLoad
- iaxflood
- Inundator
- inviteflood
- ipv6-toolkit
- mdk3
- PytheM
- Reaver (reaver-wps-fork-t6x)
- rtpflood
- SlowHTTPTest
- t50
- Termineter
- THC-IPV6
- THC-SSL-DOS
- wifijammer
Веб приложения
Инструменты эксплуатации
- Armitage
- APT2
- Backdoor Factory
- BeEF
- BDFProxy
- Cameradar
- cisco-auditing-tool
- cisco-global-exploiter
- cisco-ocs
- cisco-torch
- Commix
- crackle
- DS_Store_crawler_parser
- ds_store_exp
- Evilginx
- evilginx2
- Invoke-TheHash
- jboss-autopwn
- keimpx
- Linux Exploit Suggester
- Maltego
- Metasploit
- mimikatz
- MSFvenom Payload Creator (MSFPC)
- mXtract
- ngrok
- PoisonTap
- Router Scan by Stas’M
- RouterSploit
- seeker
- SET
- ShellNoob
- Spraykatz
- sqlmap
- sshprank
- THC-IPV6
- WPForce
- WPSploit
- XPL SEARCH
- Yersinia
Sniffing и Spoofing
- arpspoof
- bettercap
- Burp Suite
- DNSChef
- dns2proxy
- Driftnet
- etter.conf
- Ettercap
- Ettercap_curses и Ettercap-pkexec
- ettercap-plugins
- Etterfilter
- Etterlog
- fiked
- hamster-sidejack
- HexInject
- iaxflood
- Intercepter-NG
- inviteflood
- iSMTP
- isr-evilgrade
- LANs
- Mana
- MITMf
- mitmproxy
- Net-Creds
- ohrwurm
- protos-sip
- PytheM
- rebind
- Responder
- rtpbreak
- rtpinsertsound
- rtpmixsound
- sctpscan
- SIPArmyKnife
- SIPp
- SIPVicious
- SniffJoke
- SSH MITM
- SSLsplit
- SSLstrip (SSLStrip+)
- THC-IPV6
- Urlsnarf
- VoIPHopper
- WebScarab
- Webspy
- Wifi Honey
- Wireshark
- Xerosploit
- xspy
- Yersinia
- zaproxy
Атаки на пароли
Поддержка доступа
- backdoor-apk
- CryptCat
- Cymothoa
- dbd
- dns2tcp
- http-tunnel
- HTTPTunnel
- Intersect
- Nishang
- Ncat, Netcat, nc
- PhpSploit
- PoisonTap
- polenum
- PowerSploit
- Pupy
- pwnat
- RidEnum
- sbd
- shellter
- U3-Pwn
- Webshells
- Weevely
- Winexe
Взлом оборудования
- android-sdk
- apktool
- Appie
- Arduino
- dex2jar
- Sakis3G
- smali
Анонимность
Шифрование данных и антикриминалистика
Обратная инженерия
Инструменты по составлению отчётов
Уязвимые среды и программы для тренировки
Top 10 Kali Linux Tools For Hacking
Kali Linux is a Debian-derived Linux distribution that is maintained by Offensive Security. It was developed by Mati Aharoni and Devon Kearns. Kali Linux is a specially designed OS for network analysts, Penetration testers, or in simple words, it is for those who work under the umbrella of cybersecurity and analysis. The official website of Kali Linux is Kali.org. It gained its popularity when it was practically used in Mr. Robot Series. It was not designed for general purposes, it is supposed to be used by professionals or by those who know how to operate Linux/Kali. To know how to install Kali Linux check its official documentation. Sometimes we have to automate our tasks while performing penetration testing or hacking as there could be thousands of conditions and payloads to test and testing them manually is a difficult task, So to increase the time efficiency we use tools that come pre-packed with Kali Linux. These tools not only saves our time but also captures the accurate data and output the specific result. Kali Linux comes packed with more than 350 tools which could be useful for hacking or penetration testing. Here we have the list of important Kali Linux tools that could save a lot of your time and effort.
1. Nmap
Nmap is an open-source network scanner that is used to recon/scan networks. It is used to discover hosts, ports, and services along with their versions over a network. It sends packets to the host and then analyzes the responses in order to produce the desired results. It could even be used for host discovery, operating system detection, or scanning for open ports. It is one of the most popular reconnaissance tools. To use nmap:
- Replace the IP address with the IP address of the host you want to scan.
- It will display all the captured details of the host.
To know more, you can read more from here .
2. Burp Suite
Burp Suite is one of the most popular web application security testing software. It is used as a proxy, so all the requests from the browser with the proxy pass through it. And as the request passes through the burp suite, it allows us to make changes to those requests as per our need which is good for testing vulnerabilities like XSS or SQLi or even any vulnerability related to the web. Kali Linux comes with burp suite community edition which is free but there is a paid edition of this tool known as burp suite professional which has a lot many functions as compared to burp suite community edition. To use burpsuite:
- Read this to learn how to setup burp suite.
- Open terminal and type “burpsuite” there.
- Go to the Proxy tab and turn the interceptor switch to on.
- Now visit any URL and it could be seen that the request is captured.
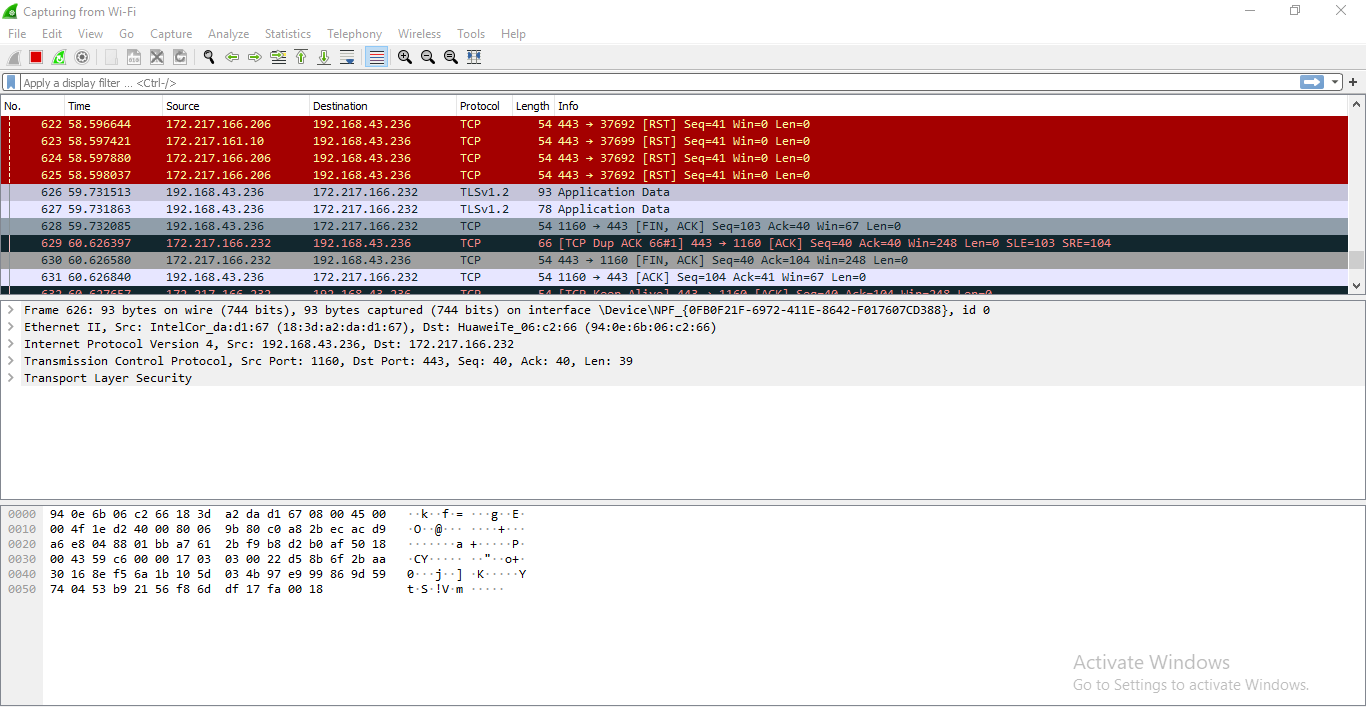
3. Wireshark
Wireshark is a network security tool used to analyze or work with data sent over a network. It is used to analyze the packets transmitted over a network. These packets may have information like the source IP and the destination IP, the protocol used, the data, and some headers. The packets generally have an extension of “.pcap” which could be read using the Wireshark tool. Read thisto learn how to set up and configure Wireshark. To use wireshark:
- Open Wireshark and download a demo pcap file from here
- Press”ctrl+o” to open a pcap file in wireshark.
- Now it can be seen that it display the list of packets along with the headers of these packets.
4. metasploit Framework
Metasploit is an open-source tool that was designed by Rapid7 technologies. It is one of the world’s most used penetration testing frameworks. It comes packed with a lot of exploits to exploit the vulnerabilities over a network or operating systems. Metasploit generally works over a local network but we can use Metasploit for hosts over the internet using “port forwarding“. Basically Metasploit is a CLI based tool but it even has a GUI package called “armitage” which makes the use of Metasploit more convenient and feasible. To use metasploit:
- Metasploit comes pre-installed with Kali Linux
- Just enter “msfconsole” in the terminal.
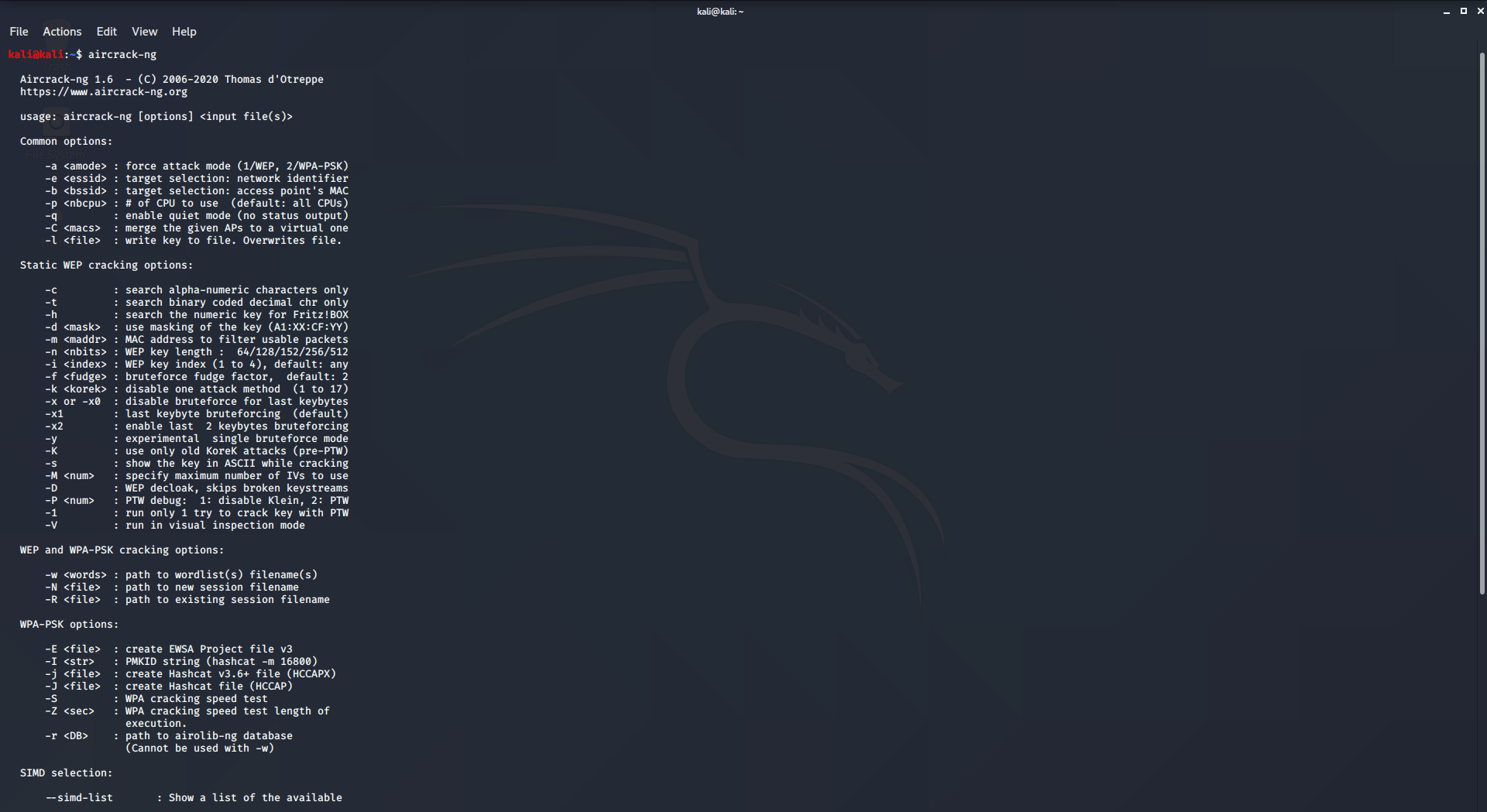
5. aircrack-ng
Aircrack is an all in one packet sniffer, WEP and WPA/WPA2 cracker, analyzing tool and a hash capturing tool. It is a tool used for wifi hacking. It helps in capturing the package and reading the hashes out of them and even cracking those hashes by various attacks like dictionary attacks. It supports almost all the latest wireless interfaces. To use aircrack-ng:
- aircrack-ng comes pre-compiled with Kali Linux.
- Simply type aircrack-ng in the terminal to use it.
6. Netcat Netcat is a networking tool used to work with ports and performing actions like port scanning, port listening, or port redirection. This command is even used for Network Debugging or even network daemon testing. This tool is considered as the Swiss army knife of networking tools. It could even be used to do the operating related to TCP, UDP, or UNIX-domain sockets or to open remote connections and much more. To use netcat:
- Netcat comes pre-installed with Kali Linux.
- Just type “nc” or “netcat” in the terminal to use the tool.
- To perform port listening type the following commands in 2 different terminals.
Read this for more information regarding netcat tool.
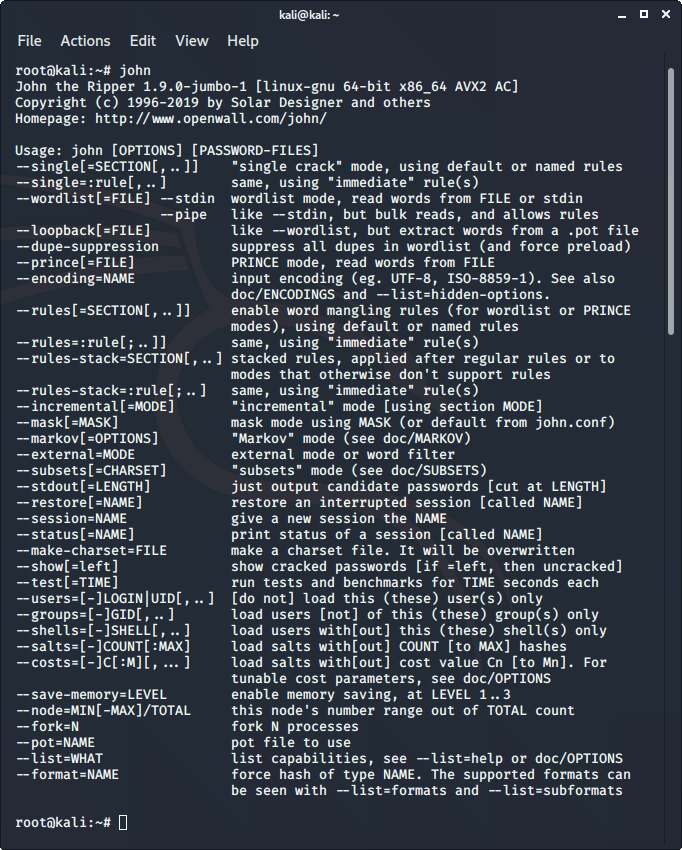
7. John the Ripper
John the Ripper is a great tool for cracking passwords using some famous brute force attacks like dictionary attack or custom wordlist attack etc. It is even used to crack the hashes or passwords for the zipped or compressed files and even locked files as well. It has many available options to crack hashes or passwords. To use John the Ripper:
- John the ripper comes pre-installed in Kali Linux.
- Just type “john” in the terminal to use the tool.
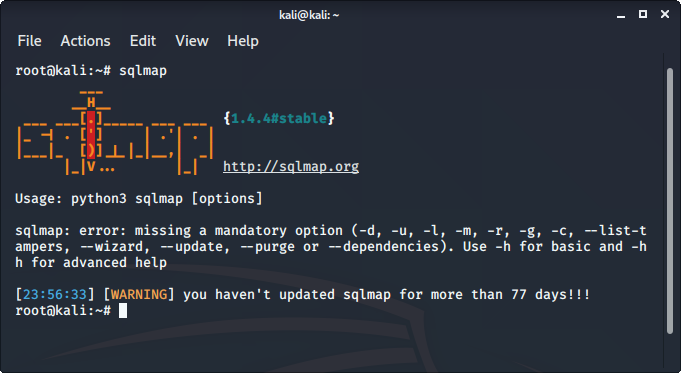
8. sqlmap
sqlmap is one of the best tools to perform SQL injection attacks. It just automates the process of testing a parameter for SQL injection and even automates the process of exploitation of the vulnerable parameter. It is a great tool as it detects the database on its own so we just have to provide a URL to check whether the parameter in the URL is vulnerable or not, we could even use the requested file to check for POST parameters. To use sqlmap tool:
- sqlmap comes pre-installed in Kali Linux
- Just type sqlmap in the terminal to use the tool.
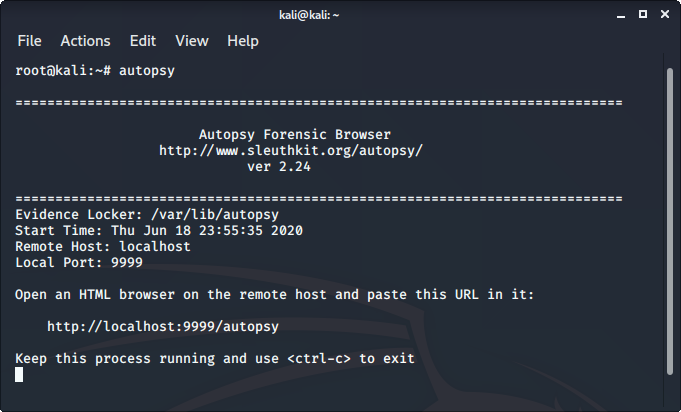
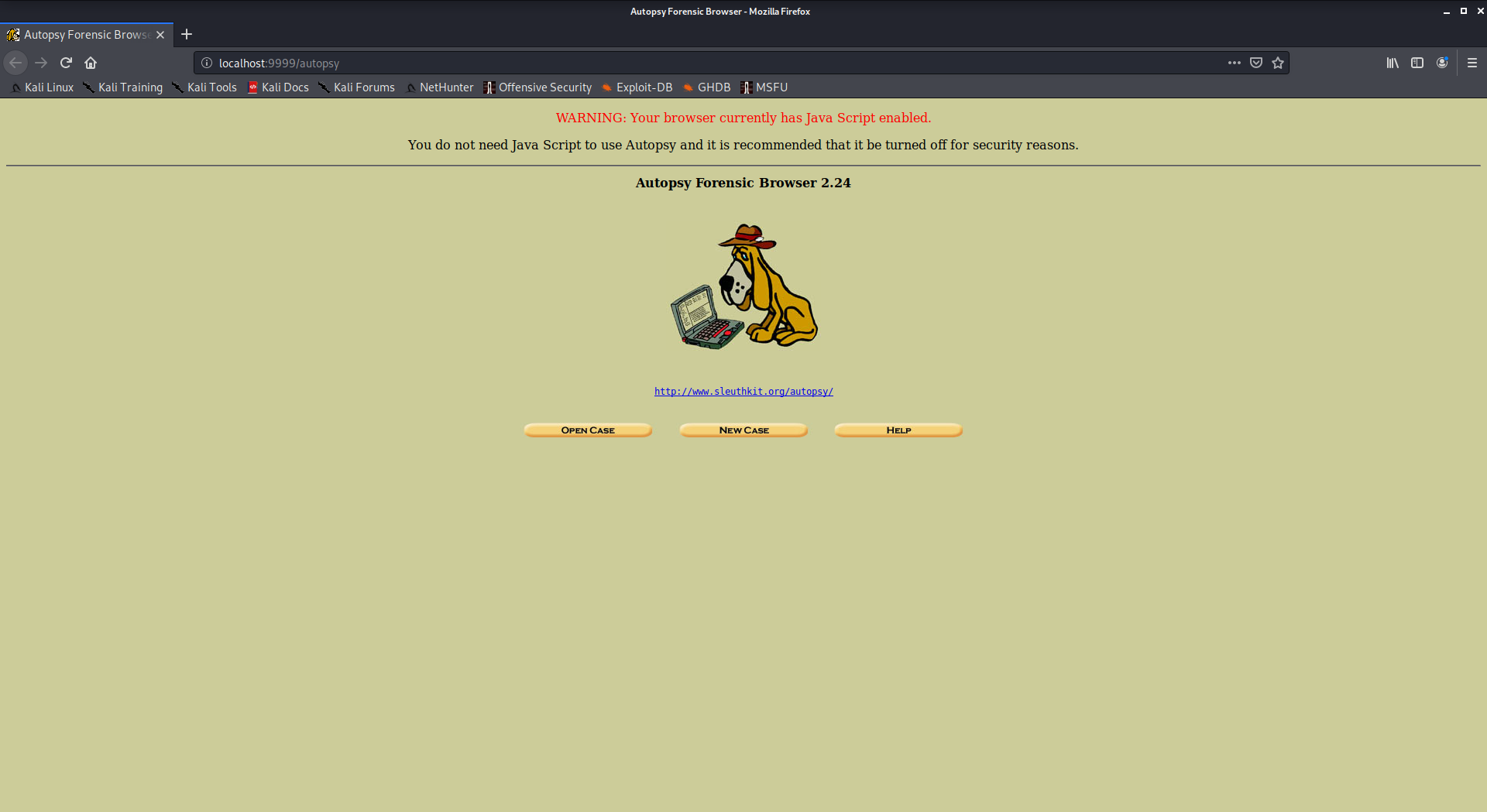
9. Autopsy
Autopsy is a digital forensics tool that is used to gather information from forensics. Or in other words, this tool is used to investigate files or logs to learn about what exactly was done with the system. It could even be used as a recovery software to recover files from a memory card or a pen drive. To use autopsy tool:
- Autopsy comes pre-installed in Kali Linux
- Just type “autopsy” in the terminal.
- Now visit http://localhost:9999/autopsy in order to use the tool.
10. Social Engineering Toolkit
Social Engineering Toolkit is a collection of tools that could be used to perform social engineering attacks. These tools use and manipulate human behavior for information gathering. it is a great tool to phish the websites even. To use Social Engineering Toolkit
- Social Engineering Toolkit comes pre-installed with Kali Linux
- Just type “setoolkit” in the terminal.
- Agree to the terms and conditions to start using the social engineering toolkit.