Kali Linux – Password Cracking Tool
Password cracking is a mechanism that is used in most of the parts of hacking. Exploitation uses it to exploit the applications by cracking their administrator or other account passwords, Information Gathering uses it when we have to get the social media or other accounts of the C.E.O. or other employees of the target organization, Wifi Hacking uses it when we have to crack the hash from the captured wifi password hash file, etc.
So to be a good Ethical hacker one must be aware of password cracking techniques. Though it is easy to crack passwords by just using guessing techniques, it is very time consuming and less efficient so in order to automate the task, we have a lot of tools. When it comes to tools Kali Linux is the Operating System that stands first, So here we have a list of tools in Kali Linux that may be used for Password Cracking.
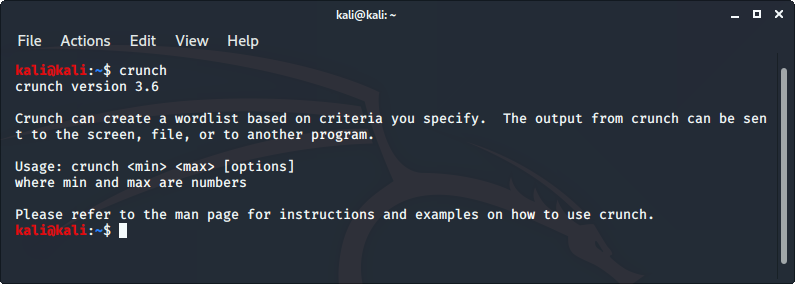
In order to hack a password, we have to try a lot of passwords to get the right one. When an attacker uses thousands or millions of words or character combinations to crack a password there is no surety that any one of those millions of combinations will work or not. This collection of a different combination of characters is called a wordlist. And in order to crack a password or a hash, we need to have a good wordlist which could break the password. So to do so we have a tool in Kali Linux called crunch.
crunch is a wordlist generating tool that comes pre-installed with Kali Linux. It is used to generate custom keywords based on wordlists. It generates a wordlist with permutation and combination. We could use some specific patterns and symbols to generate a wordlist.
To use crunch, enter the following command in the terminal.
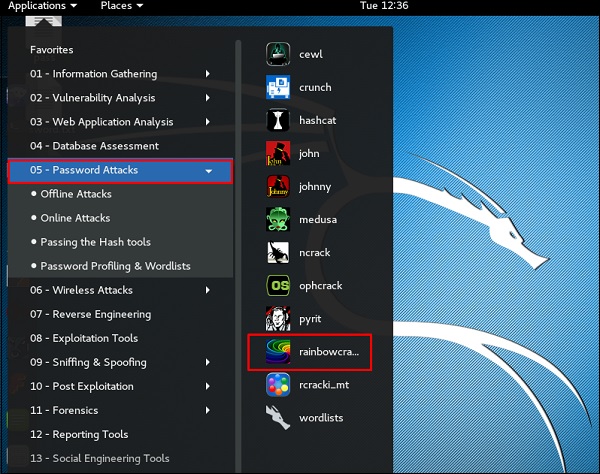
2. RainbowCrack
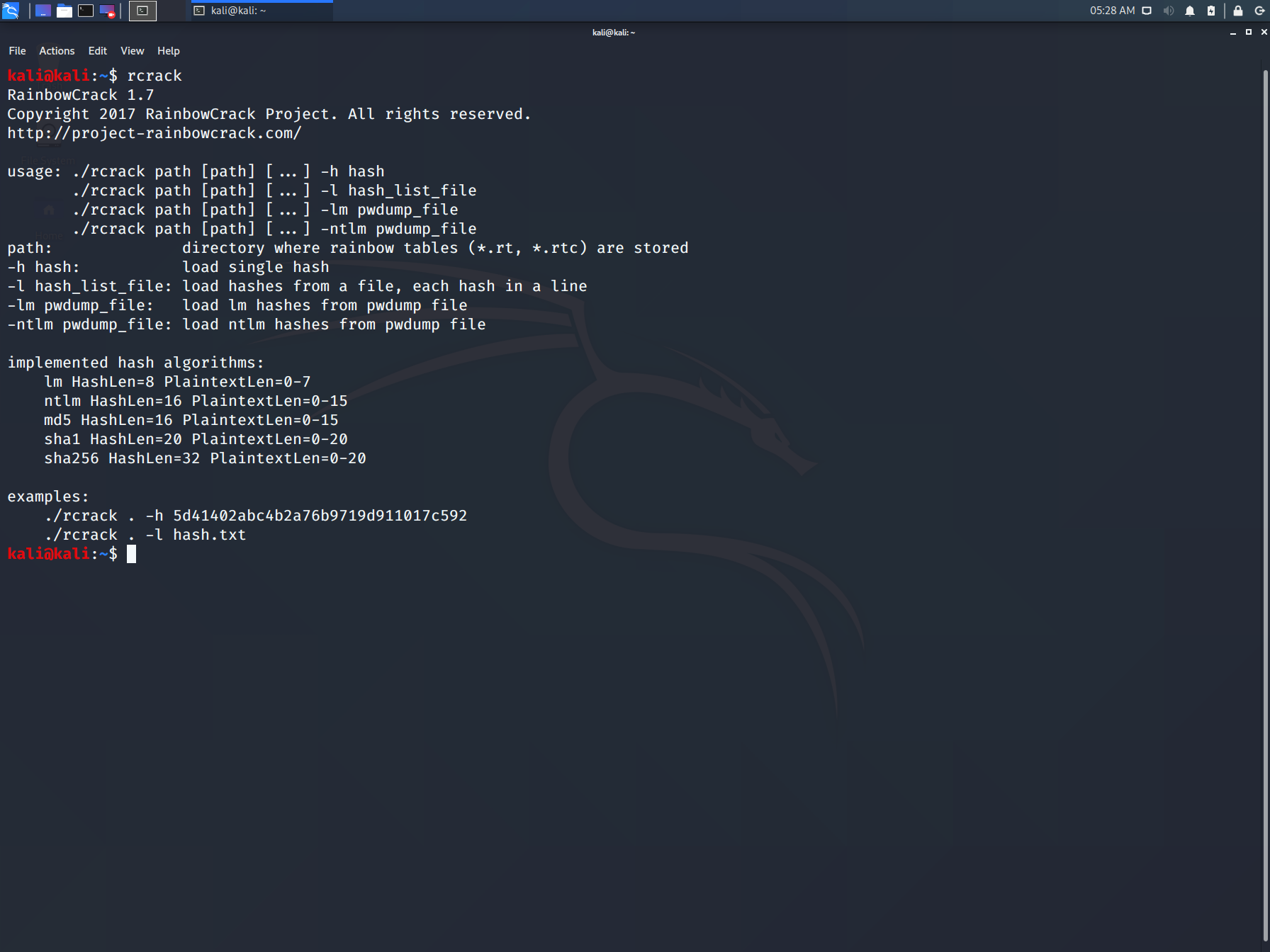
Rainbow crack is a tool that uses the time-memory trade-off technique in order to crack hashes of passwords. It uses rainbow tables in order to crack hashes of passwords. It doesn’t use the traditional brute force method for cracking passwords. It generates all the possible plaintexts and computes the hashes respectively. After that, it matches hash with the hashes of all the words in a wordlist. And when it finds the matching hashes, it results in the cracked password.
To use RainbowCrack, enter the following command in the terminal.
3. Burp Suite
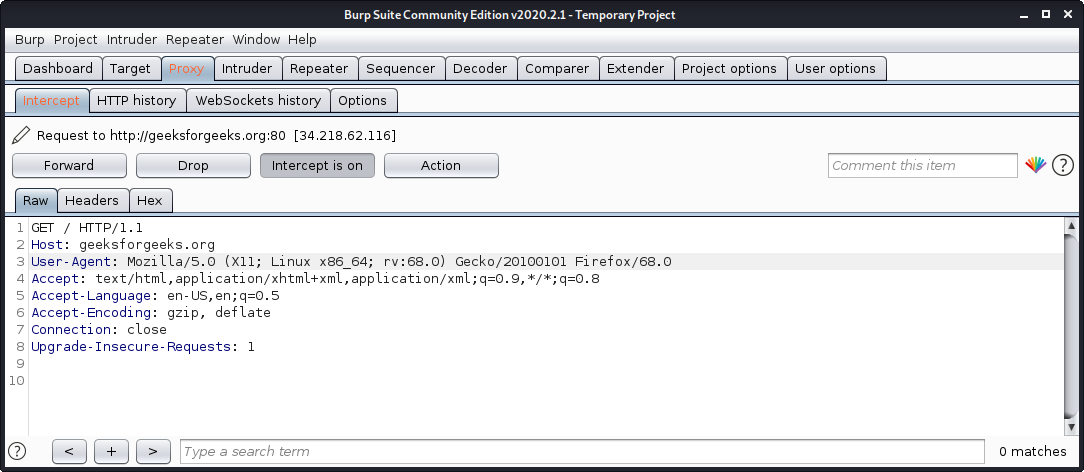
Burp Suite is one of the most popular web application security testing software. It is used as a proxy, so all the requests from the browser with the proxy pass through it. And as the request passes through the burp suite, it allows us to make changes to those requests as per our need which is good for testing vulnerabilities like XSS or SQLi or even any vulnerability related to the web. Kali Linux comes with burp suite community edition which is free but there is a paid edition of this tool known as burp suite professional which has a lot many functions as compared to burp suite community edition. It comes with an intruder tool that automates the process of password cracking through wordlists.
To use burp suite:
- Read this to learn how to setup burp suite.
- Open terminal and type “burpsuite” there.
- Go to the Proxy tab and turn the interceptor switch to on.
- Now visit any URL and it could be seen that the request is captured.
Maltego is a platform developed to convey and put forward a clear picture of the environment that an organization owns and operates. Maltego offers a unique perspective to both network and resource-based entities which is the aggregation of information delivered all over the internet – whether it’s the current configuration of a router poised on the edge of our network or any other information, Maltego can locate, aggregate and visualize this information. It offers the user with unprecedented information which is leverage and power.
Maltego’s Uses:
- It is used to exhibit the complexity and severity of single points of failure as well as trust relationships that exist currently within the scope of the infrastructure.
- It is used in the collection of information on all security-related work. It will save time and will allow us to work more accurately and in a smarter way.
- It aids us in thinking process by visually demonstrating interconnected links between searched items.
- It provides a much more powerful search, giving smarter results.
- It helps to discover “hidden” information.
To use Maltego: Go to applications menu and then select “maltego” tool to execute it.
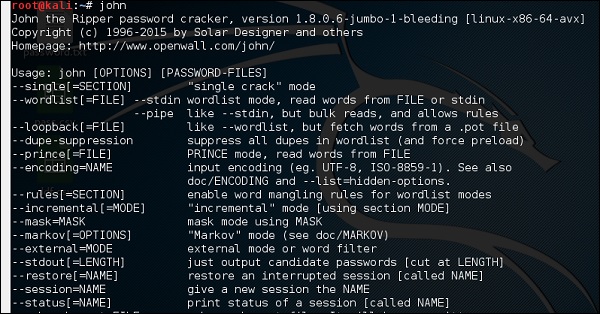
5. John the Ripper
John the Ripper is a great tool for cracking passwords using some famous brute for attacks like dictionary attack or custom wordlist attack etc. It is even used to crack the hashes or passwords for the zipped or compressed files and even locked files as well. It has many available options to crack hashes or passwords.
To use John the Ripper
- John the ripper comes pre-installed in Kali Linux.
- Just type “john” in the terminal to use the tool.
Kali Linux — Password Cracking Tools
In this chapter, we will learn about the important password cracking tools used in Kali Linux.
Hydra
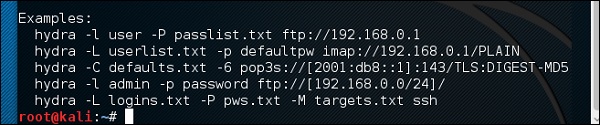
Hydra is a login cracker that supports many protocols to attack ( Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP).
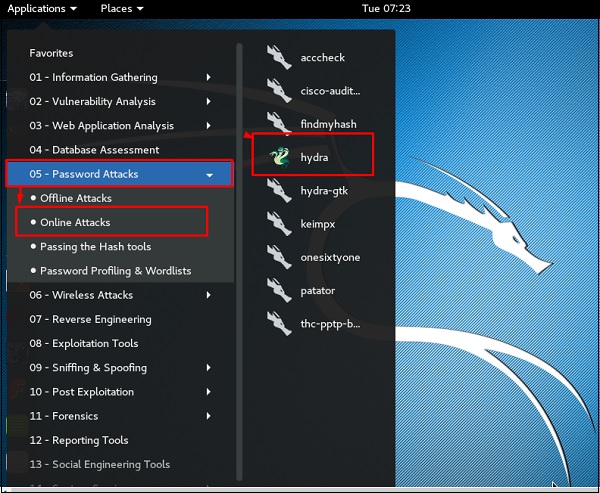
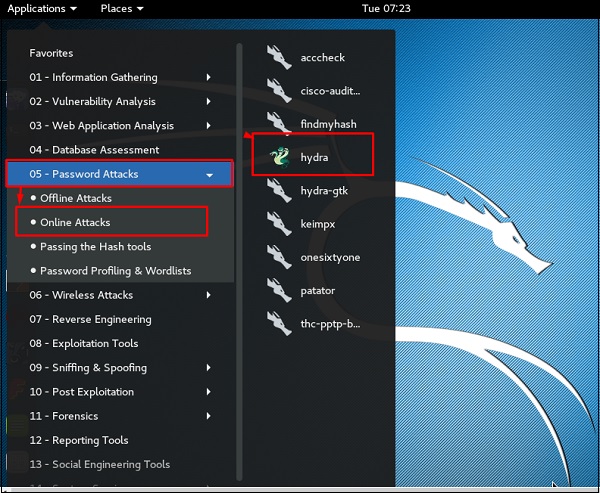
To open it, go to Applications → Password Attacks → Online Attacks → hydra.
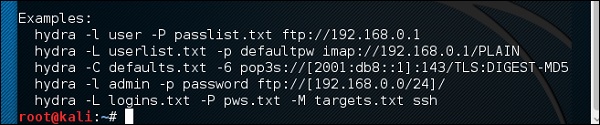
It will open the terminal console, as shown in the following screenshot.
In this case, we will brute force FTP service of metasploitable machine, which has IP 192.168.1.101
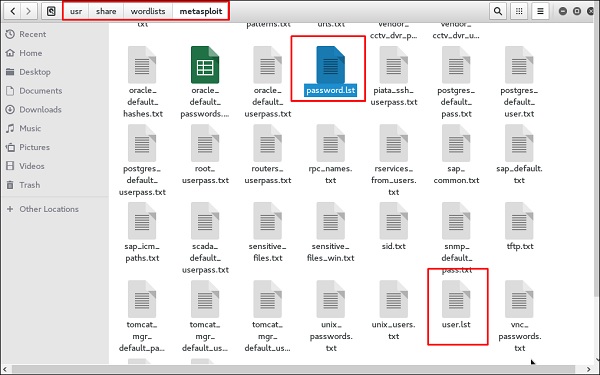
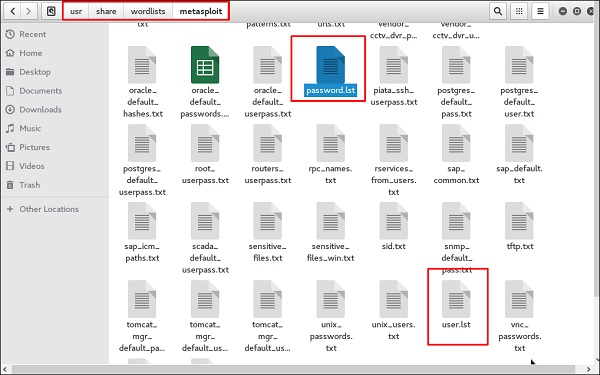
We have created in Kali a word list with extension ‘lst’ in the path usr\share\wordlist\metasploit.
The command will be as follows −
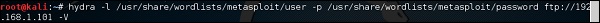
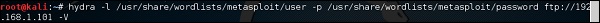
hydra -l /usr/share/wordlists/metasploit/user -P /usr/share/wordlists/metasploit/ passwords ftp://192.168.1.101 –V
where –V is the username and password while trying
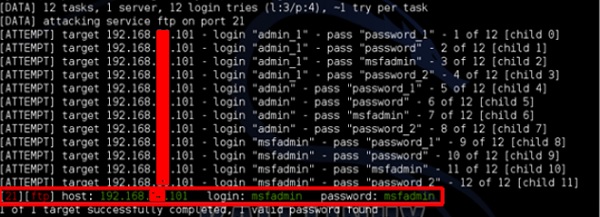
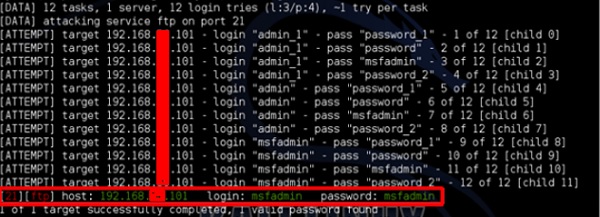
As shown in the following screenshot, the username and password are found which are msfadmin:msfadmin
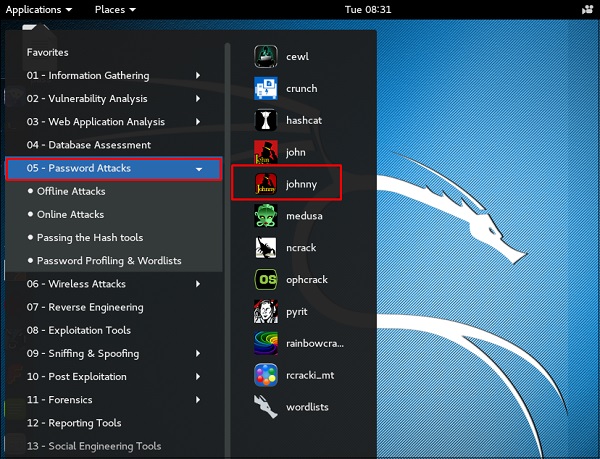
Johnny
Johnny is a GUI for the John the Ripper password cracking tool. Generally, it is used for weak passwords.
To open it, go to Applications → Password Attacks → johnny.
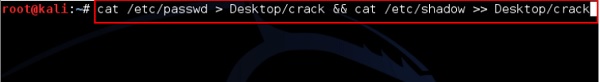
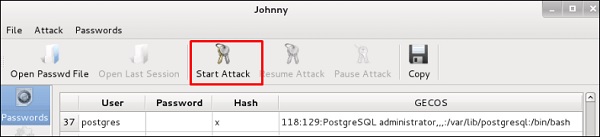
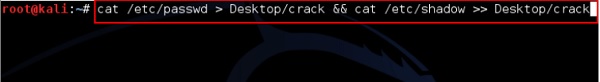
In this case, we will get the password of Kali machine with the following command and a file will be created on the desktop.
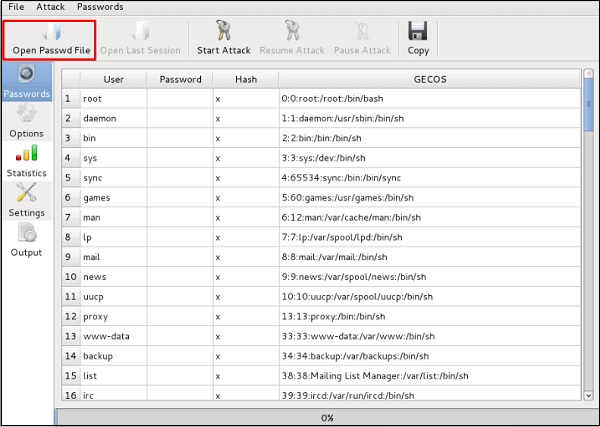
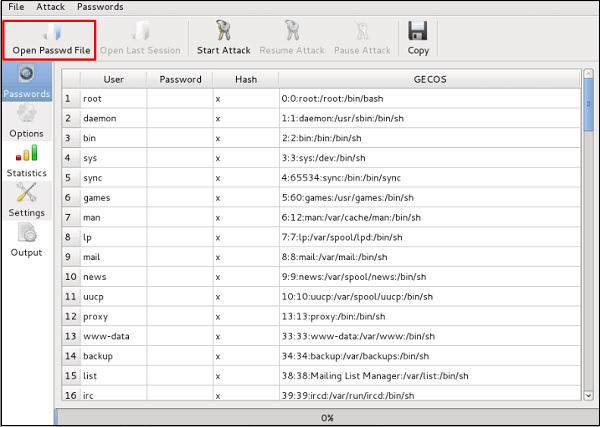
Click “Open Passwd File” → OK and all the files will be shown as in the following screenshot.
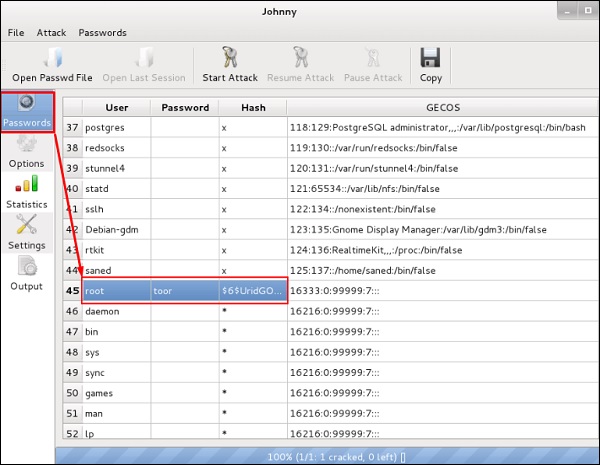
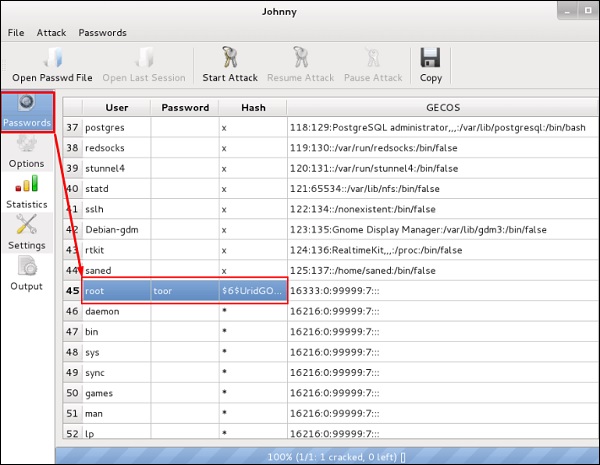
After the attack is complete, click the left panel at “Passwords” and the password will be unshaded.
John
john is a command line version of Johnny GUI. To start it, open the Terminal and type “john”.
In case of unshadowing the password, we need to write the following command −
root@kali:~# unshadow passwd shadow > unshadowed.txt
Rainbowcrack
The RainbowCrack software cracks hashes by rainbow table lookup. Rainbow tables are ordinary files stored on the hard disk. Generally, Rainbow tables are bought online or can be compiled with different tools.
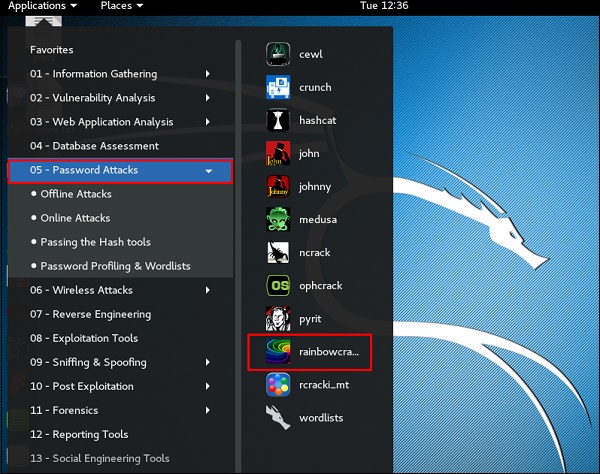
To open it, go to Applications → Password Attacks → click “rainbowcrack”.
The command to crack a hash password is −
rcrack path_to_rainbow_tables -f path_to_password_hash
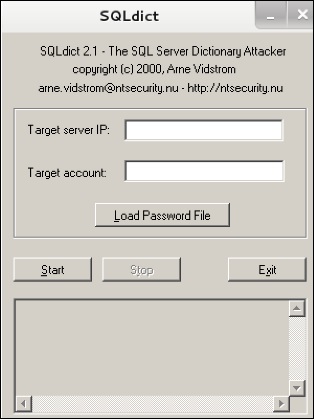
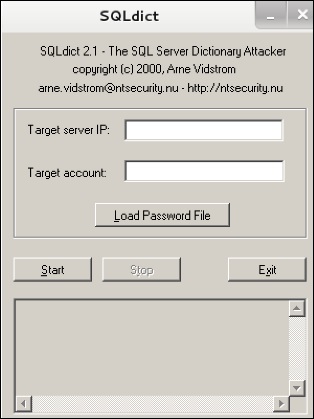
SQLdict
It is a dictionary attack tool for SQL server and is very easy and basic to be used. To open it, open the terminal and type “sqldict”. It will open the following view.
Under “Target IP Server”, enter the IP of the server holding the SQL. Under “Target Account”, enter the username. Then load the file with the password and click “start” until it finishes.
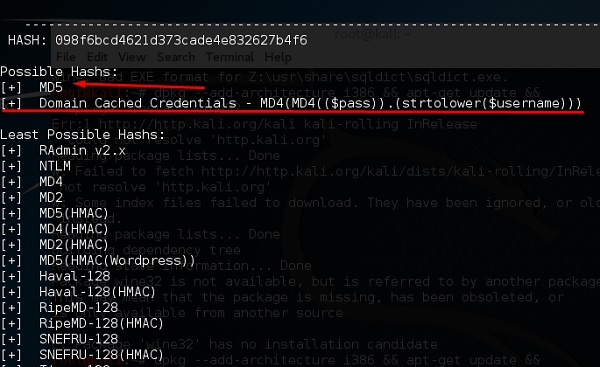
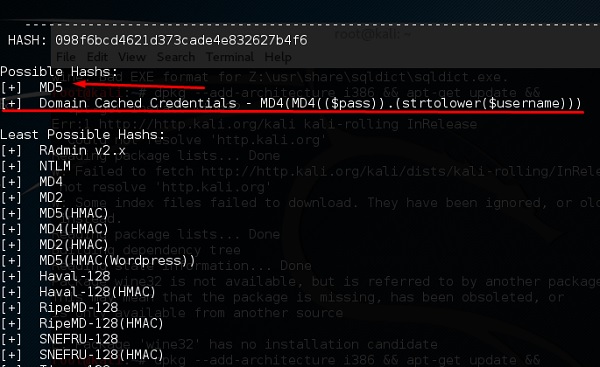
hash-identifier
It is a tool that is used to identify types of hashes, meaning what they are being used for. For example, if I have a HASH, it can tell me if it is a Linux or windows HASH.
The above screen shows that it can be a MD5 hash and it seems a Domain cached credential.
Kali linux hacking passwords
В этой статье мы разберем инструменты, которые доступны дистрибутиве Kali Linux.
Hydra
Hydra – это взломщик, который поддерживает множество протоколов: Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Чтобы запустить, перейдите в Applications → Password Attacks → Online Attacks → hydra.
Откроется консоль терминала, как показано на следующем снимке экрана.
Сейчас мы будем подбирать пароль для FTP на хосте с IP адресом 192.168.1.101
У нас есть список паролей в файле password.lst и файл с логинами в файле user.lst по пути \usr\share\wordlist\metasploit
Команда будет выглядеть следующим образом
# hydra -l /usr/share/wordlists/metasploit/user.lst -P /usr/share/wordlists/metasploit/passwords.lst ftp://192.168.1.101 –V
где –V – это выводить имя пользователя и пароль при попытке подбора (verbose)
Как показано на следующем скриншоте, имя пользователя и пароль найдены — это msfadmin:msfadmin
Если хотите, можно запустить “гидру” в GUI (графическая оболочка). Для этого выберите в меню xhydra-gtk или выполните команду
Johnny
Johnny – это графический интерфейс для инструмента взлома паролей John the Ripper. Как правило, он используется для слабых паролей.
Чтобы открыть его, перейдите в раздел Applications → Password Attacks → johnny.
Сейчас мы попробуем узнать пароль пользователя (в данном случае мы под root) на нашей машине с Kali с помощью следующей команды (файл будет создан на рабочем столе)
Нажмите “Open Passwd File” → OK, и все файлы будут показаны, как на следующем снимке экрана
Нажмите “Start Attack”. После завершения атаки нажмите в левой панели на кнопку “Passwords”, и пароль будет показан.
John
John – это версия Johnny GUI, но через командную строку (CLI). Для запуска откройте терминал и напишите команду
Если мы так же хотим узнать пароль нашего пользователя, но через командную строку, то введем команду
# unshadow passwd shadow > unshadowed.txt
В файле unshadowed.txt будут сохранены нужные нам данные.
Rainbowcrack
Программное обеспечение RainbowCrack ломает хеши по радужной таблице. Радужные таблицы — это обычные файлы, хранящиеся на жестком диске. Как правило, радужные таблицы покупаются или могут быть скомпилированы с помощью различных инструментов.
Чтобы открыть RainbowCrack, перейдите в раздел Applications → Password Attacks → click “rainbowcrack”.
Чтобы воспользоваться этой утилитой, выполните команду
# rcrack /home/user/rainbow_table.txt -f /home/user/pass_hash.txt
Где /home/user/rainbow_table.txt – это файл с радужной таблицей, а /home/user/pass_hash.txt – это файл с хешами паролей.
SQLdict
Это инструмент атаки по словарю для SQL сервера и он очень прост в использовании. Чтобы открыть его, откройте терминал и введите команду
В поле “Target IP Server” введите адрес SQL сервера. В поле “Target Account” введите имя пользователя. Затем выберите файл с паролями и нажмите “Start”. Ждите окончания подбора.
Hash-identifier
Это инструмент, который используется для определения типа хеша, чтобы понять, для чего они используются. Например, если у меня есть хеш, он может сказать мне, является ли он хешем ОС Linux или Windows.
На приведенном выше скриншоте показано, что указанный хеш может быть хешем MD5 и похож на кешированные учетные данные домена.
Вся информация представлена исключительно в образовательных целях. Помните, что все противоправные действия караются законом! 🙂