- Password Cracking with John the Ripper
- Table of contents
- What is Penetration testing?
- Types of Penetration testing
- Objectives
- Prerequisites
- How to install John the Ripper
- 1. Installing from the source
- 2. Installing from the package
- How John the Ripper cracks passwords
- Example cases of cracking passwords
- 1. Cracking a zip/rar password-protected file
- 2. Cracking a user account password in Kali Linux
- Conclusion
- How to use John, the ripper in Kali Linux
- Scenario #1: You Just Got A Password Hash
- Scenario #2: Password Protected Zip File
- Scenario #3: Increment Style Or Brute Force
- Johnny: The Gui Version
Password Cracking with John the Ripper
Most people often misunderstand the term hacking . From your perspective, you might think that hacking is the act of trying to gain access to certain network servers. Well, you might be right.
But, hacking is also an attempt to explore methods of breaching a defense mechanism and exploiting a weakness of a system to prevent unauthorized parties into the system by sealing the loopholes found in the system. This form of hacking is commonly known as penetration testing , also known as pen test.
Table of contents
What is Penetration testing?
This is an attempt to identify the level of a security system by trying to gain access into the system through identified vulnerabilities with permission from authorized personnel. On the other hand, trying to bypass the system’s security without permission is considered illegal and hence known as Red Hat hacking .
Types of Penetration testing
Penetration testing can be practiced in different ways.
Let’s take a look at some common ways a system’s vulnerability can be exploited.
- External Pen Test — This is a type of attack where a pen tester uses publicly available information to try to gain access into a system. Vulnerabilities exploited can grant access to the Pentester to remotely gain access to private data. Loopholes like these are identified and sealed before unwanted parties gain access.
- Internal Pen Test — This is a type of Pen testing where the attacker tries to gain access to a system by physically accessing the internal resources, implanting a malicious drive, or taking the role of an ill-intended employee that grants remote access to private data.
- Social Engineering — It is said that the weakest link in any security system is the human being. The pen tester can try to extract useful information from an employee by asking questions or deceiving the employee. This type of penetration testing is known as social engineering.
Having known what Penetration testing is, let’s see what password cracking is:
First, let’s understand how passwords are stored on your PC or any server.
When you enter a password into an account, the password is not saved in a raw format. The hashing algorithm converts the raw password into a series of characters (hash) that would take a lot of time and resources to decode.
This is where John the Ripper comes in. John the Ripper is a free, open-source password cracking and recovery security auditing tool available for most operating systems.
It has a bunch of passwords in both raw and hashed format. This bunch of passwords stored together is known as a password dictionary .
Now to crack the password, John the Ripper will identify all potential passwords in a hashed format. It will then match the hashed passwords with the initial hashed password and try to find a match.
If a match is found in the password hash, John the Ripper then displays the password in raw form as the cracked password. The process of matching the password hashes to locate a match is known as a dictionary attack .
Having known how the password cracking process takes place, let’s take a look at how John the Ripper executes commands in the crackig process.
Objectives
In this tutorial, we are going to learn how to spot weak passwords in a system. We will use John the Ripper , widely used by security specialists with the Kali Linux operating system.
Disclaimer: This tutorial is intended solely for academic purposes, and any action taken in response to any of the materials in this guide is entirely your own responsibility.
Prerequisites
Before you begin any hack or password cracking, you should have the following with you:
How to install John the Ripper
John the Ripper is usually pre-installed in Kali Linux but if you don’t have it yet, you can follow the steps below to install it on a Linux-based machine.
If you are facing any challenges with Kali Linux, I suggest you go through getting started with Kali Linux article.
There are numerous ways of installing John the Ripper on your machine but we will look at some of the basic ones:
1. Installing from the source
Open the terminal by simultaneously holding Ctrl+Alt+T and run the command below.
This creates a directory where we’ll store all our files.
Navigate to the src directory and clone John the Ripper repository as shown below.
git clone https://github.com/openwall/john.git This creates a directory named John . To make it active, we need to run the command below.
Navigate to the src directory where we’ll set and configure the compilation sources.
Run the make command to compile source code into executable programs and libraries. This might take some time depending on your machine and the resources allocated to it.
Lastly, run the make install command to install John the Ripper.
Run the commands below to see if the installation was successful.
2. Installing from the package
You can also install John the Ripper by running the command below:
How John the Ripper cracks passwords
During the cracking process, John the Ripper uses a rainbow table approach where it takes words from an in-built dictionary that comes with it.
It then compiles the variations of that dictionary and compares the hashed password to what is in the password file trying to find a match. This is repeated until a match is found.
Example cases of cracking passwords
You will need to run different commands depending on the type of target you are exploiting.
Let’s look at some instances we might come across when cracking passwords using John the Ripper.
1. Cracking a zip/rar password-protected file
Cracking a zip or rar file password is done using the same approach.
First, we will need to access the hash of the password we are going to crack. Note the name of your zip file as you will be required to state it in the rest of the commands.
To access the password hash, navigate to the location of your zip password-protected file and run the command below in the terminal:
You can export the output to a text document to save the password hash since we are going to use it later.
zip2john Test.zip > hash.txt To begin the attack on your zip file, run the command below:
In the command above, we have specified the format of the target file.
The password cracking process is initiated. This is where the strength of the password comes in. The stronger the password, the more the time taken to perform an attack.
After a successful attack, the password will be displayed on the terminal.
2. Cracking a user account password in Kali Linux
Moving on, we will learn how to crack another user’s account password using John the Ripper.
First, let’s create another user account that we are going to crack its password. Run the command below in the terminal.
We have created a user account named James .
Now, let’s set the password for the account.
Run the command below to crack James’ password.
John the Ripper will first identify the hash method and display it on the terminal. It then decodes the password hash into a raw password and displays it as well.
Conclusion
In this tutorial, we have learned the following:
- Installing John the Ripper in a Kali Linux machine.
- Password cracking of a zip/rar password-protected file.
- Creating and cracking a secondary user account’s password on a Kali Linux machine.
Peer Review Contributions by: Eric Gacoki
How to use John, the ripper in Kali Linux
John the Ripper is an Open Source cross-platform package that is typically used for password security auditing and password recovery. In this tutorial, we’ll be learning how to use John the Ripper in Kali Linux.
On Kali Linux, John the Ripper is preinstalled, so there’s no need to install anything! Just pick up the package, and take it for a ride.
Scenario #1: You Just Got A Password Hash
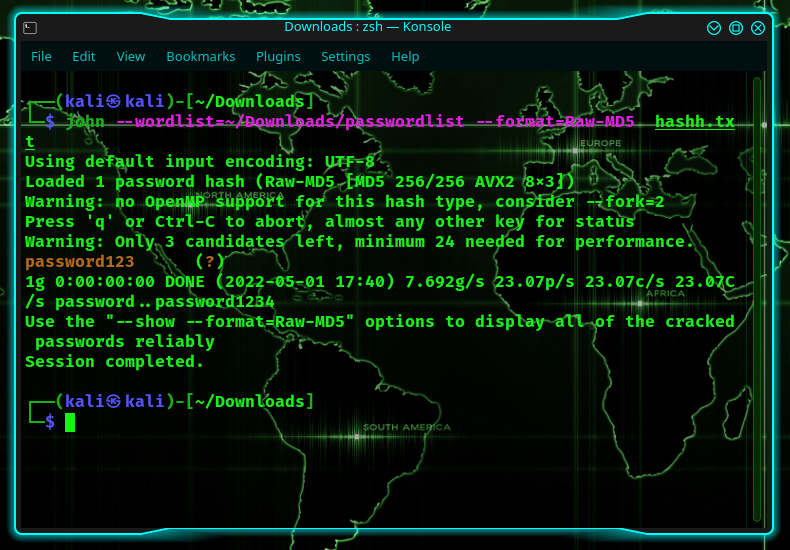
So, let’s assume that you were just handed a hash, an MD5 hash, to be specific. In real-life situations, you’d obtain these by scavenging a computer. In my case, I’m going to use the word password123:
To resolve the password, you’d use the simplest usage of the john the ripper code:
Typically, John the Ripper automatically detects the hash type. But you can augment this as much as you want! So let’s say you want to add your own word list and specify the format, then you’d write:
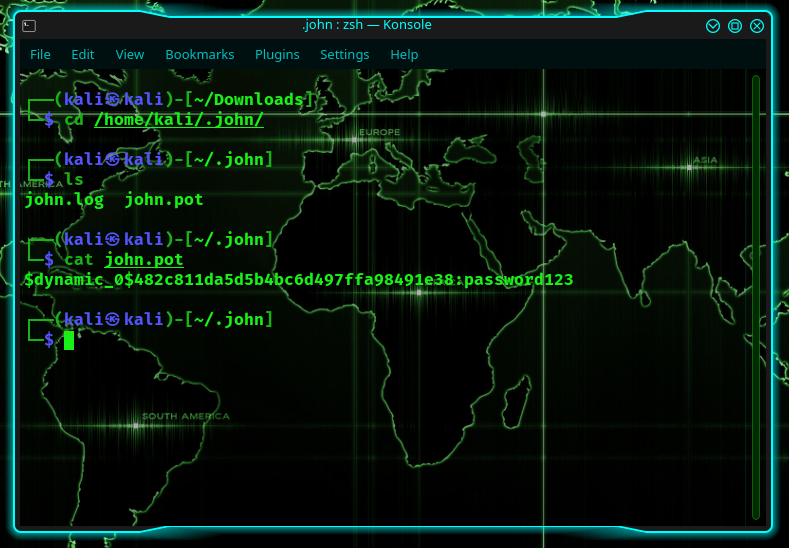
So, the first time you run the latter, it will show the password on the screen, after which point, it will save it into a file called john.pot. In my case, the folder john.pot was located at /home/kali/.john/john.pot.
Scenario #2: Password Protected Zip File
Now let’s pretend there is a Zip file with a password lock. So at some point previously, you created a zip file that is password protected. For that, you’ll need to install zip:
Then to create the zip file:
Ex: zip —password password123 linuxhint.zip linuxhint.txt
(Here, the word password123 is the actual password protecting the zip file.)
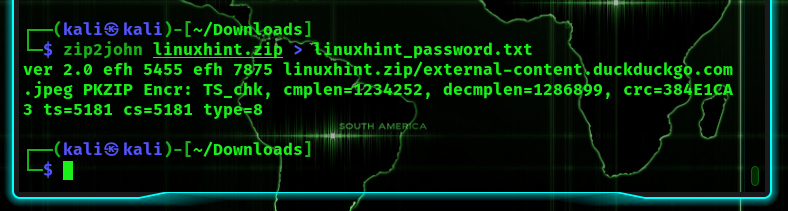
Now, 6 months later, you’ve forgotten the password. What can you do? Well, use John the Ripper, but before we can, we first need to convert the zip to john.
To do so, we’ll use the zip2john command:
The hash itself is located between the two dollar signs.
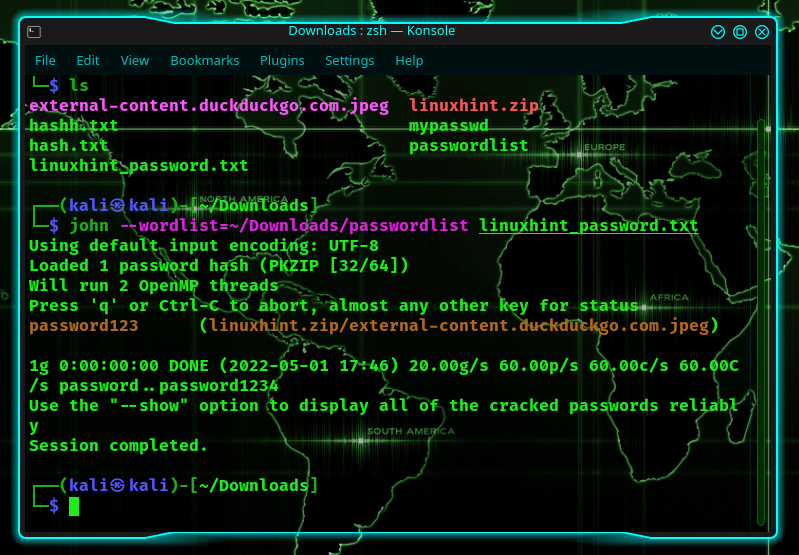
John the Ripper can retrieve the password using one of two methods: the dictionary attack or the bruteforce attack. A file with a list of potential passwords is compared to the hash at hand in a dictionary attack. If a match is found, it will chuck it out. On the other hand, if a password is not found, you can use a different password file or use a different method.
Here, what we did was crack a zip file, but it doesn’t have to be a zip file! It can be almost anything. Just remember that you have to, in such cases, use the 2john. For example, if you were cracking Wifi, you’d use Aircrack-ng and obtain a cap file. Once you’ve obtained the cap file, you’d have to convert the cap file to an hccap file. Once you have a hccap file, use the hccap2john to convert it to the john format, which will yield results on John the Ripper.
You can find more of the 2john commands using:
Scenario #3: Increment Style Or Brute Force
The most powerful of all the methods available is the bruteforce method because it will check every possible combination out there! But this also means that it’s unlikely to ever end unless the passwords are reasonably simple.
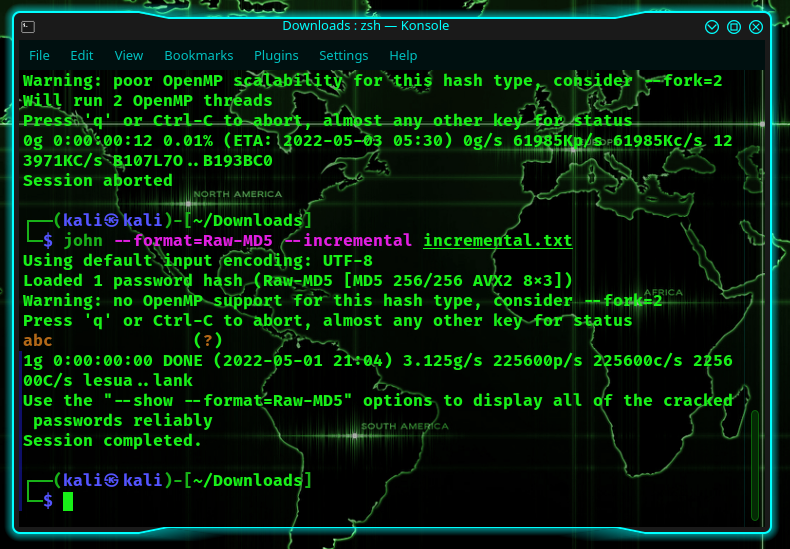
For example, I will choose a 3 character password in the MD5 format: abc. I’m doing this so that I don’t have to spend hours waiting for it to detect it.
The simplest way of doing this is to type:
Alternatively, you could have also written:
As you can see, I found it in less than a second, and I didn’t even have to supply it with a dictionary.
Next, we’re going to mess around with the configuration file located at /etc/john/john.conf.
In the /etc/john/john.conf file, you will find a section on incremental modes. Here, you can add more if you want, but first, let’s try using one of them.
There’s one in /etc/john/john.conf that is as follows:
File = $JOHN / digits.chr
MinLen = 1
MaxLen = 20
CharCount = 10
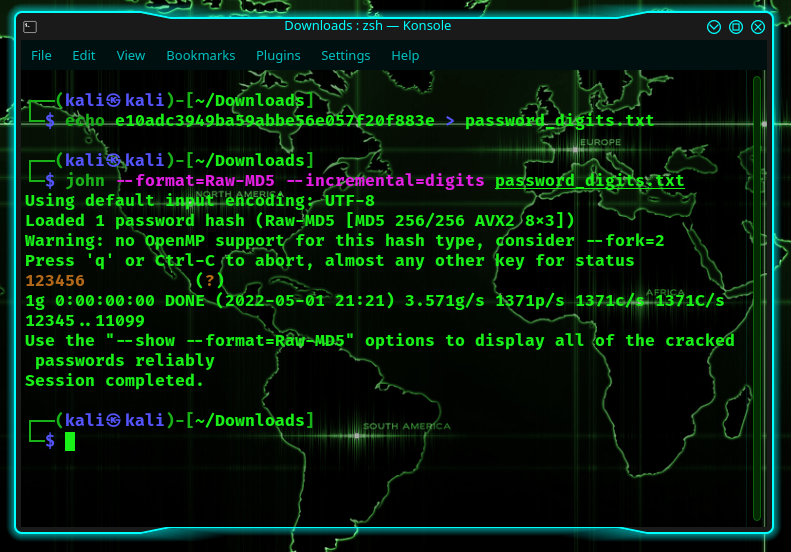
Here, let’s recreate an MD5 hash for the password 123456.
Now, let’s use the incremental mode:
The latter will search all possible combinations of digits. And since it was only a 6-digit password, it cracked it in less than one second.
However, you can add your own files in there and create your own incremental files as well. You can create rules, etc… It gets heavy!
Johnny: The Gui Version
Now for those who prefer a GUI version over a CLI version, there’s Johnny. To install johnny:
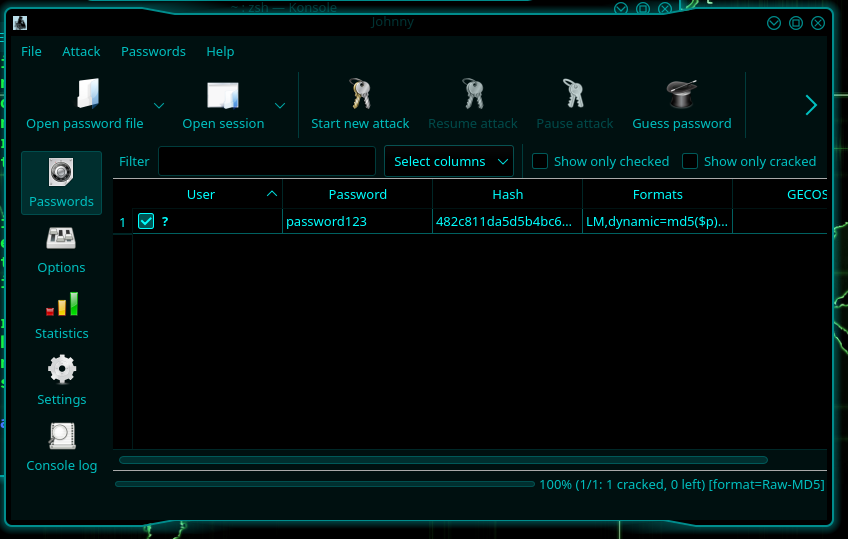
Under the File tab, you should find two options – open the password file or open other file format. For demonstration purposes, we will use the first – open password file. I will open the hash.txt file that holds a password in MD5.
In the options section, you can choose the attack mode you want. I will choose the word list and the type of hash (at the top). Then I’m going to give it a password file.
Then click on “Start new attack”.
Simple and easy! In the same way, you can choose the attack mode. So if you want the incremental mode, then set it up and watch it do its thing.
John the Ripper is a very powerful tool. In fact, it is very commonly used, so much so that it comes preinstalled on Kali Linux! John the Ripper is primarily used for password recovery, but one can always verify whether the passwords one’s chosen are safe or not by trying to break them as well. All in all, it’s a fantastic tool that takes a while to learn and master, but it’s definitely worth the effort.