- Kali linux nethunter android
- 1. NetHunter support and pre-built images
- 2. Putting your device in “Developer Mode”
- 3. — 5. Unlocking, rooting, and installing a custom recovery on your android device
- 6. Flashing Universal DM-Verity & ForceEncrypt Disabler
- 7. — 9. Installing the NetHunter Image
- Kali linux nethunter android
- Prerequisite:
- Installation:
- Usage:
- NetHunter Editions:
- Tips:
- Kali linux nethunter android
- Packages
Kali linux nethunter android
Installing NetHunter requires the following steps:
1. NetHunter support and pre-built images
You can confirm that your device and Android version is supported via our gitlab live reports: List of quarterly published NetHunter images NetHunter kernel statistics NetHunter kernel table with
The NetHunter team builds and publishes images for a selected list of devices, on the official NetHunter download page.
If you devices is supported by NetHunter but not available as a pre-build image, you can easily build your own image by following the steps in our “Building NetHunter” documentation
2. Putting your device in “Developer Mode”
Before the installation begins, you must enable Developer mode on your device. This is done by navigating to Settings -> About and tapping on the Build number field 7 times until you receive the notification that developer mode has been enabled. Go back to the main settings page and you will have a new section titled Developer options. Tap on the new Developer options section and enable both the Advanced Reboot and Android Debugging options.
3. — 5. Unlocking, rooting, and installing a custom recovery on your android device
NetHunter supports over 60 different devices running Android versions from Kitkat though to Android Q. Whilst we have standardised the NetHunter installation procedure, the steps to unlock, root, and install a custom recovery varies from device to device and even differs between Android versions. The preferred custom recovery for NetHunter is TWRP. The preferred software to root the device for NetHunter is Magisk. Please refer to the appropriate guide to unlock, root, and install a custom recovery on your device from your preferred internet resource, such as the XDA Developers Forum
6. Flashing Universal DM-Verity & ForceEncrypt Disabler
IMPORTANT NOTE for Android 9, 10, & 11 users: Please ensure that you flash the Universal DM-Verity, ForceEncrypt Disabler and format the data partition prior to installing NetHunter. Magisk does not support user context changes on encrypted data partitions, which leads to errors when connecting to the Kali rootfs via ssh (i.e. “Required key not available”) if the data partition is encrypted.
7. — 9. Installing the NetHunter Image
Now that your Android phone is ready, transfer the NetHunter image to it, reboot in recovery mode, and flash the zip on your phone. Once done, reboot and launch the NetHunter app to complete the setup!
IMPORTANT NOTE for Android 10 & 11 users: Please update the NetHunter app from the NetHunter store after flashing NetHunter. Android 10 introduced “scoped storage” restrictions which prevents NetHunter from using the storage location we traditionally used to save configuration files. We are in the process of moving the location and implementing an import/export function but updating the app after flashing NetHunter provides a workaround that allows us to continue accessing the current storage location until the new features are implemented.
Updated on: 2023-Mar-06
Author: re4son
Kali linux nethunter android
Install Kali NetHunter on any stock, unrooted Android device without voiding the warranty.
Prerequisite:
Android Device (Stock unmodified device, no root or custom recovery required)
Installation:
- Install the NetHunter-Store app from store.nethunter.com
- From the NetHunter Store, install Termux, NetHunter-KeX client, and Hacker’s keyboardNote:The button “install” may not change to “installed” in the store client after installation — just ignore it.Starting termux for the first time may seem stuck while displaying “installing” on some devices — just hit enter.
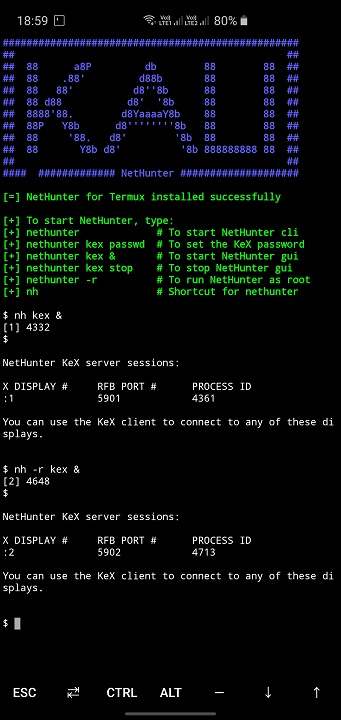
- Open Termux and type:
[email protected]:~$ termux-setup-storage [email protected]:~$ pkg install wget [email protected]:~$ wget -O install-nethunter-termux https://offs.ec/2MceZWr [email protected]:~$ chmod +x install-nethunter-termux [email protected]:~$ ./install-nethunter-termux Usage:
Open Termux and type one of the following:
| Command | To |
|---|---|
| nethunter | start Kali NetHunter command line interface |
| nethunter kex passwd | configure the KeX password (only needed before 1st use) |
| nethunter kex & | start Kali NetHunter Desktop Experience user sessions |
| nethunter kex stop | stop Kali NetHunter Desktop Experience |
| nethunter | run in NetHunter environment |
| nethunter -r | start Kali NetHunter cli as root |
| nethunter -r kex passwd | configure the KeX password for root |
| nethunter -r kex & | start Kali NetHunter Desktop Experience as root |
| nethunter -r kex stop | stop Kali NetHunter Desktop Experience root sessions |
| nethunter -r kex kill | Kill all KeX sessions |
| nethunter -r | run in NetHunter environment as root |
Note: The command nethunter can be abbreviated to nh . Tip: If you run kex in the background ( & ) without having set a password, bring it back to the foreground first when prompted to enter the password, i.e. via fg — you can later send it to the background again via Ctrl + z and bg
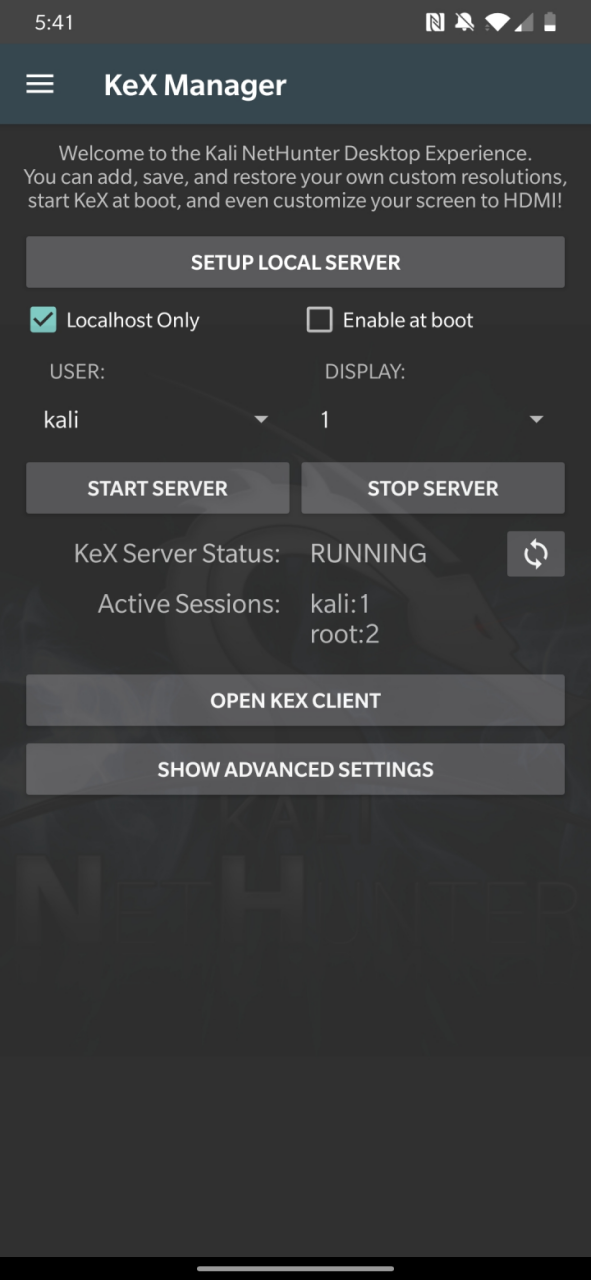
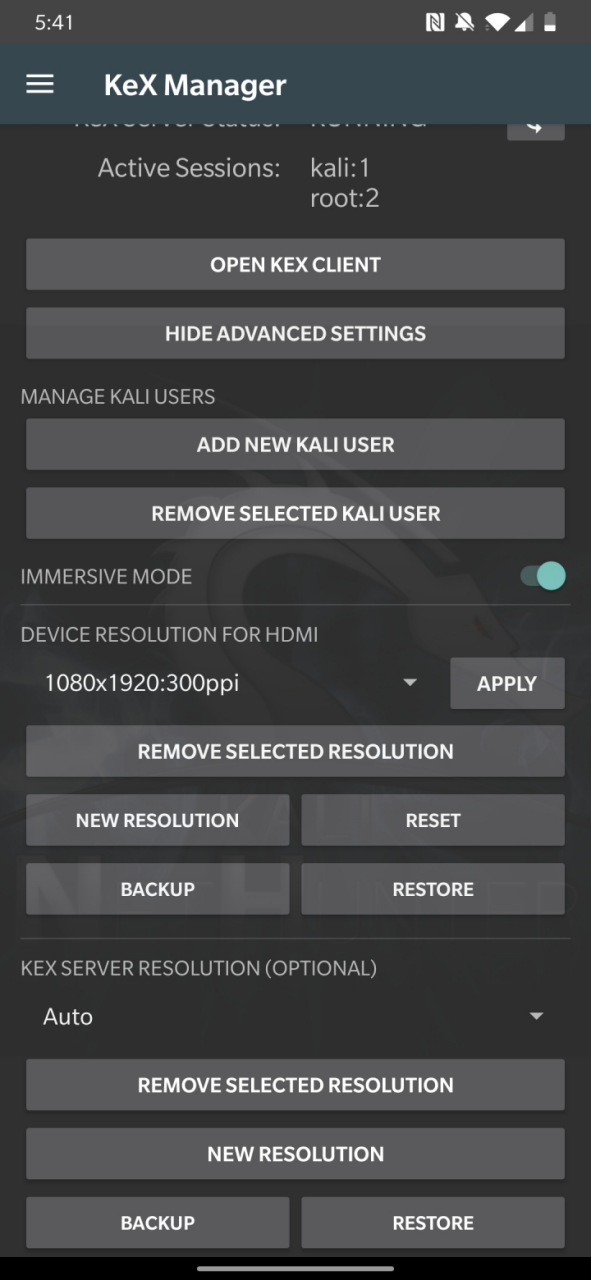
To use KeX, start the KeX client, enter your password and click connect Tip: For a better viewing experience, enter a custom resolution under “Advanced Settings” in the KeX Client
NetHunter Editions:
Please refer to this table for a comparison of the different NetHunter editions.
Tips:
- Run sudo apt update && sudo apt full-upgrade -y first thing after installation to update Kali. If you have plenty of storage space available you might want to run sudo apt install -y kali-linux-default as well.
- All of the penetration testing tools should work but some might have restrictions, e.g. metasploit works but doesn’t have database support. If you discover any tools that don’t work, please post it in our forums.
- Some utilities like “top” won’t run on unrooted phones.
- Non-root users still have root access in the chroot. That’s a proot thing. Just be aware of that.
- Galaxy phone’s may prevent non-root users from using sudo. Just use “su -c” instead.
- Perform regular backups of your rootfs by stopping all nethunter sessions and typing the following in a termux session: tar -cJf kali-arm64.tar.xz kali-arm64 && mv kali-arm64.tar.xz storage/downloads That will put the backup in your Android download folder. Note: on older devices, change “arm64” to “armhf”
- Please join us in our forums to exchange tips and ideas and be part of a community that strives to make NetHunter even better.
Updated on: 2023-Mar-06
Author: re4son
Kali linux nethunter android
2021.3
——
* Fix race condition at initial startup — @Re4son
2021.2
——
* Improved BTFragment — @CaliBerrr
* killkali: Try lazy unmount first — @CaliBerrr
* Improved chroot manager — @CaliBerrr
* Fixed space in browsed inject sound — @yesimxev
* Fixed SYSTEM mount for SAR devices — @yesimxev
* Echo fixes for zsh — @yesimxev
* Clean ups, fixed convert files typo — @yesimxev
2021.1
——
* Update build info and boot me
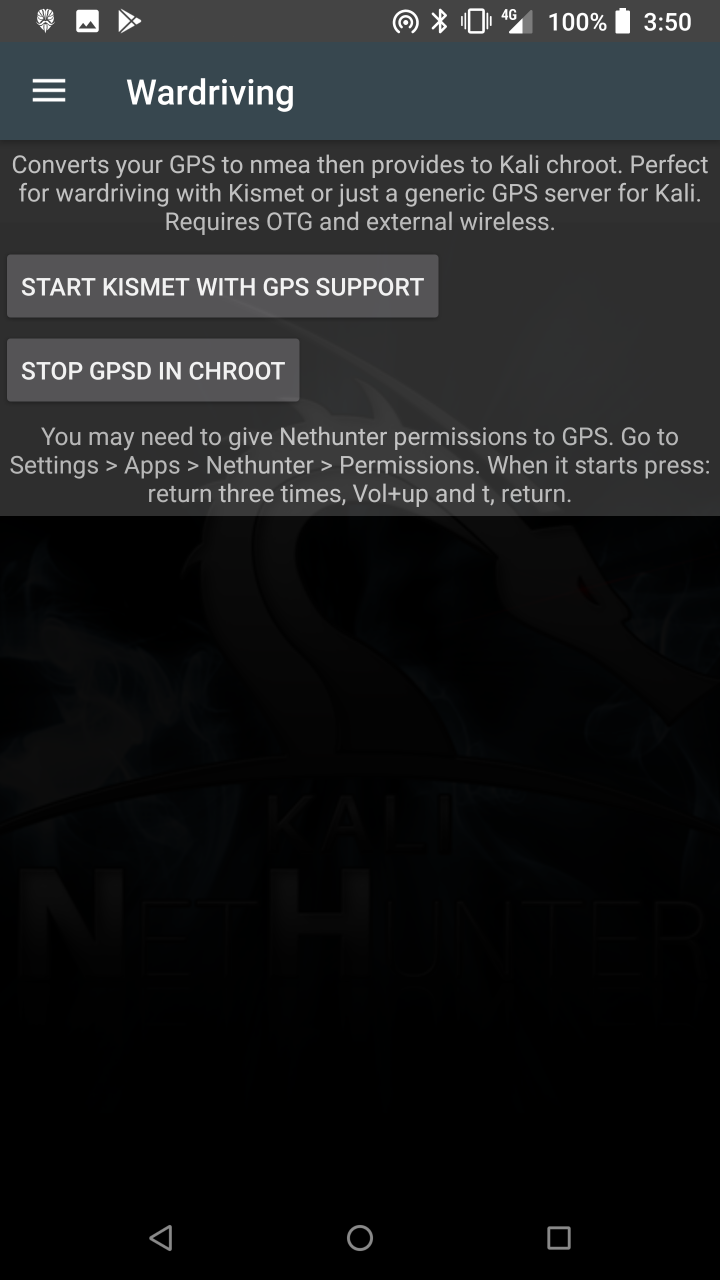
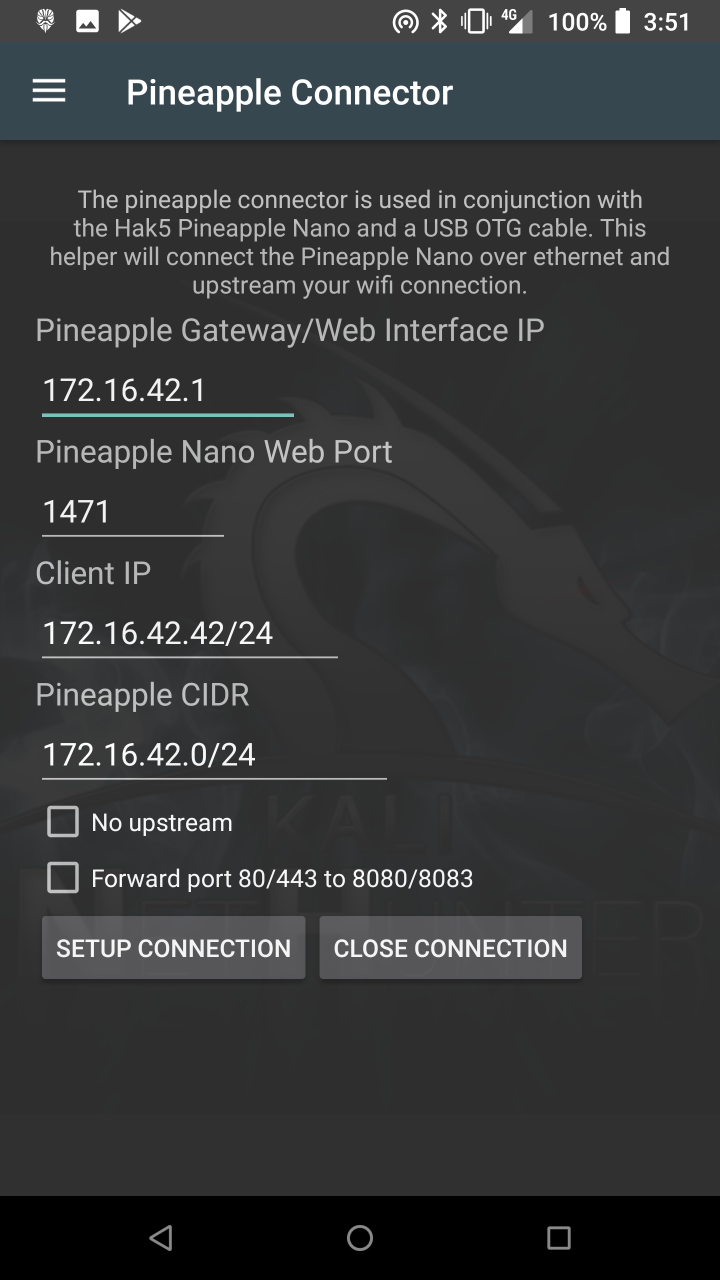
The Kali NetHunter is an Android ROM overlay that includes a robust Mobile Penetration Testing Platform. The overlay includes a custom kernel, a Kali Linux chroot, and an accompanying Android application, which allows for easier interaction with various security tools and attacks. Beyond the penetration testing tools arsenal within Kali Linux, NetHunter also supports several additional classes, such as HID Keyboard Attacks, BadUSB attacks, Evil AP MANA attacks, and much more. For more information about the moving parts that make up NetHunter, check out our NetHunter Components page. NetHunter is an open-source project developed by Offensive Security and the community.
# Kali NetHunter Application
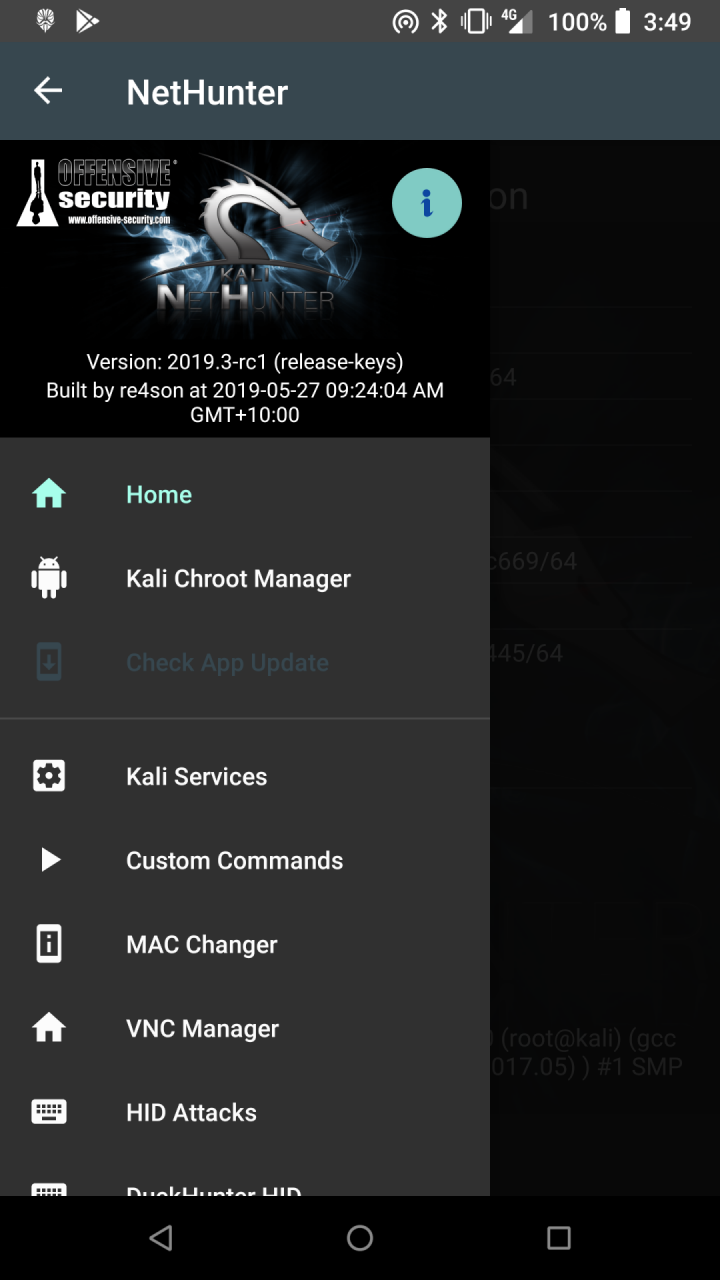
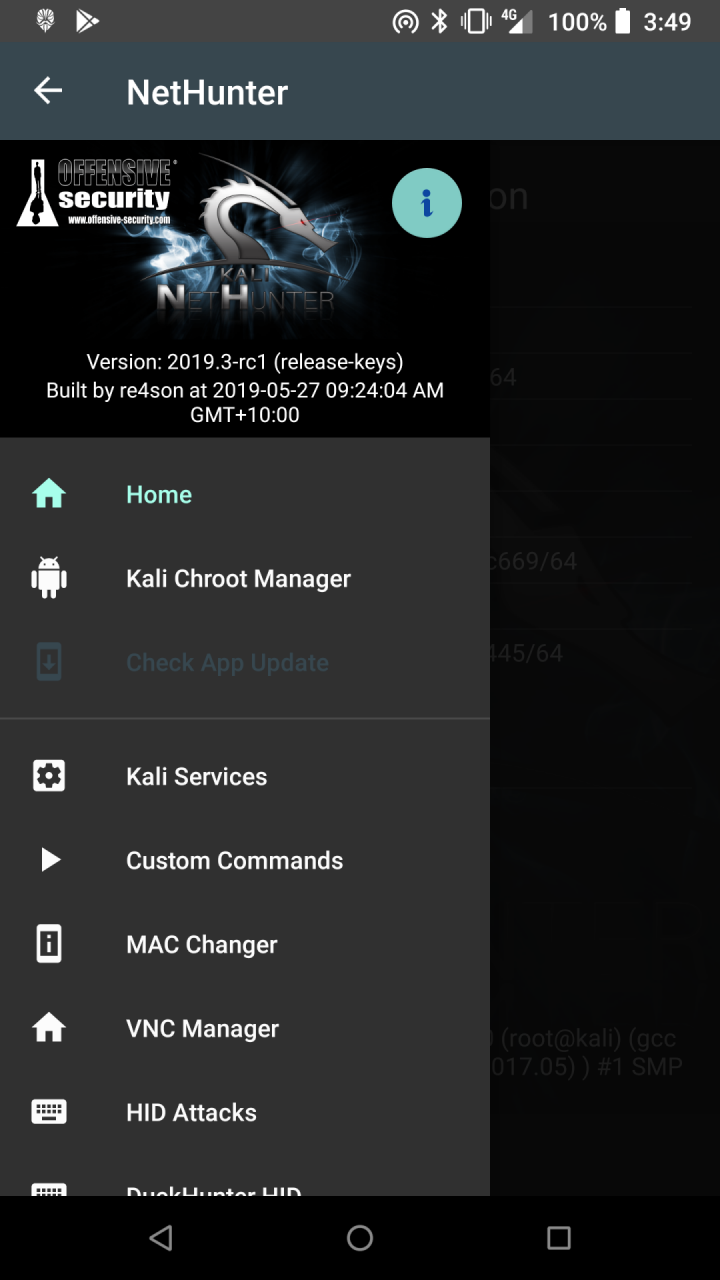
* Home Screen — General information panel, network interfaces and HID device status.
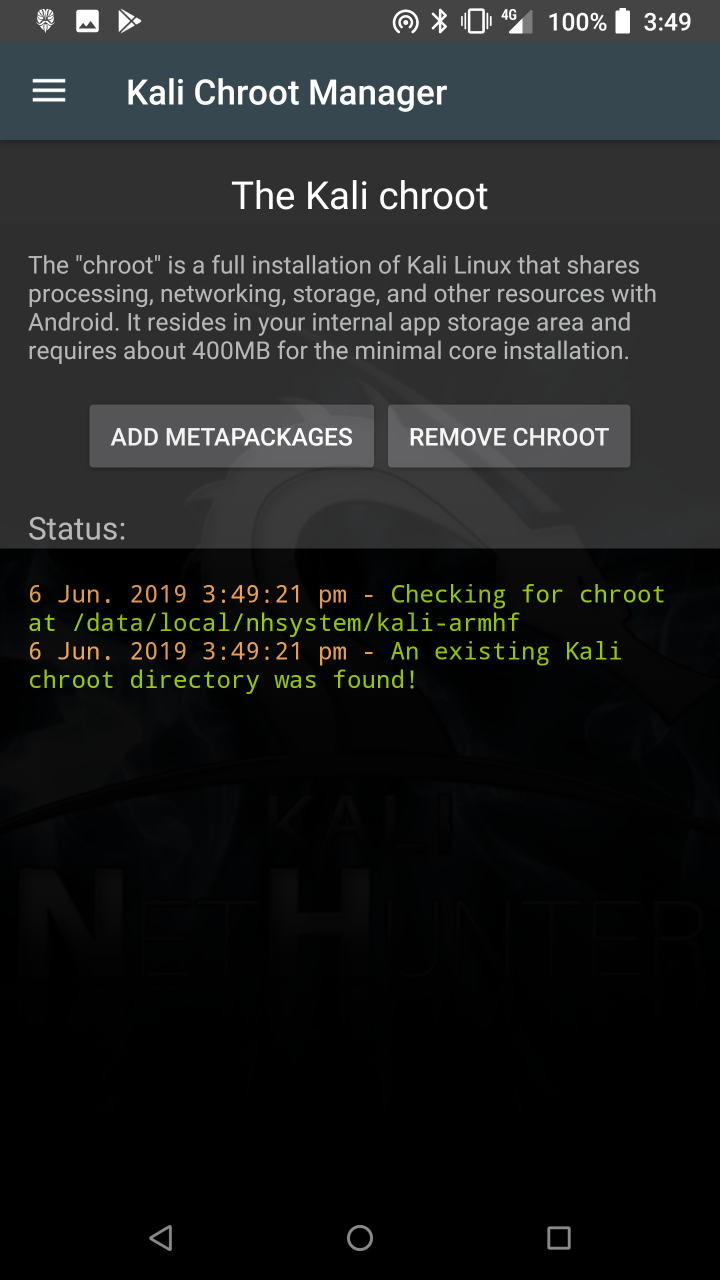
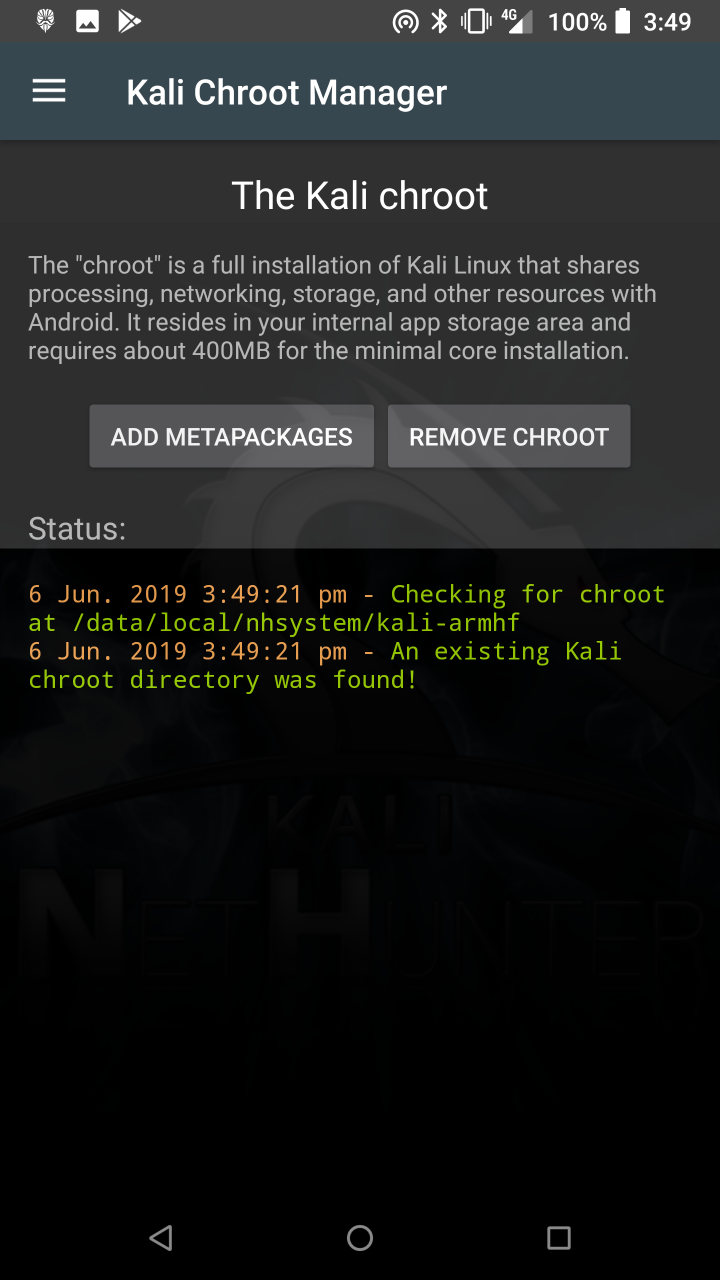
* Kali Chroot Manager — For managing chroot metapackage installations.
* Check App Update — For checking Kali NetHunter Android App updates.
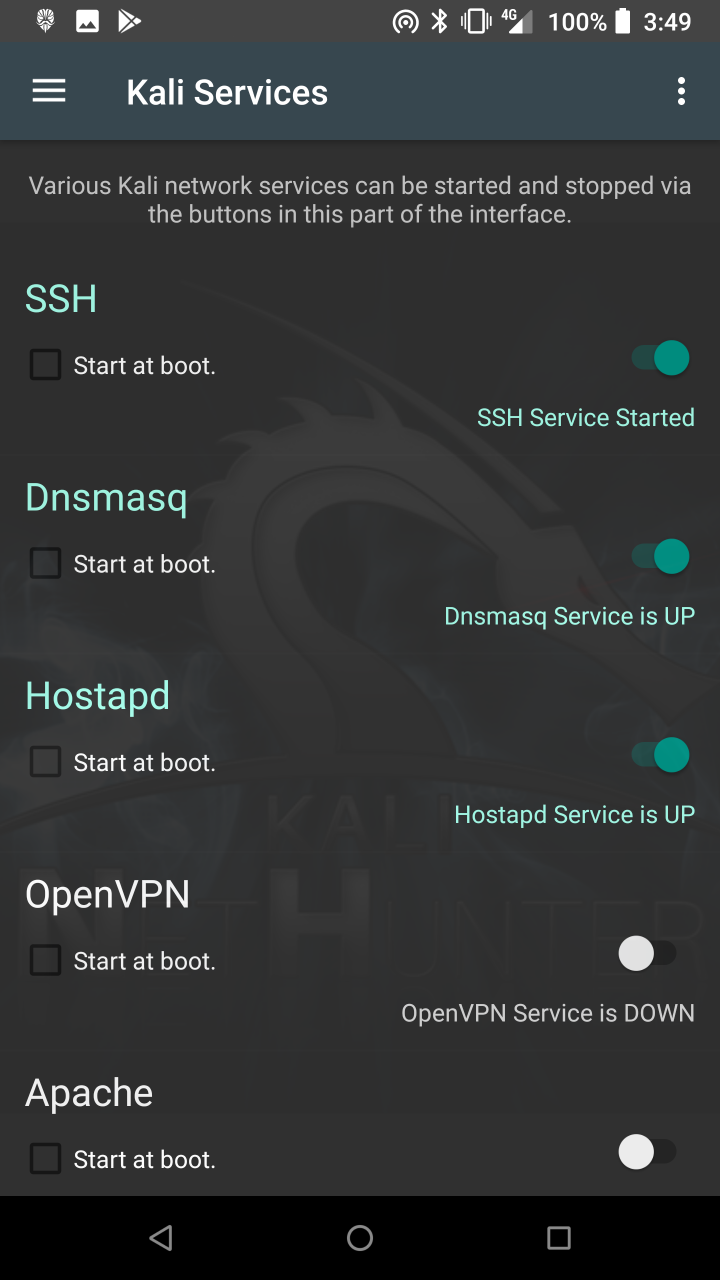
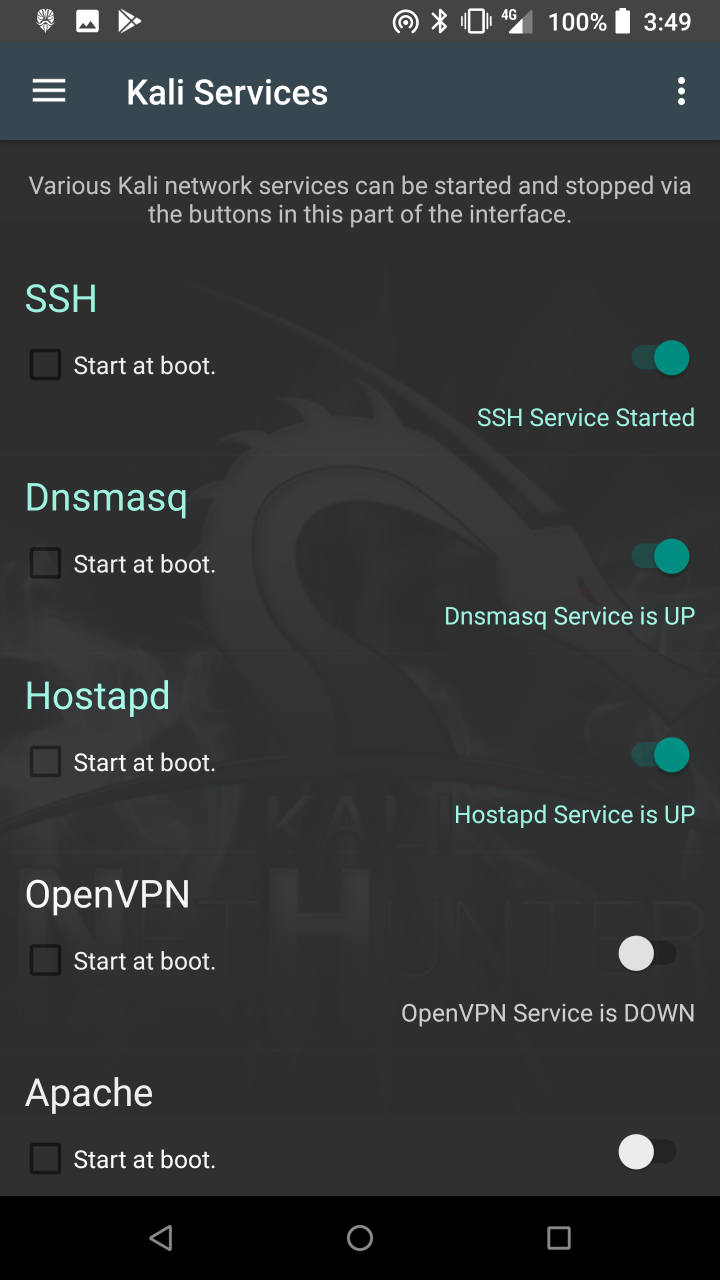
* Kali Services — Start / stop various chrooted services. Enable or disable them at boot time.
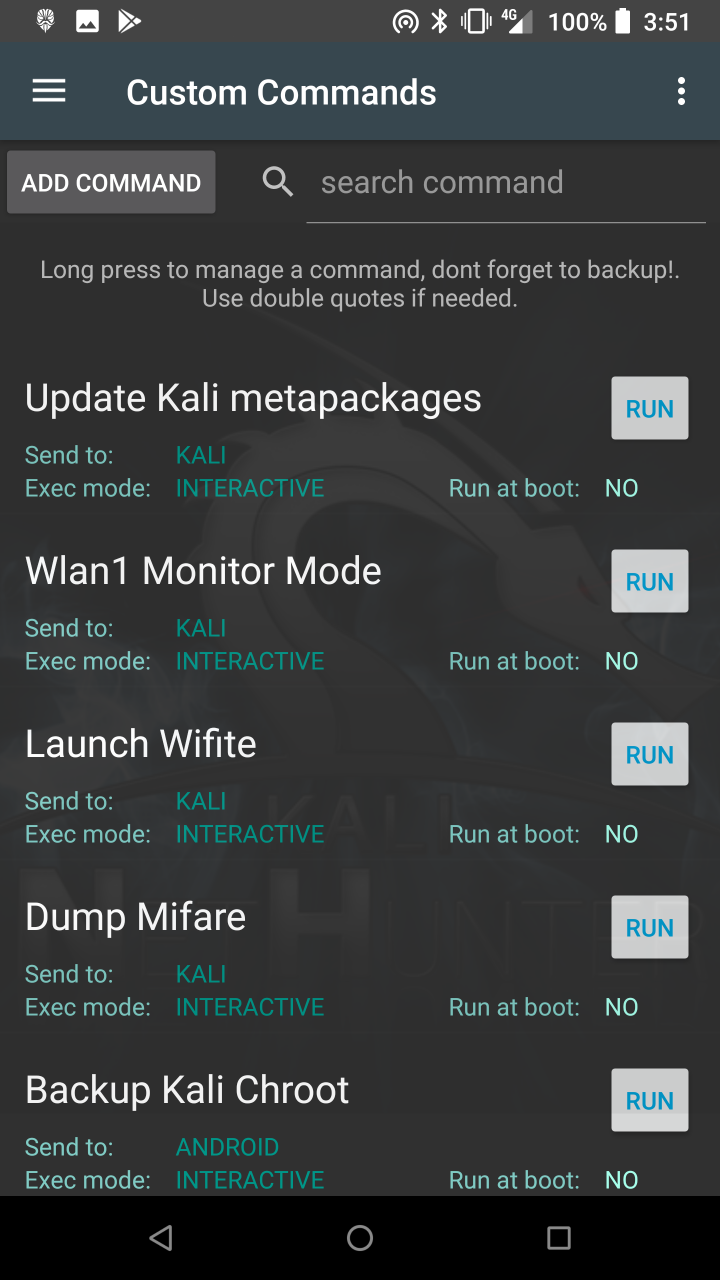
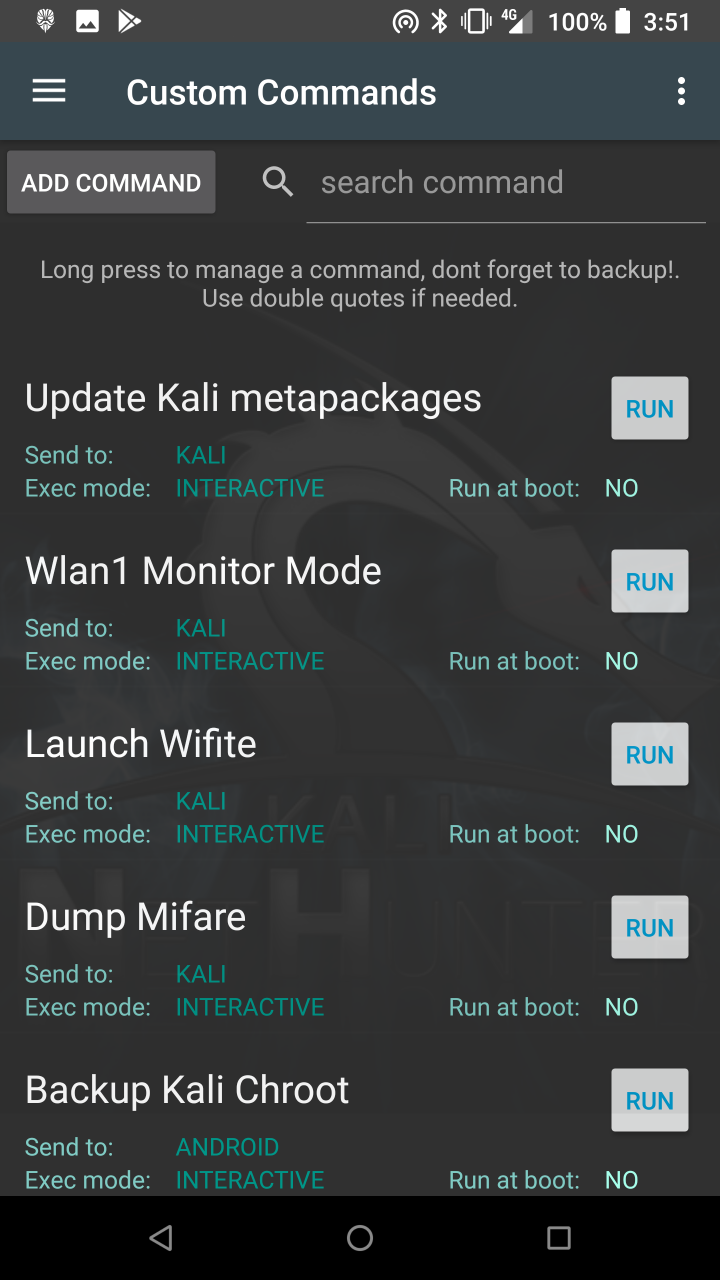
* Custom Commands — Add your own custom commands and functions to the launcher.
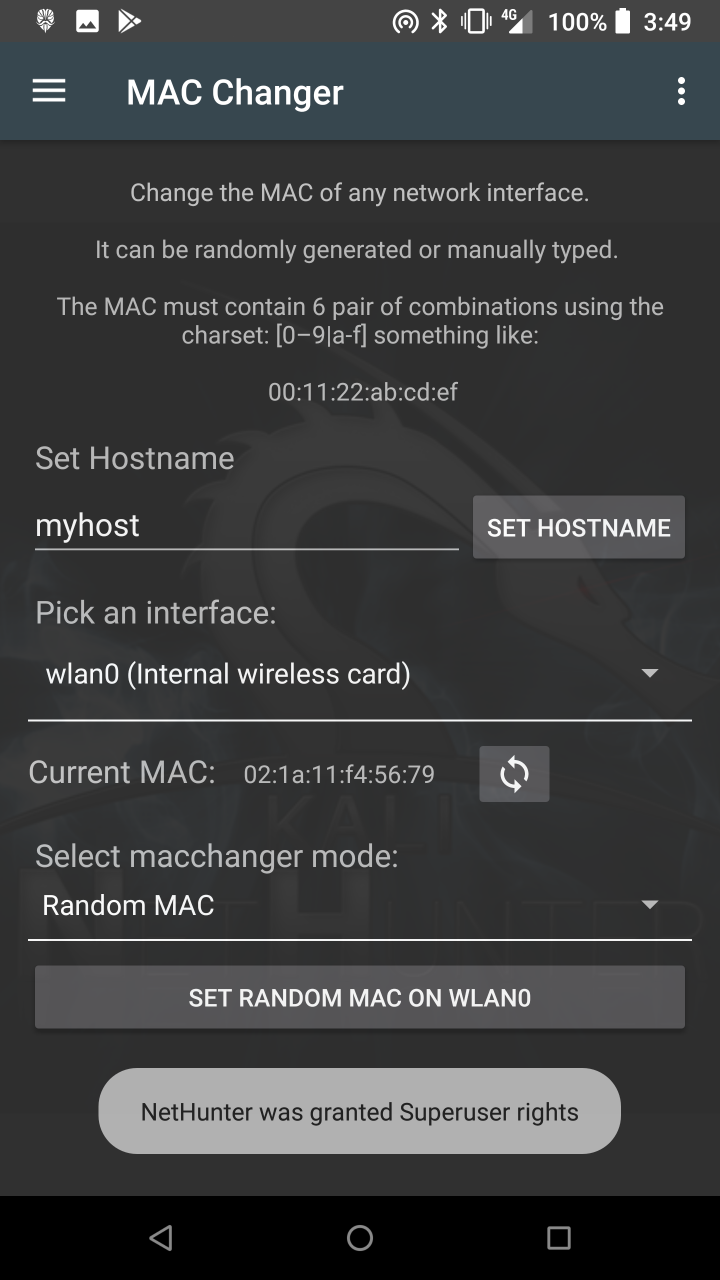
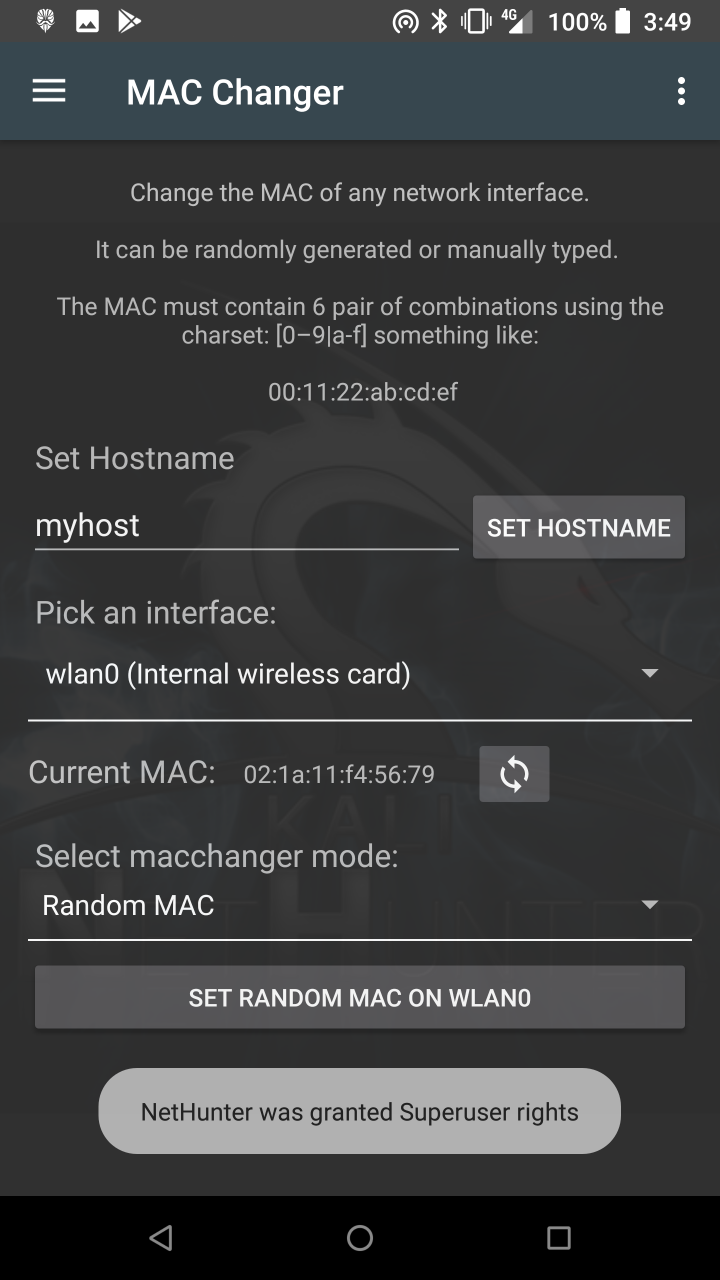
* MAC Changer — Change your Wi-Fi MAC address (only on certain devices)
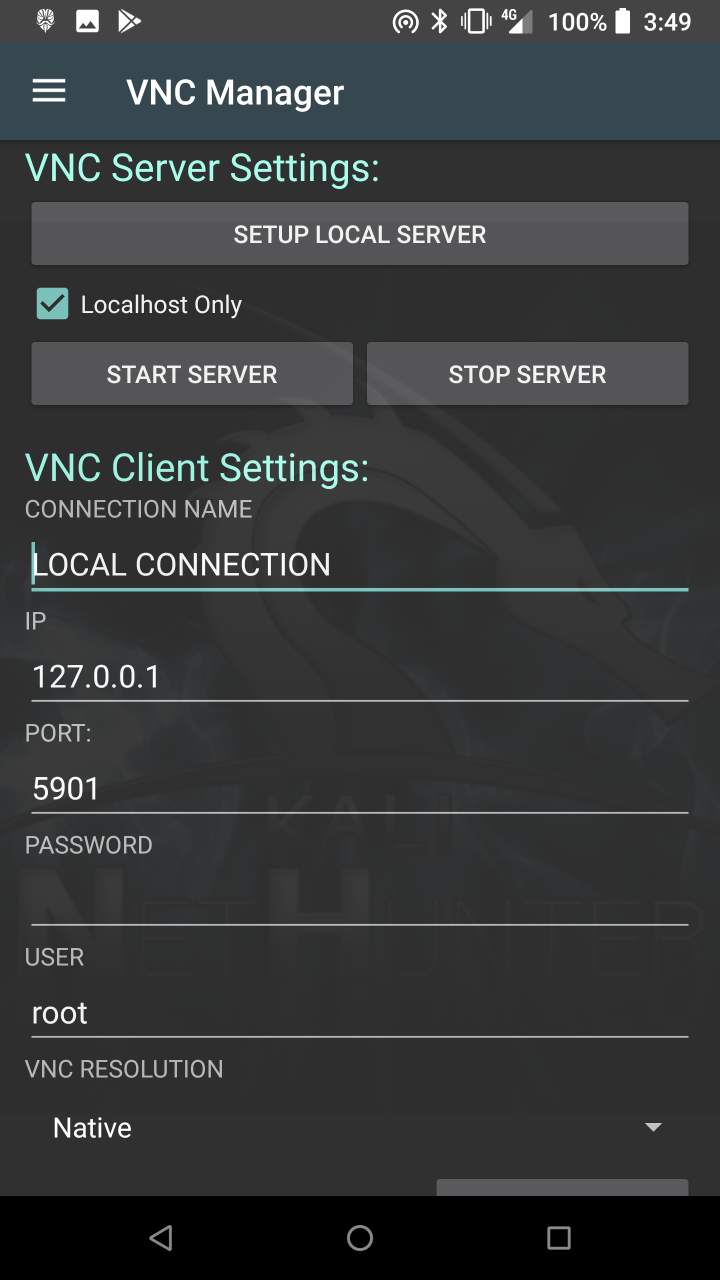
* KeX Manager — Set up an instant KeX session with your Kali chroot.
* HID Attacks — Various HID attacks, Teensy style.
* DuckHunter HID — Rubber Ducky style HID attacks
* BadUSB MITM Attack — Nuff said.
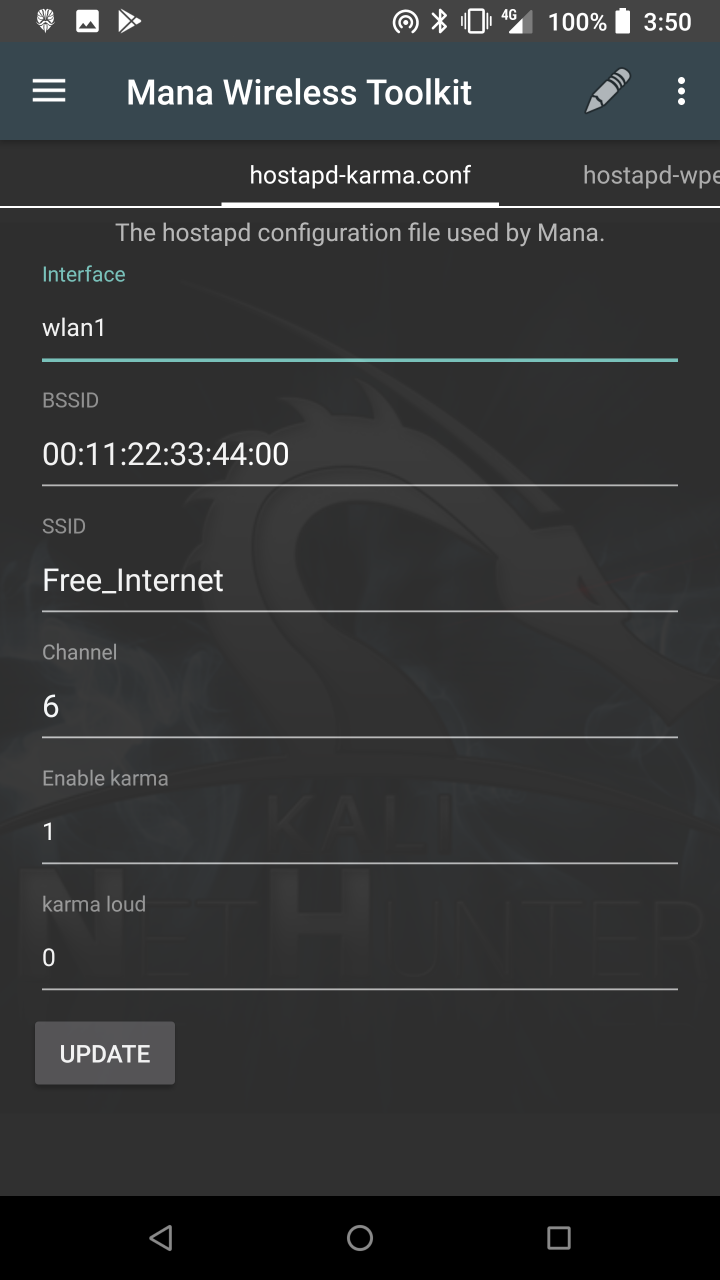
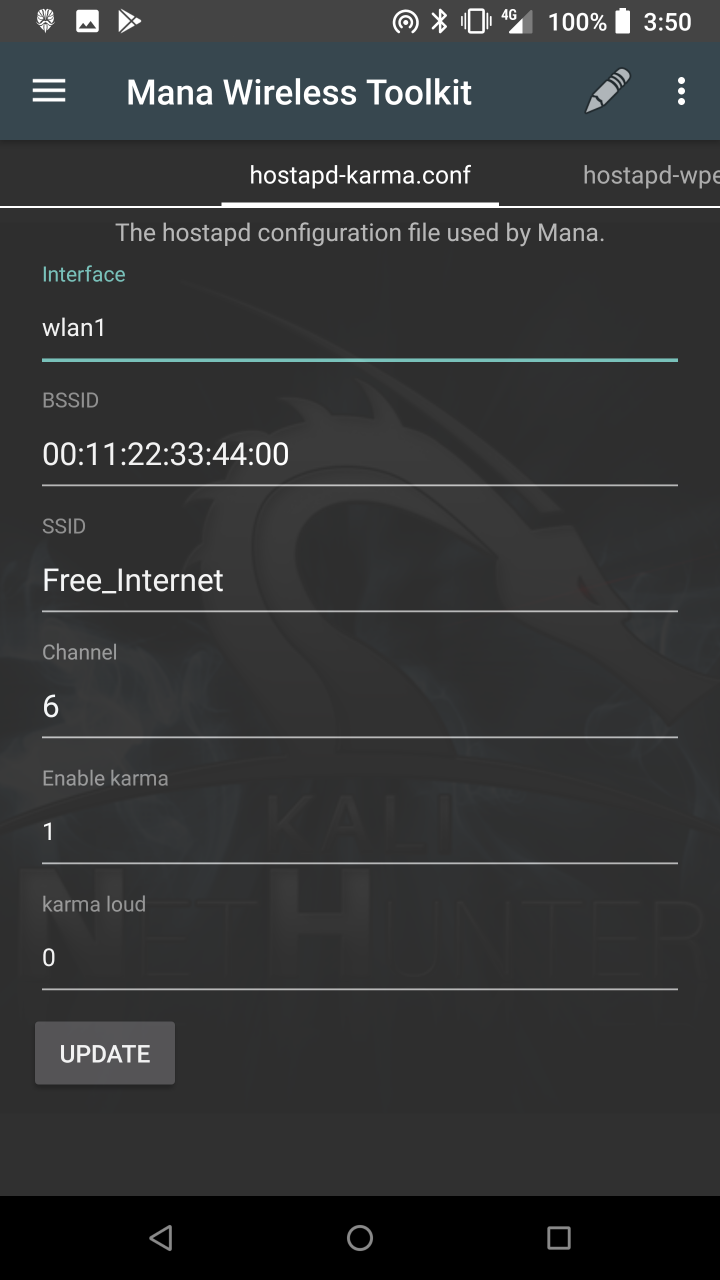
* MANA Wireless Toolkit — Setup a malicious Access Point at the click of a button.
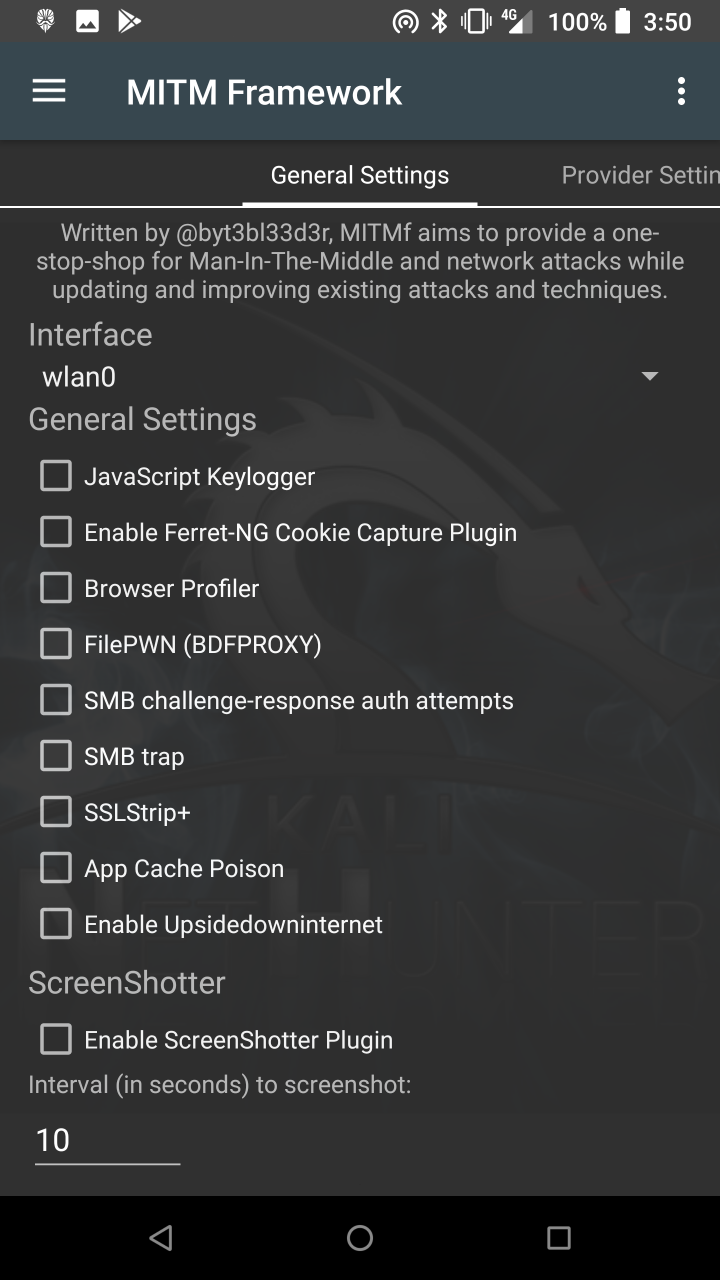
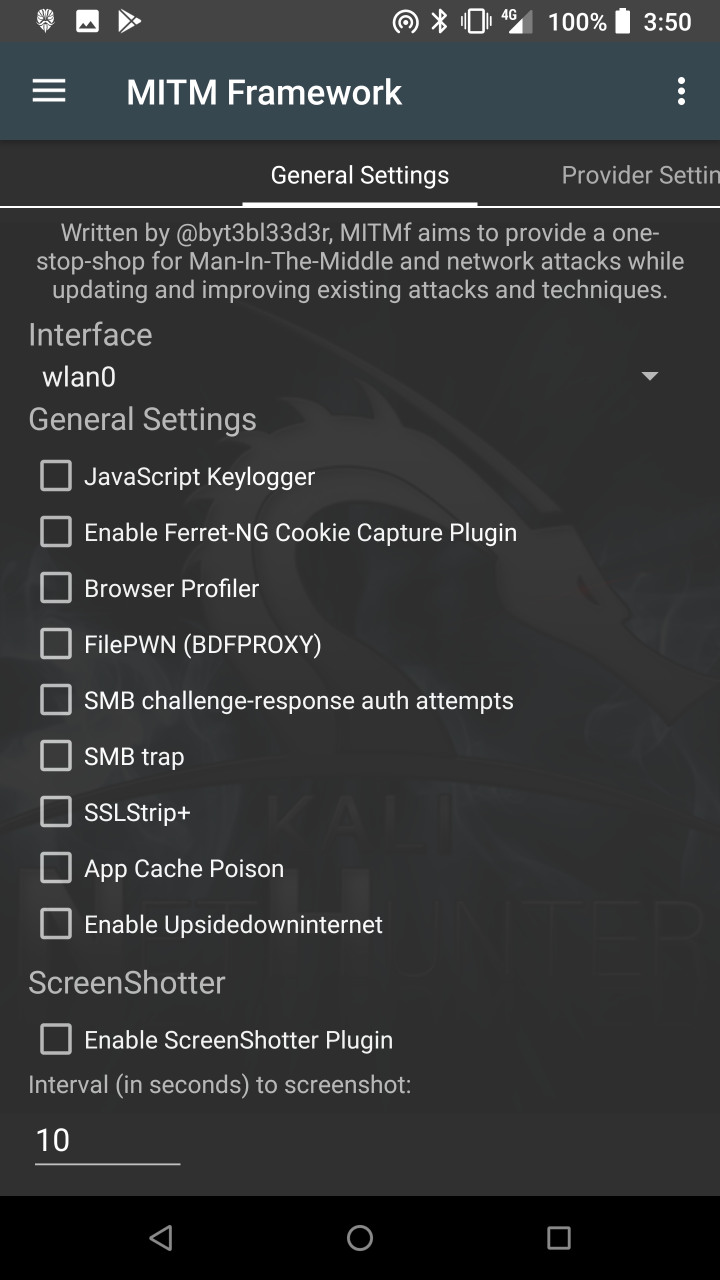
* MITM Framework — Inject binary backdoors into downloaded executables on the fly.
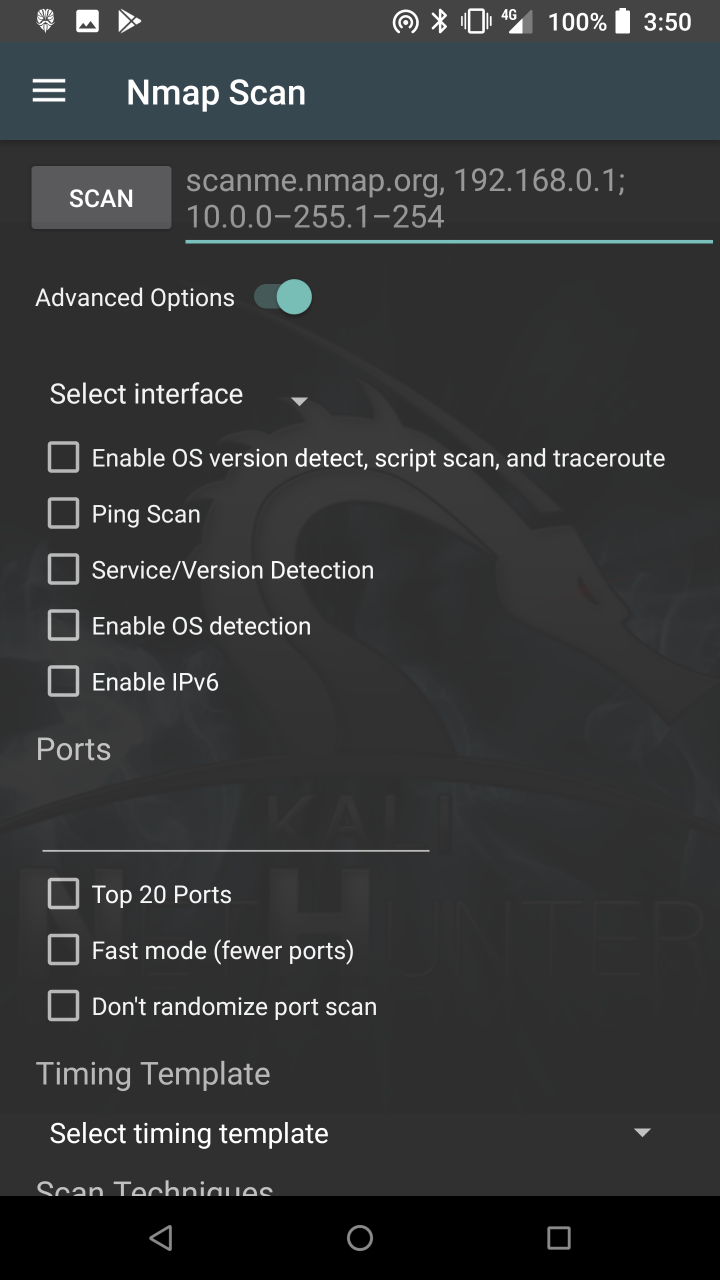
* NMap Scan — Quick Nmap scanner interface.
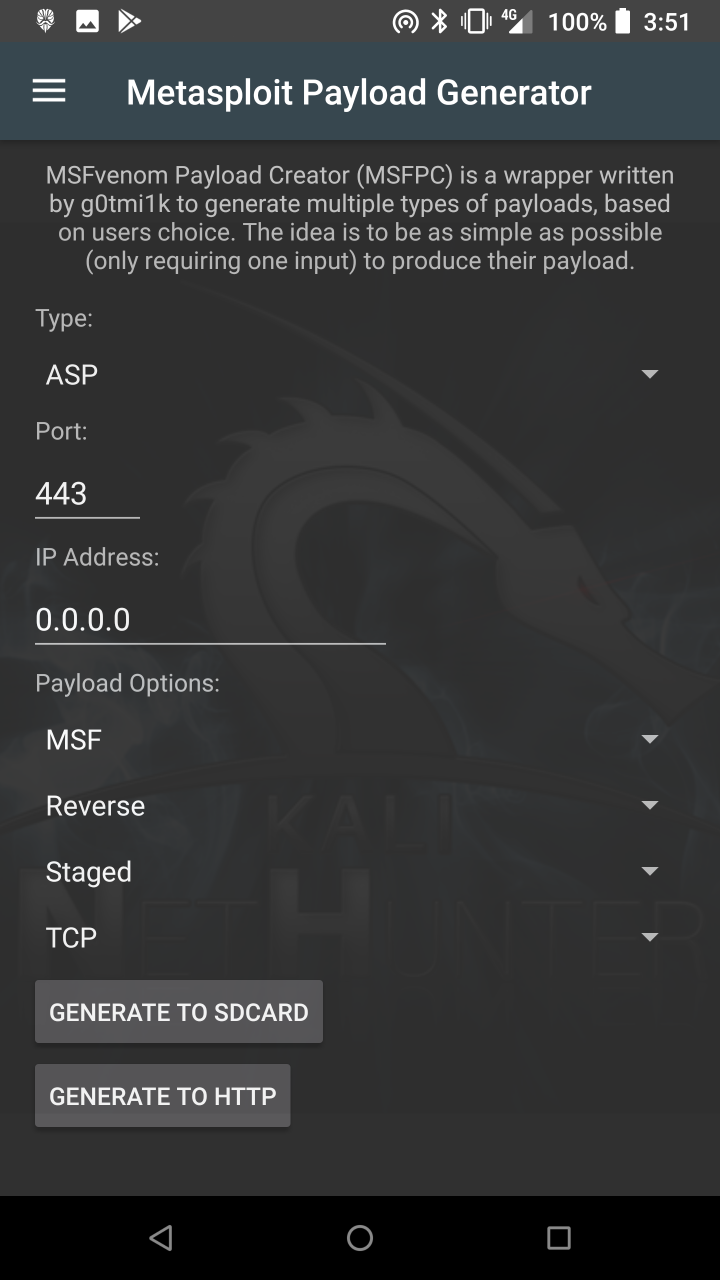
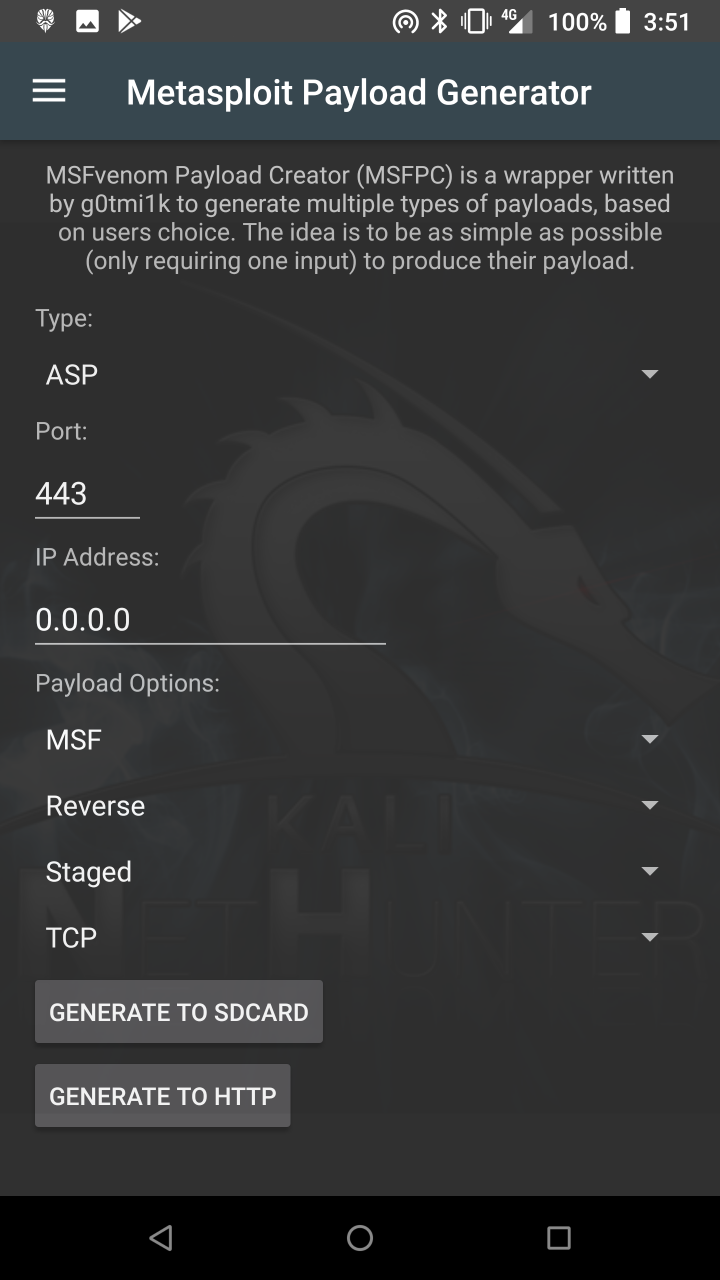
* Metasploit Payload Generator — Generating Metasploit payloads on the fly.
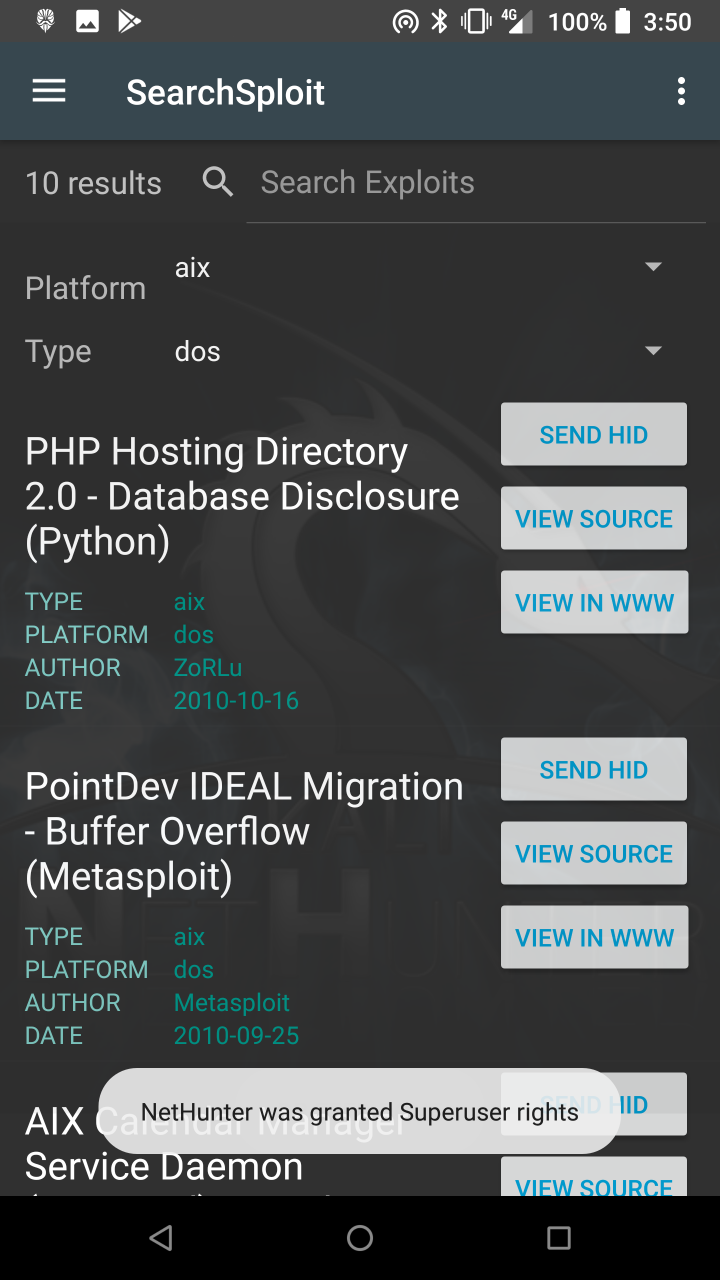
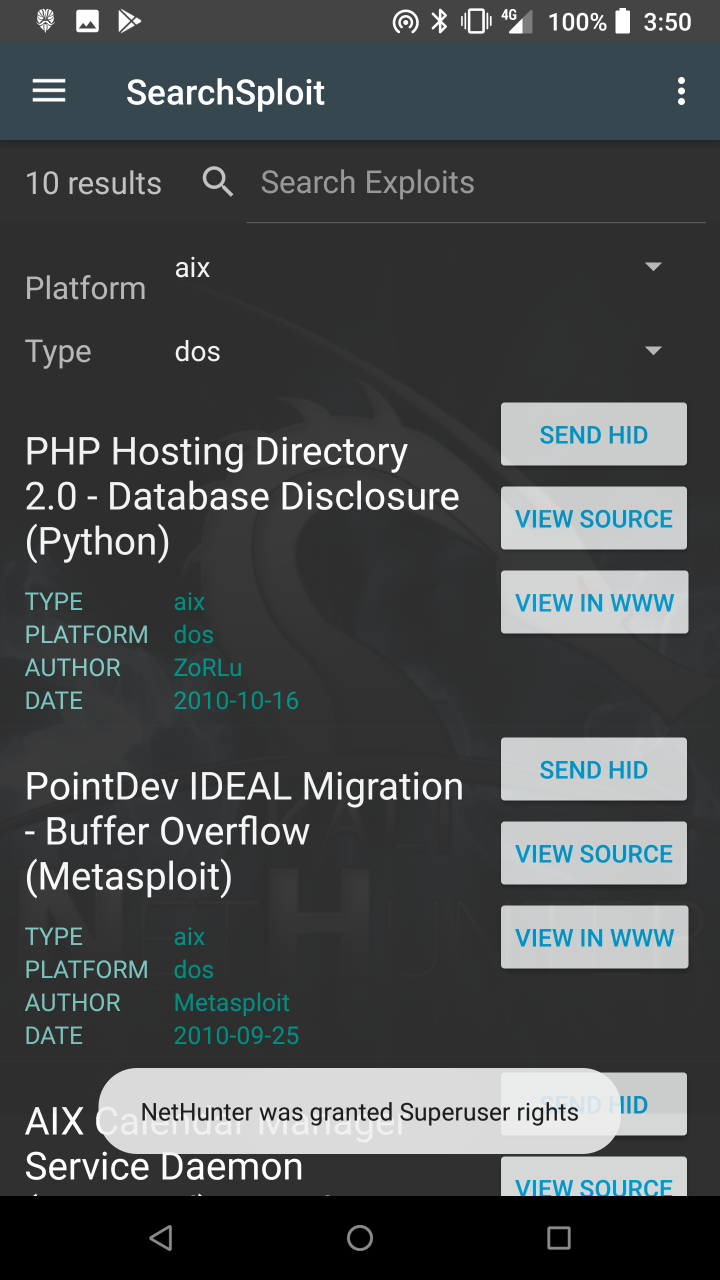
* Searchsploit — Easy searching for exploits in the Exploit-DB.
Requires root, nethunter chroot and nethunter kernel
This app is built and signed by Kali NetHunter.
Packages
Although APK downloads are available below to give you the choice, you should be aware that by installing that way you will not receive update notifications and it’s a less secure way to download. We recommend that you install the F-Droid client and use that.
This version requires Android ? or newer. It is built and signed by the original developer. Download APK 8.8 MiB PGP Signature
- android.permission.INTERNET
- android.permission.BLUETOOTH
- android.permission.BLUETOOTH_ADMIN
- android.permission.BLUETOOTH_PRIVILEGED
- android.permission.ACCESS_WIFI_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.WRITE_EXTERNAL_STORAGE
- com.offsec.nhterm.permission.RUN_SCRIPT
- com.offsec.nhterm.permission.RUN_SCRIPT_SU
- com.offsec.nhterm.permission.RUN_SCRIPT_NH
- com.offsec.nhterm.permission.RUN_SCRIPT_NH_LOGIN
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.WAKE_LOCK
- android.permission.VIBRATE
- android.permission.ACCESS_FINE_LOCATION
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_BACKGROUND_LOCATION
- android.permission.FOREGROUND_SERVICE
- android.permission.BIND_ACCESSIBILITY_SERVICE
This version requires Android ? or newer. It is built and signed by the original developer. Download APK 8.8 MiB PGP Signature
- android.permission.INTERNET
- android.permission.BLUETOOTH
- android.permission.BLUETOOTH_ADMIN
- android.permission.BLUETOOTH_PRIVILEGED
- android.permission.ACCESS_WIFI_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.WRITE_EXTERNAL_STORAGE
- com.offsec.nhterm.permission.RUN_SCRIPT
- com.offsec.nhterm.permission.RUN_SCRIPT_SU
- com.offsec.nhterm.permission.RUN_SCRIPT_NH
- com.offsec.nhterm.permission.RUN_SCRIPT_NH_LOGIN
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.WAKE_LOCK
- android.permission.VIBRATE
- android.permission.ACCESS_FINE_LOCATION
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_BACKGROUND_LOCATION
- android.permission.FOREGROUND_SERVICE
- android.permission.BIND_ACCESSIBILITY_SERVICE
This version requires Android ? or newer. It is built and signed by the original developer. Download APK 8.8 MiB PGP Signature
- android.permission.INTERNET
- android.permission.BLUETOOTH
- android.permission.BLUETOOTH_ADMIN
- android.permission.BLUETOOTH_PRIVILEGED
- android.permission.ACCESS_WIFI_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.WRITE_EXTERNAL_STORAGE
- com.offsec.nhterm.permission.RUN_SCRIPT
- com.offsec.nhterm.permission.RUN_SCRIPT_SU
- com.offsec.nhterm.permission.RUN_SCRIPT_NH
- com.offsec.nhterm.permission.RUN_SCRIPT_NH_LOGIN
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.WAKE_LOCK
- android.permission.VIBRATE
- android.permission.ACCESS_FINE_LOCATION
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_BACKGROUND_LOCATION
- android.permission.FOREGROUND_SERVICE
- android.permission.BIND_ACCESSIBILITY_SERVICE
This version requires Android ? or newer. It is built and signed by the original developer. Download APK 8.8 MiB PGP Signature
- android.permission.INTERNET
- android.permission.BLUETOOTH
- android.permission.BLUETOOTH_ADMIN
- android.permission.BLUETOOTH_PRIVILEGED
- android.permission.ACCESS_WIFI_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.WRITE_EXTERNAL_STORAGE
- com.offsec.nhterm.permission.RUN_SCRIPT
- com.offsec.nhterm.permission.RUN_SCRIPT_SU
- com.offsec.nhterm.permission.RUN_SCRIPT_NH
- com.offsec.nhterm.permission.RUN_SCRIPT_NH_LOGIN
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.WAKE_LOCK
- android.permission.VIBRATE
- android.permission.ACCESS_FINE_LOCATION
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_BACKGROUND_LOCATION
- android.permission.FOREGROUND_SERVICE
- android.permission.BIND_ACCESSIBILITY_SERVICE