Easily Crack ZIP File Passwords using Zydra
Zydra is a password recovery tool that can recover passwords from files and Linux shadow files using brute-force or dictionary attack. That means, it can crack passwords of ZIP, RAR and PDF files. Also it can recover passwords of Linux systems using the shadow file (shadow file stores user passwords in Linux system).
Key Features of Zydra
Zydra’s main features are following:
- The most important features of Zydra is the multiprocessing feature that speeds up the program. For example if we have 8 CPU cores, Zydra will use all of them for processing at the same time.
- It can be use against Legacy ZIP files, RAR files, PDF files and shadow files.
- Cracking files password using two methods dictionary method and brute force method.
- In the brute force method, we can specify the min length and max length of the passwords, also we can specify the type of characters that may be used in the password.
- A percent progress bar showing how much of the process has been performed.
- Error handling.
Installing Zydra on Kali Linux
We can found Zydra on it’s GitHub repository but before that we will install some dependencies to work Zydra perfectly.
First of all we update our system by using following command:
Then we download some dependencies by using following command:
sudo apt-get install qpdf unrarThe above command will install qpdf and unrar on our system as we can see in the following screenshot:
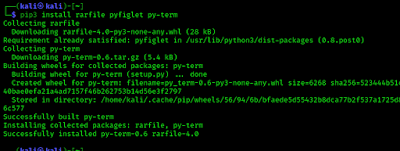
Then we need to install some Python3 modules using pip.
pip3 install rarfile pyfiglet py-termThese will be installed on our system after using above command as we can see it.
Now we just need to download figlet font «epic» for Zydra by using following command:
sudo wget http://www.figlet.org/fonts/epic.flf -O /usr/share/figlet/epic.flfNow it’s time to download the Zydra from GitHub. Either we can clone the whole repository or we can just download the Python script. Let we download just the Python script by using following command:
wget -O zydra.py https://raw.githubusercontent.com/hamedA2/Zydra/master/Zydra.pyThe python script will be saved our current working directory by the name of zydra.py.
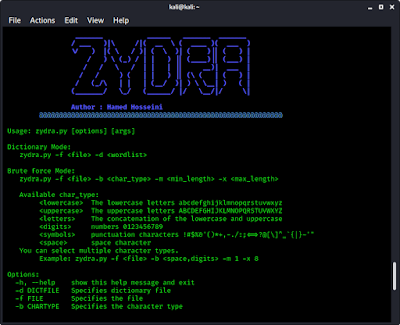
Now we can run the script. First of all we check the help option by applying following command:
We can see the help menu of Zydra in the following screenshot:
Either we can read the boring help section of Zydra or continue reading out guide to know the important uses of this tool.
How to Crack ZIP files password on Kali Linux
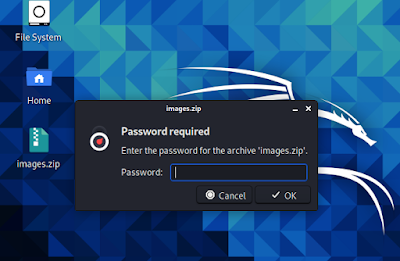
Here we have a ZIP file on our Desktop which is protected by a password. We can see that it prompt for password on the following screenshot:
Now we try to brake the password with dictionary attack. To perform this we need a password list. We will use the 10k-most-common.txt (password list). It comes with our Kali Linux (/usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt), which contains 10,000 most commonly used passwords.
So we open our terminal and our command will be following:
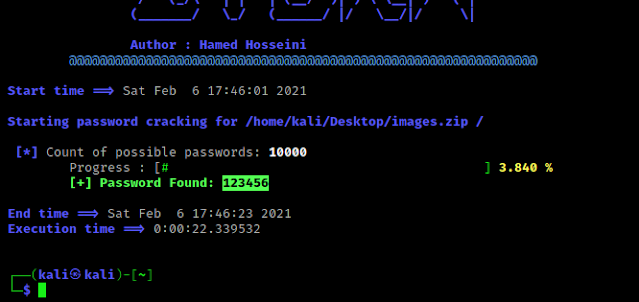
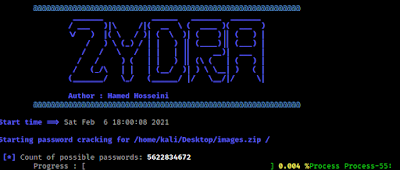
python3 zydra.py -f /home/kali/Desktop/images.zip -d /usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt
Here we have used the -f flag to specify the location of the ZIP file (in our case which is /home/kali/Desktop/images.zip ) and using the -d flag we have specify the location of the dictionary (password list). Output shown in the following screenshot:
On the above screenshot we can see that we have successfully cracked the password of the ZIP file using Zydra.
This is how we can use the dictionary attack we also can try without password list. In that case we need to use brute-force attack and we need to specify the type of characters that may be used in the password.
python3 zydra.py -f /home/kali/Desktop/images.zip -b digits,symbols -m 4 -x 6
Here we have choose -b flag for brute force attack and specified our password (mixing digits and symbols), then we use -m flag for minimum length of our password (we choose 4) and -x for maximum length of our password (we choose 6).
On the above screenshot we can see that Zydra has created a count of possible password list which is very big (5622834672 passwords). Which will take a lot of time. Also may gives error (but the scan continues).
Note: Zydra can recover legacy ZIP files password (The standard one). We have created a ZIP file on Linux system (using Archive Manager) Zydra can’t break it. But ZIP files created from Windows and internet works perfectly.
How to crack RAR files password using Zydra
Cracking a RAR file’s password is very similar to cracking ZIP file’s password on Zydra. To do it we need to run following command on our terminal:
python3 zydra.py -f /home/kali/Desktop/images.rar -d /usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt
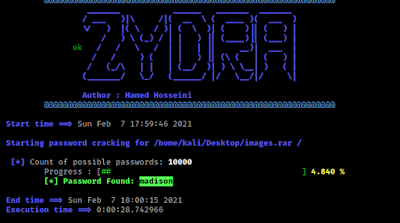
Then Zydra will start scanning the process. Here we have again choose 10k-most-common.txt password list inside our /usr/share/seclists/Passwords directory which is specified by -d flag and our target RAR file is specified by -f flag located on our Desktop.
After waiting very few moments we got our password, as we can see in the screenshot:
Now we can see on the above screenshot that we have successfully recovered the password of the RAR file.
We also can use bruteforce attack to recover the password. To do that we need to use -b flag in the place of -d flag and we should specify the type of password and length as we did on ZIP files section, an example command is following:
python3 zydra.py -f /home/kali/Downloads/file.rar -b digits,symbols -m 4 -x 6
How to Break or Crack Password of PDF file
Cracking PDF file’s password is also very similar as ZIP and RAR. We just need to use Zydra and tell Zydra the location of PDF file and the location of password list.
Here we have an example PDF file on our Desktop, which is locked. As we can see in the following screenshot:
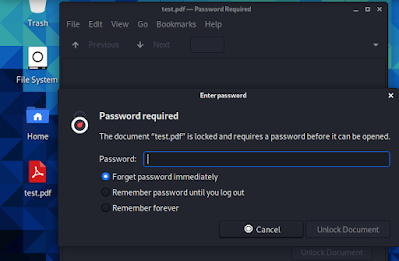 |
| Locked PDF file on Desktop |
Now we run Zydra and try to break the password of this PDF file by using following command:
python3 zydra.py -f /home/kali/Desktop/test.pdf -d /usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt
Here we have used -f flag to specify our PDF file location and we used -d to specify location of our passsword list. The output of the command shows in the following screenshot:
This is how we can crack the password of a PDF file using Zydra on our Kali Linux system.
Recover Linux passwords from shadow file
Linux’s users password stored (encrypted) on the shadow file,located on /etc/shadow. Using Zydra we also able to crack shadow file’s passwords. Zydra will crack the passwords one by one for every user on the system.
Either we can copy the shadow file from a system or we can run Zydra on the target system. Here for an example we run copied all the texts from shadow file from another system and saved it on our system (Desktop) in a file called shadow without file extension and try recover the password.
To do so we can apply following command on our terminal:
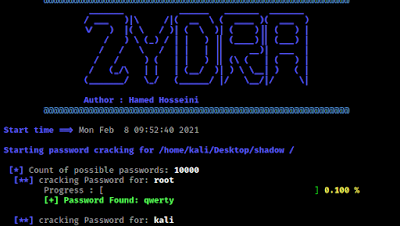
python3 zydra.py -f /home/kali/Desktop/shadow -d /usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt
The screenshot shows that Zydra cracked one user and trying for the other
If we need to crack our own system’s password then we need to use our root account (also may need to install rarfile pyfiglet py-term there). The command will be following(we need to log in as root, sudo command from non-root user may show error here):
python3 zydra.py -f /etc/shadow -d /usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt
Conclusion
This is how to crack password protected ZIP, RAR, PDF files using Zydra on Kali Linux or other debian based Linux system. We also can recover password of Linux users using Zydra.
This is created for educational perpose only we also can use it to recover forgotten password of files. But using Zydra against other’s protected file will be considered crime as per law. So please do not use it to others without proper permission. We will not be responsible if anyone did this.
Love our articles? Stay updated with our articles by following us on Twitter and GitHub . Be a part of the KaliLinuxIn community by joining our Telegram Group , where we focus on Linux and Cybersecurity. We’re always available to help in the comment section and read every comment, ensuring a prompt reply.