Kali linux persistence live
In this workshop, we will examine the various features available to us when booting Kali Linux from USB devices. We will explore features such as persistence, creating LUKS encrypted persistence stores, and even dabble in “LUKS Nuking” our USB drive. The default Kali Linux ISOs (from 1.0.7 onwards) support USB encrypted persistence.
0x01 — Start by imaging the Kali ISO onto your USB drive (ours was /dev/sdb). Once done, you can inspect the USB partition structure using parted /dev/sdb print:
For ease of use, please use a root account. This can be done with “sudo su”.
[email protected]:~$ dd if=kali-linux-2023.2-live-amd64.iso of=/dev/sdb conv=fsync bs=4M 0x02 — Create and format an additional partition on the USB drive. In our example, we create a persistent partition in the empty space above the Kali Live partitions:
When fdisk completes, the new partition should have been created at /dev/sdb3 ; this can be verified with the command lsblk .
0x03 — Encrypt the partition with LUKS:
[email protected]:~$ cryptsetup --verbose --verify-passphrase luksFormat /dev/sdb3 0x04 — Open the encrypted partition:
[email protected]:~$ cryptsetup luksOpen /dev/sdb3 my_usb 0x05 — Create an ext4 filesystem and label it:
[email protected]:~$ mkfs.ext4 -L persistence /dev/mapper/my_usb [email protected]:~$ e2label /dev/mapper/my_usb persistence 0x06 — Mount the partition and create your persistence.conf so changes persist across reboots:
[email protected]:~$ mkdir -p /mnt/my_usb [email protected]:~$ mount /dev/mapper/my_usb /mnt/my_usb [email protected]:~$ echo "/ union" | sudo tee /mnt/my_usb/persistence.conf [email protected]:~$ umount /dev/mapper/my_usb 0x07 — Close the encrypted partition:
[email protected]:~$ cryptsetup luksClose /dev/mapper/my_usb Now your USB drive is ready to plug in and reboot into Live USB Encrypted Persistence mode.
Multiple Persistence Stores
At this point we should have the following partition structure:
We can add additional persistence stores to the USB drive, both encrypted or not… and choose which persistence store we want to load, at boot time. Let’s create one more additional non-encrypted store. We’ll label and call it “work”.
0x01 — Create an additional, 4th partition which will hold the “work” data. We’ll give it another 5GB of space:
[email protected]:~$ parted /dev/sdb GNU Parted 2.3 Using /dev/sdb Welcome to GNU Parted! Type 'help' to view a list of commands. (parted) print Model: SanDisk SanDisk Ultra (scsi) Disk /dev/sdb: 31.6GB Sector size (logical/physical): 512B/512B Partition Table: msdos Number Start End Size Type File system Flags 1 32.8kB 2988MB 2988MB primary boot, hidden 2 2988MB 3050MB 64.9MB primary fat16 3 3050MB 10.0GB 6947MB primary (parted) mkpart primary 10000 15000 (parted) quit Information: You may need to update /etc/fstab. 0x02 — Format the fourth partition, label it “work”:
[email protected]:~$ mkfs.ext4 /dev/sdb4 [email protected]:~$ e2label /dev/sdb4 work 0x03 — Mount this new partition and create a persistence.conf in it:
[email protected]:~$ mkdir -p /mnt/usb [email protected]:~$ mount /dev/sdb4 /mnt/usb [email protected]:~$ echo "/ union" > /mnt/usb/persistence.conf [email protected]:~$ umount /mnt/usb Boot the computer, and set it to boot from USB. When the boot menu appears, edit the persistence-label parameter to point to your preferred persistence store!
Emergency Self Destruction of Data in Kali
As penetration testers, we often need to travel with sensitive data stored on our laptops. Of course, we use full disk encryption wherever possible, including our Kali Linux machines, which tend to contain the most sensitive materials. Let’s configure a nuke password as a safety measure:
[email protected]:~$ sudo apt install -y cryptsetup-nuke-password [email protected]:~$ dpkg-reconfigure cryptsetup-nuke-password The configured nuke password will be stored in the initrd and will be usable with all encrypted partitions that you can unlock at boot time.
Backup you LUKS keyslots and encrypt them:
[email protected]:~$ cryptsetup luksHeaderBackup --header-backup-file luksheader.back /dev/sdb3 [email protected]:~$ openssl enc -e -aes-256-cbc -in luksheader.back -out luksheader.back.enc Now boot into your encrypted store, and give the Nuke password, rather than the real decryption password. This will render any info on the encrypted store useless. Once this is done, verify that the data is indeed inacessible.
Lets restore the data now. We’ll decrypt our backup of the LUKS keyslots, and restore them to the encrypted partition:
[email protected]:~$ openssl enc -d -aes-256-cbc -in luksheader.back.enc -out luksheader.back [email protected]:~$ cryptsetup luksHeaderRestore --header-backup-file luksheader.back /dev/sdb3 Our slots are now restored. All we have to do is simply reboot and provide our normal LUKS password and the system is back to its original state.
Updated on: 2023-May-30
Author: g0tmi1k
Kali linux persistence live
One of the fastest method, for getting up and running with Kali Linux is to run it “live” from a USB drive. This method has several advantages:
- It’s non-destructive — it makes no changes to the host system’s hard drive or installed OS, and to go back to normal operations, you simply remove the Kali Live USB drive and restart the system
- It’s portable — you can carry Kali Linux in your pocket and have it running in minutes on an available system
- It’s customizable — you can roll your own custom Kali Linux ISO image and put it onto a USB drive using the same procedures
- It’s potentially persistent — with a bit of extra effort, you can configure your Kali Linux “live” USB drive to have persistent storage, so the data you collect is saved across reboots
In order to do this, we first need to create a bootable USB drive which has been set up from an ISO image of Kali Linux.
The specifics of this procedure will vary depending on whether you’re doing it on a Linux, macOS/OS X, or Windows system.
What You’ll Need
- A verified copy of the appropriate ISO image of the latest Kali build image for the system you’ll be running it on.
- If you’re running under Windows, there is not one tool that is considered the overall best for imaging. We recommend Etcher(installer or portable) as it is simpler to use, however Rufus is another popular option with its advance options. If one does not work for you, consider the other.
- A USB drive, 8GB or larger (Systems with a direct SD card slot can use an SD card with similar capacity. The procedure is identical.)
During this procedure, you might see some warnings telling you that Kali Linux contains malware, trojan, virus or whatever. This message usually comes from Windows Defender or USB Defender, or a third-party antivirus. Those warnings are expected: Kali Linux is packed with pentesting tools that are likely to be flagged as malware. Just ignore the warnings.
Creating a Bootable Kali USB Drive on Windows (Etcher)
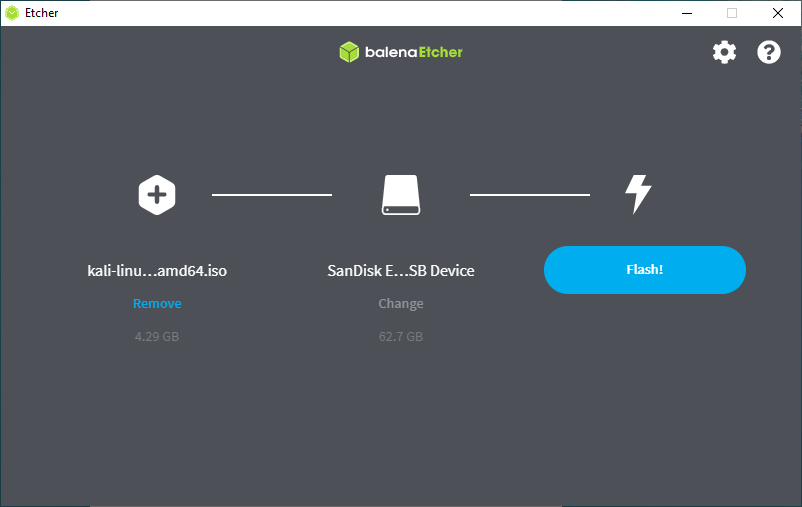
- Plug your USB drive into an available USB port on your Windows PC, note which drive designator (e.g. “ G:\ ”) it uses once it mounts, and launch Etcher.
- Click Flash from file, and locate the Kali Linux ISO file to be imaged with.
- Click Select target and choose the USB drive you want to make bootable.
- Click the Flash! button once ready.
Note: You may get a UAC prompt asking for administrator privileges that you will need to accept.
5. Once Etcher alerts you that the image has been flashed, you can safely remove the USB drive and proceed to boot into Kali with it.
At the time of writing, Etcher will use MBR. This is to allow for the most hardware compatibility.
Creating a Bootable Kali USB Drive on Windows (Rufus)
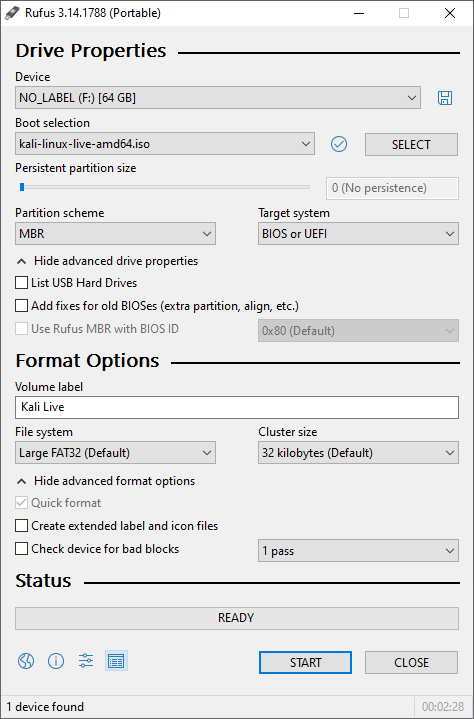
- Plug your USB drive into an available USB port on your Windows PC, note which drive designator (e.g. “ G:\ ”) it uses once it mounts, and launch Rufus.
- With Device, check the dropdown list of options for the USB drive (e.g. “ G:\ ” and size).
- Boot selection needs to point to point to the Kali Linux ISO file, which can be done by clicking the SELECT button
- Depending on your configuration, you can set the Partition scheme, as well as Target system. If you are not sure, leave it as the default values.
While you can easily create a persistent live usb with the integrated options in Rufus by increasing the persistence slider, this is not the officially supported method (check Adding Persistence to a Kali Linux Live USB Drive), as it doesn’t work for all images, like the Kali Everything Live ISO introduced in release 2022.1.
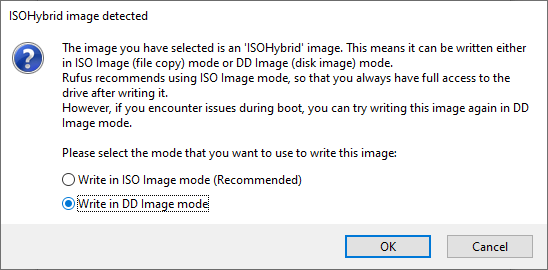
6. You may get a prompt saying about ISOHybird image. Selecting ISO image, will allow you to edit the files from the Kali Linux ISO, but at the potential lose of hardware compatibility. As a result, we recommend selecting DD Image.
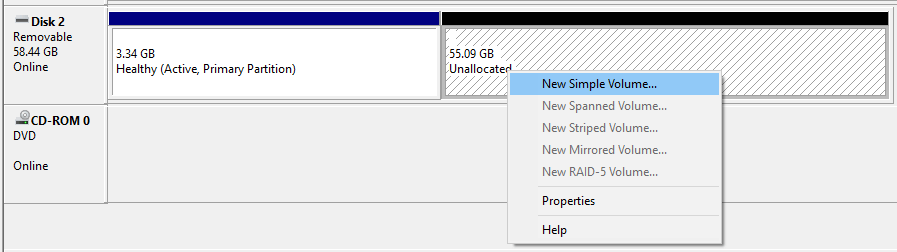
Note: If you select “DD Image” option, you can create another partition on the USB drive, allowing you to use the rest of the space. Start -> Run (Windows + R) -> diskmgmt.msc -> Locate the USB drive -> Right-click in “Unallocated” -> New Simple Volume -> Follow the rest of the wizard with next, next, next…
Booting A USB Drive In Windows
Depending on the system (such as BIOS or UEFI), as well as the version of Windows, and how they are each configured, you may need to re-image the USB drive.
- Master Boot Record (MBR) is often used on legacy systems that use BIOS as well as UEFI which has Compatibility Support Module (CSM) enabled
- GUID Partition Table (GPT) is required where UEFI has CSM disabled, forcing to use the modern standard
After writing the image to the USB drive, reboot Windows with the USB inserted. Depending on the motherboard manufacture, will also depend on the next stage. Some motherboard’s support a “temporary” boot menu, allowing for a one off selection. Others you need to enter BIOS/UEFI to configure it to try and boot from USB first. Entering either location, also depends on the motherboard. You can look up on the manufactures website and read the manual, try and read the screen when booting (however the text may be shown too quick or full logos used), or try common key combinations (such as ESC , F1 , F2 , F3 , F4 , F8 , F10 , F11 , F12 or DEL ).
Updated on: 2023-May-18
Author: g0tmi1k