- Top 8 reverse engineering tools for cyber security professionals [updated 2021]
- Apktool:
- dex2jar:
- diStorm3:
- edb-debugger:
- Jad Debugger:
- Javasnoop:
- OllyDbg:
- Valgrind:
- Kali Linux — Reverse Engineering
- OllyDbg
- dex2jar
- jd-gui
- apktool
- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- Reverse
- Описание Reverse
- Справка по Reverse
- Руководство по Reverse
- Редактировать с vim
- Пользовательские цвета
- Примеры запуска Reverse
- Псевдодекомпиляция функций
- Интерактивный режим (-i)
- Анализ шелл-кода
- Установка Reverse
- Установка в Kali Linux, Debian, Ubuntu, Mint
- Скриншоты Reverse
- Инструкции по Reverse
Top 8 reverse engineering tools for cyber security professionals [updated 2021]
Whether it is rebuilding a car engine or diagramming a sentence, people can learn about many things simply by taking them apart and putting them back together again. This process of breaking something down to understand it, build a copy to improve it, is known as reverse engineering.
The process of reverse engineering was originally applied to hardware only, but it is now being applied to software, databases and even human DNA as well. In the field of cyber security, the reverse engineering can be used to identify the details of a breach that how the attacker entered the system, and what steps were taken to breach the system.
Cyber criminals behind the attack, utilize the full spectrum of computer intrusion techniques to breach into corporate networks. They have a specific objective and are skilled, motivated, organized and well-funded. Here, reverse engineering enables us to identify their techniques to prevent it in future. There are some tools available for reverse engineering in Kali Linux (The most preferred operating system by ethical hackers). Here are some essential tools that are used to perform reverse engineering in Kali Linux:
Apktool:
Apktool is a tool third party tool for reverse engineering that can decode resources to nearly original form and recreate them after making some adjustments. It allows debugging smali code step by step and also it allows working with app easier due to its project-like files structure and automation of some repetitive tasks like building apk, etc.
Apktool features:
- decoding resources to nearly original form (including resources.arsc, XMLs and 9.png files) and rebuilding them
- smali debugging
- helping with some repetitive tasks
dex2jar:
Dex2jar is a lightweight API designed to read the Dalvik Executable (.dex/.odex) format. It is used to work with Android and Java .class files. dex2jar contains following components:
- dex-reader is designed to read the Dalvik Executable (.dex/.odex) format. It has a lightweight API similar with ASM.
- dex-translator is designed to do the convert job. It reads the dex instruction to dex-ir format, after some optimize, convert to ASM format.
- dex-ir used by dex-translator is designed to represent the dex instruction
- dex-tools tools to work with .class files. here are examples: Modify an apk, DeObfuscate a jar
- d2j-smali [To be published] disassemble dex to smali files and assemble dex from smali files. different implementation to smali/baksmali, same syntax, but we support escape in type desc “Lcom/dex2jartu1234;”
- dex-writer [To be published] write dex same way as dex-reader.
diStorm3:
diStorm is a lightweight, easy-to-use and a fast decomposer library. It disassembles instructions in 16, 32 and 64-bit modes. It is also the fastest disassembler library. The source code is very clean, readable, portable and platform independent (supports both little and big endianity). diStorm solely depends on the C library. Therefore it can be used in embedded or kernel modules.
diStorm3 is backward compatible with the interface of diStorm64. However, make sure you use the new header files.
edb-debugger:
edb debugger is a Linux equivalent of the famous “Olly debugger” on the Windows platform. One of the main goals of this debugger is modularity. Some of its features are:
- Intuitive GUI interface
- The usual debugging operations (step-into/step-over/run/break)
- Conditional breakpoints
- Debugging core is implemented as a plugin so people can have drop-in replacements. Of course, if a given platform has several debugging APIs available, then you may have a plugin that implements any of them.
- Basic instruction analysis
- View/Dump memory regions
- Effective address inspection
- The data dump view is tabbed, allowing you to have several views of memory open at the same time and quickly switch between them.
- Importing and generation of symbol maps
- Various plugins
Jad Debugger:
Jad has been the most popular Java decompiler ever written. It is a command line utility written in C++. Several graphical shells are available that execute this program behind the scenes while providing the user with a more comfortable interface for source browsing, project management, etc. It is available in Kali Linux for debugging Java applications for reverse engineering and many other purposes.
Javasnoop:
JavaSnoop is an Aspect Security tool that allows security testers to test the security of Java applications easily. JavaSnoop is an example of how Aspect is leading the industry in providing Verification Services, and not just for your web applications.
JavaSnoop allows you to attach an existing process (like a debugger) and instantly begin tampering with method calls, run custom code, or just watch what’s happening on the system.
OllyDbg:
OllyDbg is a 32-bit assembler level analyzing debugger for Microsoft Windows. Emphasis on binary code analysis makes it particularly useful in cases where the source is unavailable.
- Intuitive user interface, no cryptic commands
- Code analysis – traces registers, recognizes procedures, loops, API calls, switches, tables, constants, and strings
- Directly loads and debugs DLLs
- Object file scanning – locates routines from object files and libraries
- Allows for user-defined labels, comments and function descriptions
- Understands debugging information in Borland® format
- Saves patches between sessions, writes them back to executable file and updates fixups
- Open architecture – many third-party plugins are available
- No installation – no trash in registry or system directories
- Debugs multithread applications
- Attaches to running programs
- Configurable disassembler supports both MASM and IDEAL formats
- MMX, 3DNow! and SSE data types and instructions, including Athlon extensions
- Full UNICODE support
- Dynamically recognizes ASCII and UNICODE strings – also in Delphi format!
- Recognizes complex code constructs, like call to jump to procedure
- Decodes calls to more than 1900 standard API and 400 C functions
- Gives context-sensitive help on API functions from external help file
- Sets conditional, logging, memory and hardware breakpoints
- Traces program execution, logs arguments of known functions
- Shows fixups
- Dynamically traces stack frames
- Searches for imprecise commands and masked binary sequences
- Searches whole allocated memory
- Finds references to constant or address range
- Examines and modifies memory, sets breakpoints and pauses program on-the-fly
- Assembles commands into the shortest binary form
Valgrind:
Valgrind is a suite for debugging and profiling Linux programs. With its tool, we can automatically identify memory management and threading bugs, by eliminating hours of provoking bug-hunting and make programs more stable. We can also perform detailed profiling to help speed up program’s processes and use Valgrind to build new tools. The Valgrind distribution currently includes six production-quality tools:
- a memory error detector (Memcheck)
- two thread error detectors (Helgrind and DRD)
- a cache and branch-prediction profiler (Cachegrind)
- a call-graph generating cache and branch-prediction profiler (Callgrind)
- a heap profiler (Massif)
It also includes three experimental tools:
- a stack/global array overrun detector (SGCheck)
- a second heap profiler that examines how heap blocks are used (DHAT)
- a SimPoint basic block vector generator (BBV)
Manufacturers look at reverse engineering as an important means to sustain competition, or some may take it as a tool to understand flaws in the design and re-work for the same. However, Kali Linux provides us with some great and well known reverse engineering tools to perform such activities. Moreover, there are many other reverse engineering tools as well, but these tools are already built-in and come out of the box with Kali Linux.
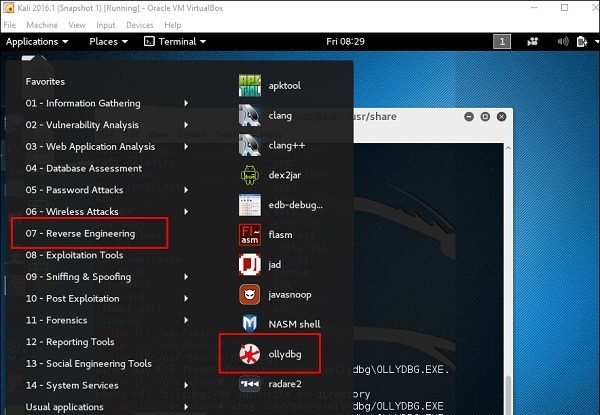
Kali Linux — Reverse Engineering
In this chapter, we will learn about the reverse engineering tools of Kali Linux.
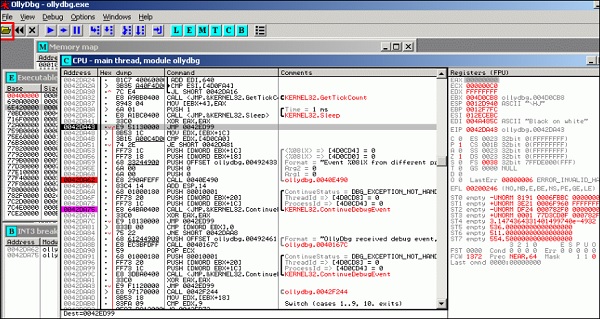
OllyDbg
OllyDbg is a 32-bit assembler level analyzing debugger for Microsoft Windows applications. Emphasis on binary code analysis makes it particularly useful in cases where the source is unavailable. Generally, it is used to crack the commercial softwares.
To open it, go to Applications → Reverse Engineering → ollydbg
To load a EXE file, go the “Opening folder” in yellow color, which is shown in a red square in the above screenshot.
After loading, you will have the following view where you can change the binaries.
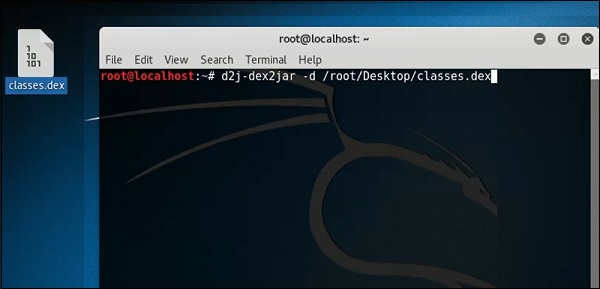
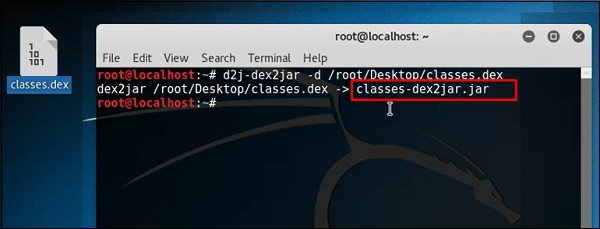
dex2jar
This is an application that helps convert APK file (android) to JAR file in order to view the source code. To use it, open the terminal and write ”d2j-dex2jar –d /file location”.
In this case, the file is “classes.dex” on the desktop.
The following line shows that a JAR file has been created.
jd-gui
JD-GUI is a standalone graphical utility that displays Java source codes of “.class” files. You can browse the reconstructed source code. In this case, we can reconstruct the file that we extracted from the dex2jar tool.
To launch it, open the terminal and write “jd-gui” and the following view will open.
To import the file, click the open folder icon on the left upper corner and then import the file.
apktool
Apktool is one of the best tools to reverse the whole android application. It can decode resources to nearly an original form and rebuild them after making modifications.
To open it, go to the terminal and write “ apktool”.
To decompile a apk file, write “apktool d apk file”.
Decompilation will start as shown in the following screenshot.
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
Reverse
Описание Reverse
Инструмент осуществляет обратный инжиниринг для двоичных файлов x86/ARM/MIPS. Генерирует более читаемый код (псевдо-C) с раскраденным синтаксисом.
Поддерживаемые форматы : ELF, PE, RAW.
Makefile используется только для проверки тестов.
Лицензия: GNU GENERAL PUBLIC LICENSE Version 3
Справка по Reverse
reverse.py [-h] [-nc] [-g] [--nocomment] [--noandif] [--datasize N] [-x SYMBOLNAME|0xXXXXX|EP] [--vim] [-s] [-c SECTION_NAME] [--sections] [--dump] [-l N] [--bytes] [-i] [-d] [-ns] [--raw x86|x64|arm|mips|mips64] [--rawbase 0xXXXXX] [--rawbe] [FILENAME]
позиционные аргументы:
опциональные аргументы:
-h, —help показать это сообщение справки и выйти
-nc, —nocolor без цветов
-g, —graph Сгенерировать html потокового графика. Смотри d3/index.html.
—nocomment Не печатать комментарии
—noandif Печатать нормальные ‘if’ вместо ‘andif’
—datasize N по умолчанию 30, максимальное количество отображаемых символов для строк или для массивов байт.
-x SYMBOLNAME|0xXXXXX|EP, —entry SYMBOLNAME|0xXXXXX|EP Псевдодекомпиляция, по умолчанию — главная. EP выступает за точку входа
—vim Генерирует синтаксис цветов для vim
-s, —symbols Печатать все символы
-c SECTION_NAME, —calls SECTION_NAME Напечатать все вызовы, которые в заданной секции
—sections Напечатать все секции
—dump Дамп ассемблера без декомпиляции
-l N, —lines N Максимум строк, используется с —dump
—bytes Напечатать instruction bytes
-i, —interactive Интерактивный режим
-d, —opt_debug Отладка
-ns, —nosectionsname Без имён секций
—raw x86|x64|arm|mips|mips64 Рассматривать входной файл как сырой бинарный файл
—rawbase 0xXXXXX Установить базовый адрес сырого файла (по умолчанию=0)
—rawbe Если не установлено, то прямой порядок байтов.
Руководство по Reverse
Редактировать с vim
./reverse tests/dowhile1.bin --vim
Теперь вы можете запустить:
vim dowhile1.bin.rev -S dowhile1.bin.vim
Пользовательские цвета
При первой загрузке reverse.py создаёт новый файл custom_colors.py, в котором значения по умолчанию. В нём вы можете установить ваши собственные цвета.
Примеры запуска Reverse
Псевдодекомпиляция функций
Опция -x main является опциональной, поскольку бинарные файлы содержат символ main.
Интерактивный режим (-i)
Больше команд доступны в этом режиме (da, db, …). Смотрите спаску для полного списка.
Анализ шелл-кода
Для каждого int 0x80, инструмент пытается определить системные вызовы с параметрами.
$ ./reverse.py --raw x86 tests/shellcode.bin function 0x0 < 0x0: eax = 0 # xor eax, eax 0x2: al = '\x0b' # mov al, 0xb 0x4: cdq 0x5: push edx 0x6: push 1752379246 "n/sh" 0xb: push 1768042287 "//bi" 0x10: ebx = esp # mov ebx, esp 0x12: push edx 0x13: push ebx 0x14: ecx = esp # mov ecx, esp 0x16: int 128 ; execve(ebx, ecx, edx) # int 0x80 >
Установка Reverse
Установка в Kali Linux, Debian, Ubuntu, Mint
- python >= 3.4
- capstone + python bindings (see requirements.sh)
- python-pyelftools
- https://github.com/simonzack/pefile-py3k
- терминал с 256 цветами (если не используется опция `—nocolor`)
Для связки Python и Capstone engine, вы можете установить его из PyPi следующим образом:
sudo pip3 install capstone
Вы также можете запустить requirements.sh, который получит все компоненты.
git clone https://github.com/joelpx/reverse.git cd reverse/ ./requirements.sh ./reverse.py --help
Скриншоты Reverse

Инструкции по Reverse
Ссылки на инструкции будут добавлены позже.