- Saved searches
- Use saved searches to filter your results more quickly
- zacheller/rockyou
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- Rockyou Txt Wordlist Download 2022/2023 – #1 Password List in Kali Linux
- What is Rockyou Txt Used for?
- Why Choose Rockyou
- Rockyou Password List Location in Kali Linux
- How to Unzip rockyou.txt.gz To rockyou.txt
- Creating Your Own Custom Wordlist
- Rockyou is best for Brute-Forcing WPA, SSH, FTP & other credentials
- Update: RockYou2021 Password File Download
- Rockyou Txt (Rockyou.txt 2021) Download 2022/2023 – Best Password List File
- What is Rockyou wordlist?
- Rockyou wordlist in Kali Linux 2022.2
- Location of Rockyou wordlist
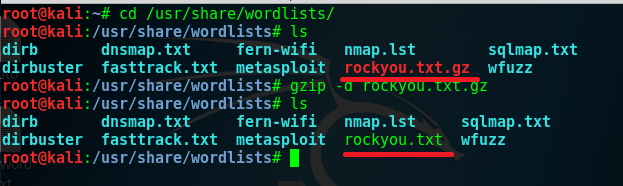
- Unzip rockyou.txt.gz into rockyou txt
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
zacheller/rockyou
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
rockyou.txt is a list of over 14 million plaintext passwords from the 2009 RockYou hack. Passwords from this wordlist are commonly used in CTF and penetration testing challenges. On default Kali Linux installations, the file is in the /usr/share/wordlists/ directory.
Rockyou Txt Wordlist Download 2022/2023 – #1 Password List in Kali Linux
Rockyou is a password dictionary that is used to help perform various kinds of password brute-force attacks. It is a collection of the most widely used and potential access codes. Rockyou.txt download is a free wordlist found in Kali Linux used by various penetration testers.
Many tools use the dictionary attack method; this requires a wordlist.
By default, Offensive Security has added many dictionaries in Kali Linux. This is one of the biggest amongst others. This guide teaches you how to find its location and unzip it.
What is Rockyou Txt Used for?
It was first added in backtrack and then in this. 1n 2013, the first version was launched.
It is awesome to use as one can create his own dictionary using such an attack.
For a wonderful dictionary use “crunch” and “cwel”, in case you are a beginner and want to test or practice any tool then this one is for you.
Why Choose Rockyou
Many lists are present online; some are free to download while others need to be purchased. These are collections of passwords used once by users.
Recovering them is a real art required just above each type of penetration test. These are kinds of tools that penetration testers and other CyberSecurity professionals require to make their jobs easier yet efficient. Anyone out there who wished to discover or recover them needs to learn how to use these with their password cracking software.
Rockyou Password List Location in Kali Linux
For now, we do not know the correct location even we have used it many times.
Let us direct you to find it out in case you forget it.
Following is the command locate used to find a file in Linux in all directories or any specific location.
Check out the last line, the location is
Confirm it by using the Is command followed by the wordlist location.
The example is as follows:
How to Unzip rockyou.txt.gz To rockyou.txt
Its file carries a .gz extension of the file. Keep in mind that this is not a normal file it is a ZIP. You can neither see content from this nor use it.
This is not useful anymore therefore you need to extract or unzip it by using the following commands:
Such tests require some kind of cracking for the tests done internally, the tester would have to guess the captured hashes to access the domain. That can involve many hashes pulled from the domain controller that shall have to crack for the tester so that he can evaluate the overall effectiveness of access codes. Knowing the strengths and weaknesses of an organization’s password, help the IT team to communicate proper ways to choose them that are harder to guess, making the overall protection of digital information a bit better.
Using these to aid in such a method makes penetration testing quite faster. These can try out thousands of passcodes within seconds which saves a lot of time for the testers, time that can be better spent resolving any vulnerabilities their test identifies.
If you are a tester or want to become one then it is important that you know about these lists, how they work, where to get them from, and how to use such tutorials shall provide users with all the knowledge they need to utilize lists to simplify the testing process.
Creating Your Own Custom Wordlist
Beginners who learn brute-force attacks against WPA handshakes are let down by limitations of default lists like this which is based on stolen access codes. Science of these goes beyond using these default lists, allowing users to be more efficient by making customized lists. Using mentalists, generate millions based on details regarding the target.
This is along-established art that relies on a combination of brute-force processing power and the ability to refine the list down to likely options based on what we know about the target. Different security protocols are vulnerable to such attacks which at core rely on some key principles.
First, you must be allowed to try out different passcodes many times quickly. After this, you need to be able to determine the difference between success and failure. Moreover, you need to have a list of codes to try out automatically. Finally, this needs to present in the list for the attack to succeed. As this list gets bigger, CPU and GPU performance becomes important as the rate at which these can be attempted is sped up.
Rockyou is best for Brute-Forcing WPA, SSH, FTP & other credentials
Wireless networks are mostly secured by WPA or WPA2 encryption, this is able to be cracked by network handshake and using the system’s CPU to brute-force it. Besides, WPA, protocols such as SSH and FTP are vulnerable to it though methods of this can be differentiated between online and offline type attacks.
In online attacks, we are directly connected to a service and send passcode attempts in a way that can be logged. An example is Reaver or SSHtrix, this needs to be connected with the network on which the host is to send guesses. In such cases, the limiting factor is often how many incoming connections FTP or SSH or server can accept and the amount of time spent connected to the host.
In offline attacks, the major limiting factor is the CPU or GPU’s ability to try out different passwords very quickly. An example can be the brute-forcing WPA handshake, a WPS-Pixie dust attack after collecting required information or hashes from the stolen database. This is the only time to be a bit worried about the performance of your GPU or CPU during this.
Rather than starting with a dictionary-style attack, an attacker who is smart will first look for lists that carry the real passcodes; these are known as the starting point for these kinds of techniques, as they work against anyone with a truly common one. In the wild, expect the success rates to be around 15% for these types of audits. If you are targeting a certain network or account then the chances of success are pretty small.
This being said, users can still use these lists as a seed for a more refined attack that is based on information that you know regarding the target. The reason behind these lists being effective is that you think of them as a statistical survey of the common passcodes used by people in the wild, these can be used as a seed to change small things such as adding or removing numbers, in a program that is known as word mangler.
For all the ethical hackers out there, a wealth of information is present online to crack a certain target. A Brute-force attack by the average script-kiddie might not be a substantial threat to an organization that enforces using strong access codes. An attack that is well-researched can cut down the number of guesses and present only relatively strong guesses based on information available regarding the target and any requirements. This makes an attack quite effective against selected, well-researched parts of the target’s infrastructure.
Update: RockYou2021 Password File Download
The password list was just leaked online by a user on a forum. The user claimed that the records are around 100 GB in a text file. The claim was made that there are around 82 Billion different combinations of words. Upon checking and analyzing the file there were much fewer. The passwords available are of various length sizes of around between 20 and 6 characters.
Various security researchers made their verdict that this file is made up of various other breaches combined. The precise size of the list came to be around 3.2 Billion which is a very large scale. Researchers are also saying that it may have Gmail and LinkedIn hashes too. The RockYou2021 download should be available soon.
Note: These are only the most unique ones and not the ones discovered in the (COMB) breaches.
Rockyou Txt (Rockyou.txt 2021) Download 2022/2023 – Best Password List File
I hope your search for finding the biggest password list has now ended as you have discovered Rockyou.txt.gz download. We share its location with you and where you can find it in Kali Linux. We take it a step further and also show you how to unzip the .gz wordlist file. This can also be used in tools such as Cain and Abel.
Rockyou.txt size: 133 MB (100 GB when fully uncompressed).
Author: Hob0Rules
Rockyou is one of the most in-demand password lists available with Kali Linux. It has the most complex combinations of passwords that you can use to guess a password.
What is Rockyou wordlist?
rockyou wordlist is a password dictionary used to help to perform different types of password cracking attacks. It is the collection of the most used and potential passwords.
Many Password cracking tools are used dictionary attack method to retrieve the password. If you are using same method to crack the password then you will have to require a password wordlist.
So Offensive Security (Mother of Kali Linux) has added already many dictionaries in Kali Linux by default, RockYou wordlist is one of the biggest dictionaries.
Rockyou wordlist in Kali Linux 2022.2
First, rockyou wordlist was added in the backtrack and later it was added in Kali Linux 1. This is the first version of kali Linux launched in 2013.
I have eyes on Kali Linux from the born of it. by the way, using Kali Linux awesome. You can create your own dictionary during a password cracking attack.
You can use crunch and cwel for creating a wonderful dictionary. But if you are a beginner and just want to test tools or practice the tool, then RockYou wordlist is good for you.
Location of Rockyou wordlist
Trust me or not, you can’t remember rockyou location if I will tell you. Right now I don’t know the location exactly. I can’t remember it. Even I used this dictionary multiple time.
Who cares about its location?
I believe to give you a direction to find out the location by yourself whenever you forget the location.
Here is the command locate which is used to Find a File in Linux in All Directories. or any specific location.
Use the following command to know the location of rockyou wordlist:
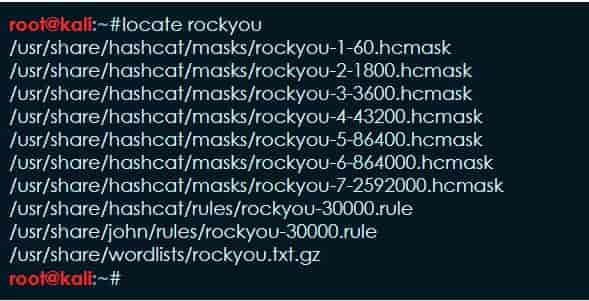
[email protected]:~#locate rockyou /usr/share/hashcat/masks/rockyou-1-60.hcmask /usr/share/hashcat/masks/rockyou-2-1800.hcmask /usr/share/hashcat/masks/rockyou-3-3600.hcmask /usr/share/hashcat/masks/rockyou-4-43200.hcmask /usr/share/hashcat/masks/rockyou-5-86400.hcmask /usr/share/hashcat/masks/rockyou-6-864000.hcmask /usr/share/hashcat/masks/rockyou-7-2592000.hcmask /usr/share/hashcat/rules/rockyou-30000.rule /usr/share/john/rules/rockyou-30000.rule /usr/share/wordlists/rockyou.txt.gz [email protected]:~#
See the last line of the result in the above image. the location is /usr/share/wordlists/rockyou.txt.gz
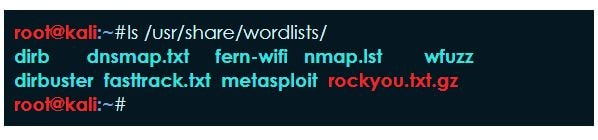
You can confirm the location by using the ls command followed by rockyou wordlist location.
[email protected]:~#ls /usr/share/wordlists/ dirb dnsmap.txt fern-wifi nmap.lst wfuzz dirbuster fasttrack.txt metasploit rockyou.txt.gz [email protected]:~#
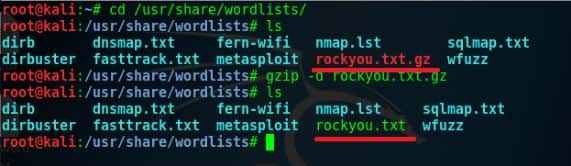
Unzip rockyou.txt.gz into rockyou txt
Have you noticed one thing? The rockyou file has .gz extension of the file. This is not a normal file, this is a zip file. Neither you can see the content from this file nor you can use it.
zip file is not useful anymore. So you need to extract / unzip by using following commands
I hope you have liked this article, If yes then please thumbs up. If you have questions leave in the comment box. Whenever I will get time, reply to you.
Thanks for Reading full article.