- Spoof Email Address using Espoofer in Kali Linux
- Install Espoofer
- Setting up the Config File
- Launch Attack
- Saved searches
- Use saved searches to filter your results more quickly
- hackerxphantom/Spoof_AnyMail
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
- Saved searches
- Use saved searches to filter your results more quickly
- License
- lunarca/SimpleEmailSpoofer
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- How Hackers Send Fake Mail Using SETOOLKIT
Spoof Email Address using Espoofer in Kali Linux
W elcome back again to GigoCyberSpace.com. Sorry for not being around. I have been working on a project.
Today we’re going to learn how to spoof your email or email messages using espoofer in Kali Linux. There are different types of spoofing in penetration testing like IP Spoofing, DNS Spoofing, MAC Spoofing but we’re going to go on Email Spoofing.
In email spoofing, the attacker forges the sender’s email address, making it appear as if the message originated from a different person or organization. Espoofer has the ability to spoof email address using it’s tools. And what more it can bypass SPF/DKIM/DMARC authentication.
Espoofer has special features like spoofing email even with authentication. But for you to meet the requirements must me have port 25 open and not block by your ISP. Also there are three more you use to initiate this attack:
- Server Mode(which is default configuration) — This requires n IP address and port 25 not blocked by your ISP
- Client mode — Must have an account with the victim(for example the hacker must have an account in Gmail if the victim address is vitcim@gmail.com)
- Manual mode — For debug purposes
But in this tutorial, we will use Client Mode for simplicity.
Install Espoofer
Install Espoofer from the tool from GitHub by typing:
root@kali: ~ # git clone https://github.com/chenjj/espoofer
And install the required modules in pip with the command:
root@kali: ~ # pip install -r requirements.txt
Setting up the Config File
You need to set the configuration in a python file called config.py to set for example the receiver’s and sender’s email, your password, email to be spoofed and case id. Your case id is like how espoofer would treà treat the spoofing and attack. The case id case_a1 is the would convenient case being used. Other case ids are:
Set the configuration file like this:
config =< “legitimate_site_address”: b””, “victim_address”: b””, “case_id”: b”client_a1>″, “client_mode”: < “sending_server”: (“smtp.gmail.com”, 587), # SMTP sending serve ip and port #Your Real Email and Password “username”: b””, “password”: b””, >, >
Launch Attack
Now we’re set up the configuration file, it is time to launch the attack. Please just note that the SMTP server should be your own message server and not the receiver’s.
Now type this to launch the attack:
root@kali: ~ # python3 espoofer.py -m c
And that’s it. Once this is executed if everything requirements is meet, you will successful spoof your email address. If not seen in inbox, check your spam and promotion tab.
Tank you and see you next time.
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Most Powerful Send Fake Mail Using Any Mail I’d undetectable
hackerxphantom/Spoof_AnyMail
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Most Powerfull Fake Mail Sender Tool
Spoof_AnyMail Undetectable Tool
Commands to run tool in ur terminal
Note : Tool is Made of Educational Purposes only. Please try not to harm anyone device it's For Fun Purpose Not For Revenge (Join Us All https://bit.ly/3PV3S3r)
Spoof_AnyMail is a bash && Python based script which is officially made for termux && linux users and from this tool you can Send Any Fake Mail Using Anyone Mail. This tool works on both rooted Android device and Non-rooted Android device.
- [+] Send Fake Mail To anyone!
- [+] Use any Mail ID to send Fake Mail !
- [+] Easy for beginners !
- [+] Working spoof anymail tool for termux && linux !
Language is used to Make this tool
Commands to run tool in ur Termux
pkg update && pkg upgrade -y git clone https://github.com/hackerxphantom/Spoof_AnyMail
Scrool Down For ScreenShots
Commands to run tool in ur Kali Linux
sudo apt-get update && pkg upgrade -y sudo apt-get install git -y
git clone https://github.com/hackerxphantom/Spoof_AnyMail

About
Most Powerful Send Fake Mail Using Any Mail I’d undetectable
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
A simple Python CLI to spoof emails.
License
lunarca/SimpleEmailSpoofer
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
A few Python programs designed to help penetration testers with email spoofing.
Due to improvements in email protections and anti-spam techniques, it is no longer effective to attempt to spoof emails simply because they do not have a proper DMARC record or from arbitrary email servers. This project is retired and will not be maintained.
Email servers do not accept connections from normal computers. In an effort to limit the amount of spam, most MTAs will only accept connections from relays that have a fully-qualified domain name (FQDN). As such, the easiest way to use this project is from a Linux Virtual Private Server. There are several free or cheap options available, such as Digital Ocean, Linode, and Amazon EC2.
Once the server is set up, the next step is to install and start an SMTP server. This is required to actually send the spoofed emails. I personally use Postfix, though any will do. This script defaults to using localhost:25 for the mail server.
On Kali Linux, the easiest method of doing this is:
sudo apt-get install postfix sudo service postfix start
When installing postfix, specify Internet-facing and provide the correct FQDN when prompted.
This script has two dependencies:
These can be installed using pip:
pip install -r requirements.txt
Add the desired contents of the email in HTML format to an HTML file. Then, execute the following command:
./SimpleEmailSpoofer.py -e [Path to Email file] -t [To address] -f [From address] -n [From name] -j [Email subject]
Additional flags can be found by running
Email spoofing has been an issue since the earliest days of the SMTP protocol. The root cause of email spoofing is that SMTP does not require authentication between mail relays. An attacker can stand up or find an «Open Relay» (i.e. an SMTP server that can send from arbitrary domains), which is the default configuration for SMTP servers, and use that to send arbitrary emails from arbitrary email addresses.
In an effort to combat spam, many SMTP servers now block any mail relay that does not have a Fully-qualified Domain Name (FQDN). An FQDN is a DNS A record that points to the relay’s IP address. This can be either a domain purchased from a domain registrar, or by using a domain automatically associated with a virtual private server.
As email spoofing is a serious and widespread issue, over the years several protection mechanisms have been added to combat it. However, all of these protections are opt-in and require significant configuration. As such, as much as 98% of the internet is still vulnerable. For additional information, please see the Bishop Fox blog post on the subject.
To determine if a domain is vulnerable to email spoofing, Bishop Fox has created two tools:
- A web interface that produces a report with analysis and recommendations
- A command line utility that only performs analysis
Only use this tool for education, research, or in the course of approved social engineering assessments. While email spoofing is a powerful tool in the social engineer’s arsenal, it is also trivial to identify the server that sent any email. Furthermore, this tool makes no claims to bypass any products such as Barracuda or ForcePoint email protections suites. Please use responsibly.
The Spoofcheck program, which allows users to identify whether or not domains are vulnerable to email spoofing, has moved to the following repository:
How Hackers Send Fake Mail Using SETOOLKIT
The information security environment has changed vastly over the years. Now, in spite of having security policies, compliance, and infrastructure security elements such as firewalls, IDS/IPS, proxies, and honey pots deployed inside every organization, we hear news about how hackers compromise secured facilities of the government or of
private organizations because of the human element involved in each activity.
Typically, employees are not aware of the tricks and techniques used by social engineers in which they can be used as mediators to gain valuable information such as credit card details or corporate secrets. The security of the entire organization can be at stake if an employee visits a malicious website, answers a social engineer’s phone call, or clicks on the malicious link that he/she received in their personal or company e-mail ID.
Today we’ll show you a method through which you can easily send a fake email with one of the most popular tools called SET (Social Engineering Toolkit).
The Social-Engineering Toolkit (SET) is a product of TrustedSec. SET is a Python-driven suite of custom tools created by David Kennedy (ReL1K) and the SET development team, comprising of JR DePre (pr1me), Joey Furr (j0fer), and Thomas Werth.
SET is a menu-driven attack system that mainly concentrates on attacking the human element of security. With a wide variety of attacks available, this toolkit is an absolute must-have for penetration testing.
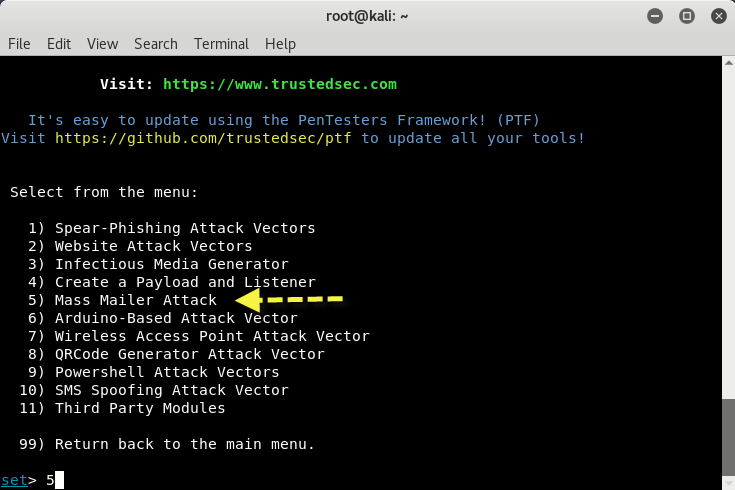
SET comes preinstalled in Kali Linux. You can simply invoke it through the command line using the command “setoolkit“.
Once the user clicks on the SET toolkit, it will open with the options shown in the following screenshot:
Select 1) Social-Engineering Attacks to receive a listing of possible attacks that can be performed.
You can select the attacks that you want to perform from a menu that appears as follows:
- 1 Spear-Phishing Attack Vectors
- 2 Website Attack Vectors
- 3 Infectious Media Generator
- 4 Create a Payload and Listener
- 5 Mass Mailer Attack
- 6 Arduino-Based Attack Vector
- 7 Wireless Access Point Attack Vector
- 8 QRCode Generator Attack Vector
- 9 Powershell Attack Vectors
- 10 SMS Spoofing Attack Vector
- 11 Third-Party Modules
- 99 Return back to the main menu
We will start with the Mass Mailer Attack. Enter 5 to move to the next menu.
For this example, on the list, we will take a look at the first option, E-Mail Attack Single Email Address.
Now further you need to fill all the following details as shown below:
- Send email to:
- From address:
- The FROM Name the user will see:
- Username for open-relay:
- Password for open-relay:
- SMTP email server address:
- Port number for the SMTP server:
- Flag this message/s as high priority?:
- Do you want to attach a file:
- Do you want to attach an inline file:
- Email Subject:
- Send the message as html or plain:
- Enter the body of the message, type END when finished:
Here you just need an open relay SMTP server which you can easily get it through smtp2go.com by creating a free account whose SMTP server address will be “mail.smtp2go.com“and port will be “2525“.
This is the output of the fake email which we sent from spyboyblog@gmail.com via smtp2go.com open relay server.
In SMTP2GO.com App Dashboard, you can even manage all the records and can see all the information about the fake emails sent from your account as shown below: