- Вики IT-KB
- Утилита ldapsearch (клиент OpenLDAP) и проверка подключения к контроллеру домена Active Directory
- Проверка подключения по протоколу LDAP (TCP 389)
- Проверка подключения по протоколу LDAPS (TCP 636)
- Проверка подключения по протоколу LDAP с защитой StartTLS (TCP 389)
- Обсуждение
- How To Install LDAP Client On Ubuntu 20.04
- Tutorial Install LDAP Client On Ubuntu 20.04
- Install and Configure LDAP Client on Ubuntu 20.4 | Ubuntu 18.04
- LDAP Client configuration
- Conclusion
- LDAP Browser For Linux
- LDAP Admin Tool v6.10 has been released!
- Access multiple directory servers
- Welcome to the Cutting Edge
- SSL
- Query LDAP like Database
Вики IT-KB
Утилита ldapsearch (клиент OpenLDAP) и проверка подключения к контроллеру домена Active Directory
Проверку выполняем на примере Debian GNU/Linux 8 (Jessie). Сначала убедимся в том, что клиент OpenLDAP установлен в системе:
ii ldap-utils 2.4.40+dfsg-1+deb8u2 amd64 OpenLDAP utilities ii libldap-2.4-2:amd64 2.4.40+dfsg-1+deb8u2 amd64 OpenLDAP libraries
Исходные данные для проверки подключения клиента OpenLDAP к LDAP-каталогу на примере контроллера домена Active Directory (AD):
s-LDAP-Check-User — Имя пользователь в домене AD, от имени которого выполняется подключение (уровень прав в домене — рядовой пользователь);
«OU=Test Users,OU=KOM,DC=ad,DC=holding,DC=com» — DN-имя контейнера в AD, в котором выполняется поиск пользователя Test-User.
Проверка подключения по протоколу LDAP (TCP 389)
Используется подключение типа ldap:/. Учётные данные пользователя s-LDAP-Check-User передаются по сети в открытом виде:
$ ldapsearch -v -x \ -D "s-LDAP-Check-User@ad.holding.com" -w "PaZsw0rd" \ -b "OU=Test Users,OU=KOM,DC=ad,DC=holding,DC=com" \ -H "ldap://dc01.ad.holding.com" sAMAccountName=Test-User
Проверка подключения по протоколу LDAPS (TCP 636)
Используется подключение типа ldaps:/. LDAP-сессия шифруется с помощью SSL-сертификата, предоставляемого контроллером домена. Чтобы LDAP-клиент доверял сертификату контроллера домена, нам нужно создать файл, содержащий корневые сертификаты доменных Центров сертификации, которыми подписан сертификат контроллера домена. Назовём этот файл, например /etc/ssl/certs/cacerts.pem, и скопируем в него корневые сертификаты доменных ЦС в формате PEM и кодировке Base-64.
Изменим на время проверки конфигурационный файл клиента OpenLDAP /etc/ldap/ldap.conf, указав в переменной TLS_CACERT путь к созданному нами файлу с корневыми сертификатами доменных ЦС:
. #TLS_CACERT /etc/ssl/certs/ca-certificates.crt TLS_CACERT /etc/ssl/certs/cacerts.pem .
После этого можно попробовать выполнить поиск по протоколу LDAPS:
$ ldapsearch -v -x \ -D "s-LDAP-Check-User@ad.holding.com" -w "PaZsw0rd" \ -b "OU=Test Users,OU=KOM,DC=ad,DC=holding,DC=com" \ -H "ldaps://dc01.ad.holding.com" sAMAccountName=Test-User
Проверка подключения по протоколу LDAP с защитой StartTLS (TCP 389)
Используется подключение типа ldap:/ с дополнительными ключами, включающими TLS : -Z и -ZZ. LDAP-сессия также шифруется с помощью SSL-сертификата, предоставляемого контроллером домена. Первичное подключение к контроллеру домена AD происходит по порту 389, затем создаётся отдельный защищённый TLS-туннель, внутри которого и происходит весь LDAP-обмен между клиентом и сервером. Используется настроенный нами ранее файл корневых сертификатов доменных ЦС.
$ ldapsearch -Z -v -x \ -D "s-LDAP-Check-User@ad.holding.com" -w "PaZsw0rd" \ -b "OU=Test Users,OU=KOM,DC=ad,DC=holding,DC=com" \ -H "ldap://dc01.ad.holding.com" sAMAccountName=Test-User
Автор первичной редакции:
Алексей Максимов
Время публикации: 19.03.2017 18:04
Обсуждение
unix-linux/linux-cli-tools/openldap-ldap-client-check-connection-to-active-directory-domain-controller-with-ldapsearch.txt · Последнее изменение: 19.03.2017 19:05 — Алексей Максимов
How To Install LDAP Client On Ubuntu 20.04
The Lightweight Directory Access Protocol is a core protocol that was developed for directory services. It is designed to be used to distribute lists of information organized into directory information tress which is stored within an LDAP database. Users must first authenticate their identity to be able to access the information stored within an LDAP database. You may have been forced to tolerate a very unlovable classmate because he is very well at your common project! To reach a target, you accept this symbolic relationship. Also, there is a symbolic relationship between the LDAP client and server. In fact, the server needs the client to ask it questions such as usernames, home directory locations, group memberships, and so on. The client needs the server to feed it information and it will be responsible for delivering that information. In this article, you will learn How To Install LDAP Client On Ubuntu 20.04. If you need to buy a Dedicated Server, we will keep a real relationship with you and support you in any hours of day and night. Purchase your own Ubuntu VPS safely.
To let this tutorial work better, please consider the below Prerequisites:
A non-root user with sudo privileges.
Tutorial Install LDAP Client On Ubuntu 20.04
LDAP is an open-source and cross-platform protocol to be used for directory service authentication. There are many different implementations available. It is used to store and retrieve data from a hierarchical directory structure.
Install and Configure LDAP Client on Ubuntu 20.4 | Ubuntu 18.04
You are ready to start to install and configure the LDAP client when you configure the LDAP server and add user accounts.
In case you have no active DNS server in your network, add the LDAP server address to /etc/hosts.
sudo vim /etc/hosts 192.168.18.50 ldap.example.comTo install LDAP client utilities on your Ubuntu system, run:
sudo apt -y install libnss-ldap libpam-ldap ldap-utilsLDAP Client configuration
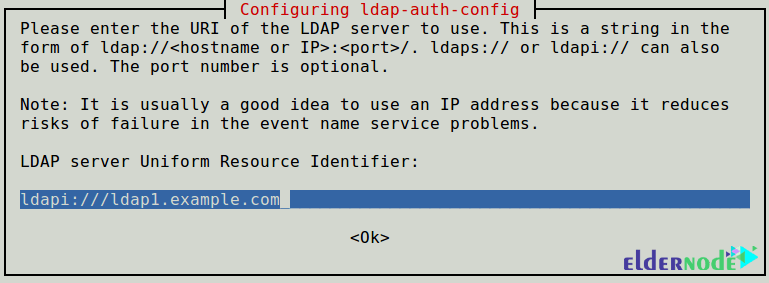
Now, you can set LDAP URL. It can be an IP address or hostname. You will be prompted for details of your LDAP server. The ldap-auth-config package is auto-installed will do most of the configuration based on the inputs you enter.
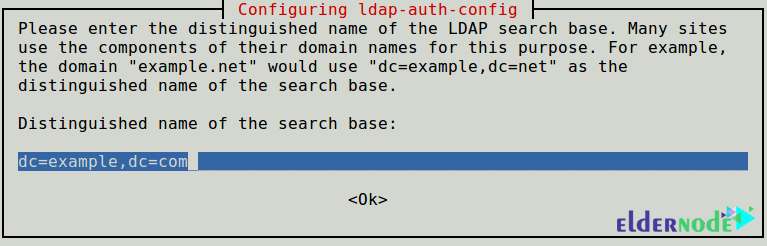
Then, you should enter the name of the LDAP search base, so set a distinguished name of the search base. You can use the components of their domain names.
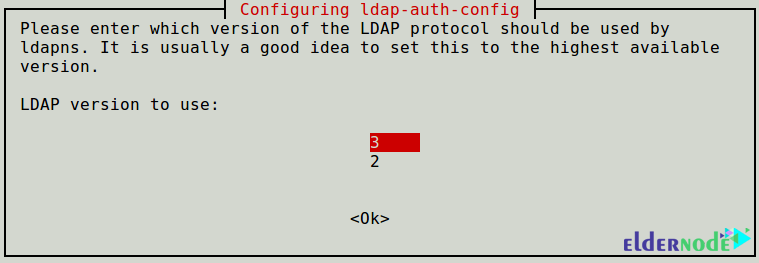
Select LDAP version 3 to use and click Ok.
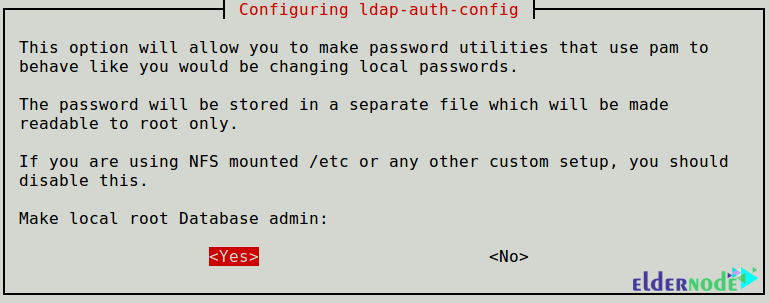
To be able to make password utilities that use Pam to behave like you would be changed local passwords. So, to Make local root Database admin, press Yes.
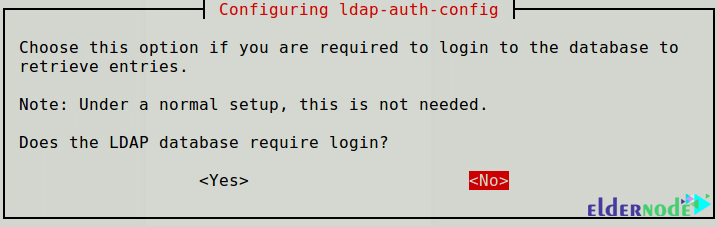
In this step, you will answer No for Does the LDAP database require login? to disable login requirements to the LDAP database.
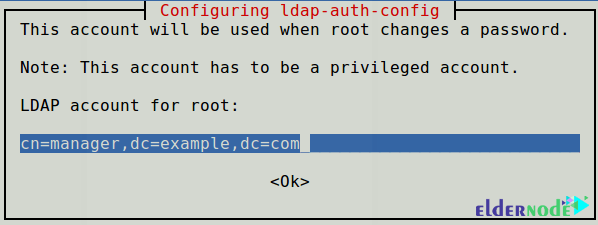
You need to set the LDAP account for root.
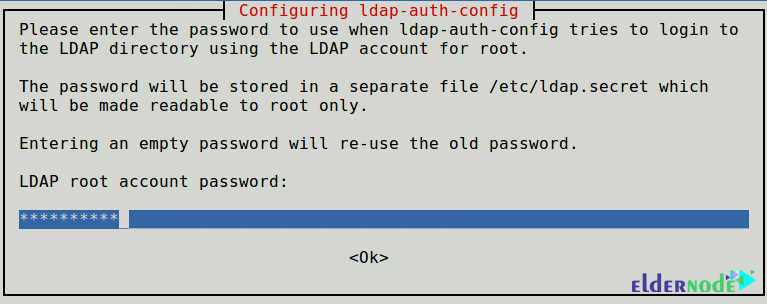
You need to consider a password to use when ldap-auth-config tries to log in to the LDAP directory using the LDAP account for root.
You can find the result of the dialog in the file /etc/ldap.config. If you need to make some changes, open and edit this file using your considered command-line editor.
Now, to configure the LDAP profile for NSS, type:
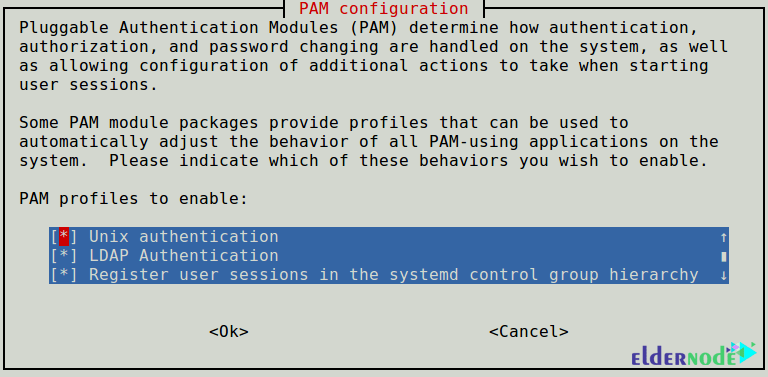
sudo auth-client-config -t nss -p lac_ldapNext, to use LDAP for authentication by updating PAM configurations, you must configure the system. Choose LDAP from the menu and log in using LDAP-based credentials.
If you wish the home directory of the user to be created automatically, perform one more configuration in the common-session PAM file.
sudo vim /etc/pam.d/common-sessionAnd add the line below in it:
session required pam_mkhomedir.so skel=/etc/skel umask=077At this point, you can save the changes and close the file. Restart Name Service Cashe Daemon (NCSD) by running:
sudo systemctl restart nscdsudo systemctl enable nscdIn the case of using replication, LDAP clients will need to refer to multiple servers specified in /etc/ldap.conf. Specify all the servers in the following form:
uri ldap://ldap1.example.com ldap://ldap2.example.comIt implies that the request will time out and if the provider becomes unresponsive, the consumer will attempt to be reached to process it.
Consider the provider for ldap1.example.com and the consumer as ldap2.example.com
Finally, use the command below to check the LDAP entries for a particular user from the server.
That’s that! Once you view the details of the specific user from the /etc/passwd file, it means your client machines are configured to authenticate with the LDAP server. So, you should be able to log in using LDAP-based credentials.
Conclusion
In this article, you learned How To Install LDAP Client On Ubuntu 20.04. Using LDAP helps you to have the communication language to communicate the applications with other directory services servers. The information of the users needs to be shared with other entities on the network and directory services store the users, passwords, and computer accounts.
Click on a star to rate it!
Average rating 0 / 5. Vote count: 0
No votes so far! Be the first to rate this post.
LDAP Browser For Linux
Installation Instructions: Download the .sh file, give the file executable permission and run the file.
LDAP Admin Tool v6.10 has been released! 
Access multiple directory servers
LDAP Admin Tool allows you to access OpenLDAP, Netscape/iPlanet, Novell eDirectory, Oracle Internet Directory, IBM Tivoli Directory, Lotus Domino, Microsoft Active Directory or any other LDAP v2 or LDAPv3 directory server. You can also connect to multiple directory servers simultaneously and copy data across servers. More LDAP Admin Tool features
Welcome to the Cutting Edge
LDAP Admin Tool sets the pace with dozens of new features, including the search tool bar, attribute editors, tabbed browsing, sqlldap search, server monitor and fast performance. More LDAP Admin Tool features
SSL
LDAP Admin Tool allows you to connect to the ldap server using SSL/TLS. You can add certificate to your store using Manage Certificates or it will prompt you to add the certificate to your store (Like any html browser.. Would you like to continue any way). More LDAP Admin Tool features
Query LDAP like Database
LDAP Admin Tool allows you to search the LDAP using SQL like syntax. It provides two powerful tools which allow you either to edit query text directly with syntax highlighting or to build a query visually with a drag and drop of keywords and attributes. More LDAP Admin Tool features
Linux® is a registered trademark of Linus Torvalds in the United States, other countries, or both. Red Hat® Enterprise Linux® and Red Hat® Linux® are trademarks of Red Hat, Inc. in the United States, other countries, or both. SUSE® is a trademark of SUSE AG, a Novell business, in the United States, other countries, or both. eDirectory is a trademark of Novell, Inc. in the United States, other countries, or both. Siemens® is a registered trademark of Siemens AG.Oracle® is a registered trademark of Oracle Corporation and/or its affiliates. OpenLDAP® is a registered trademark of OpenLdap Foundation. Ubuntu is a registered trademarks of Canonical Ltd. . Other third-party trademarks are the property of their respective owners.
- Products
- LDAP Admin Tool
- AD Admin Tool
- AD Admin & Reporting Tool
- LDAP Admin Tool Professional Edition
- LDAP Admin & Reporting Tool
- LDAP Plus AD Help Desk Tool
- Purchase License
- Discounts Program
- More Ways to Buy
- LDAP Admin Tool EULA
- Shopping Cart
- Shopping FAQ
- LDAP Client Support
- LDAP Admin Tool Documentation
- AD Admin Tool Documentation
- AD Admin & Reporting Tool Documentation
- LDAP Admin & Reporting Tool Documentation
- LDAP Plus AD HelpDesk Prof. Tool Documentation
- Upgrade Center
- Order Status
- LDAP Browser For Linux
- LDAP Browser For Windows
- LDAP Browser For Mac
- LDAP Client
- Contact Us
- Privacy Policy
- Download Center
Terms of Service | DMCA Policy | Copyright © 2020-2021 LDAPSoft Corporation. All rights reserved.